Alerts aren’t protection. Legacy DAM isn’t enough.
IBM Guardium is a legacy DAM that requires appliances, agents, manual workflows, and years’-long deployment cycles.
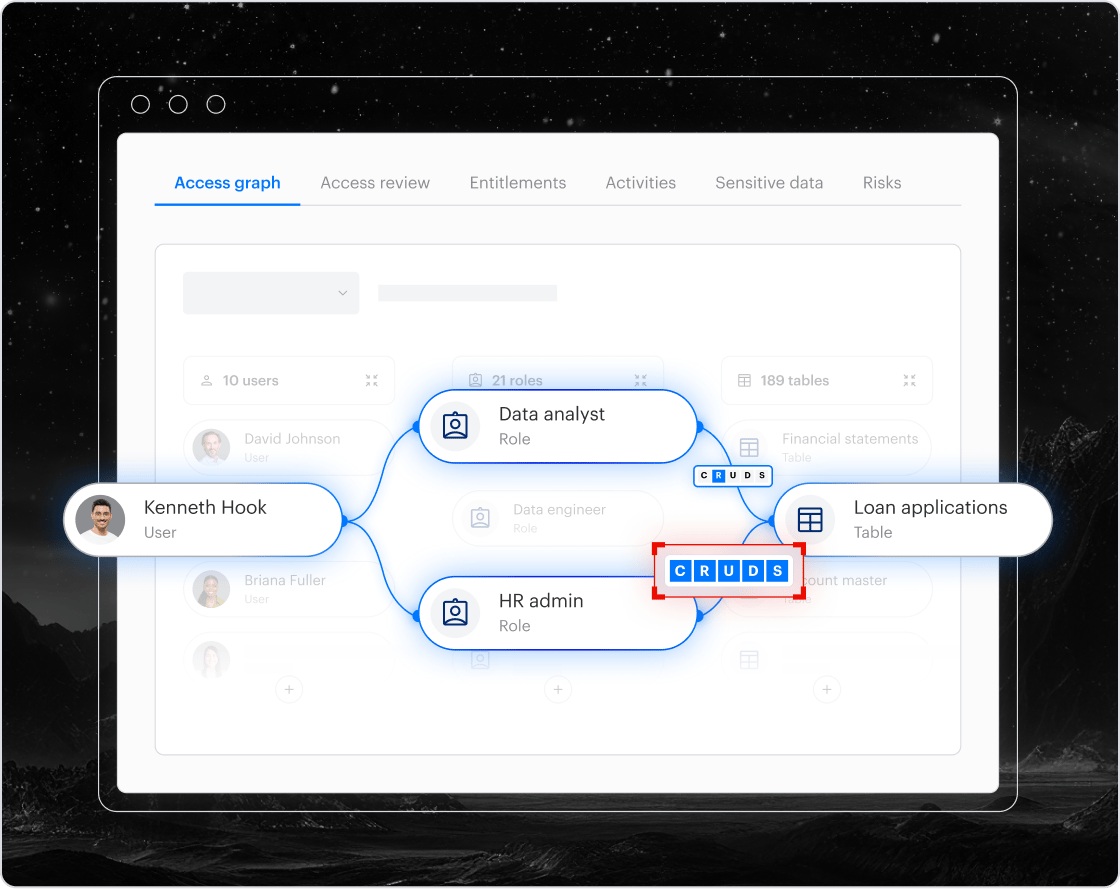
Varonis DAM is a next-gen, agentless database security and activity monitoring system that’s part of a unified data security platform that reduces exposure automatically and detects threats in real time.


Partner with a leader in data security.

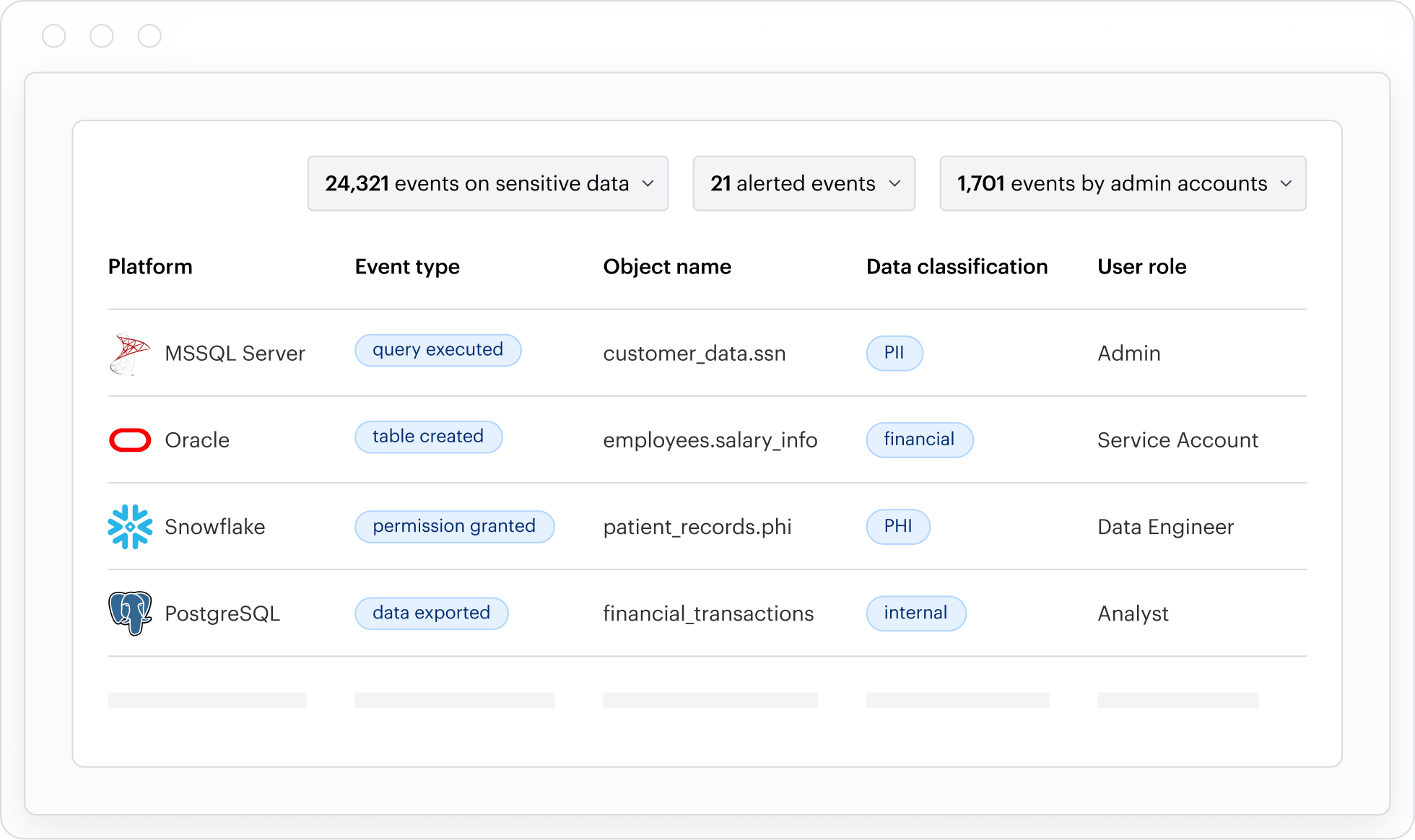
Feature Comparison
Guardium is a legacy DAM. Varonis is modern data security platform.
Guardium provides you with a heavy infrastructure, slow implementations, and limited ability to reduce exposure automatically. Varonis delivers agentless, cloud‑native DAM with automated remediation and real‑time threat detection across the entire data estate.
| CAPABILITY | VARONIS | Guardium |
| Deployment | Nothing to install, manage, or upgrade (deploy in weeks, not years) | ❌ Complex length implementation (measured in years) |
| Architecture | Out-of-the-box cloud application | ❌ Self-managed appliances |
| Overhead | 100% agentless | ❌ Agent focus + (native logs + new proxy) |
| Threat detection | Proactive detection MDDR | ❌ No SOC service - DIY |
| Automation | Automated risk prevention | ❌ No automations |
| Identity security | Identity protection | ❌ Very limited permissions |
Feature Comparison
Guardium is a legacy DAM. Varonis is modern data security platform.
Guardium relies on agents, proxies, and appliances to monitor database activity. Once deployed, you’re left with a heavy infrastructure, slow implementations, and limited ability to reduce exposure automatically. Varonis delivers agentless, cloud‑native DAM with automated remediation and real‑time threat detection across the entire data estate.
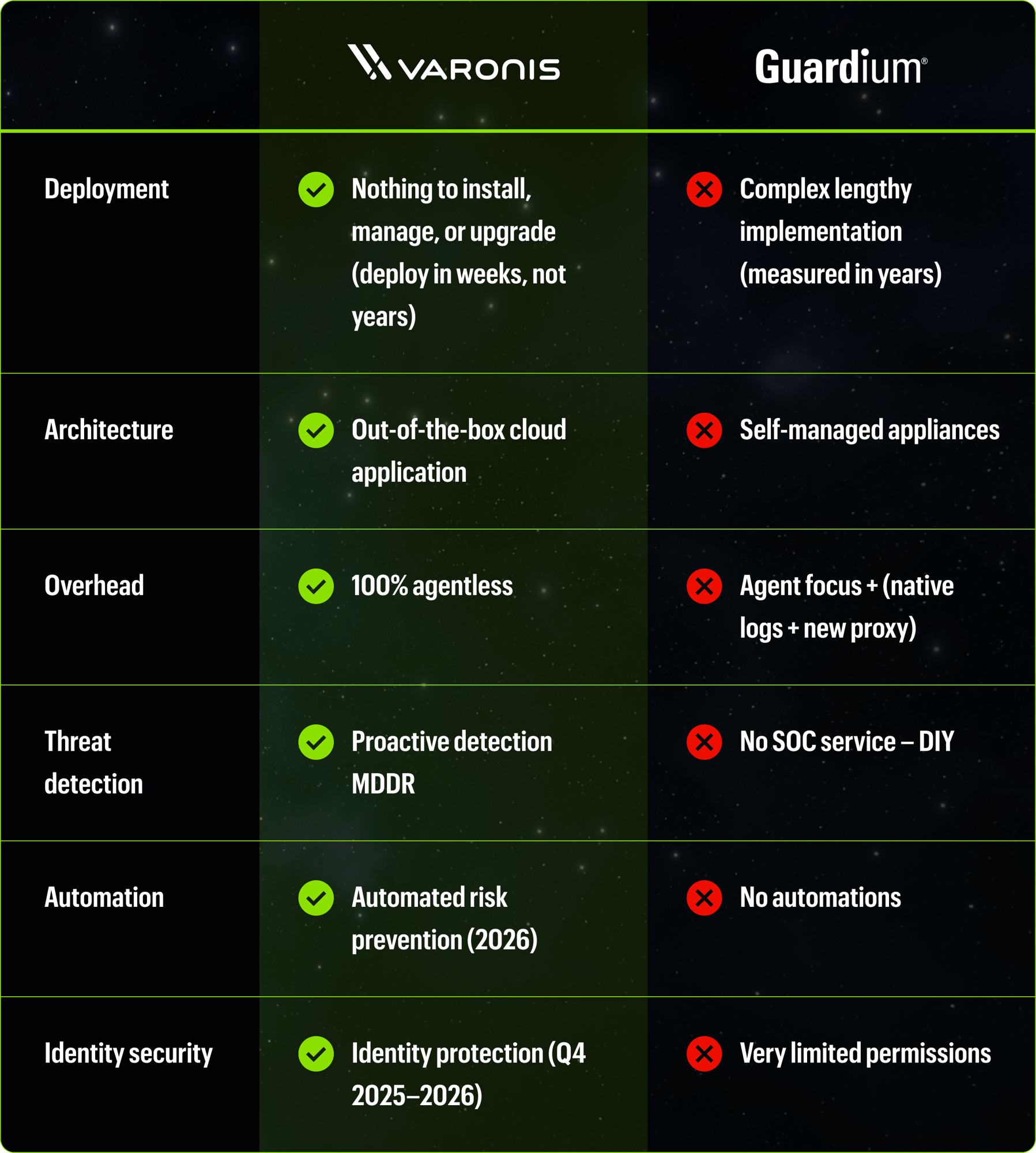
Guardium alerts, Varonis acts
Guardium can generate database activity alerts, but it doesn’t close the loop on exposure. Teams still have to manually investigate any suspicious activity and manually correlate database credentials to corporate identities.
Varonis automatically flags suspicious identities and revokes their access as well as proactively reduces blast radius by revoking stale permissions, right-sizing access, and continuously enforcing policies. Risk shrinks without waiting on tickets.
Why it matters: Reporting isn't security. Real security is providing you with outcomes.
