-
 Data Security
Data SecurityMar 04, 2025
Varonis Named a Leader and Customer Favorite in The Forrester Wave™: Data Security Platforms, Q1 2025
Varonis is recognized in The Forrester Wave™ for its strongest Current Offering and Strategy, receiving more 5/5 scores than any vendor evaluated.

Avia Navickas
2 min read
-
 AI Security Data Security
AI Security Data SecurityMar 03, 2025
AI Security: Frequently Asked Questions for 2025
AI-related questions and answers for business leaders. If you're trying to build more productive and secure AI strategies, these are the FAQS for you.

Shawn Hays
12 min read
-
 Cloud Security
Cloud SecurityFeb 28, 2025
Overcoming Cloud Security Challenges: Key Risks and Threats
Moving to the cloud brings several benefits, but it also means dealing with new security issues.

Daniel Miller
5 min read
-
.png) Varonis Products
Varonis ProductsFeb 27, 2025
What’s New in Varonis: February 2025
Discover Varonis' latest features, including automated Google Workspace labeling, Azure Blob exposure remediation, Entra ID group remediation, and more.

Nathan Coppinger
2 min read
-
 Data Security
Data SecurityFeb 26, 2025
Varonis Opens Data Centers in India to Support Expanding Customer Base and Minimize Cloud Data Risk
Varonis' newest international data centers in India help customers comply with local regulatory frameworks and data privacy sovereignty rules.

Megan Garza
1 min read
-
 Cloud Security
Cloud SecurityFeb 26, 2025
Understanding Cloud Governance: A Comprehensive Guide
In the rapidly evolving digital landscape, cloud governance has emerged as a crucial framework for organizations using cloud technologies.

Daniel Miller
3 min read
-
 Cloud Security
Cloud SecurityFeb 24, 2025
What is Cloud Security?
The risks associated with cloud environments are only growing. This blog highlights the basics of cloud security to secure data in the cloud.

Daniel Miller
4 min read
-
 Threat Research
Threat ResearchFeb 13, 2025
Astaroth: A New 2FA Phishing Kit Targeting Gmail, Yahoo, AOL, O365, and Third-Party Logins
Discover how Astaroth phishing kits bypass security, offer bulletproof hosting, and how Varonis protects businesses from advanced cyber threats.

Daniel Kelley
2 min read
-
 AI Security Salesforce
AI Security SalesforceFeb 11, 2025
3 Steps to Get Ready for Agentforce
Discover the risks of enabling Agentforce without proper data security and learn specific tactics to ensure a safe deployment.

Eugene Feldman
4 min read
-
 AI Security Data Security
AI Security Data SecurityJan 31, 2025
DeepSeek Discovery: How to Find and Stop Shadow AI
Understand the security implications of employees using DeepSeek, such as shadow AI, and how your organization can immediately mitigate risks.

Rob Sobers
2 min read
-
.png) Varonis Products
Varonis ProductsJan 30, 2025
What’s New in Varonis: January 2025
Discover Varonis' latest features, including recommendations for right-sizing access in AWS, new M365 remediation policies, and enhanced search management.

Nathan Coppinger
2 min read
-
 Threat Research
Threat ResearchJan 29, 2025
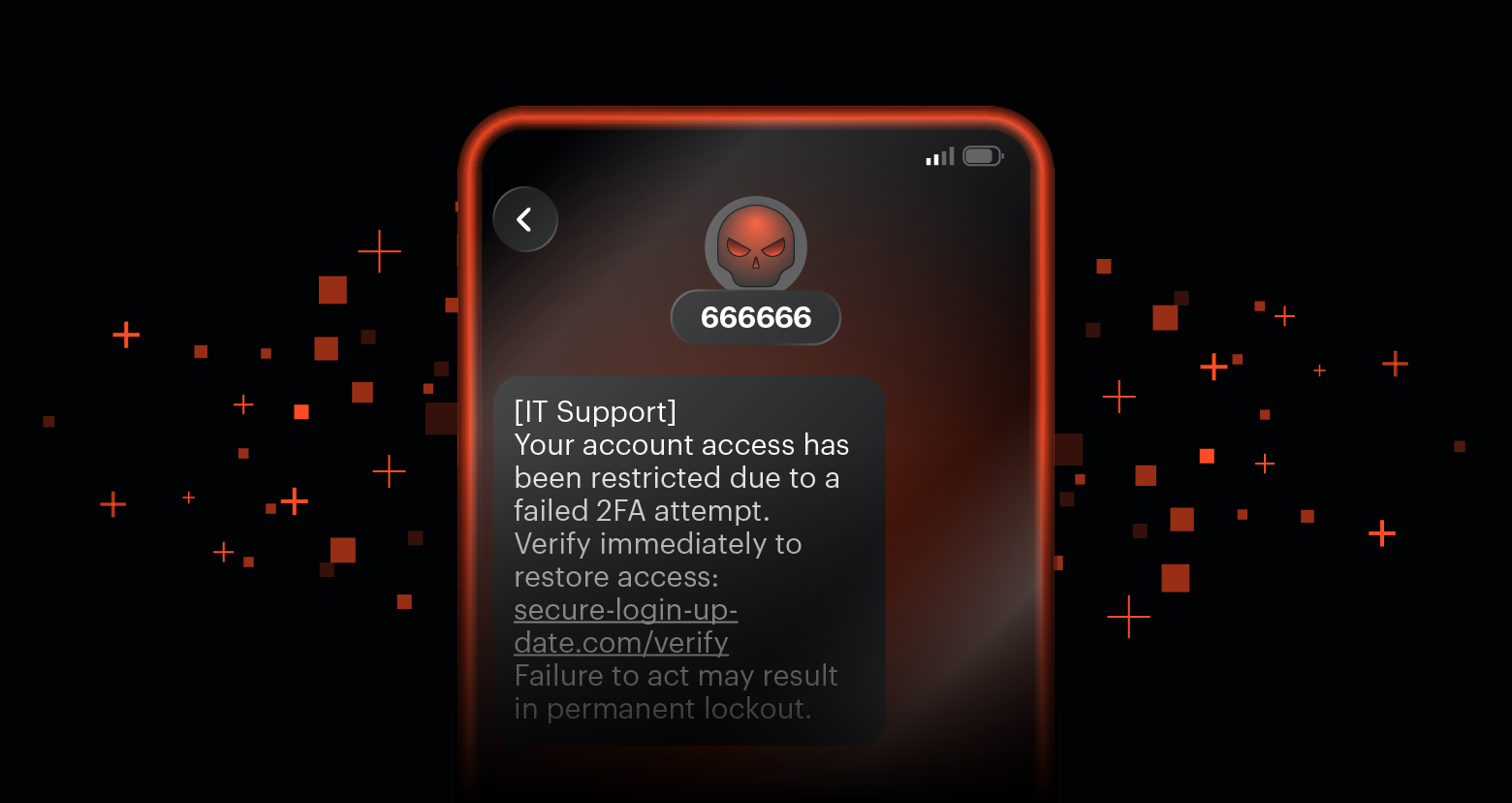
Devil-Traff: A New Bulk SMS Platform Driving Phishing Campaigns
Discover how the Devil-Traff bulk SMS platform fuels phishing attacks with spoofing and automation.

Daniel Kelley
2 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital


