Cloud apps and malicious links are changing the way attackers mess with organizations, especially when they borrow a little trust from well-known vendors.
The smartest hackers aren’t just smashing through the front door — they’re sneaking in through the crowd, blending their digital moves with legitimate business traffic and making their attacks look just like regular, everyday cloud activity.
How hackers use cloud platforms
Imagine a busy train station, packed with people who all have tickets. Attackers have figured out how to slip in and ride along with everyone else because security guards (or security tools) tend to trust anyone who gets on using a known train company. In cyber terms, attackers rent space on popular cloud services or buy time on virtual servers from big vendors. These providers make everything easy to use, offering fast and reliable web hosting, email, and storage. This convenience is precisely what cybercriminals exploit.
They’ll use these platforms to launch phishing scams, distribute malware, or even run sneaky cryptojacking operations. Sometimes, they steal cloud account credentials, then use those identities to deliver spam or create mailbox rules that help them stay hidden. Advanced attackers might even wait for managed service providers to connect before piggybacking into target environments for broader access.
Defenders struggle because the traffic looks normal, comes from reputable vendors, and the tools are designed to help businesses, not stop criminals. With more businesses going all-in on cloud providers, security teams face a war in which every attacker wears a clever disguise.
Cloaked links and URL trickery
Links aren’t always what they seem. Hackers can rewrite URLs in crafty ways, making them look fine at first glance but secretly leading people straight into trouble. Take the classic trick with '@' symbols — hackers wedge them into links and fool browsers into ignoring everything before the symbol, landing users on the wrong site. Sometimes it’s about swapping letters for lookalikes (“homographs”) or using clever formats to hide the real destination.
Then layer on more tricks: hiding the destination behind chains of redirects, using short URLs, or running everything through big-name cloud services. Security users and automated checks often see a link pointing to a trusted vendor. That’s much less likely to get flagged and blocked. This leads to attacks quietly making their way to users.
Layers of obfuscation
Attackers are pros at stacking their tricks. Maybe the path starts with a cloud app everyone knows, then hops through rewritten URLs, before passing through several respected vendors. Each redirect makes it harder for defenders to spot the attack. API abuse and stolen tokens mean the criminal can leap from one trusted service to another, gathering more data or spreading laterally without raising alarms.
In a recent attack, a malicious link jumped across four different email security vendors before landing on a credential-stealing WordPress site disguised as a Microsoft login. The vendors’ domains were allowlisted, so automated tools trusted each stop along the way. Because tools rely heavily on static rules or allowlists, these multi-hop links often zip by undetected — unless something more creative is watching the real destination.
Real attack example
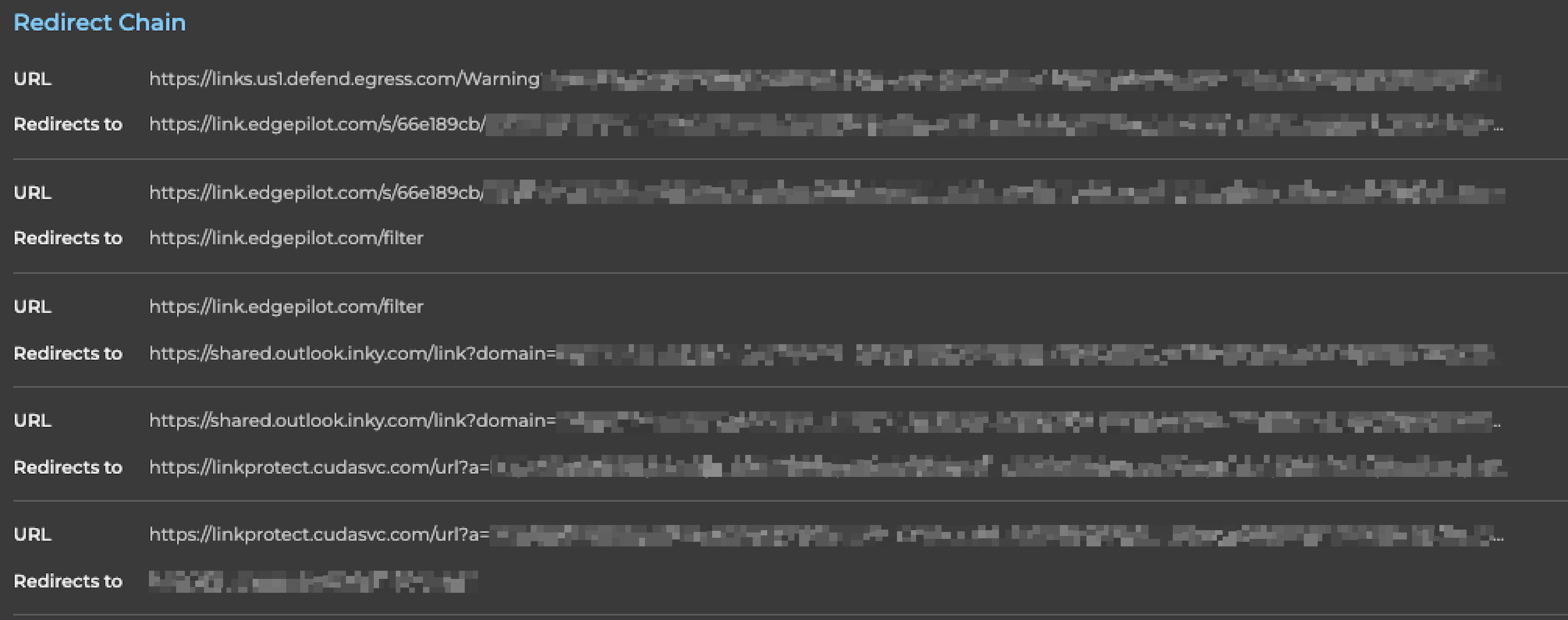
Here’s how a complicated credential-stealing attack played out: A link started by passing through egress (part of KnowBe4), which passed off to OpenText’s edgepilot.com. Next came a forward to a server owned by Inky, another security vendor. Finally, it redirected to Barracuda’s cudasvc.com, ending up at a fake WordPress login page set up to swipe Microsoft credentials. All these hops ran through companies that organizations know and trust.
Since defenders allow traffic from those vendors, the link didn’t get blocked. Most automated tools don’t actually follow the chain all the way to the true destination. Click-time protection only works if you inspect the content users will ultimately see. If the last page is a fake login while the route starts through trusted vendors, legacy security filters often miss it completely.
Behavior over blocks
So, what can defenders do? It’s time to get smarter and go beyond simple blocklists. Behavioral detection is the star player here. By watching for odd moves — like logins from unusual locations, mailbox rule changes, or traffic spikes from trusted cloud domains —security teams can spot what’s odd, not just what’s listed.
Continuous review of cloud app integrations, logging, and smart monitoring for strange API use is a must. When it comes to URLs, scanning and intelligent filtering that analyzes the whole journey, not just the first vendor or obvious redirects, are key. Organizations need tools such as Varonis Interceptor's Phishing Sandbox that can follow the twists and turns of rewritten links, expose what's really being served to users, and protect even when the traffic looks "safe."
Sometimes, this means using advanced solutions baked deeply into the infrastructure to provide context-rich logging and visibility, tracking access and changes that stand out, even on platforms everyone trusts. By tuning defenses toward behavior and full journey analysis, organizations can keep cloud security strong — even as attacker tactics get trickier by the day.
Adapt, don’t just react
Modern cyberattacks are clever, fast-moving, and great at blending in. Defenders who adapt, watch for behaviors, and inspect all the moving parts (not just the ones on the trusted list) have the best shot at keeping their cloud environments safe. In an age where trust can be borrowed, building security that looks for what attackers do, rather than who they pretend to be, is the way forward.
Varonis Interceptor is continuously adapting to the tricks that attackers are creating every single day by being able to follow every single link to their destination. Inspecting what's there in real time, no matter what obfuscations are put in their way.
Interested in how predictive AI can protect organizations against complex phishing attacks? Try Varonis Interceptor.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.



-1.png)