There's a phrase security professionals have repeated for years: "Attackers don't break in, they log in." A decade ago, it was a great way to keep phishing top of mind. Today, it reads less like a warning and more like a business model, one that's scaled into a shadow cybercrime economy.
Underground networks that once catered to hobbyists have matured into full-service cybercrime marketplaces, complete with reputation systems, escrow, and specialist vendors.
One operator runs infostealers across thousands of machines. Another extracts and sorts the credentials. A third sells curated access. A fourth deploys the ransomware. Each person focuses on what they do best, and the ecosystem has become ruthlessly efficient.
In this post, we'll break down the four commodities that power this access economy: remote credentials, infostealer logs, breach databases, and web shells.
Remote access credentials for sale
The most direct path into a network is through the front door. Enterprise remote access gives employees secure connectivity to internal resources, whether through VPN gateways like Fortinet, Cisco, and Palo Alto, or RDP servers that provide direct desktop access to internal machines. From an attacker's perspective, working credentials for either system are indistinguishable from a physical presence inside the network. Once you authenticate, you're in.
Initial access brokers turned this into a structured business. They harvest credentials through vulnerability exploitation, credential stuffing, or phishing, then list them with detailed metadata: target organization, geographic region, industry vertical, and product in use. Buyers shop for access the way procurement teams shop for software, filtering by sector and geography to match their objectives.
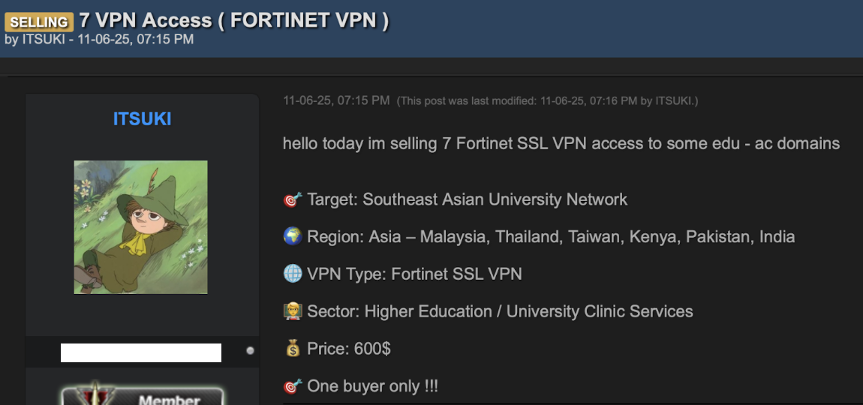
This sale offers seven Fortinet SSL VPN credentials for educational institutions across Southeast Asia, priced at $600 with exclusive access guaranteed to one buyer. Sellers specify sectors because different buyers have different targeting criteria, and the "one buyer only" guarantee ensures the access won't be burned before the purchaser can use it.
Pricing follows predictable patterns: $100 to $200 for small businesses, thousands for large enterprises or government agencies. Sellers build reputations over time, and buyers learn which vendors deliver working access consistently.
Infostealer logs at an industrial scale
VPN and RDP credentials represent just one slice of the market. Attackers who want a broader reach turn to infostealers. Malware families like Redline, Raccoon, Vidar, Lumma, and Risepro infect consumer and corporate machines, then systematically extract everything of value like saved passwords from browsers, session cookies, autofill data, cryptocurrency wallets, and authentication tokens. Each infected machine produces a "log" containing this harvested data.
These logs get aggregated into massive datasets and distributed through dedicated channels. Some operators run subscription services with daily fresh uploads. Others dump logs publicly to build their reputation before monetizing premium content. The distribution infrastructure mirrors legitimate SaaS businesses, with consistent branding and release schedules.
