Ever had an app sneak into your Salesforce environment without warning? It happens more often than you’d think — and attackers are counting on it.
However, Salesforce’s new API Access Control feature prevents unwanted apps from connecting to your environment. Think of it as a security checkpoint where only trusted apps get through, and only after you say so.
When OAuth phishing hits home
In a recent phishing campaign, stealing trust was the main focus over passwords. Salesforce users were tricked into authorizing a malicious OAuth app that mimicked a legitimate productivity tool. Once approved, the app gained persistent access to Gmail, Drive, and other services, bypassing MFA and operating silently in the background.
Without API Access Control, any user can authorize an app that’s never been vetted or installed. That’s how attackers sneak in.
This is where the principle of least privilege becomes critical. When every user has the ability to grant broad access, the attack surface expands dramatically. Least privilege means limiting access to only what’s necessary and only for those who truly need it.
By enforcing tighter controls over who can authorize apps and what those apps can do, organizations shrink the window of opportunity for attackers.
Salesforce’s new controls flip the script:
- Apps must be installed before they can connect
- Access can be scoped to specific users
- Admins must manually unblock them
Least privilege is a simple but powerful way to stop OAuth-based attacks before they start. It puts control back where it belongs — in the hands of your security team.

Now that we’ve outlined the high-level changes, let’s explore why they matter and how they reshape app governance in Salesforce.
What API Access Control changes
Regardless of their role, any Salesforce user can currently authorize an application to act on their behalf. This open policy can be risky for several reasons, specifically with attackers targeting unsuspecting users and tricking them into granting access to malicious apps via OAuth flows.
Once granted, these apps can quietly siphon sensitive company data, impersonate users, or even bypass multifactor authentication. Without proper gatekeeping, organizations lose visibility and control over which apps are active in their environment, making it easier for threats to slip through the cracks.
As attackers become more sophisticated, this lack of oversight becomes a glaring vulnerability that can lead to data breaches, compliance failures, and reputational damage. Threats are not just using Data Loader anymore — they exploit several OAuth-connected apps to bypass traditional authentication and gain persistent access.
Salesforce’s new default behavior helps shut that door. Here’s how it works:
- Newly installed applications will now require users to be pre-authorized before using the app, even if it was installed before.
- Unmanaged apps are blocked by default. If an app tries to connect without being installed, it’s automatically blocked.
- Manual approval is required. Once installed, admins must:
- Approve access for a pre-authorized list of users
- Unblock the app to confirm it’s trusted
- Applications that were previously installed must be secured by an administrator
This process ensures that no app gains access without deliberate administrative oversight — a significant win for security teams.
As you begin configuring API access controls in Salesforce, understanding the mechanics of connected app management becomes essential. The following guidance will walk you through the steps for specifying user permissions, granting admin approval, and tailoring OAuth policies to fit your organization’s security requirements.
Considering the risks and new controls, let's discuss configuring access to connected apps in your Salesforce org.
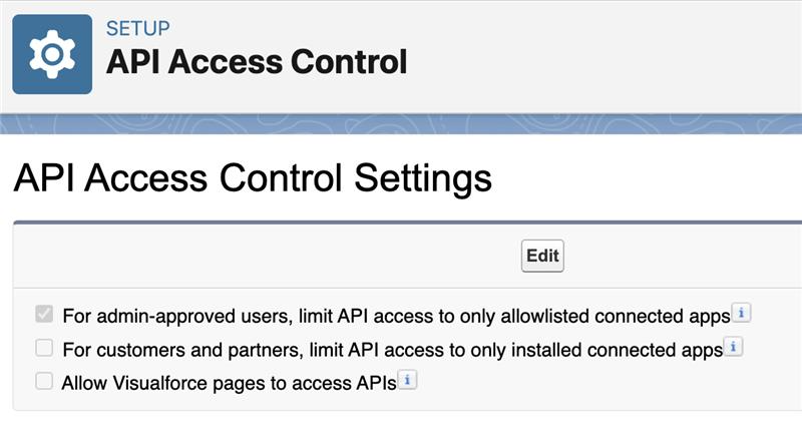
Manage access to a connected app after install
After installing a connected app in your Salesforce org, you can manage access by selecting the Permitted Users setting and configuring which users can access it. Follow these steps:
- From setup, enter Connected Apps in the Quick Find box and select Manage Connected Apps.
- Click Edit next to the connected app you are configuring access for.
- Under OAuth Policies, click the Permitted Users dropdown menu and select one of the following options.
All users may self-authorize: This default option allows all users within the organization to authorize the app after they log in successfully. Users need to approve the app the first time they access it.
Admin-approved users are pre-authorized: This setting permits only users with the relevant profile or permission set to access the app without prior authorization. After choosing this option, you can manage profiles for the app by editing each profile’s Connected App Access list or by editing each permission set’s Assigned Connected App list.
You cannot manage individual user access with profiles in a Group Edition org. However, you can control all users’ access by modifying the OAuth settings of a connected app.
Beyond configuration, it’s essential to understand API Access Control's strategic impact and how it reinforces a data-first security model.

