Varonis Version 7 is now generally available – check out our latest 7.4 release and see some of the highlights of what’s new.
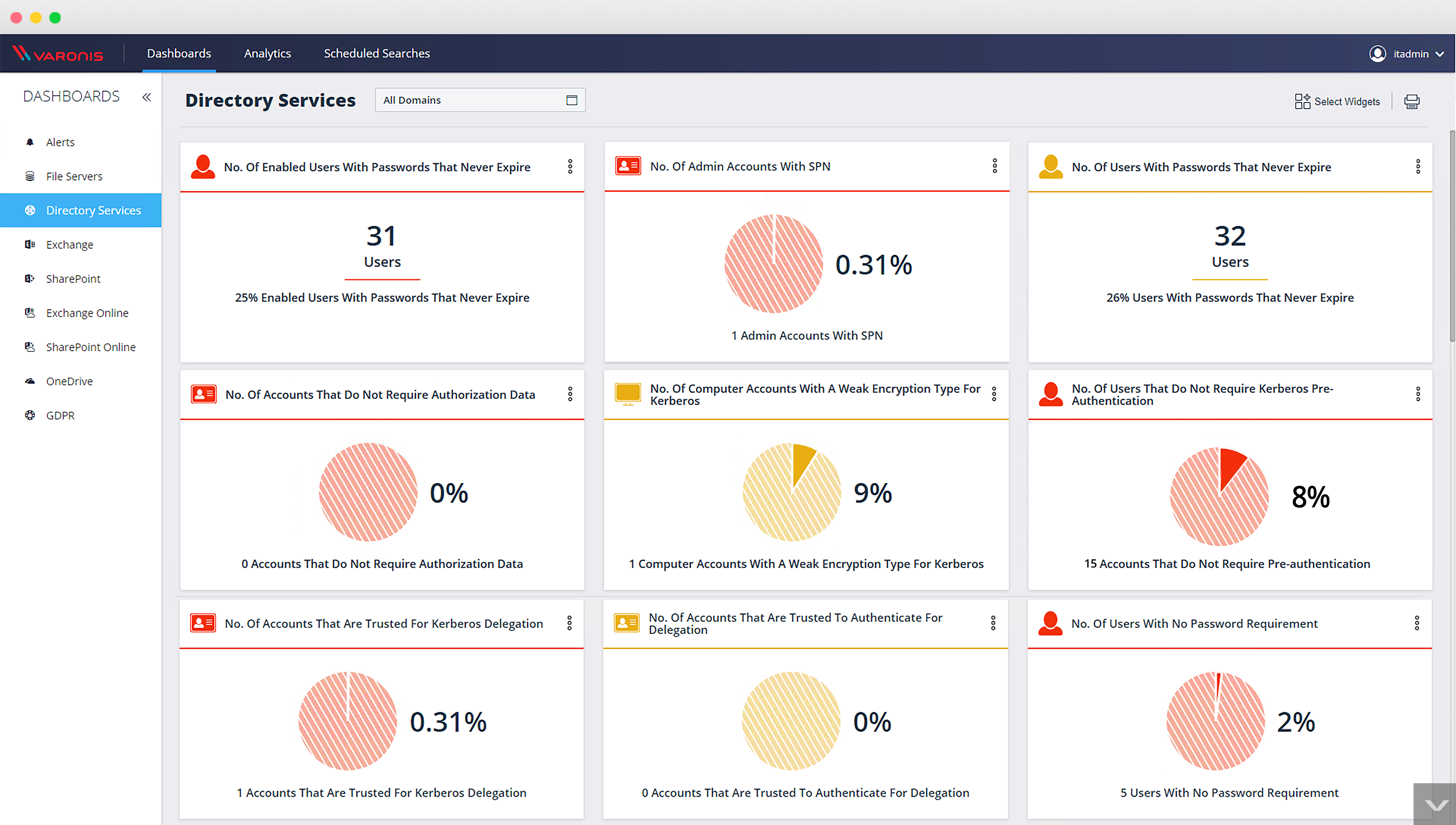
Find and fix vulnerabilities with a new Active Directory dashboard
25 new widgets to manage and protect your active directory environment at a glance. From vulnerable Kerberos passwords to domain indicators, this dashboard is designed to help prevent attacks on Active Directory like Kerberoasting and golden ticket attacks.
Detect email attacks like never before
We’ve added new threat models to detect even more threats: customers can detect spearphishing attacks by monitoring proxy activity; detect malicious attachments in email; and more.
Get the benefits of the cloud without sacrificing security
Office 365 dashboards, Box security events, more threat models designed to protect Exchange Online, and saved searches – so you can enjoy the convenience of storing data in the cloud without sacrificing security.
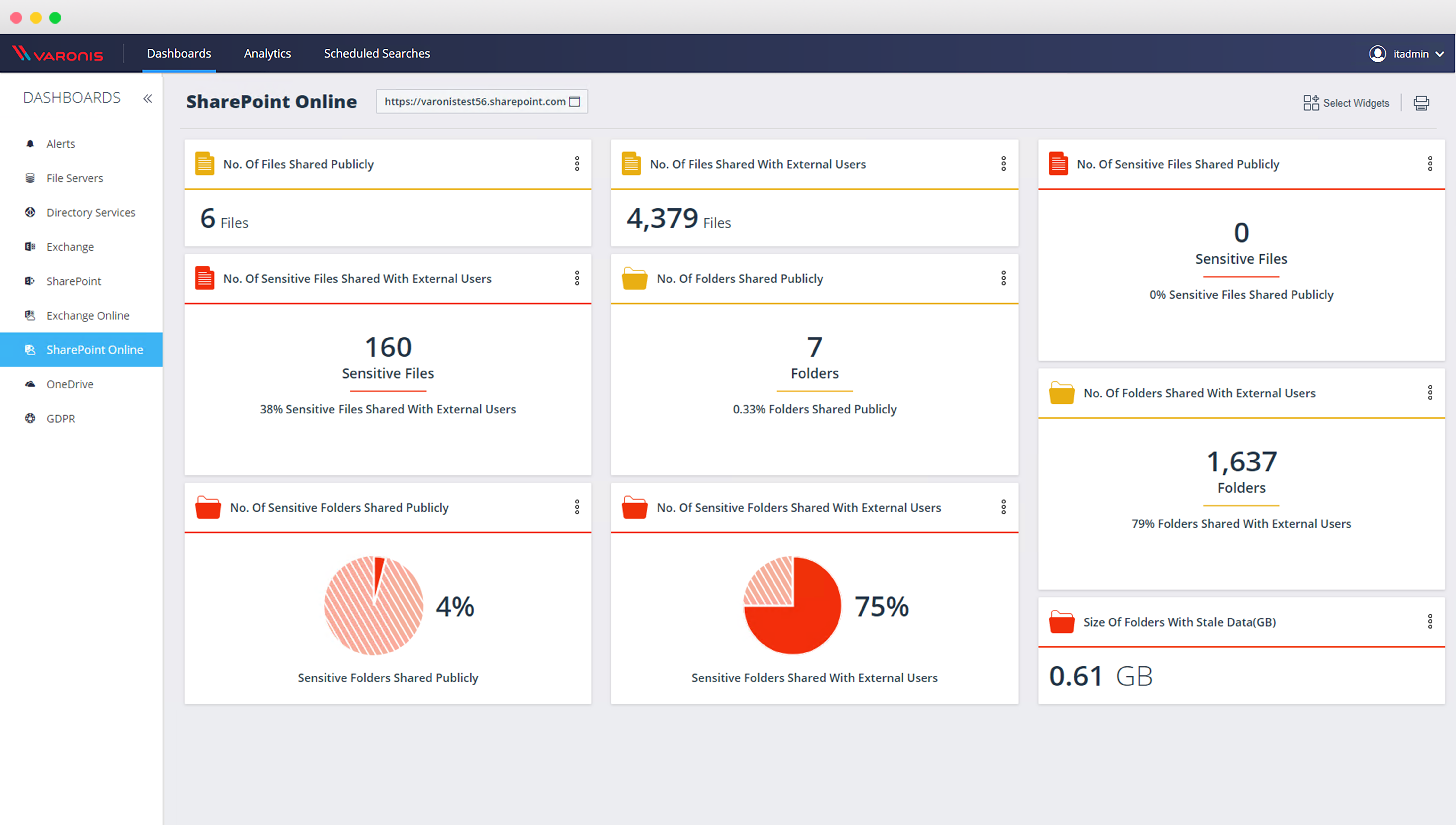
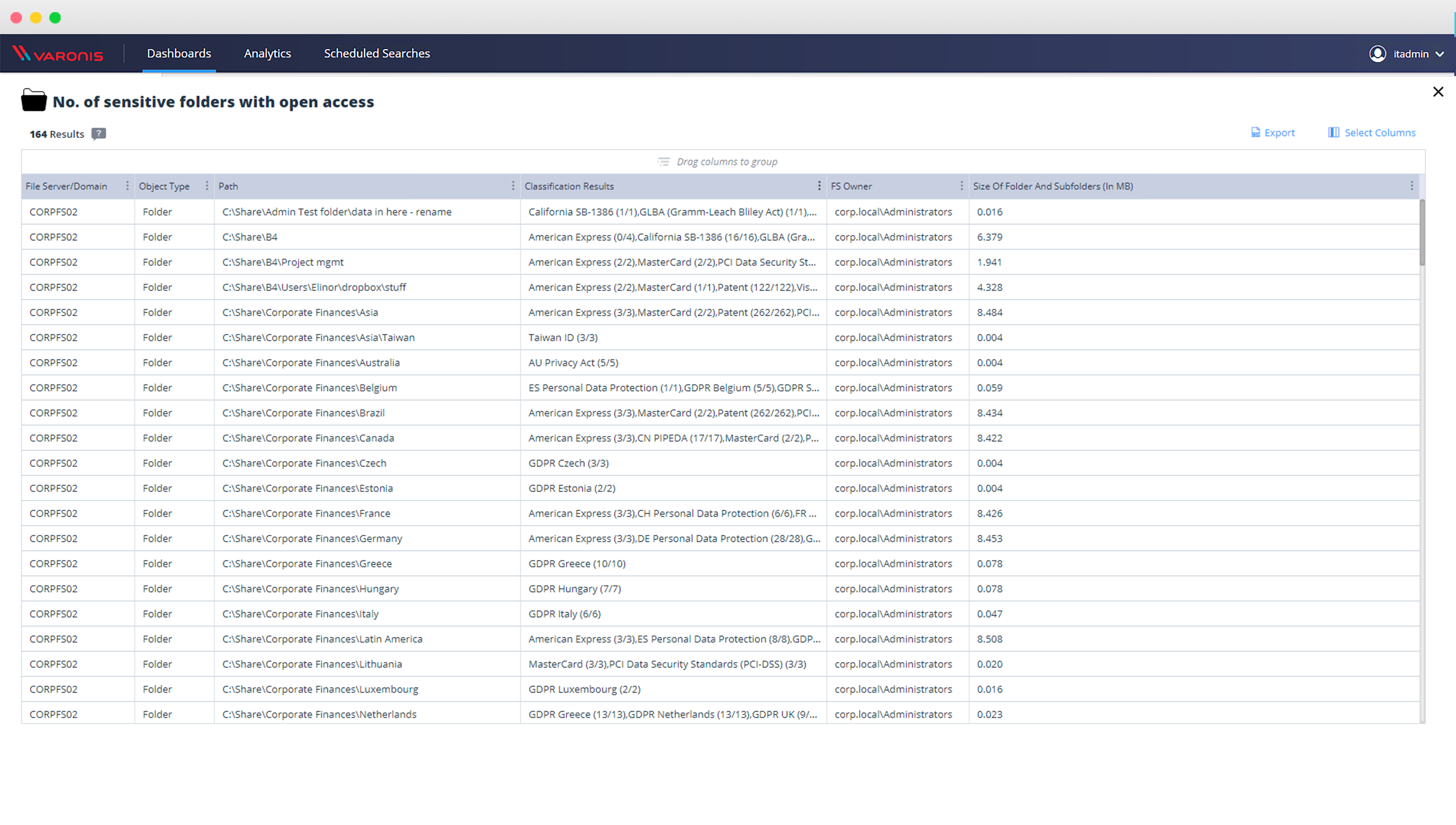
Drill down into sensitive data directly from the dashboard
You asked, we listened: you can now drill down and review sensitive data directly from the dashboard – see what data is overexposed in the click of a button.
Incident response playbooks from the pros
Our security research lab has developed incident response playbooks for cyberattacks and we added them right in the UI – so that you know how to respond, who needs to be notified, and how to improve your security posture for future attacks.
Combine threat intelligence with perimeter telemetry
Track suspicious activity from the core to the edge. Varonis Edge puts perimeter telemetry in context and simplifies security investigations – bringing in threat detection, geolocation, and more to give you the full picture of what’s happening on your data.
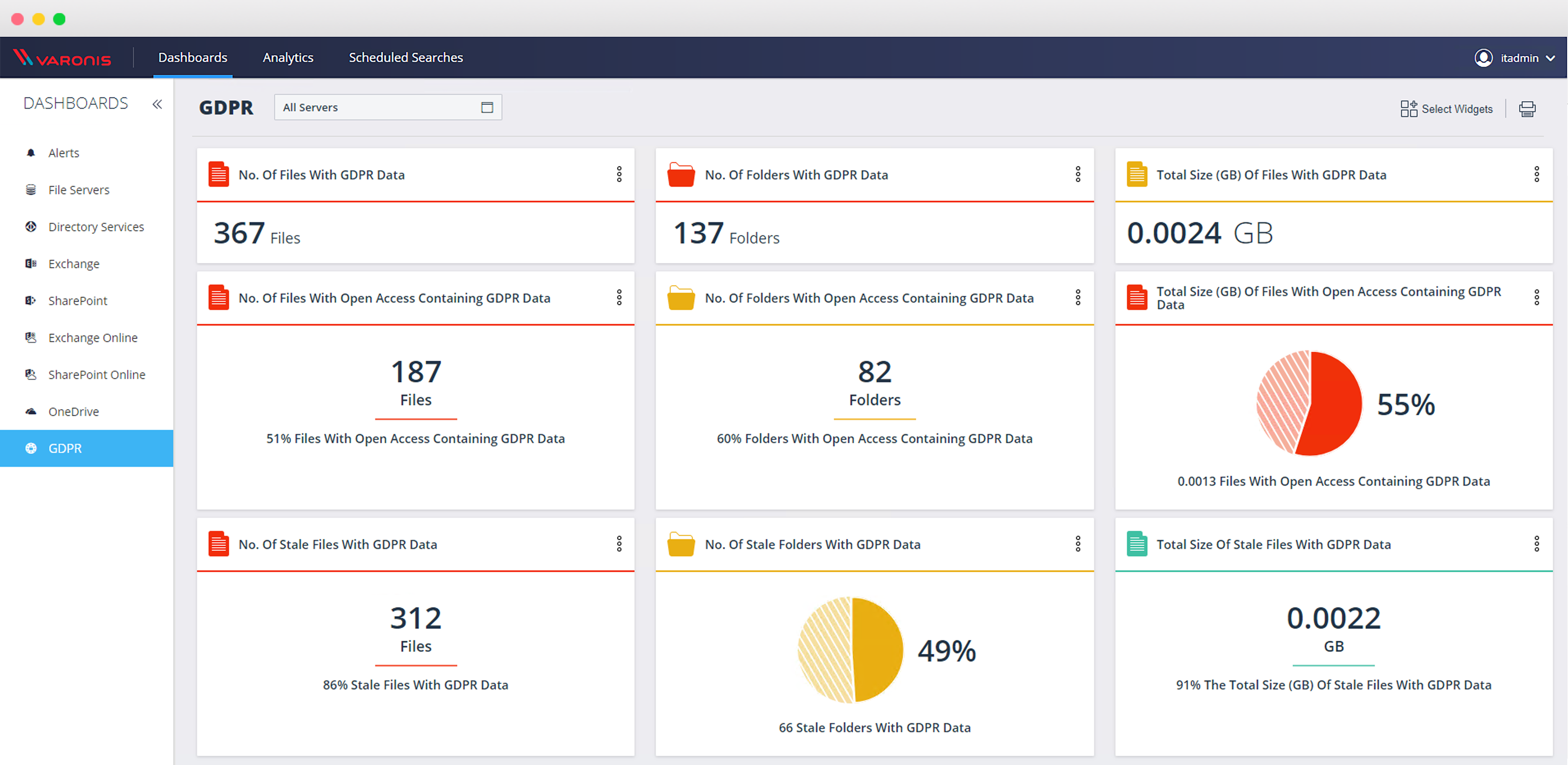
GDPR-ready
Version 7 makes it easier than ever to see where your GDPR data is overexposed with a GDPR dashboard, out-of-the-box GDPR reports, and threat models focused on protecting GDPR data.
Scale and Speed with Solr
We’re leveraging Solr to get you responsive, fast results – even while handing billions of events at scale. You’ll see significant performance improvements, run lightning-fast investigations, and get immediate access to search results.
Broader support for platforms, proxies, and more
- Support for NetApp ONTAP 9.5 cloud
- New proxy source: Cisco
- TLS 1.2 support
Customers can download Varonis 7.4 GA release via our support portal – and don’t forget to check out the product documentation (including an upgrade guide) in our customer community.
Want to learn more about what’s new in Version 7? Check out our on-demand webinar, or request a custom product tour with one of our security engineers.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.

