-
 Security Bulletins
Security BulletinsMar 29, 2020
Varonis Brings Data Security to Nasuni Cloud NAS
We’re excited to announce that, in an upcoming release, the Varonis Data Security Platform will bring data-centric audit and protection to Nasuni Enterprise File Services. Nasuni is a key Varonis...

Rob Sobers
1 min read
-
 Security Bulletins
Security BulletinsMar 29, 2020
Varonis Version 7 Highlights
Varonis Version 7 is now generally available – check out our latest 7.4 release and see some of the highlights of what’s new. 25 new widgets to manage and protect...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsMar 29, 2020
64% of Americans Don’t Know What to Do After a Data Breach — Do You? (Survey)
We surveyed Americans to gauge their data breach literacy including awareness and how to respond — see how you data breach literacy stacks up.

Rob Sobers
5 min read
-
 Data Security Security Bulletins Threat Research
Data Security Security Bulletins Threat ResearchMar 19, 2020
COVID-19 Threat Update #1
Varonis sees the highest number of VPN and O365 events ever recorded across customer base. Click to watch our security experts discuss what they’re seeing on the front lines, and what...

Kilian Englert
1 min read
-
 Security Bulletins Threat Research
Security Bulletins Threat ResearchJan 27, 2020
Varonis Uncovers Another New Strain of the Qbot Banking Malware
Varonis has discovered and reverse engineered another new strain of Qbot, a sophisticated, well-known type of malware that collects sensitive data, such as browser cookies, digital certificate information, keystrokes, credentials, and session data from its victims to commit financial fraud.

Dolev Taler
2 min read
-
 Data Security PowerShell Security Bulletins
Data Security PowerShell Security BulletinsOct 17, 2019
What is Endpoint Security? A Complete Guide
Endpoint security is a growing concern for enterprises in every industry, given the value of digital assets and data, and must be a cybersecurity priority.

Michael Buckbee
7 min read
-
 Data Security Security Bulletins
Data Security Security BulletinsOct 02, 2019
What is a Security Operations Center (SOC)?
Learn how a security operations center (SOC) functions in an enterprise, SOC models, job roles, best practices and the value it brings to an organization

Michael Buckbee
7 min read
-
 Security Bulletins
Security BulletinsMay 05, 2017
Introducing the Automation Engine, DatAlert Analytics Rewind, and more
Getting to least privilege can be a nightmare. The first steps – tracking down inconsistent ACLs and remediating global access groups can turn even the most basic file share clean-up...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsApr 26, 2017
Varonis + Splunk: Epic Threat Detection and Investigations
We’re bringing our powerful DatAlert functionality to Splunk® Enterprise to give you comprehensive visibility into data security with our new Varonis App fo

Michael Buckbee
1 min read
-
 Security Bulletins
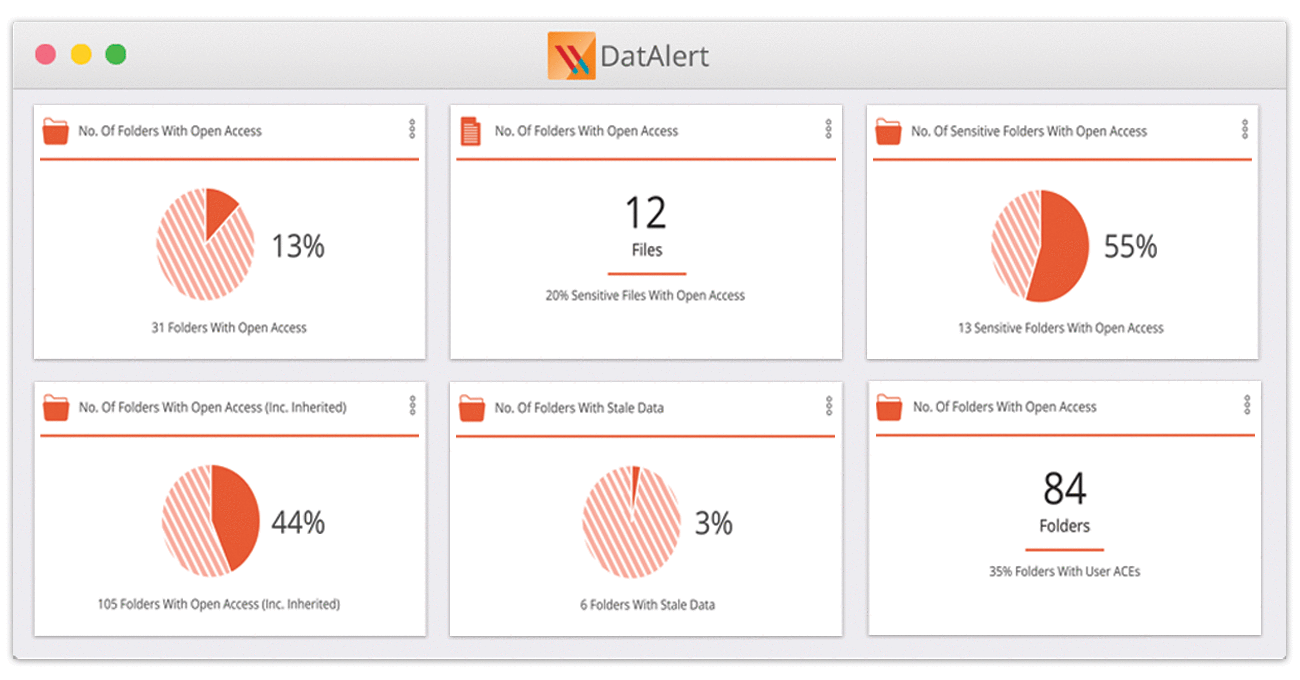
Security BulletinsFeb 13, 2017
Introducing a new security dashboard, enhanced behavioral analysis, and more
Every day we hear new stories about how our customers are using DatAlert to stop cyberattacks: detecting and disabling ransomware infections, discovering misconfigurations and vulnerabilities, and setting up automatic responses...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsFeb 24, 2016
DatAlert Analytics and the Varonis Behavior Research Laboratory
Last November, we introduced Varonis UBA threat models to automatically analyze behavior and detect insider threats throughout the lifecycle of a breach. Our UBA threat models, which are major enhancements...

Michael Buckbee
1 min read
-
 Security Bulletins
Security BulletinsAug 21, 2013
New PII Discovered: License Plate Pictures
After finishing up some research on personally identifiable information I thought, mistakenly, that I was familiar with the most exotic forms of PII uncovered in recent years, including zip code-birth...

Michael Buckbee
1 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital