In today's data-driven world, proper data governance is critical to ensure compliance with privacy regulations, avoid penalties, and protect your organization's reputation.
But sensitive data often ends up where it shouldn’t or stays beyond its required retention period, posing privacy and security risks. Creating and enforcing the policies and procedures for data governance can be a daunting task when faced with petabytes worth of data flowing through your various systems.
In addition to ensuring compliance with strict privacy regulations, organizations face other data governance and lifecycle challenges, such as identifying and purging obsolete data that increases storage costs and risks. Moreover, preparing for large-scale migrations to the cloud presents significant difficulties, particularly when attempting to separate the files you need from those you don’t.
Introducing Varonis Data Lifecycle Automation
To address these challenges, we’re pleased to introduce Varonis Data Lifecycle Automation, the industry's first fully automated data lifecycle solution. With Varonis Data Lifecycle Automation, you can securely manage data from creation to deletion by automatically enforcing data governance and lifecycle policies without writing any code.
This release expands the automated outcomes that customers can achieve with Varonis, building on existing features such as automated classification and labeling, permission remediation, exposure reduction, configuration fixes, and data masking.
With Varonis Data Lifecycle Automation, organizations can automatically and effortlessly:
- Enforce data lifecycle, residency, and retention policies
- Quarantine exposed, misplaced, and stale sensitive data to reduce the blast radius
- Ensure that sensitive data is not used for AI training or disclosed in responses
- Prepare for large-scale data migrations
- Reduce storage costs by cleaning up stale data.
In this blog, we’ll dive deeper into the outcomes it can help you achieve and discuss how Varonis Data Lifecycle Automation works.
Automated data governance outcomes
Automatic policy enforcement
Varonis allows you to create and automatically enforce unique lifecycle, retention, and residency requirements tailored to different departments, servers, data types, and sensitivity levels. It continuously monitors your environment to identify instances where data governance practices violate company policies, such as retaining personally identifiable information (PII) beyond its permitted timeframe. Varonis addresses these compliance issues by relocating the non-compliant data to a secure location. Once the data is moved, admins can take further actions on the data, such as review, archival, or deletion, to ensure compliance and protect sensitive information.
These policies are also designed to mitigate the impact of a data breach and ensure that sensitive information does not end up in risky, non-compliant locations or become accessible to AI systems. Varonis consistently monitors your data and enforces quarantine protocols immediately upon detecting any policy violations, such as GDPR data being exposed to the entire organization.
Support large-scale domain consolidation and cloud migrations.
Develop policies to easily consolidate domains and handle large-scale data migrations, all while ensuring data stays protected and permissions are optimized. Stage on-premises data for cloud migrations with powerful rules that can separate the files you need from those you don’t.
Seamlessly copy or move large amounts of data cross-domain or cross-platform without the risk of breaking permissions or interrupting business. Take full control of naming conventions, permission structures, and collision behavior to ensure consistency as data moves across the environment.
For instance, if your organization is transitioning part of its operations from Windows file servers to a new NAS device, you can establish a policy targeting specific folders for migration. This policy will automatically move the selected folders from the file server to the NAS device while preserving the original file and permission structures.
Optimize storage and reduce costs.
Another significant challenge organizations face is efficiently managing storage and eliminating obsolete data without disrupting operations. Organizations must balance retaining information for compliance with streamlining storage.
Varonis Data Lifecycle Automation helps by implementing robust storage optimization strategies. By monitoring data activity, Varonis identifies stale files and automatically transfers them to a secure location for archival or deletion, optimizing storage and reducing costs.
Varonis creates granular policies for specific retention requirements, ensuring non-essential data is removed. Policies based on creation date, last access date, or data sensitivity help maintain an efficient storage environment. Varonis Data Lifecycle Automation proactively manages the data lifecycle, adjusting policies to meet business and regulatory needs.
How Varonis Data Lifecycle Automation works
Creating and enforcing data governance policies has never been easier than with Varonis Data Lifecycle Automation. You can easily create custom, no-code policies that will automatically and seamlessly copy or move data across your environment from one location to another.
Varonis Data Lifecycle Automation is just one part of the comprehensive Varonis Data Security Platform (DSP). By combining Data Lifecycle Automation with Varonis' industry-leading data discovery and classification, automated risk reduction, and threat detection capabilities, you can ensure sensitive data is identified, secured, and compliant throughout its lifecycle from a single, unified platform with little to no manual effort.
Configuring granular policies
You can configure granular policies based on a multitude of attributes, such as source location, sensitivity, regulation, exposure, activity, creation date, and more. This enables you to easily create custom policies to fulfill your unique data governance, lifecycle, and compliance needs. As you configure your policy, you can also preview the data that will be affected before you apply it.
Configure the Varonis Data Lifecycle Automation Policy to fit your needs.
Configure the Varonis Data Lifecycle Automation Policy to fit your needs.
As a part of the policy creation, you can set whether you want to maintain the file structure and permissions in the new location, ensuring that users can continue to access and use the data in the new location if necessary.
Determine if the folder structure and system permissions should be copied with the data.
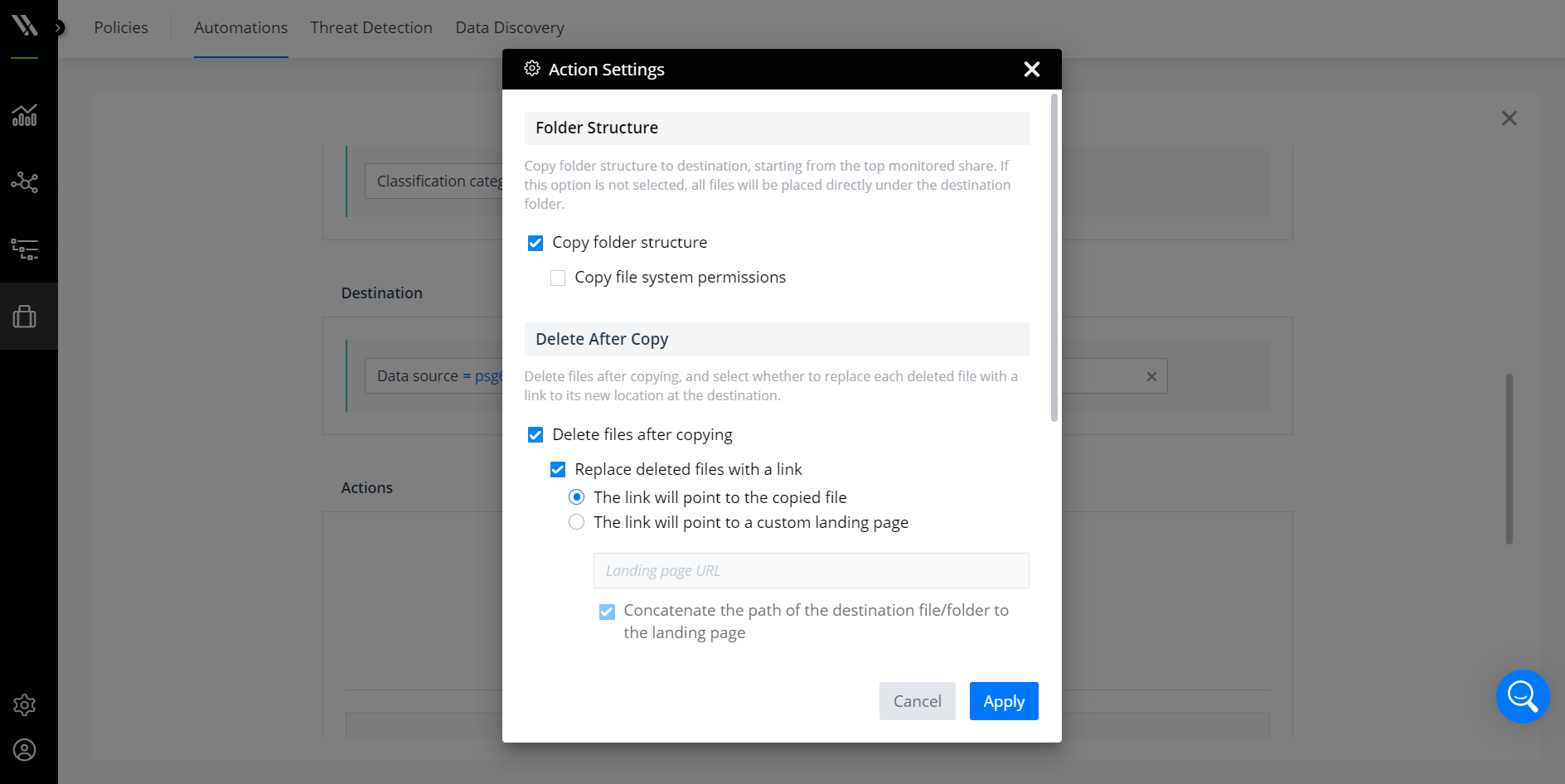
Determine if the folder structure and system permissions should be copied with the data.
Additionally, you can set the collision behavior and specify the copy logic for situations where folders and files already exist in the destination. Options include overwriting the existing data, merging the data, skipping the data, or renaming the new data.
Configure the policy’s collision behavior.
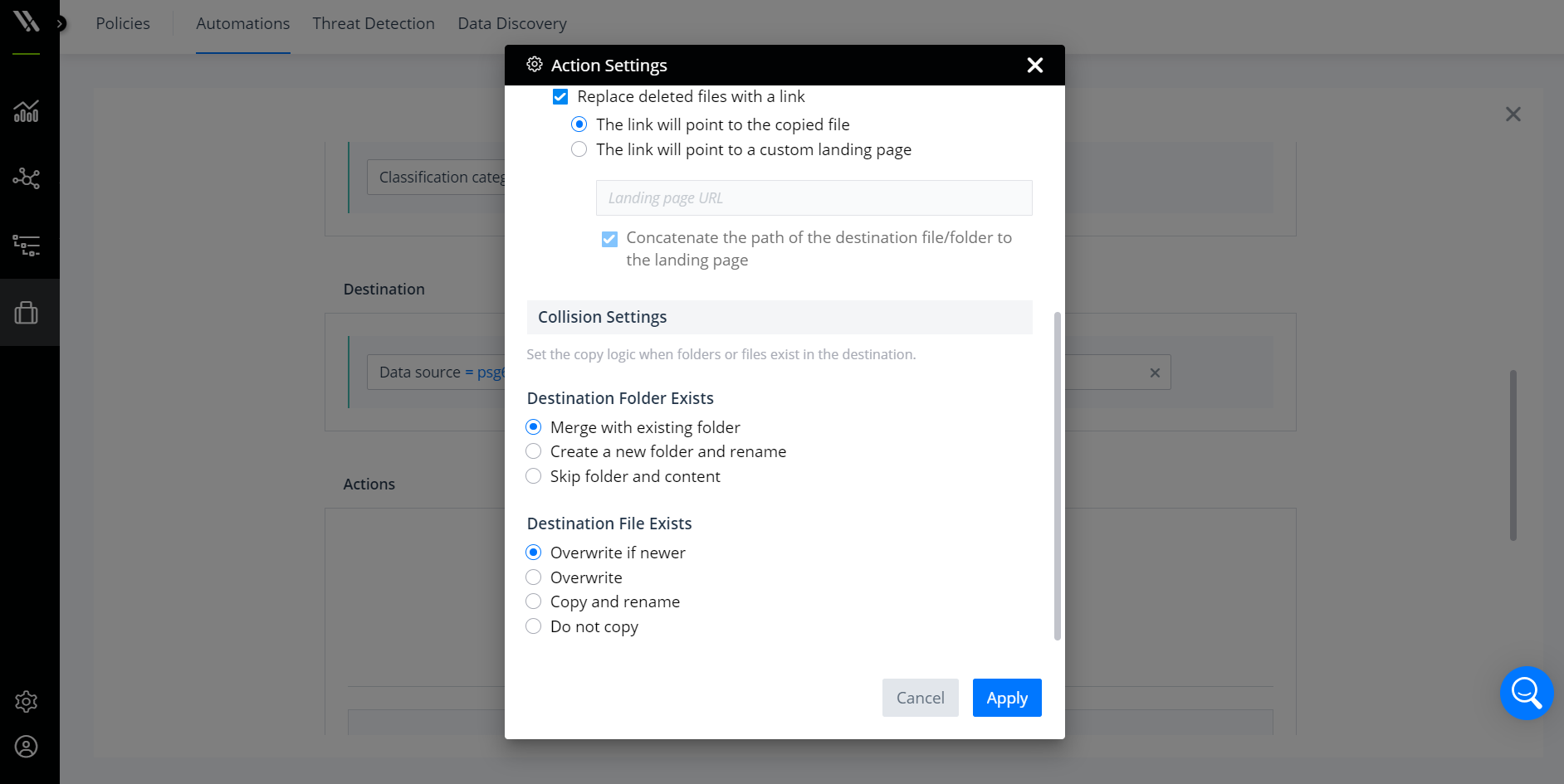
Configure the policy’s collision behavior.
Scheduling and approving policies
You can configure policies to run once, daily, weekly, monthly, or continuously. If set to run continuously, Varonis will automatically execute the policy once it identifies data that falls within the policy’s parameters.
Varonis includes human-in-the-loop controls to verify that policies function correctly by requiring authorization before execution. When configured, Varonis notifies the appropriate authorizers for approval prior to running the action.
Configure authorizers and the action schedule.
