Looking for some good data security news after the devastating Equifax breach? You won’t find it in this post, although this proposed federal breach notification law could count as a teeny ray of light. Anyway, you may recall the Shadow Brokers, which is the group that hacked the NSA servers, and published a vulnerability in Windows that made WannaCry ransomware so deadly.
Those very same Shadow Brokers have a new product announcement that also appears to be based on NSA spyware first identified in the Snowden documents. Bruce Schneier has more details on its origins.
Want to learn ransomware basics and earn a CPE credit? Try our free course.
(Way back in 2014, Cindy and I listened to Schneier speak at a cryptography conference, warning the attendees that NSA techniques would eventually reach ordinary hackers. Once again, Schneier proved depressingly right.)
Known as United Rake or UNITEDRAKE in hacker fontology, this is an advanced remote access trojan or RAT along with accompanying “implants” – NSA-speak for remote modules. It makes some of the admittedly simple RATs I investigated in my pen testing series look like the digital-version of Stone-Age tools.
The UNITEDRAKE Manual
How do we know how UNITEDRAKE works?
The Shadow Brokers kindly published a user’s manual. I highly recommend that IT folks who only know about malware by scanning the headlines of tech-zines peruse the contents of this document.
Forgetting for a moment that Evil Inc. is behind the malware, the 67-page manual appears on the surface to be describing a legit IT tool: there are sections on minimum software requirements, installation, deployment, and usage (lots of screenshots here).

To my eyes, this is a detailed user’s manual that puts many business-class software collateral to shame. It’s the productized malware that we often hear about, and now we can all see for our itself. UNITEDRAKE will likely be sold on the dark web, and the manual is the teaser to get hackers interested.
I didn’t see all the capabilities explained that were implied in the screen shots, but there’s enough in the manual to convince the likely buyer that UNITEDRAKE is the real-deal and worth the investment
But It’s Still a Trojan
Once you read through the UNITEDRAKE manual, you see it’s essentially a RAT with a classic modern architecture: the client-side with the implants is on the victim’s computer, and it communicates to the hacker’s server on the other side of the connection.
Port 80 seems to be the communications channel, and that means HTTP is the workhorse protocol here —although raw TCP is mentioned as well.
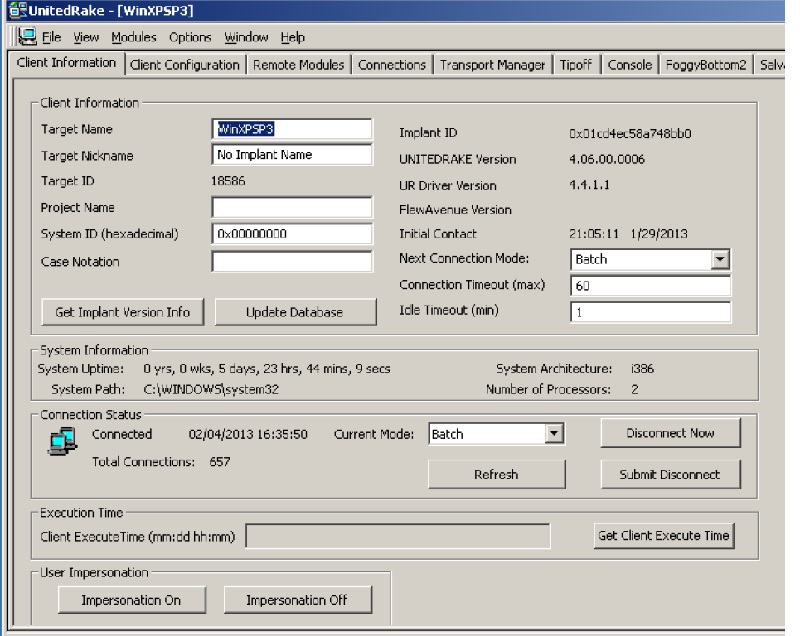
Scanning a few specialized websites, I learned that NSA implants such as Salvage Rabbit can copy data off a flash drive, Gumfish can take pictures from an embedded camera, and Captivated Audience can — what else — spy on users through a laptop’s microphone. You can read more about this spy-craft in this Intercept article.
The NSA guys at least get credit for creative product naming.
The Prognosis
Obviously, the NSA was in a better position to install these implants than typical hackers. And it’s unclear how much of the NSA-ware the Shadow Brokers were able to implement.
In any case, with phishing and other techniques (SQL-injection, and say probing for known but unpatched vulnerabilities), hackers have had a good track record in the last few years in getting past the perimeter undetected.
Schneier also says that Kapersky has seen some of these implants in the wild.
My takeaway: We should be more than a little afraid of UNITEDRAKE, and other proven productized malware than hackers with some pocket change can easily get their hands on.
We never believed the perimeter was impenetrable! Learn how Varonis can spot attackers once they’re inside.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