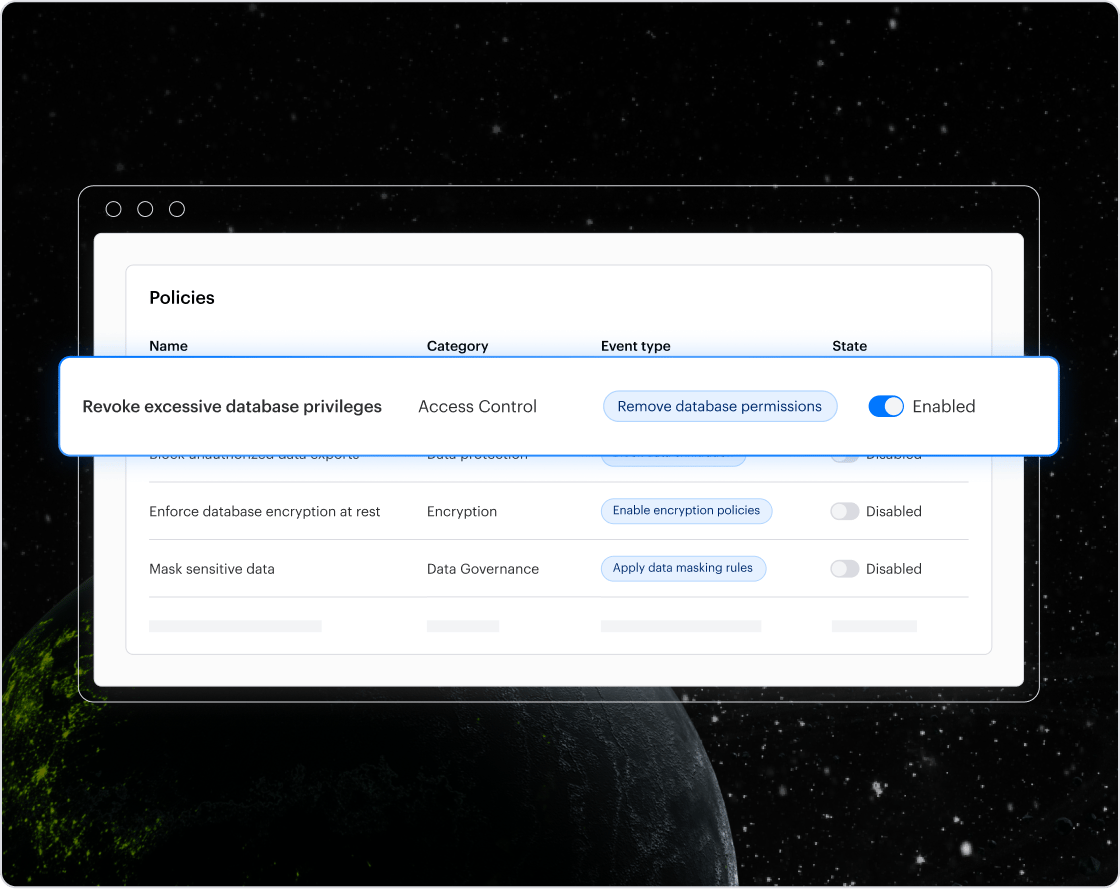
Guardium comes with a legacy architecture tax
Guardium’s model depends on self-managed infrastructure (appliances, agents, and proxies) which increases overhead and adds friction to deployment and operations. That complexity slows adoption and creates on-going maintenance burden.
Varonis is agentless with nothing to install, manage, or upgrade. You get coverage at scale without infrastructure sprawl or performance tradeoffs.
Why it matters: If the tool is hard to run, it won’t be run well and gaps will grow.
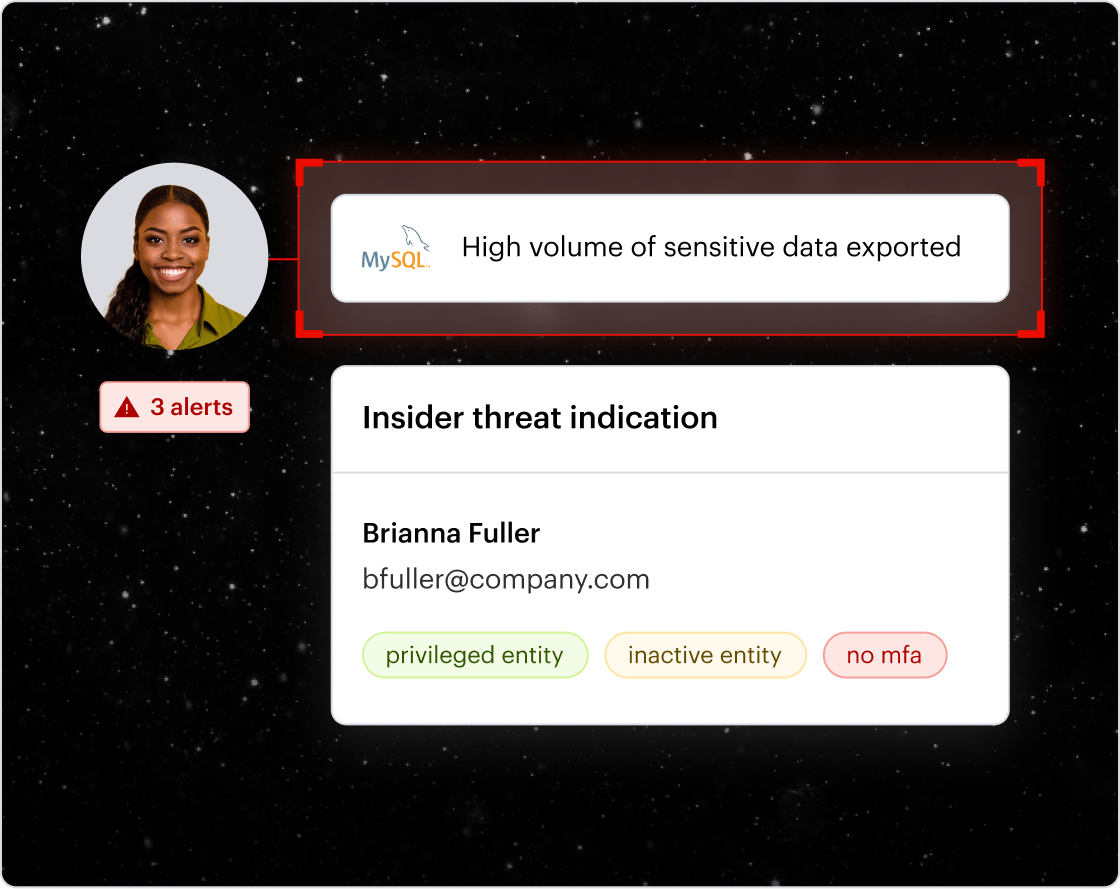
Guardium lacks unified, identity-aware threat detection
Guardium’s focus on database activity limits its ability to detect identity abuse patterns. Compromised accounts and insiders often blend in without behavioral correlation across systems.
Varonis correlates identity, permissions, and activity across databases, cloud, and SaaS to detect and respond to threats in real time, backed by 24x7x365 MDDR.
Why it matters: Breaches happen through abused access. If you can’t connect identity to data risk, you can’t stop the attack.
“Some of these platforms promise a lot of things. Varonis’ support has been completely on point — every implementation, the follow-ups afterwards — it’s not the situation where they just put it in place and then walk away. Varonis has had outstanding response times and support for our organization.”
Ruben Justiniano
Data Security Engineer, VACU
“Varonis' support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution. Varonis cemented itself on my list of must-have products.”
Al Faella
CTO, Prospect Capital
“We had real-time data showing: here’s the exact time this happened, here’s what the person was doing, here’s what they tried—and failed—to access. We can easily determine, with evidence, that there was no incident.”
Mike Taylor
CIO, USNS Mercy
Frequently Asked Questions
Guardium is a traditional DAM solution focused on database monitoring. Varonis is a modern data security platform that reduces exposure and stops threats across all data sources.
Guardium primarily generates alerts. Remediation is largely manual. Varonis continuously reduces risk by automatically enforcing least‑privilege access.
Varonis is cloud‑native and agentless, built for hybrid and SaaS‑heavy environments. Guardium is rooted in legacy DAM architecture that adds on operational overhead and slows time-to-value.
Choose Varonis if you need automated risk reduction, real‑time threat detection, and unified data security across your entire environment.
Choose Guardium if you only need traditional database activity monitoring and are prepared to run the legacy infrastructure that comes with it.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO

"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO