
Michael Buckbee
Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.
-
 Data Security PowerShell
Data Security PowerShellJun 19, 2020
How to use PowerShell Objects and Data Piping
This article is a text version of a lesson from our PowerShell and Active Directory Essentials video course (use code ‘blog’ for free access). The course has proven to be...

Michael Buckbee
5 min read
-
 Privacy & Compliance
Privacy & ComplianceJun 19, 2020
GDPR Data Breach Guidelines
Index Personal Data Breach vs. Reportable Breach Notifying the Regulators Breach Notification and Ransomware Individual Reporting Breach Notification in Phases Notification Details This Is Not Legal Advice The General Data...

Michael Buckbee
8 min read
-
 Privacy & Compliance
Privacy & ComplianceJun 19, 2020
A Few Thoughts on Data Security Standards
Did you know that the 462-page NIST 800-53 data security standard has 206 controls with over 400 sub-controls1? By the way, you can gaze upon the convenient XML-formatted version here....

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 19, 2020
More NSA Goodness: Shadow Brokers Release UNITEDRAKE
Looking for some good data security news after the devastating Equifax breach? You won’t find it in this post, although this proposed federal breach notification law could count as a...

Michael Buckbee
2 min read
-
 Privacy & Compliance
Privacy & ComplianceJun 19, 2020
Do Your GDPR Homework and Lower Your Chance of Fines
Advice that was helpful during your school days is also relevant when it comes to complying with the General Data Protection Regulation (GDPR): do your homework because it counts for...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 19, 2020
DNSMessenger: 2017's Most Beloved Remote Access Trojan (RAT)
I’ve written a lot about Remote Access Trojans (RATs) over the last few years. So I didn’t think there was that much innovation in this classic hacker software utility. RATs, of...

Michael Buckbee
2 min read
-
 Data Security
Data SecurityJun 17, 2020
How to Protect GDPR Data with Varonis
In the overall data security paradigm, GDPR data isn’t necessarily more important than other sensitive data, but demands specific monitoring, policy, and processing – with significant fines to encourage compliance....

Michael Buckbee
3 min read
-
 Data Security
Data SecurityJun 17, 2020
Adventures in Fileless Malware, Part II: Sneaky VBA Scripts
I’m a fan of the Hybrid Analysis site. It’s kind of a malware zoo where you can safely observe dangerous specimens captured in the wild without getting mauled. The HA...

Michael Buckbee
5 min read
-
 Data Security Privacy & Compliance
Data Security Privacy & ComplianceJun 17, 2020
Wyden’s Consumer Data Protection Act: Preview of US Privacy Law
The General Data Protection Regulation (GDPR) has, for good reason, received enormous coverage in the business and tech press in 2018. But wait, there’s another seismic privacy shift occurring, and...

Michael Buckbee
4 min read
-
 Data Security
Data SecurityJun 17, 2020
MITRE ATT&CK Framework: Everything You Need to Know
The MITRE ATT&CK matrices are an invaluable resource for cybersecurity pros. Read on to learn more about ATT&CK tactics and techniques.

Michael Buckbee
6 min read
-
 Data Security
Data SecurityJun 17, 2020
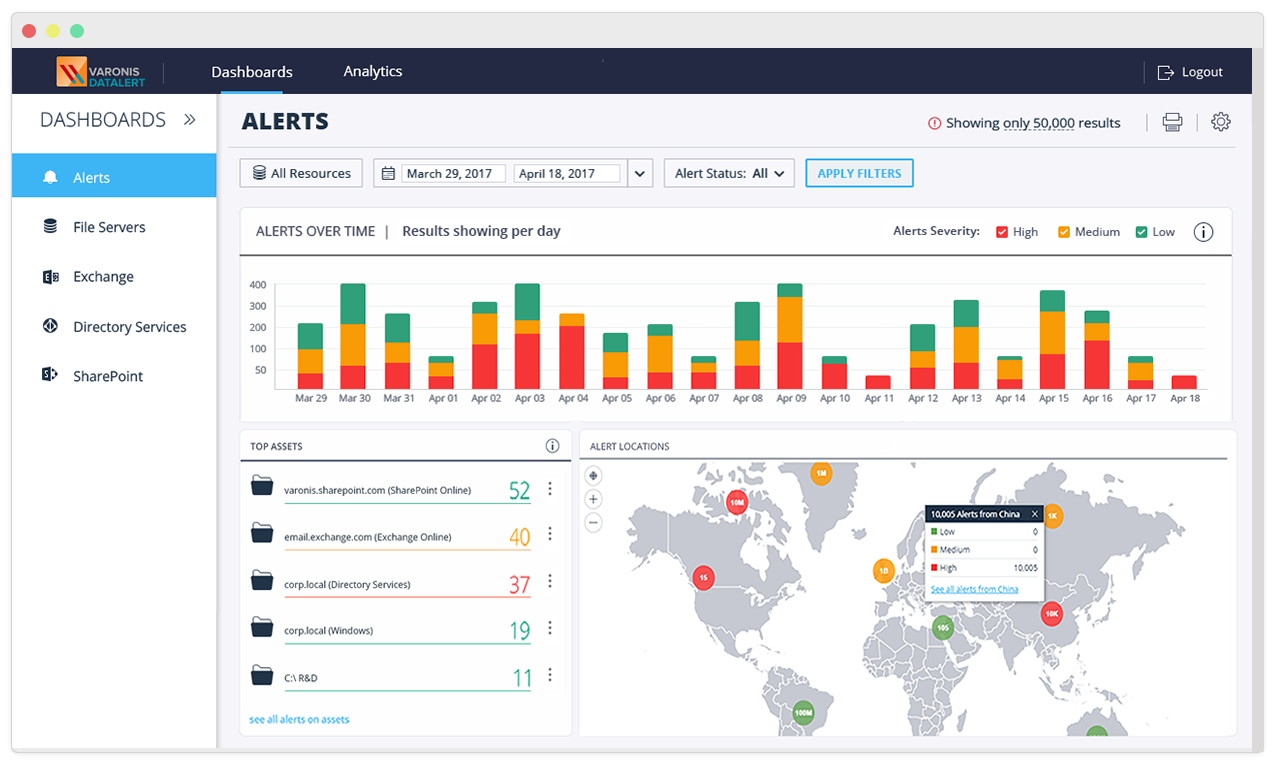
Introducing Varonis Data Security Platform 6.4.100: Varonis Edge, GDPR Threat Models, Geolocation and More
It’s the beginning of a new year, and we have a huge new beta release to share with you. The beta release of the Varonis Data Security Platform 6.4.100 dropped...

Michael Buckbee
1 min read
-
 Data Security
Data SecurityJun 17, 2020
How To Prevent Ransomware: The Basics
Ransomware is a destructive type of malware that has taken down city governments and cost organization millions. Learn more about how to prevent ransomware

Michael Buckbee
12 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital