Atroposia is a new remote access trojan (RAT) found by Varonis that uses encrypted command channels, hidden remote access, credential and wallet theft, and persistence.
Atroposia isn’t an outlier. It’s the latest entry in a growing market of turnkey, plug-and-play criminal toolkits we recently found, alongside tools such as SpamGPT and MatrixPDF.
SpamGPT is an AI-driven “spam-as-a-service” platform that automates phishing campaign creation, SMTP/IMAP cracking, and deliverability tooling, effectively packaging marketing-grade campaign features for criminals. MatrixPDF is a malicious PDF builder that weaponizes ordinary PDF files by adding overlays, redirects, and embedded actions that help attackers bypass email filters and deliver phishing or malware lures.
Together with modular RATs like Atroposia, these toolkits show how discovery, delivery, and evasion are bundled into easy-to-use control panels that put sophisticated attacks within reach of low- and no-skill operators.
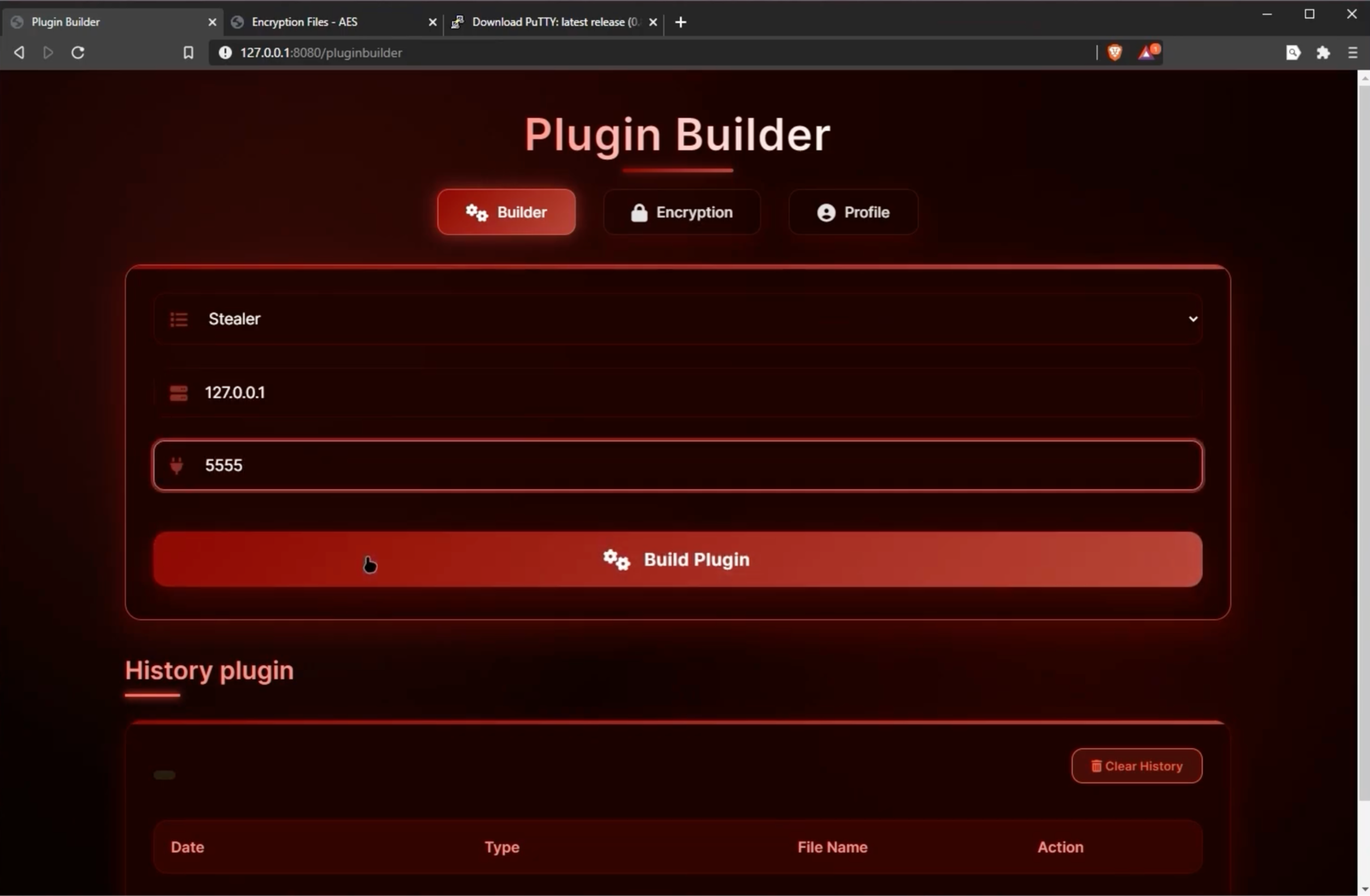
Varonis recently uncovered Atroposia being promoted on underground forums as a modular remote access trojan with a full complement of offensive capabilities: hidden remote desktop takeover, credential and cryptocurrency wallet theft, DNS hijacking, and local vulnerability scanning all in one package.
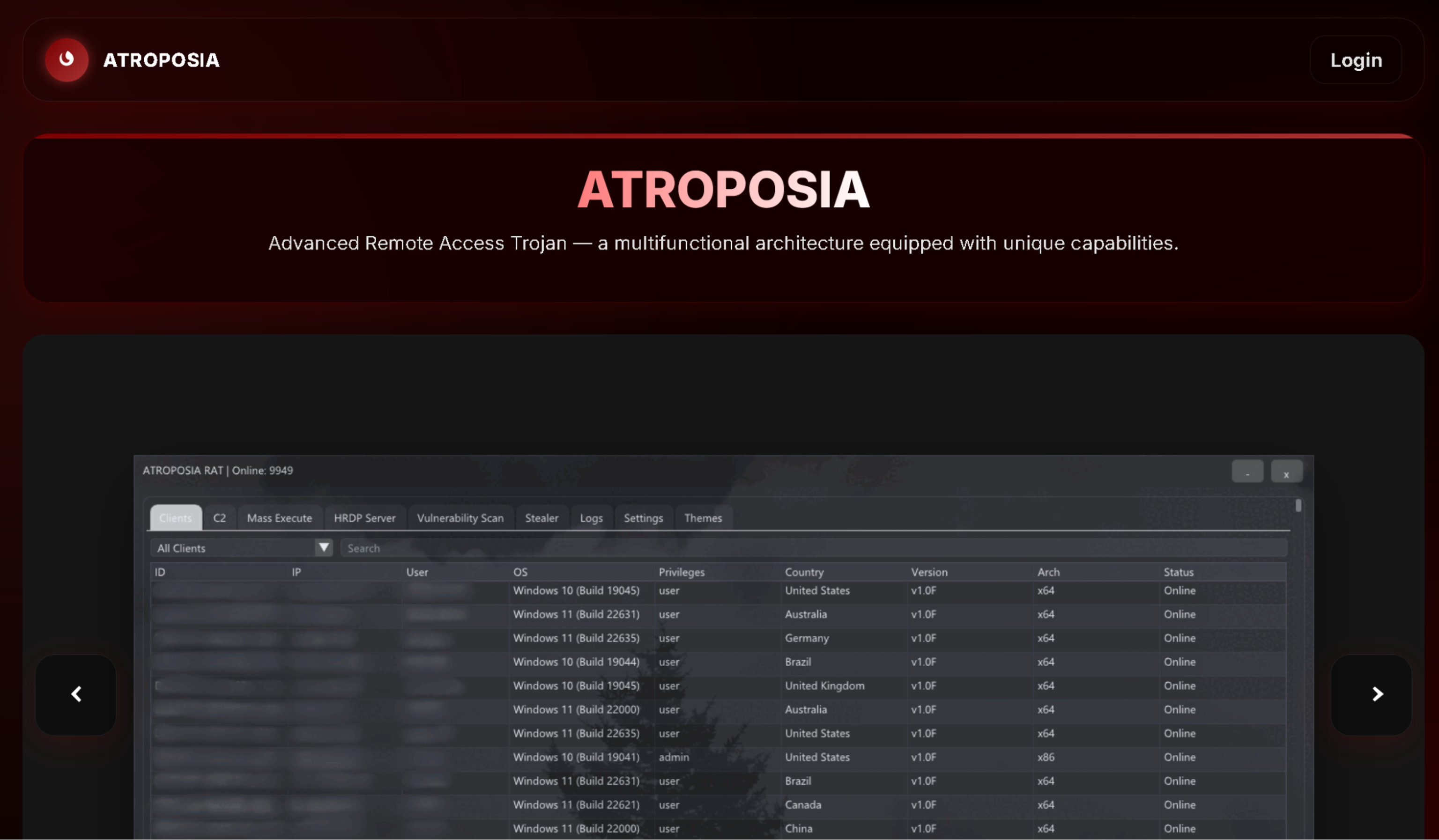
Its control panel and plugin builder make the tool surprisingly easy to operate, lowering the skill required to run complex attacks. Priced at roughly $200 per month, $500 every three months, or $900 for six months, Atroposia’s affordability and user-friendly interface make it accessible even to low- and no-skill attackers.
All command-and-control (C2) server communication is encrypted to foil traffic inspection. The malware can automatically escalate privileges via UAC bypass to gain admin rights and install multiple persistence mechanisms to survive reboots. These techniques allow Atroposia to blend into systems, avoid antivirus software, and maintain long-term access without tipping off users or IT staff.
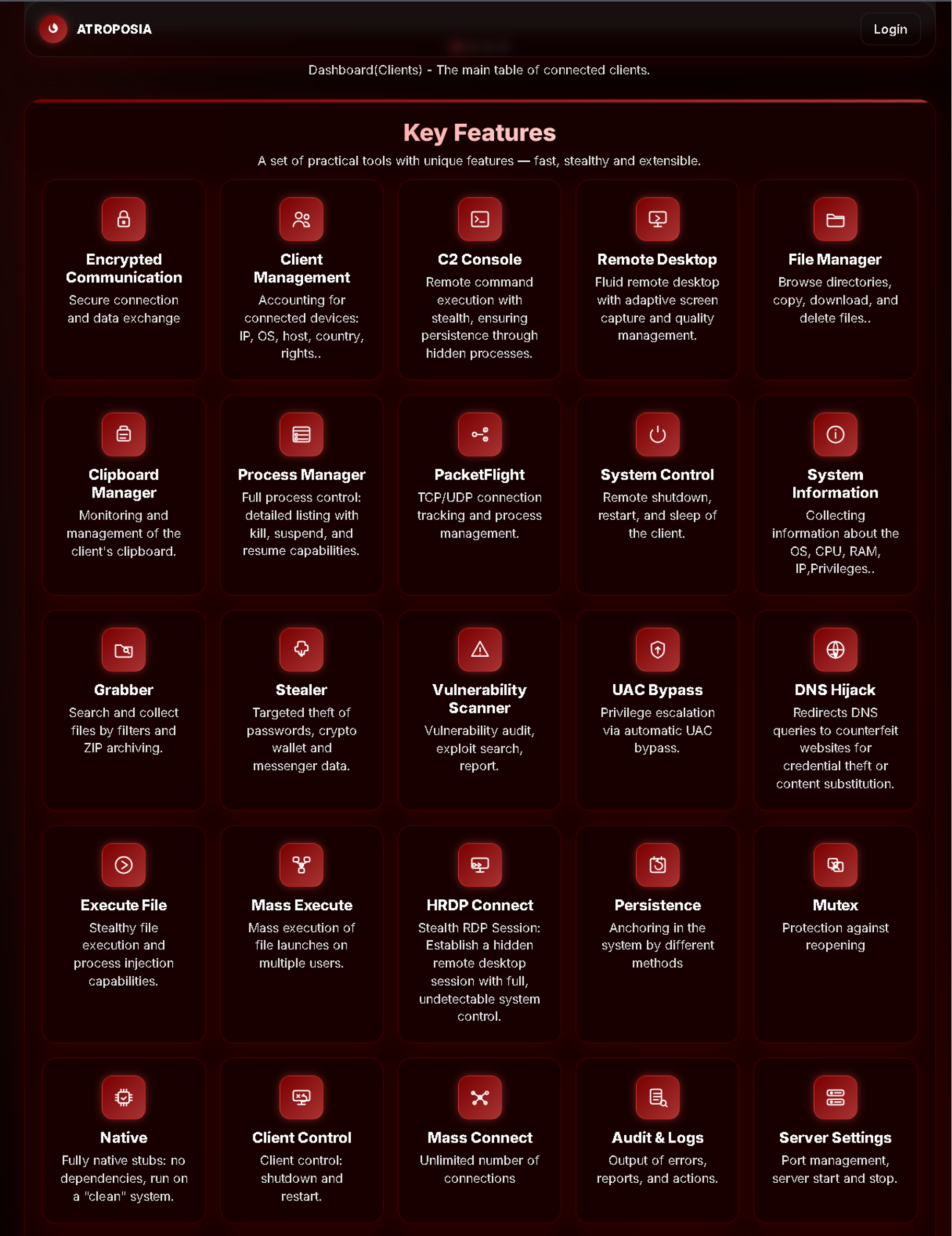
Hidden desktop access with HRDP (Stealth RDP)
One of Atroposia’s main capabilities is its hidden remote desktop feature. Branded “HRDP Connect” establishes a remote desktop session invisibly, so the victim sees no on-screen indication of remote control.
In practice, Atroposia spawns a covert desktop session in the background, essentially an invisible shadow login, that attackers can use to interact with the system fully. An intruder can surveil the users' activities or piggyback on their authenticated sessions without detection through this hidden RDP.
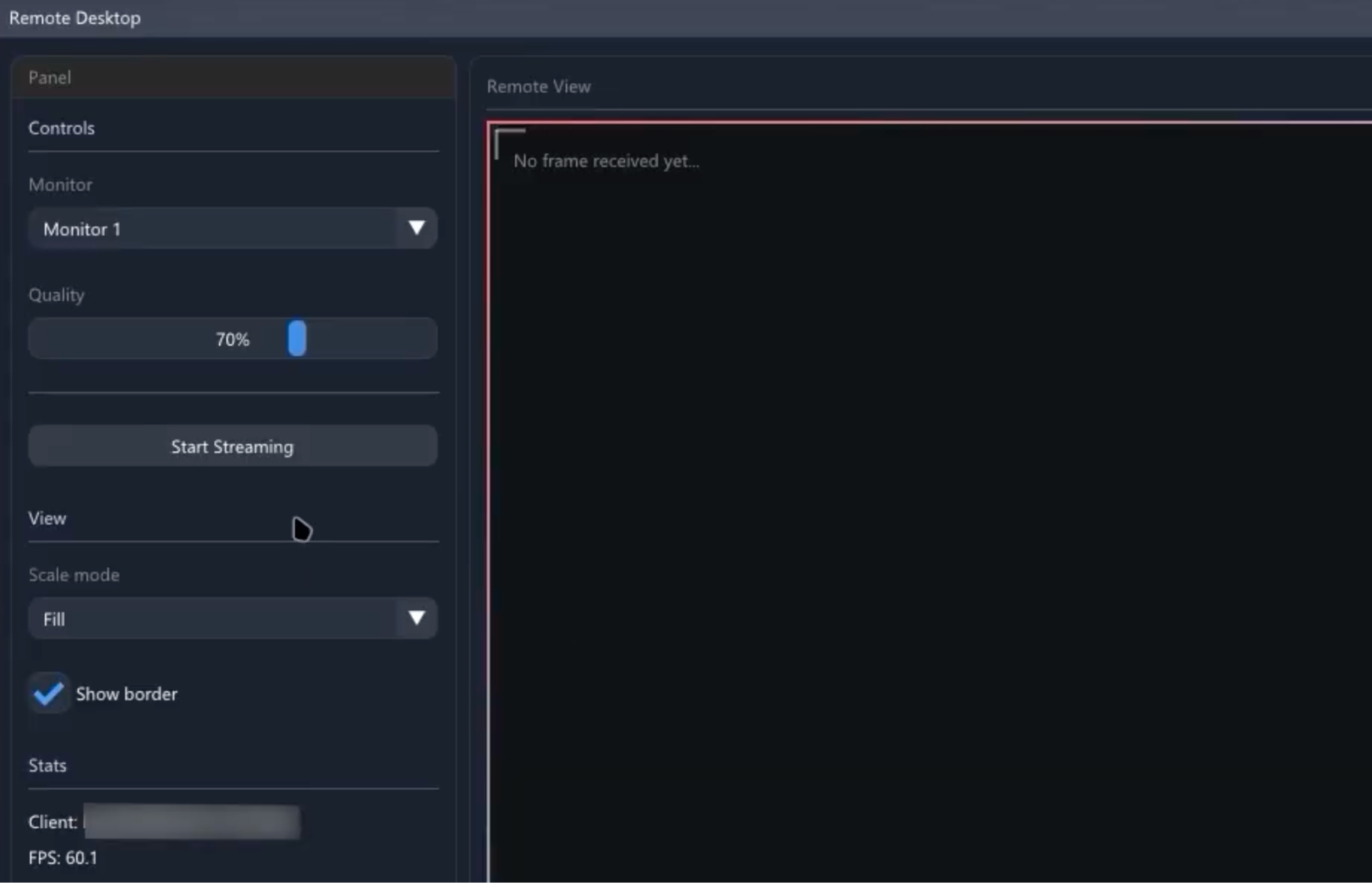
They gain the ability to open applications, view sensitive documents or emails, and manipulate the victim’s workflow as if they were the user, all while the legitimate user remains unaware. This undermines employee session integrity by allowing a silent man-in-the-desktop presence.
Even traditional remote access monitoring may miss HRDP, because it doesn’t rely on standard remote desktop notifications or logged-in user prompts. By covertly streaming the screen, Atroposia enables attackers to conduct espionage or data theft in real time under the guise of the user’s own session.
File system control and stealthy data exfiltration
Atroposia grants attackers complete remote file system access on infected endpoints. Its built-in file manager provides a full explorer-like view of the drives and directories. Attackers can remotely browse directories, search for sensitive files, download or delete data, and execute files on the victim’s machine. This level of control means an intruder can quietly rifle through documents, source code, or databases on user workstations or network shares. Atroposia’s data theft tools are designed to filelessly and bulk exfiltrate information.
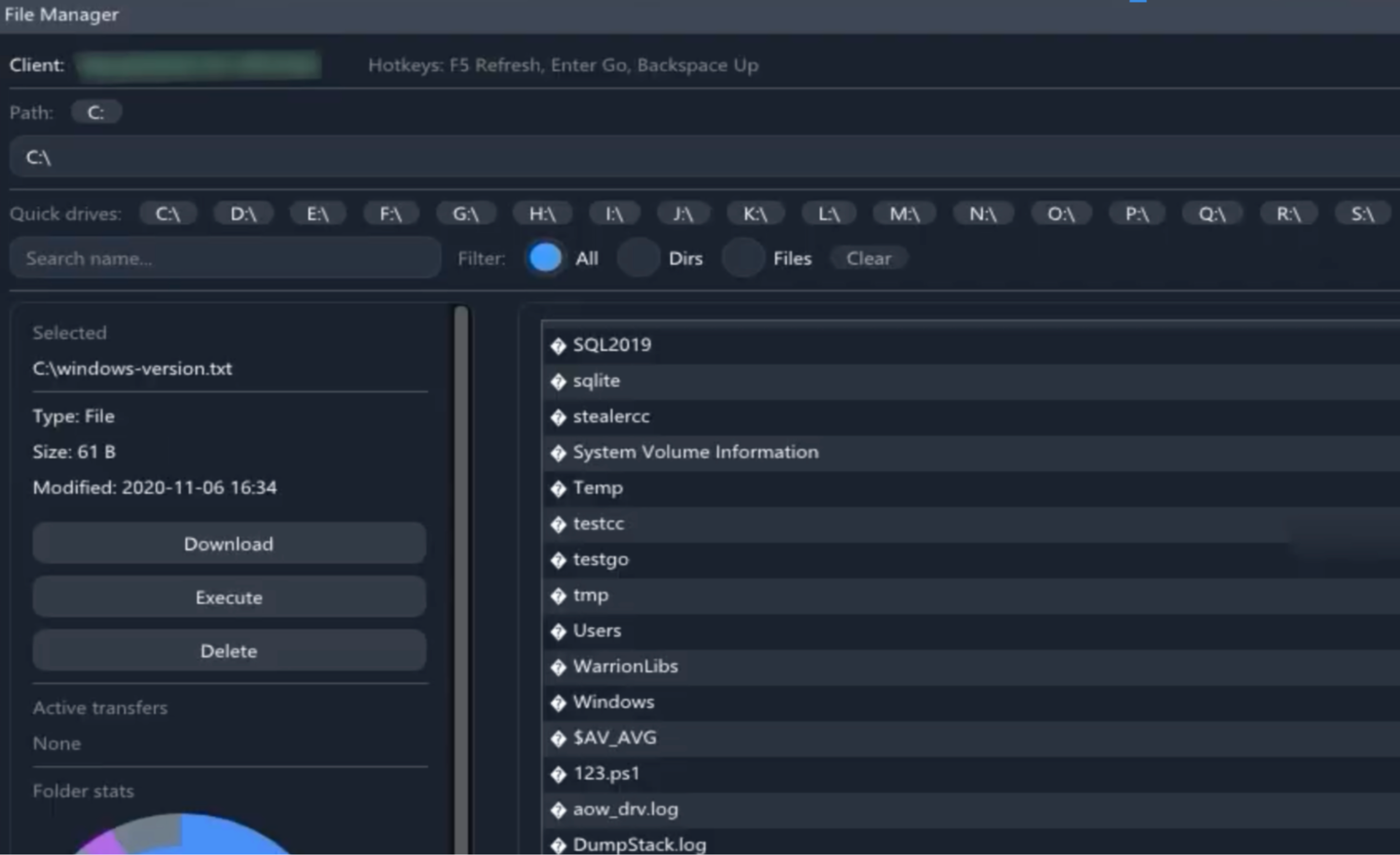
A dedicated Grabber module can automatically hunt for files by extension or keyword (for example, all PDFs or CSV files) and compress them into a password-protected ZIP for exfiltration.
The screenshot above shows an example archive containing stolen browser data, messenger sessions, and an automated screenshot collected in one sweep. Because the RAT can package and extract data in memory (and leverage legitimate tools on the host), it minimizes on-disk footprint, effectively a form of fileless exfiltration that leaves few traces for traditional DLP systems.
