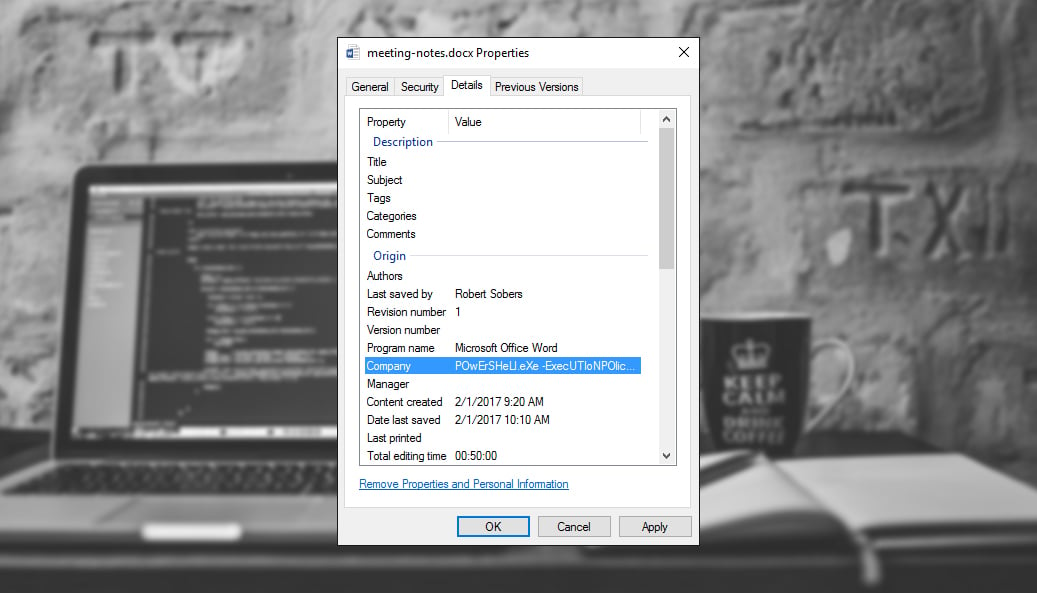
Ever consider document properties like “Company,” “Title,” and “Comments” a vehicle for a malicious payload? Checkout this nifty PowerShell payload in the company metadata:
Here’s the full VirusTotal entry. The target opens the Office document and, with macros enabled, the payload stored within the document’s own metadata executes and does its work. No extra files written to disk or network requests made.
The question about whether DatAlert can detect stuff like this came up in the Twitter thread, so I decided to write up a quick how-to.
Get a Free Data Risk Assessment
Finding Malicious Metadata with Varonis
What you’ll need: DatAdvantage, Data Classification Framework, DatAlert
Step 1: Add Extended File Properties to be scanned by Data Classification Framework.
- Open up the Varonis Management Console
- Click on Configuration → Extended File properties
- Add a new property for whichever field you’d like to scan (e.g., “Company”)

(Note: prior to version 6.3, extended properties are created in DatAdvantage under Tools → DCF and DW → Configuration → Advanced)
Step 2: Define a malicious metadata classification rule
- In the main menu of DatAdvantage select Tools → DCF and DW → Configuration
- Create a new rule
- Create a new filter
- Select File properties → Company (or whichever property you’re scanning)
- Select “like” to search for a substring
- Add the malicious value you’d like to look for (e.g., .exe or .bat)

Step 3: Create an alert in DatAlert to notify you whenever a file with malicious metadata is discovered
- In the main menu of DatAdvantage select Tools → DatAlert
- Click the green “+” button to create a new rule
- Click on the “Where (Affected Object)” sub menu on the left
- Add a new filter → Classification Results
- Select your rule name (e.g., “Malicious Metadata”)
- Select “Files with hits” and “Hit count (on selected rules)” greater than 0

You can fill out the rest of the details of your alert rule–like which systems to scan, how you want to get your alerts, etc.
As an extra precaution, you could also create a Data Transport Engine rule based on the same classification result that will automatically quarantine files that are found to have malicious metadata.
That’s it! You can update your “Malicious Metadata” over time as you see reports from malware researchers of new and stealthier ways to encode malicious bits within document metadata.
If you’re an existing Varonis customer, you can setup office hours with your assigned engineer to review your classification rules and alerts. Not yet a Varonis customer? What are you waiting for? Get a Get a demo of our Data Security Platform today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.