A new phishing kit called Spiderman makes it easy for attackers to weave an extensive web of attacks targeting customers of dozens of European banks and online financial services providers.
This kit is noteworthy for its professional structure and broad target scope, spanning multiple countries and even cryptocurrency platforms. Its organized interface provides cybercriminals with an all-in-one platform to launch phishing campaigns, capture credentials, and manage stolen session data in real time.
This level of automation means attackers no longer need web development or phishing expertise. It’s part of an alarming trend we continue to see with feature-packed tools (SpamGPT, MatrixPDF, Atroposia) making widescale attacks easier than ever before. In practice, it reduces European bank phishing to a few clicks: pick a bank, launch a pixel-perfect clone, and send a ready-made lure that looks like it came from the real institution.
Spiderman is a full-stack phishing framework that replicates dozens of European banking login pages, and even some government portals. While single-bank phishing kits are widely available for purchase, Spiderman consolidates multiple European financial brands into one kit for cross-country targeting at scale. It includes modules for banks such as Deutsche Bank, Commerzbank, ING (Germany & Belgium), CaixaBank, and several crypto wallet providers.
Taken together, this breadth points to a framework that’s already being used at scale. A Signal messenger group linked to the seller behind Spiderman includes roughly ~750 members, suggesting a sizable, active user community and continued circulation of the kit.

A multi-country threat with multi-year implications
Spiderman isn't the first European banking phishing kit, but its scale, polish, and cross-border coverage make it one of the most dangerous we’ve analyzed this year, targeting the financial industry.
1. Consolidation of targets into a single interface
Most phishing kits focus on a single bank or region. Spiderman merges dozens of institutions across five countries. This increases efficiency and enables attackers to pivot between regions quickly.
2. Targeting that bypasses traditional detection
With ISP whitelisting, geo-blocking, and device filtering, Spiderman dramatically reduces visibility to cybersecurity experts. Many phishing-detection products are designed to scan the infrastructure that this kit explicitly filters out.
3. Strong support for crypto theft
Crypto seed phrase capture modules ("Ledger Seedphrase,” “Metamask Seedphrase,” “Exodus Seedphrase”) signal a shift toward hybrid banking + crypto fraud operations.
4. Real-time OTP interception will become the norm
The inclusion of Phototan and OTP capture indicates a high level of general sophistication. European banks relying on TAN authentication remain especially vulnerable.
5. Long-term evolution is inevitable
Because Spiderman is modular, new banks, portals, and authentication methods can be added. As European countries roll out updated e-banking flows, this kit will likely evolve in parallel.
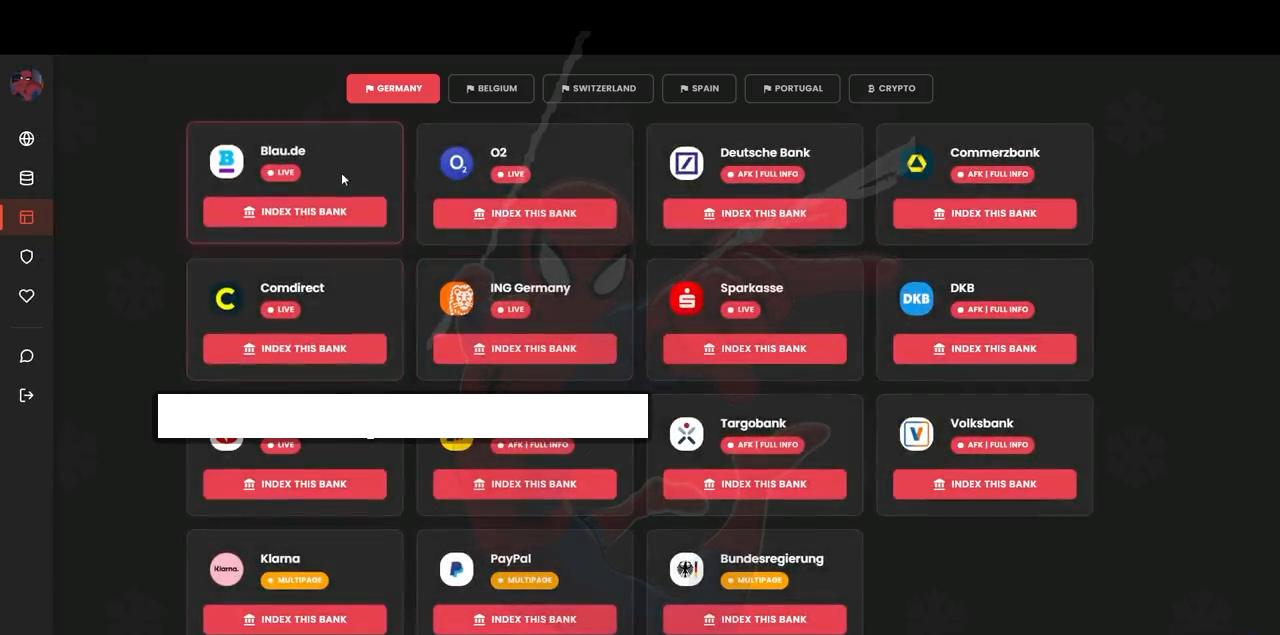
Attackers using Spiderman select the bank or service they want to impersonate, click “Index This Bank,” and the kit automatically prepares a phishing page clone with login, password, PhotoTAN/2FA prompts, and credit card input forms.
Inside the Spiderman control panel
The operator dashboard displays victim sessions in real time, tracking each target’s status, chosen bank, user inputs, and machine details. The interface supports several features to optimize attacks, including:
- Live session monitoring
- One-click credential export
- PhotoTAN capture (real time OTP interception)
- Full credit card and identity harvesting
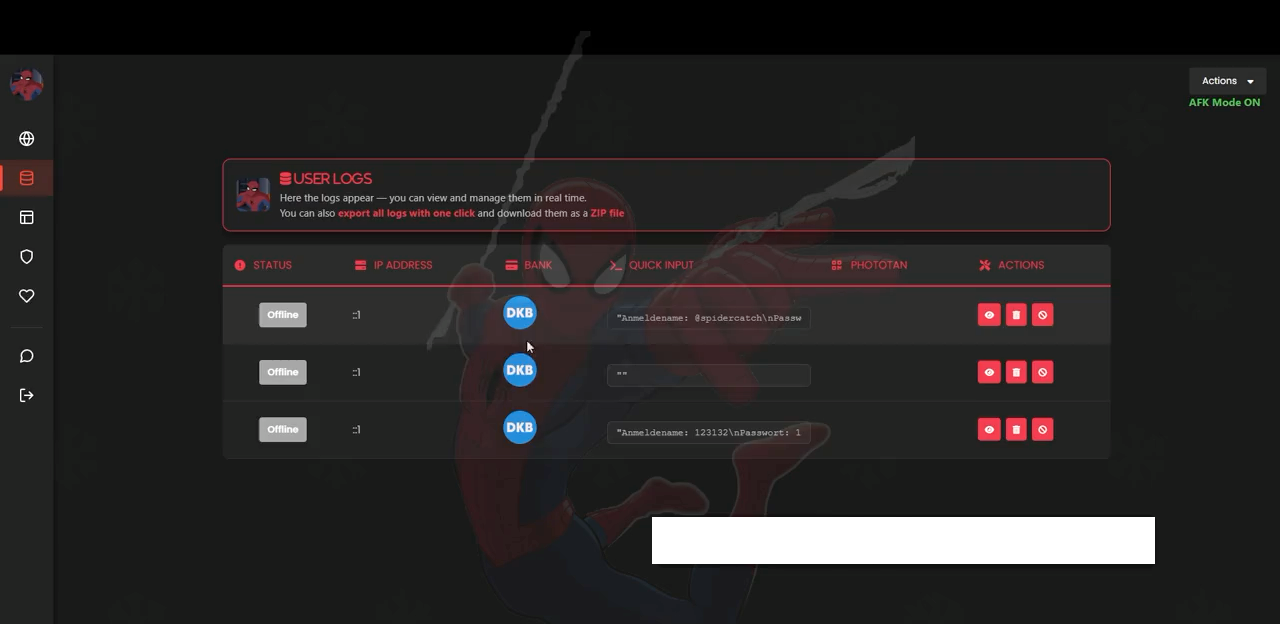
The UI reveals that once a victim enters their initial login credentials, the operator can trigger additional prompts, such as asking for a credit card number, expiration date, phone number, or a PhotoTAN code.
This flexible, multi-step approach is particularly effective in European banking fraud, where login credentials alone often aren’t enough to authorize transactions. After capturing credentials, Spiderman logs each session with a unique identifier so the attacker can maintain continuity through the entire phishing workflow.
Advanced targeting and filtering features
Spiderman comes with an unusually detailed access-control module that lets attackers restrict who can load the phishing page. The module is designed to minimize exposure, block security researchers, and ensure only legitimate targets reach the malicious site. Capabilities include:
- Country whitelisting – Only allow traffic from specific countries (Germany, Austria, Switzerland, Belgium, etc.).
- ISP/ASN whitelisting – Exclude visits from known data centers, VPNs, or unwanted networks.
- Device-type filtering – Serve the phishing page only to certain device types (desktop, mobile, Android, iOS).
- Custom redirect control – Send unwanted visitors to Google or another benign page instead of the phishing site.
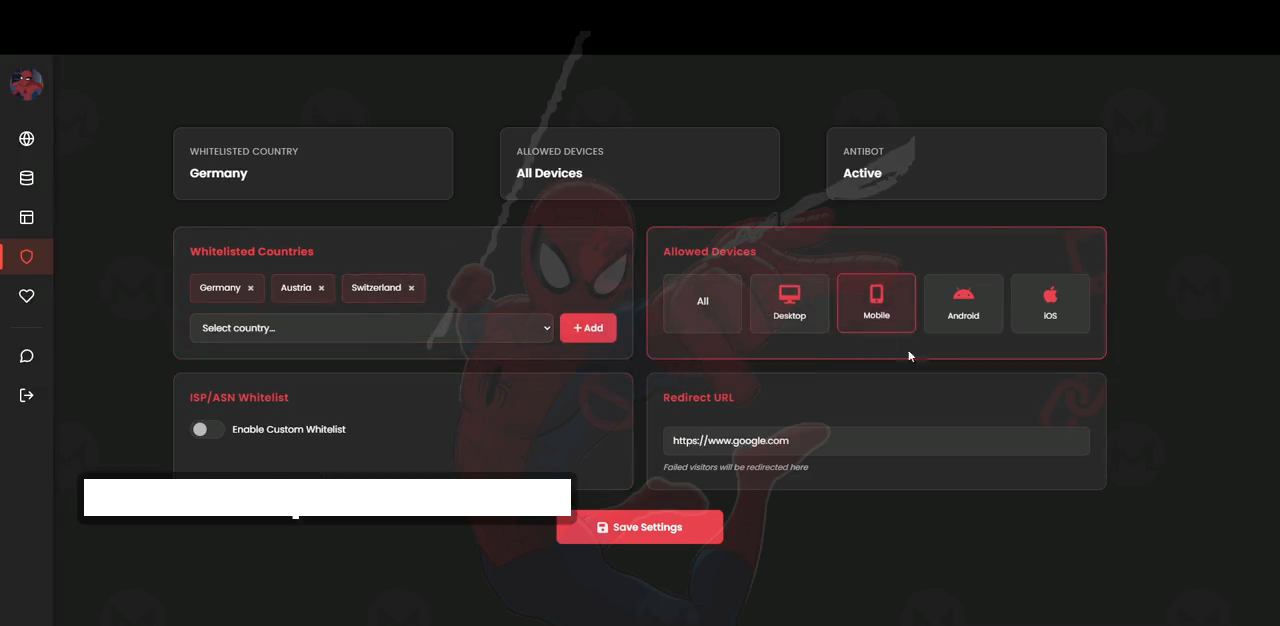
These anti-analysis controls allow the kit to evade automated crawlers, security scanners, and threat intelligence tools, making overall detection harder.