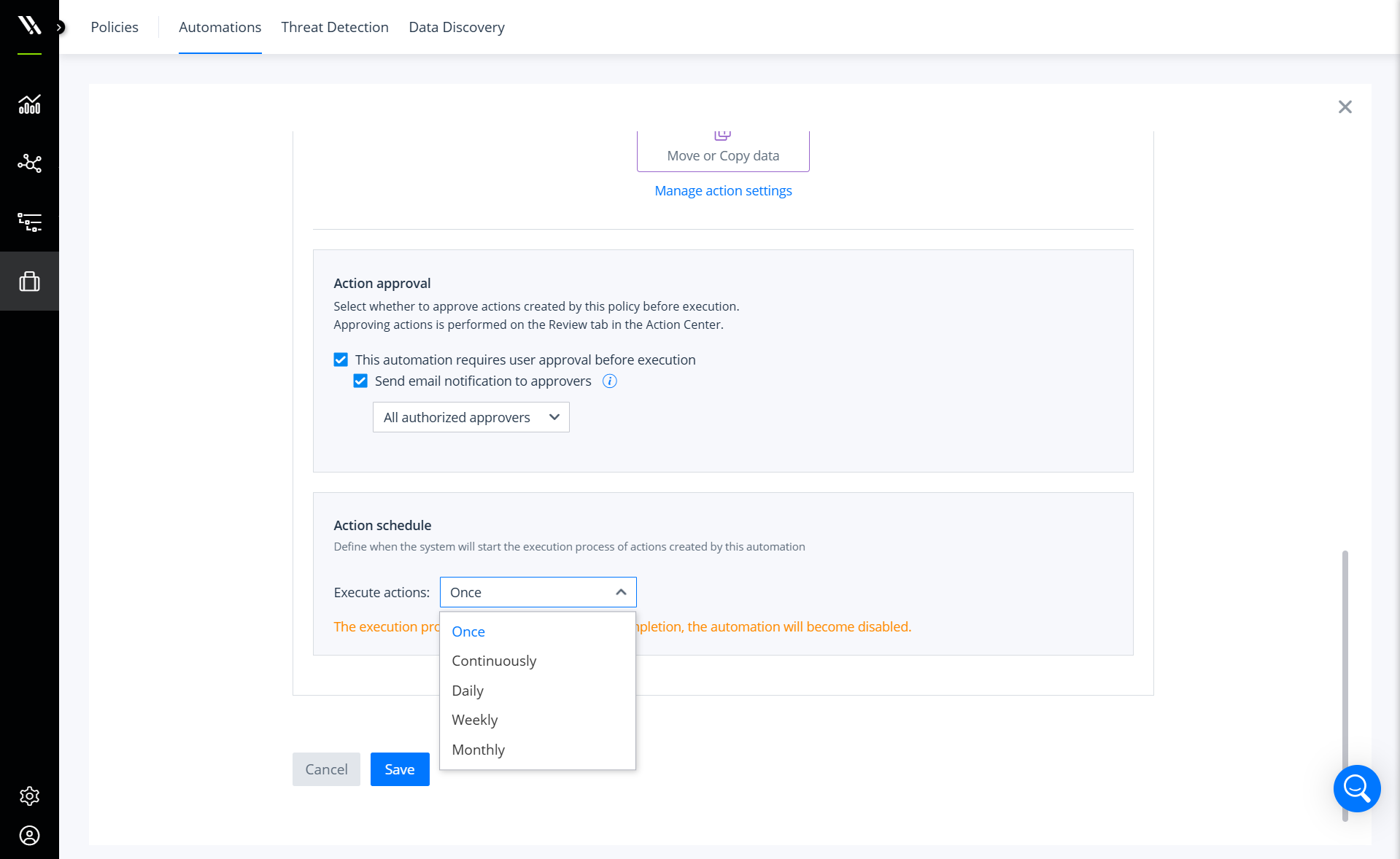
Configure authorizers and the action schedule.
Executing the policy
Once the policy is created, Varonis continuously monitors your environment to detect data that falls within the policy’s set parameters. Varonis Data Lifecycle Automation then automatically copies or moves the target data to a specified secure location, ensuring your data governance practices consistently comply with relevant business and regulatory requirements.
After the data is moved, Varonis creates a stub file in the original location that explains why the data was relocated and provides a link to the new location or a designated landing page.
From there, admins can take further action on the data if necessary, such as reviewing, deleting, or archiving the data.
Try Varonis for free.
Knowing where your sensitive data exists, who can access it, and what users are doing with it are all critical questions that need answers to ensure compliance and protect it from cyberattacks. Varonis uniquely combines these key security aspects in one unified solution.
At Varonis, we’re on a mission to deliver automated security outcomes with a holistic approach to data security. Our unified Data Security Platform installs in just minutes and protects your sensitive data wherever it resides, including cloud, SaaS, and data center.
Are you curious to see what risks may exist in your environment and achieve tangible security outcomes with minimal effort? Schedule a demo to get started today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