A stealer module targets specific sensitive data like saved logins, cryptocurrency wallets, and chat app files. Credentials for enterprise applications, virtual private networks, or password managers stored on the machine are ripe targets, which can then be used to penetrate further into corporate systems.
Clipboard snooping and credential theft
Atroposia also invades less obvious channels of sensitive data, namely, the user’s clipboard. Its clipboard manager monitors the target’s clipboard in real time, capturing anything the user copies or cuts on their machine. If an employee copies a password from a vault, a snippet of source code, or any confidential text, the RAT immediately logs it.
The image below shows how the malware presents a history of clipboard entries to the attacker, who can extract or modify them.
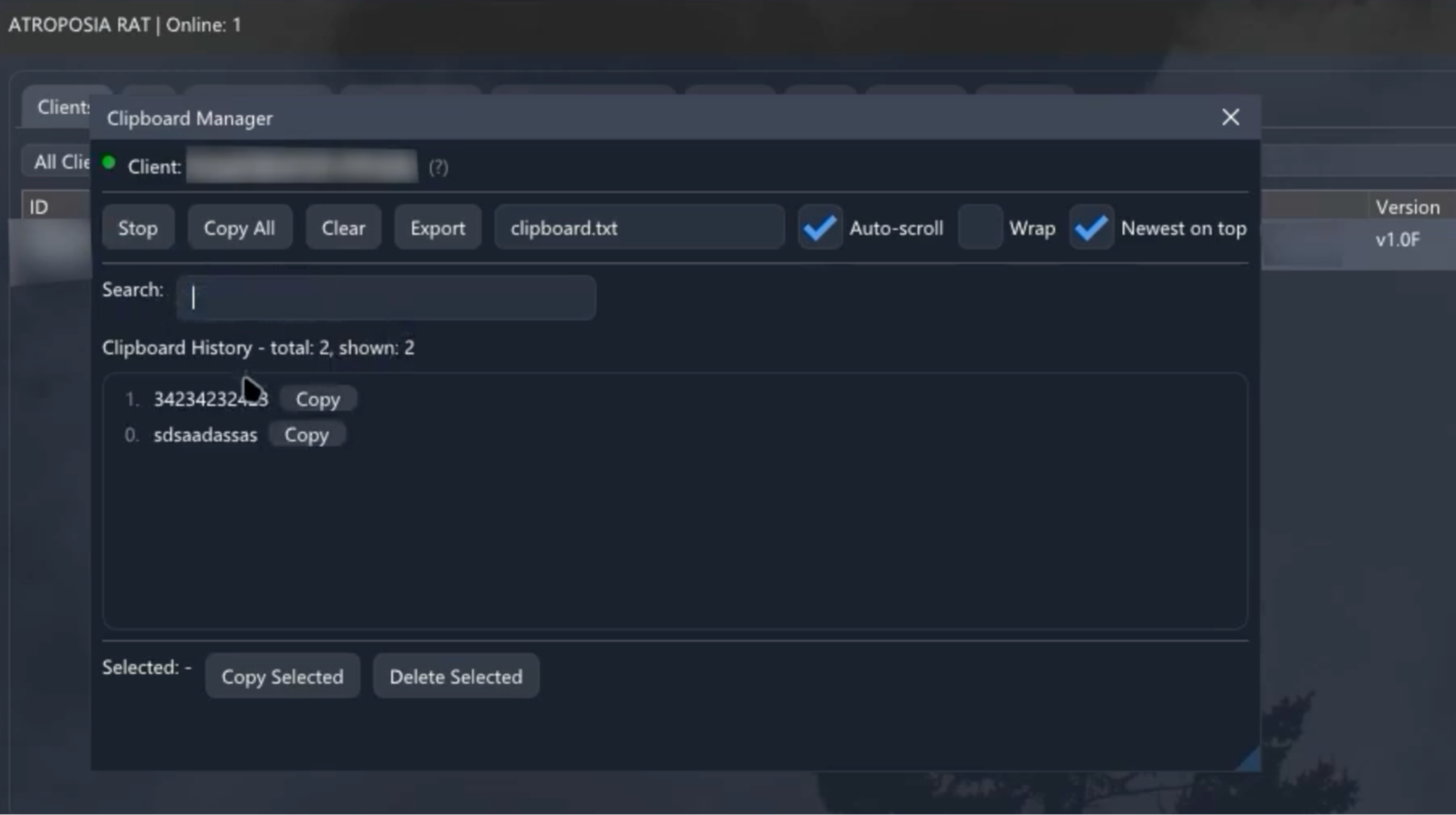
Many users copy credentials, API keys, or sensitive messages to the clipboard, assuming it’s ephemeral. Atroposia turns that assumption against the enterprise by harvesting clipboard data, undermining the confidentiality of even transient information.
In concert with its stealer, the RAT can collect authentication tokens, session cookies, or crypto wallet addresses from the clipboard, allowing attackers to hijack accounts or reroute cryptocurrency transactions.
DNS hijacking and network interference
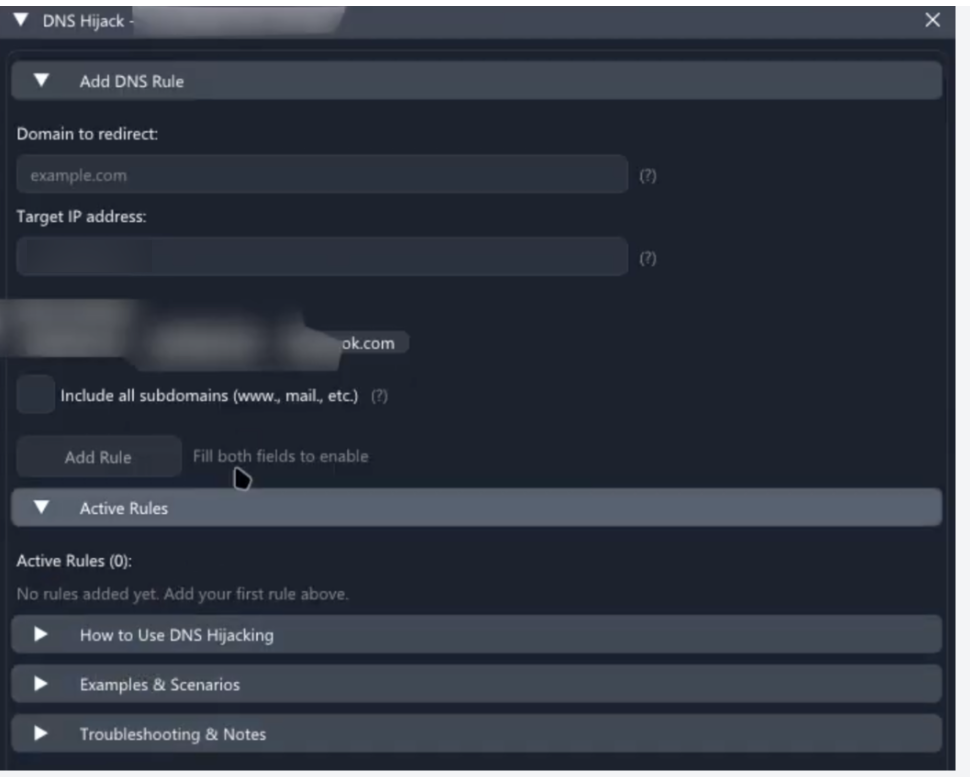
Beyond stealing data from the host, Atroposia manipulates network traffic to compromise the victim further. It features a DNS hijack module that lets the attacker arbitrarily redirect the infected system’s DNS queries. The operator can input a domain and assign it a fake IP address.
Once a rule is added, any attempt by the victim’s machine to reach that domain will be silently rerouted to the attacker’s chosen server.
This opens the door to phishing and man-in-the-middle attacks. An attacker could redirect an enterprise login portal — or any enterprise service — to a lookalike malicious site to capture credentials, all while the URL in the user’s browser appears correct.
By hijacking DNS at the host level, Atroposia bypasses external DNS protections and makes even HTTPS connections unsafe, because the victim is truly connecting to a rogue server.
This technique undermines network security controls and can be used to deploy fake software updates, inject ads or malware, or exfiltrate data through DNS tunnels.
Combined with the RAT’s other features, DNS hijacking means the malware isn’t just lurking on the endpoint; it’s actively altering the victim’s network experience in favor of the attacker.