How Spiderman steals credentials in real time
Once a victim enters their banking username and password, the kit sends that data instantly to the operator panel. Operators can then trigger more requests in real time.
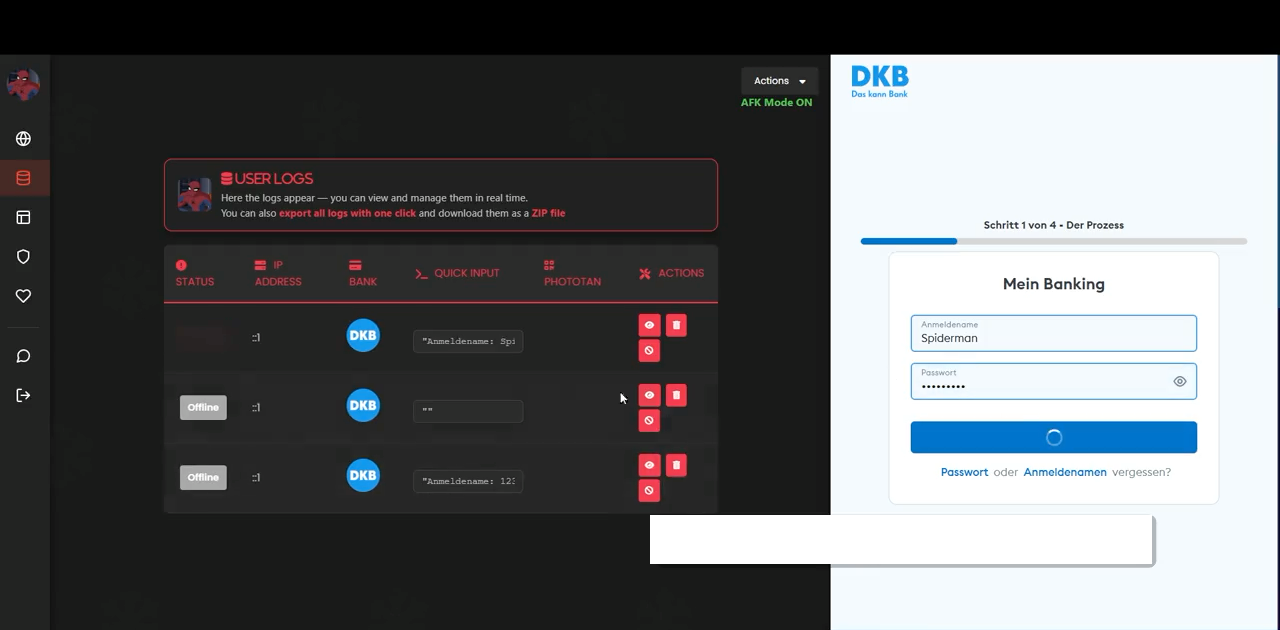
The example below shows how the kit captures a full identity packet from a single victim session, including:
- Username and password
- Full name
- Phone number
- Date of birth
- Credit card details
- User agent & IP metadata
This is more than enough information for account takeover, SIM-swap attacks, credit card fraud, and identity theft. Operators can also mark sessions as “Finished” once the workflow is complete, keeping stolen data organized for later exploitation.
How Varonis Interceptor can help
Varonis Interceptor is built to detect and disrupt phishing kits like Spiderman before they trick your employees. As an AI-based email security solution, Interceptor excels at spotting phishing emails that traditional filters might miss.
Interceptor analyzes messages on multiple levels, examining the language, tone, logos, and even the URLs hiding behind “click here” links, to catch subtle signs of deception. Phishing lures impersonating bank portals or urgent transfer requests are flagged and quarantined, keeping them out of inboxes.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