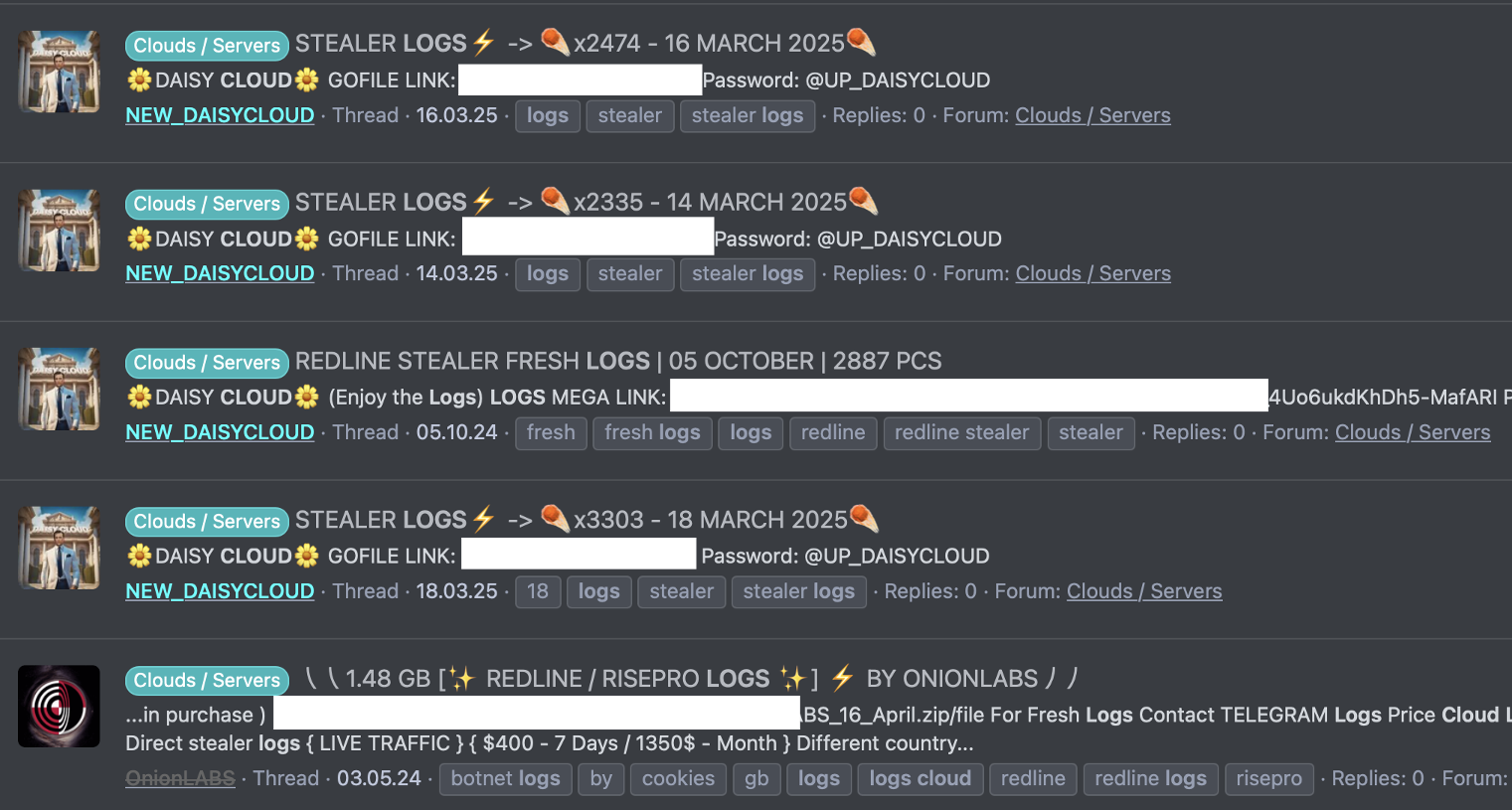
Operators like "DAISY CLOUD" distribute stealer logs with subscription pricing ($400 for 7 days, $1,350 per month). The logs are structured and searchable by domain, letting buyers extract credentials for specific targets without downloading entire datasets.
Session cookies are particularly valuable. When a user authenticates with MFA, the session token gets stored as a cookie. If an infostealer grabs that cookie while valid, an attacker can import it into their browser and inherit the authenticated session. No password needed, no MFA prompt triggered.
Database sales from past breaches
Infostealer logs capture credentials at the moment of infection. For credentials that leaked months or years ago, attackers turn to breach databases. Data breaches produce databases containing credentials, personal information, and organizational data that attackers can weaponize. The market for this data is mature, segmented, and surprisingly organized.
Sellers categorize offerings by geography, sector, data freshness, and field completeness. A database with full names, emails, phone numbers, and physical addresses commands higher prices than one with just email and password hashes.