Technical deep dive: why API Access Control works
Salesforce’s API Access Control is a strategic shift toward data-first security. By gating API connections and enforcing manual trust validation, Salesforce is helping organizations move away from perimeter-based defenses and toward Zero Trust and least privilege principles.
Here’s how it works and why it matters:
- IP Restriction: When admins install a new application, they can take the third-party app's known IP range and only allow it to connect from that specified range, reducing the potential impact of the third-party provider being attacked.
- Connection gating: Apps must be installed before they can be unblocked. This prevents drive-by API connections and forces a deliberate installation process. It’s a simple but powerful way to reduce exposure to rogue OAuth flows.
- User-level access control: Admins can restrict API access to specific users. This minimizes the attack surface if an app is compromised — a critical capability when attackers increasingly log in with stolen credentials.
- Manual trust validation: Unblocking an app is a deliberate action, not a default. This gives admins time to vet app behavior, permissions, and risk before granting access. It’s a shift from reactive to proactive security.
- Baseline enforcement: Salesforce is moving toward making this behavior the default for all orgs. That means a stronger security posture across the board — even for teams that have yet to adopt a Zero Trust model.
This layered defense aligns with Varonis’ core belief: data is where the damage happens, and protecting it requires more than just perimeter defenses. API Access Control helps enforce the least privilege at the integration layer, a critical blind spot in many environments.
These changes don’t just affect admins; they reshape the experience for everyday Salesforce users, too.
How this affects Salesforce end users
If you’re a Salesforce user, here’s what API Access Control means for you:
- Newly installed apps will now require pre-authorized users.
- You might see fewer apps available at first. That’s because unmanaged apps are now blocked by default. If you try to connect to an app that doesn’t work, it’s likely waiting for admin approval.
- App access isn’t automatic anymore. Even if you’ve used an app before, it may need to be reinstalled and approved under the new policy. This helps keep your environment secure.
- Admins are your go-to for access. If you need a specific app to do your job, contact your admin with the app name and why you need it. They’ll review and approve access if it’s safe.
- Security is a team effort. These changes help protect your organization from OAuth-based attacks. By following the new process, you’re helping keep sensitive data safe.
Tip: If you’re unsure why an app isn’t working, check with your admin before troubleshooting. API Access Control might have blocked it.

Salesforce’s message: this is the new normal
Salesforce recently announced that this behavior will become the default baseline for all organizations. That’s a significant shift from today’s opt-in model — a clear signal that the platform takes app governance seriously.
It also validates what we’ve been saying at Varonis: attackers exploit OAuth flows, and organizations need better controls to stop them.
To stay ahead of OAuth-based threats, Salesforce admins should follow this action plan:
- Review your connected apps and uninstall anything unmanaged or unused
- Set up approval workflows for new app installations
- Educate your admins and users on the new process and why it matters
Protect your Salesforce data
Whether you're an admin or end user, these changes are part of a broader shift toward proactive security.
To help you navigate it, we offer free Salesforce Data Risk Assessments. These assessments summarize your data security risks and provide actionable recommendations for simpler, safer permission structures.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







.png)