Local scanning for vulnerabilities and evasion
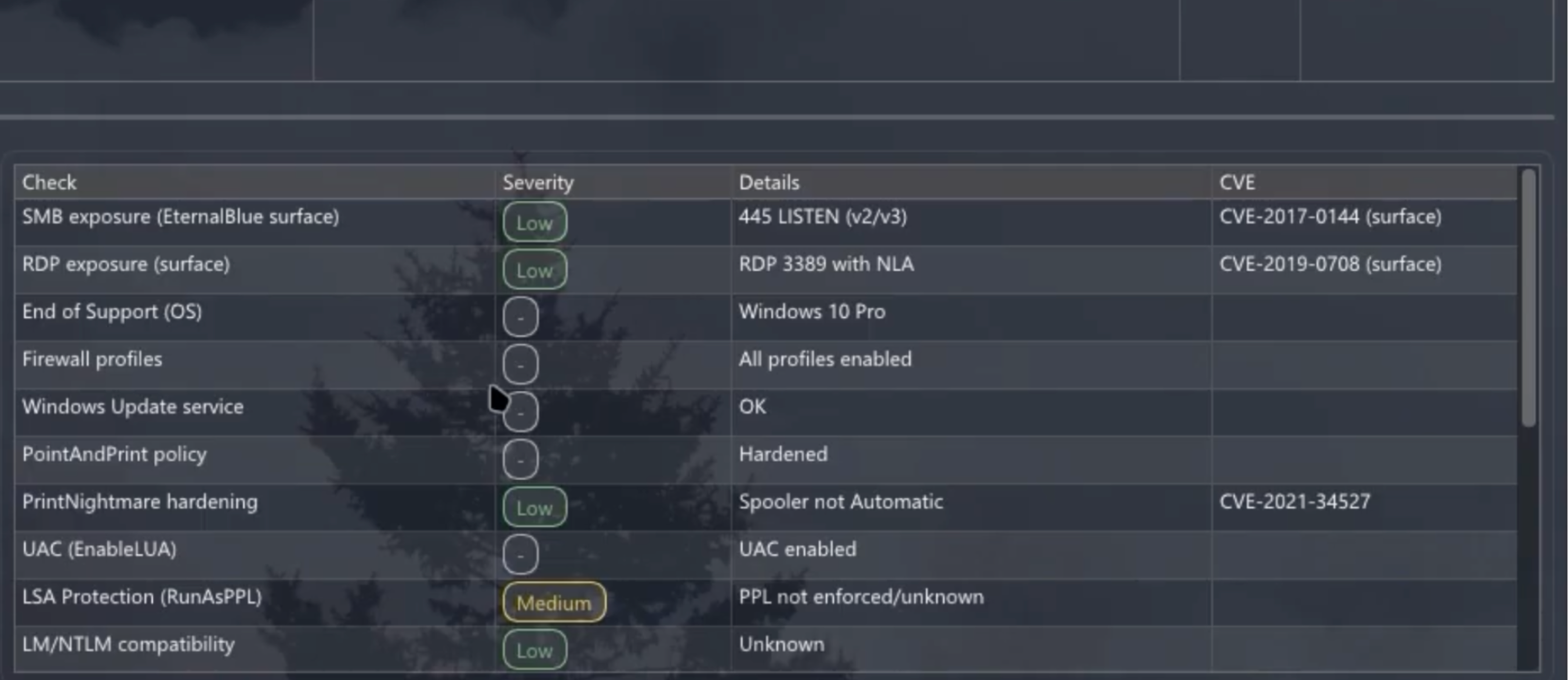
Atroposia also advertises a built-in vulnerability scanner module. Once a machine is compromised, the RAT can perform a local audit of the system’s security posture, enumerating missing patches, unsafe settings, or vulnerable software versions. The results (as a score or report) give the attacker a roadmap of vulnerabilities to exploit.
This is dangerous in corporate environments because the malware might find an outdated VPN client or an unpatched privilege escalation bug, which attackers can leverage to deepen their foothold.
This capability shows the RAT’s modular design: many of its functions (stealing, grabbing files, scanning vulnerabilities) operate as separate plugins that can run independently. An attacker could deploy only specific modules as needed to remain stealthy.
For instance, they might run the vulnerability scan to check if the host or nearby systems are exploitable quietly, then use the privilege escalation function to gain SYSTEM-level access based on those findings.
How cybercrime is being simplified
Running attacks used to require technical skill and custom-built malware. Today, cryptocurrency, Telegram channels, and underground marketplaces have made it possible for almost anyone to buy ready-made tools and launch complex campaigns.
Atroposia, SpamGPT, and MatrixPDF are examples of this new generation of criminal toolkits. Each package advanced attack capabilities into easy-to-use interfaces that automate phishing, delivery, and data theft.
They show how cybercrime is evolving into a service industry where sophistication no longer depends on skill but access.
Take your next steps with Varonis
Varonis plays a key role in detecting and mitigating threats like Atroposia.
Our Data Security Platform uses behavioral analytics to flag abnormal activity that matches the malware’s techniques. It monitors user and device behavior across the network and alerts on lateral movement or privilege escalation, the same internal reconnaissance and exploitation types Atroposia performs.
If an endpoint starts accessing unfamiliar file shares or a user account begins dumping credentials and sensitive data, Varonis correlates those deviations from normal behavior. Even if Atroposia evades antivirus, Varonis can detect it by spotting unusual data access, rogue DNS changes, or automated account activity before severe damage occurs.
Request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








-1.png)