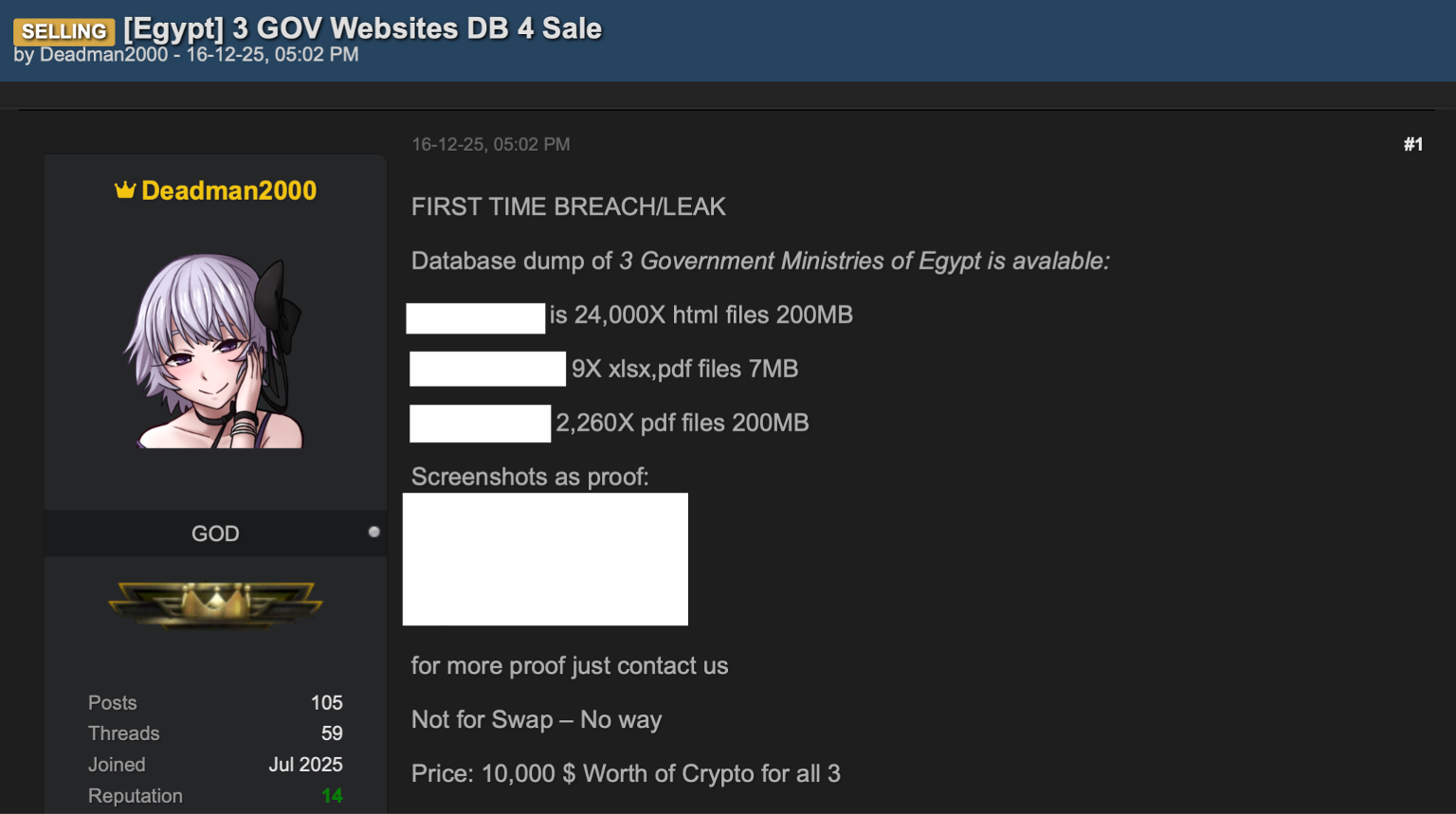
Here, a seller advertises database dumps from three Egyptian government ministries for $10,000 in cryptocurrency, including 24,000 HTML files and thousands of PDF documents. Government breaches command premium prices because they contain citizen data, internal communications, and documents useful for both fraud and espionage.
Buyers use these databases in layers. The first layer is direct credential reuse, because people recycle passwords across services. The second layer is reconnaissance, where employee names and email formats feed social engineering campaigns. The third layer is identity construction, where enough personal data lets attackers pass verification checks or reset passwords through support channels.
Web shells as persistent backdoors
VPN credentials, infostealer logs, and breach databases all provide access through legitimate authentication. Web shells bypass authentication entirely. They're planted backdoors on already-compromised servers that give buyers command execution capability without needing any credentials.
An attacker who exploits a vulnerable web application or unpatched file upload form gains initial access and installs a small script that accepts commands via HTTP. Once planted, this backdoor persists independently of whatever vulnerability enabled the original compromise. The hole can be patched, but the shell remains.
