-
 Varonis Products
Varonis ProductsSep 27, 2022
Varonis Adds Secrets Discovery for On-Prem and Cloud Data Stores
Varonis can help you scan your environments for rogue secrets exposed in files and code stored on-prem and in the cloud.

Rob Sobers
5 min read
-
 Data Security
Data SecurityJul 08, 2022
157 Cybersecurity Statistics and Trends [updated 2024]
These cybersecurity statistics for 2024 are grouped by category and include breaches, costs, crime type, compliance, industry-specific stats, & job outlook.

Rob Sobers
13 min read
-
 Data Security
Data SecurityJul 05, 2022
Ransomware Statistics, Data, Trends, and Facts [updated 2024]
Ransomware is one of the most common types of malware used in cyberattacks. Check out these comprehensive ransomware statistics, plus prevention tips.

Rob Sobers
11 min read
-
 Data Security
Data SecurityMay 20, 2022
82 Must-Know Data Breach Statistics [updated 2024]
These data breach statistics cover risk, cost, prevention and more — assess and analyze these stats to help prevent a data security incident.

Rob Sobers
11 min read
-
 Data Security
Data SecurityJan 29, 2021
What Is Cryptojacking? Prevention and Detection Tips
Learn how cryptocurrency, cryptomining and cryptojacking work — also included are tips to prevent and detect cryptojacking before it's too late

Rob Sobers
8 min read
-
 Data Security PowerShell Security Bulletins
Data Security PowerShell Security BulletinsSep 28, 2020
How Varonis Helps Stop Emotet
Our incident response team is tracking an unprecedented number of Emotet malware infections. This post will cover indicators of compromise, mitigations, and how Varonis can help you detect and stop Emotet at each phase of an attack.

Rob Sobers
6 min read
-
 Data Security
Data SecuritySep 24, 2020
Data Migration Strategy Guide: Best Practices for Success and Security
Learn best practices for your cloud migration strategy and get a step-by-step plan for a secure and effective process.

Rob Sobers
7 min read
-
 Data Security
Data SecuritySep 08, 2020
Government Hacking Exploits, Examples and Prevention Tips
In this guide, we’ll explore how governments launch attacks, the different government hacking exploits and how you can defend yourself.

Rob Sobers
10 min read
-
 Data Security
Data SecurityJun 19, 2020
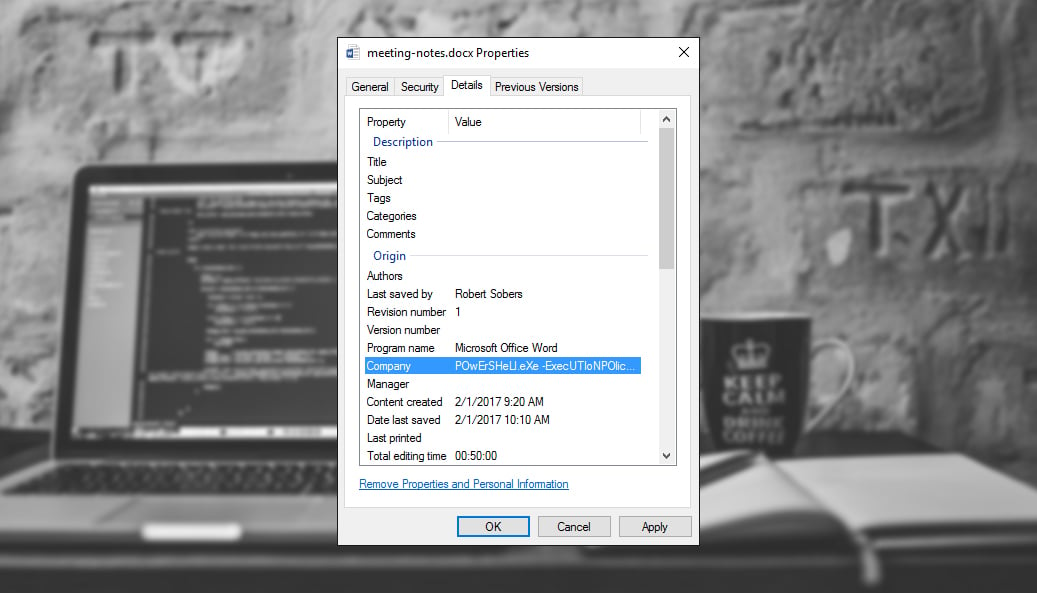
Detecting Malware Payloads in Office Document Metadata
Ever consider document properties like “Company,” “Title,” and “Comments” a vehicle for a malicious payload? Checkout this nifty PowerShell payload in the company metadata: #powershell payload stored in office metadataDocument...

Rob Sobers
1 min read
-
 Data Security
Data SecurityJun 17, 2020
Is Your Biggest Security Threat Already Inside Your Organization?
Is your company protected against insider threats? From malicious ex-employees to negligent staff, your biggest cybersecurity concern may already be inside.

Rob Sobers
1 min read
-
 Data Security
Data SecurityJun 17, 2020
Is Your Company Prepared for a Cyber Attack?
Would your company survive a cyber attack? Use our flowchart to see if your business is prepared for cybersecurity threats.

Rob Sobers
1 min read
-
 Privacy & Compliance
Privacy & ComplianceJun 17, 2020
A Year in the Life of the GDPR: Must-Know Stats and Takeaways
This review of the GDPR covers how it's changed the way industries and individuals function online through GDPR stats, fines and policies of this past year

Rob Sobers
10 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital