Most organizations' employees receive countless communications daily—emails, Slack messages, or ticket updates, for example. Phishing scams are hidden among these routine interactions designed to exploit trust and compromise security.
Imagine an employee receiving a text that appears to be from their bank: “Suspicious activity detected on your account. Click here to secure your account.” Or a message that mimics an IT ticket update: “Your password will expire soon. Click here to reset it.” At a glance, these messages seem legitimate, don’t they?
This is how many phishing campaigns begin, often powered by platforms like Devil-Traff. These bulk SMS services use features like sender ID spoofing and automated messaging to impersonate trusted sources, enabling attackers to deliver thousands of fake messages in minutes. One careless click or an incorrectly entered credential can expose an entire organization.
This article will explore how platforms like Devil-Traff enable phishing attacks, why they’re so effective against employees, and how Varonis can help organizations detect and stop these evolving threats.
Taking a closer look at Devil-Traff
Devil-Traff is a platform offering bulk SMS services designed for high-volume messaging. Its features—such as sender ID customization, API integration, and "black content" support—make it an ideal resource for cybercriminals.
By enabling mass phishing campaigns and other malicious operations at a low cost, Devil-Traff exemplifies the role of bulk SMS platforms in modern cybercrime.
The official sales thread for the Devil-Traff SMS platform.
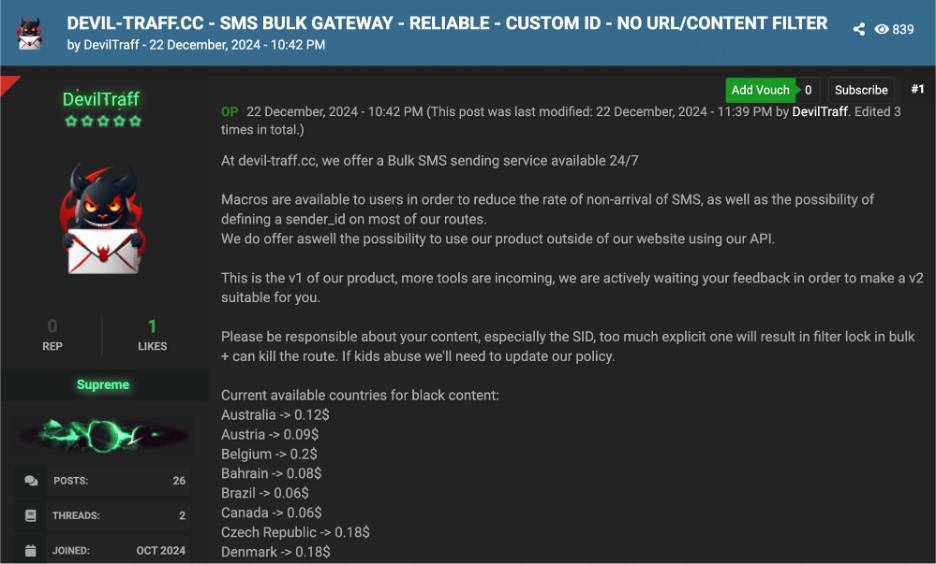
The official sales thread for the Devil-Traff SMS platform.
Cybercriminals use Devil-Traff to conduct large-scale phishing and spam campaigns. One of the most abused capabilities is sender ID customization, which allows attackers to impersonate trusted organizations like banks or government agencies.
For example, an attacker might send messages appearing to come from “PayPal Support,” claiming suspicious activity and prompting the recipient to click a fraudulent link.
Another common tactic involves one-time-password (OTP) interception attacks, where attackers impersonate service providers to trick victims into revealing one-time passwords sent via SMS. With access to these OTPs, attackers can bypass two-factor authentication (2FA) and take over accounts.
Part of the user dashboard for the Devil-Traff SMS platform
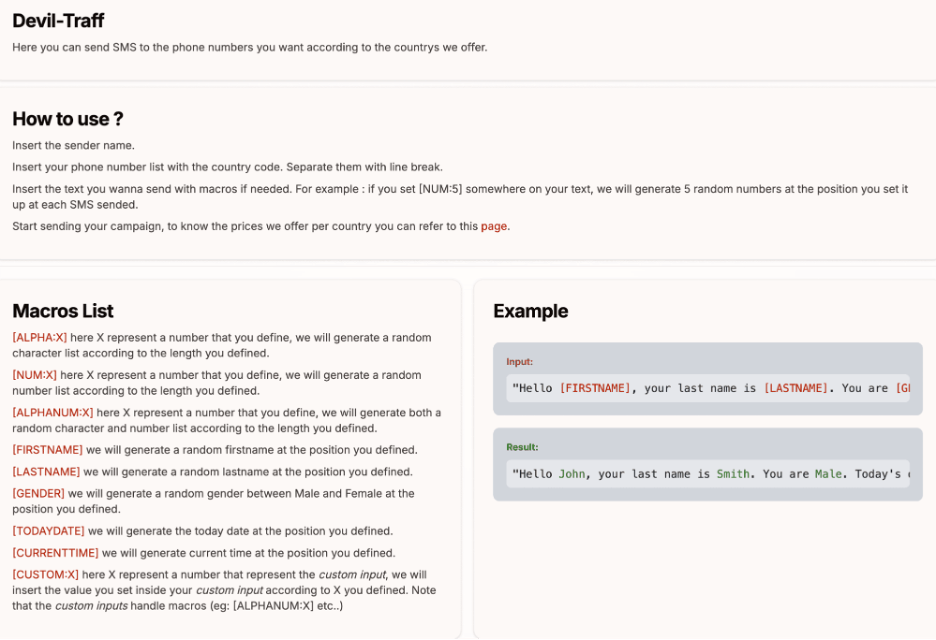
Part of the user dashboard for the Devil-Traff SMS platform
The API integration offered by Devil-Traff allows for automated campaigns, enabling thousands of SMS messages to be sent with minimal manual effort. Attackers use this to launch phishing campaigns across multiple countries, leveraging macros to optimize delivery rates and avoid spam filters.
The usage of SMS platforms in cybercrime
Platforms like Devil-Traff are becoming quite popular on cybercrime forums. Discussions about bulk SMS services now dominate these spaces, with users sharing reviews, delivery optimization techniques, and recommendations for the most effective routes.
Some forums also serve as marketplaces for phone number databases, allowing attackers to purchase highly targeted lists for their campaigns.
Just a fraction of cybercrime discussions in relation to SMS abuse
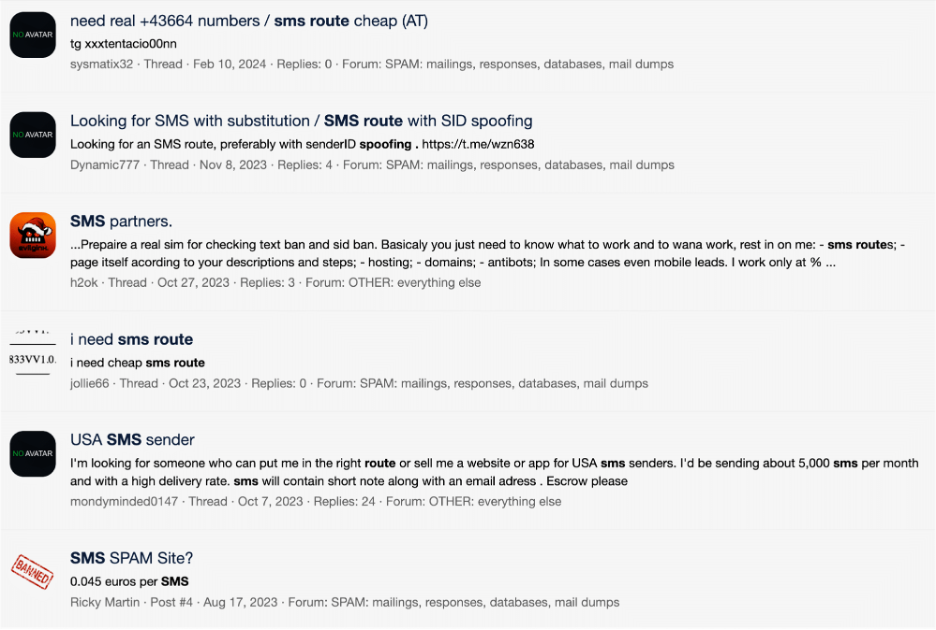
Just a fraction of cybercrime discussions in relation to SMS abuse
For example, a user might recommend a specific route for bypassing filters in France or share tips on using macros to improve delivery rates. Unfortunately, this accessibility and support have helped bulk SMS platforms become integral to the cybercrime ecosystem.
Key features of Devil-Traff
Devil-Traff offers several features that make it appealing to cybercriminals:
- Sender ID Customization: Spoof trusted organizations, making phishing messages appear legitimate.
- API Integration: Automate campaigns and send thousands of SMS messages with minimal effort.
- Macros for Optimization: Increase delivery rates and bypass telecom spam filters.
- Affordable Pricing: Rates start at $0.02 per SMS, with a $10 minimum deposit.
The platform enables attackers to reach victims worldwide with global routes spanning countries like Turkey, Brazil, France, and Australia. Private routes are also available for exclusive campaigns, such as those using Binance sender IDs, further increasing the effectiveness of targeted attacks.
Get protection with Varonis
Varonis delivers a robust security platform to protect users from phishing attacks. With real-time threat detection and prevention, our platform defends against a wide range of phishing threats.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)