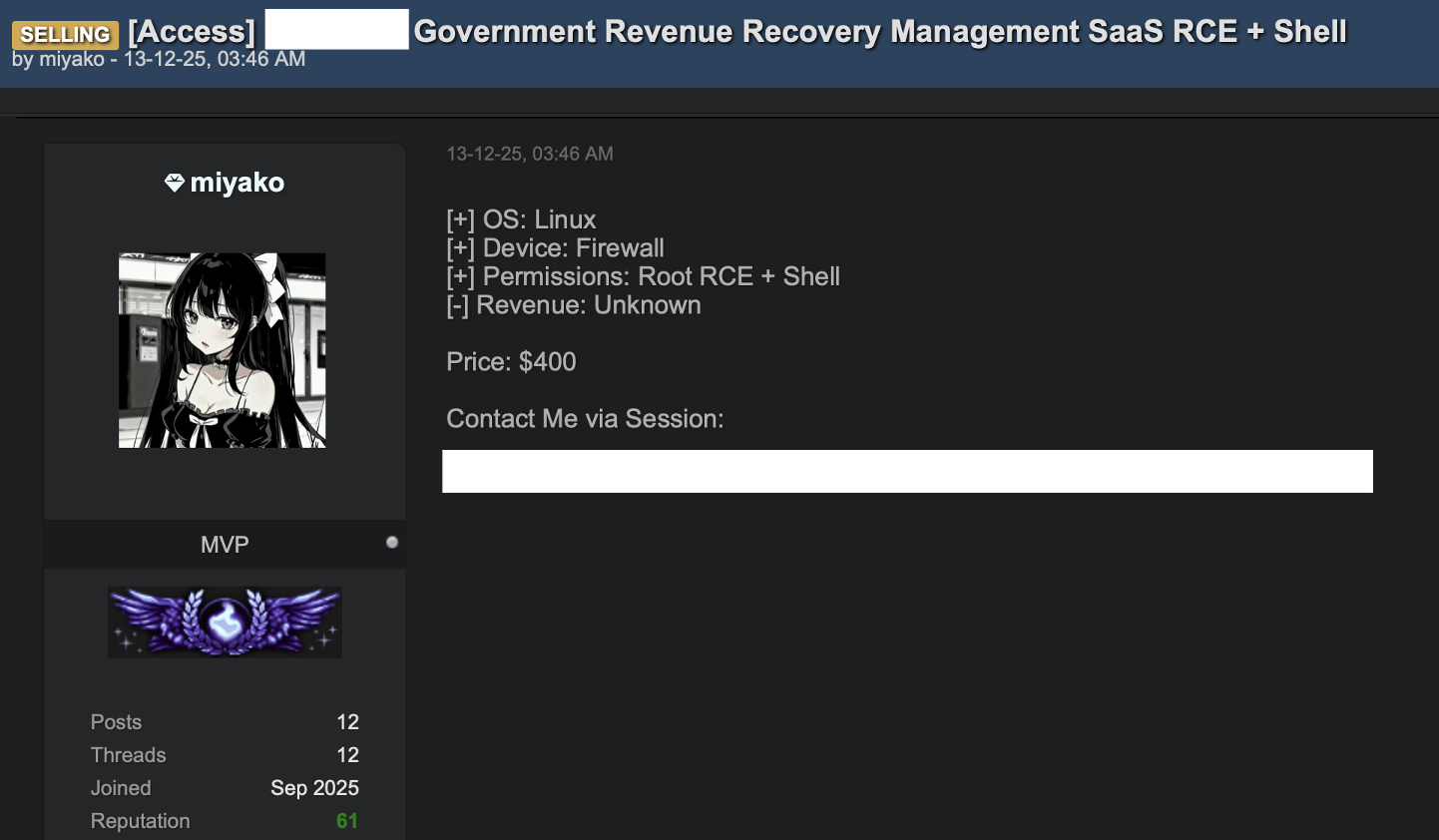
This vendor offers root RCE and shell access to a government revenue management system: Linux OS, firewall device, root-level permissions, priced at $400. A reputation score of 61 over four months signals an established seller. Government systems attract buyers for espionage, as pathways into private-sector networks, or for fraud when they handle financial data.
Seller reputation matters in these transactions. Forums track post counts, thread history, and reputation scores accumulated over months of activity. Buyers assess whether a vendor delivers working access consistently or has a history of burning customers with invalid or already-sold footholds.
How commoditization built this market
Ten years ago, pulling off a network intrusion meant handling every step: find the vulnerability, write the exploit, compromise the target, figure out how to cash out. Most attackers couldn't do all of that well, which limited how many operations any single operator could run.
That changed when underground networks started functioning like actual marketplaces. Reputation systems let strangers assess each other. Escrow services meant buyers didn't have to trust sellers with upfront payment. Someone great at running infostealers but clueless about ransomware could sell their logs to someone who wasn't. The attack chain broke into pieces, and each piece became its own specialty.
Today, everything is standardized. Access listings follow predictable formats. Stealer logs use consistent structures. Database dumps come with field definitions. A buyer in Eastern Europe can purchase credentials from a seller in Southeast Asia without negotiating what "VPN access" means.
The barrier to entry for any single role dropped dramatically, while the ecosystem's combined capability grew. Cybercrime has industrialized, and access is now just another product on the shelf.
If you're interested in learning more about how these access markets operate and evolve, Varonis Threat Labs will be publishing ongoing research throughout 2026.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







