For years, database activity monitoring (DAM) has been a necessary evil — an obligation driven more by checking a box than driving security outcomes or simplifying compliance. Legacy DAM vendors like Imperva and Guardium were built for a different era: one where deploying hundreds of agents and monitoring databases in isolation was considered acceptable.
The AI era demands a new approach to data security. The days of fragmented data security products are over. Now, users and DBAs are not the only ones accessing databases. AI agents can directly query databases and execute actions autonomously, thereby exponentially increasing the risk of a data breach. In the AI era, database security is of the utmost importance.
The problem with traditional DAM
Legacy DAM solutions are plagued by complexity and manual overhead. They take years to deploy and require hardware and multiple FTEs to operate. Even when deployed successfully, legacy DAM rarely provides more than a compliance checkbox. They offer limited visibility and struggle to correlate activity with real identities. As a result, security teams are left in the dark, unable to detect threats or enforce meaningful policies.
Legacy DAM vs Next-Gen DAM at a glance
As you can see below, next-gen DAM doesn’t just streamline operations; it transforms database security into a proactive, outcome-driven capability.
Manual log parsing
Automated insights
Mostly compliance-foucsed
Siloed database monitoring
A new approach: Agentless, cloud-native DAM
Next-generation DAM is radically different. Varonis Next-Gen DAM is architected from the ground up to overcome the challenges inherent in legacy DAM solutions:
- Agentless: No more fragile agents or appliances. Monitor thousands of databases — cloud, on-prem, managed, or unmanaged — with nothing to install, manage, or upgrade.
- Scalable: Deploy in weeks, not years. Scale effortlessly across thousands of databases. No appliances to manage, no database upgrades to coordinate, no FTEs to dedicate.
- Unified: Integrated into Varonis’ leading Data Security Platform for complete visibility and control across your entire data estate.
Activity monitoring
Capture every database query, transaction, and access event in the cloud or on-premises, with a complete audit trail of who accessed which data, when, and how.
Monitor every query, transaction, and access event
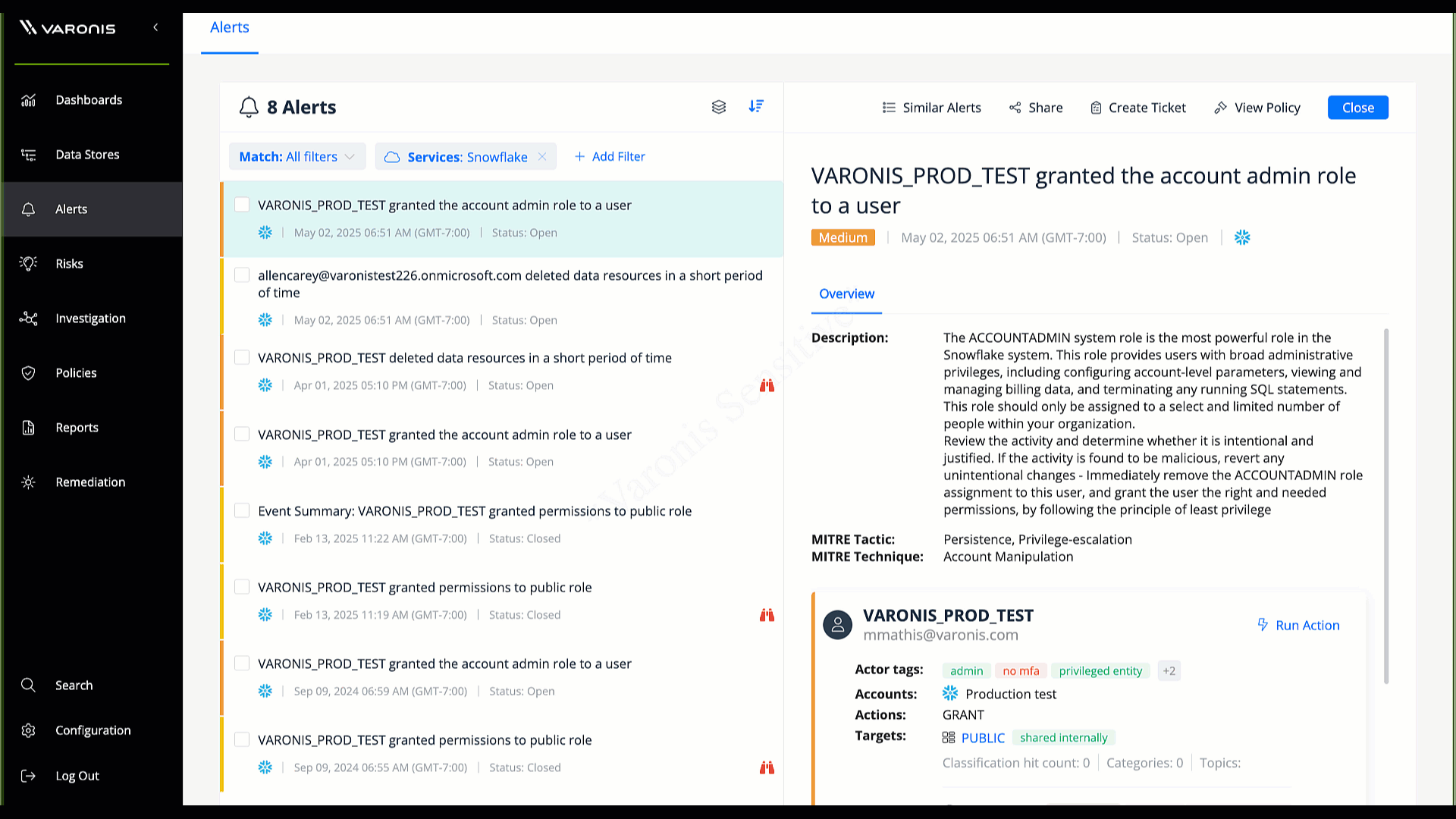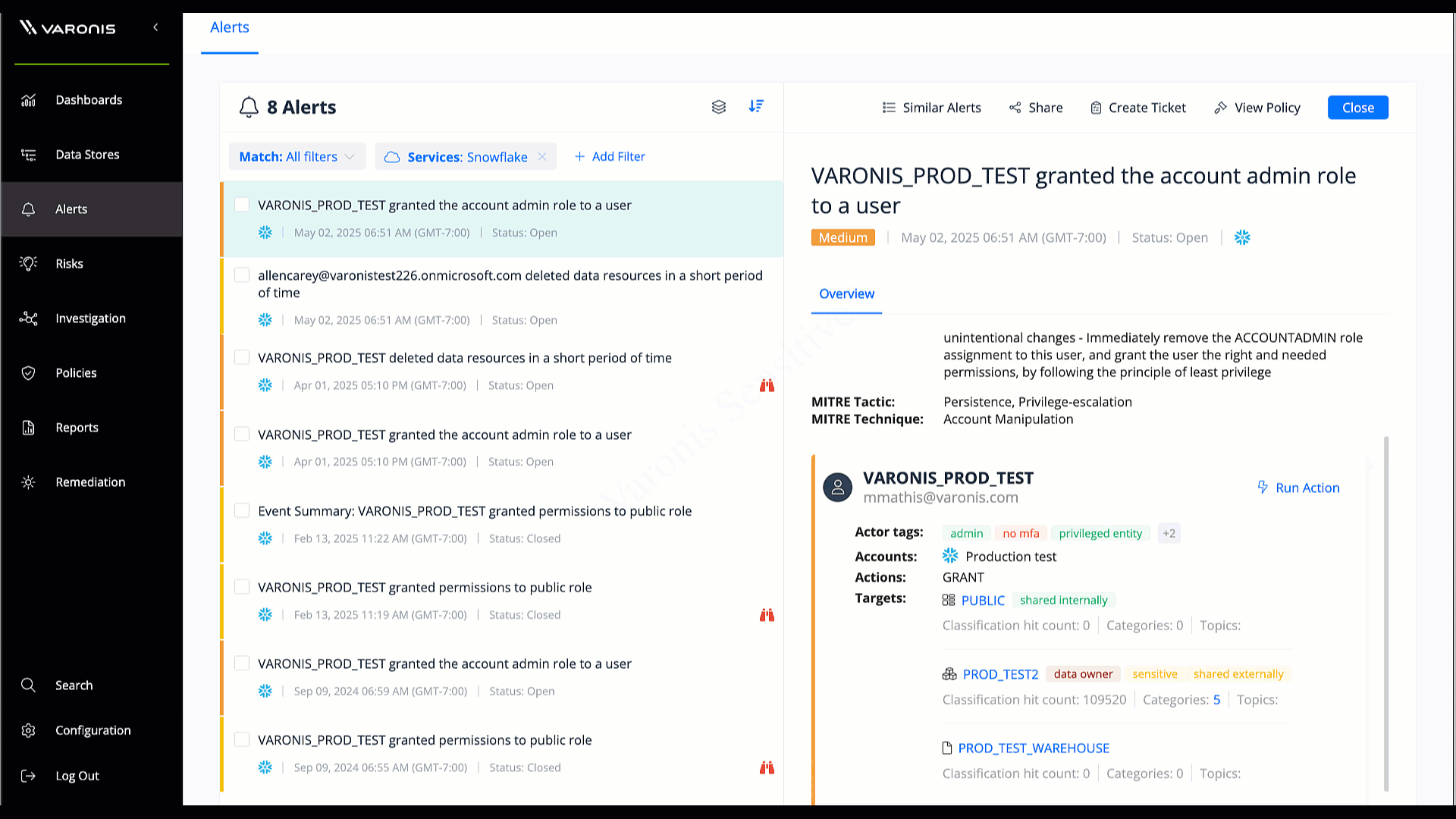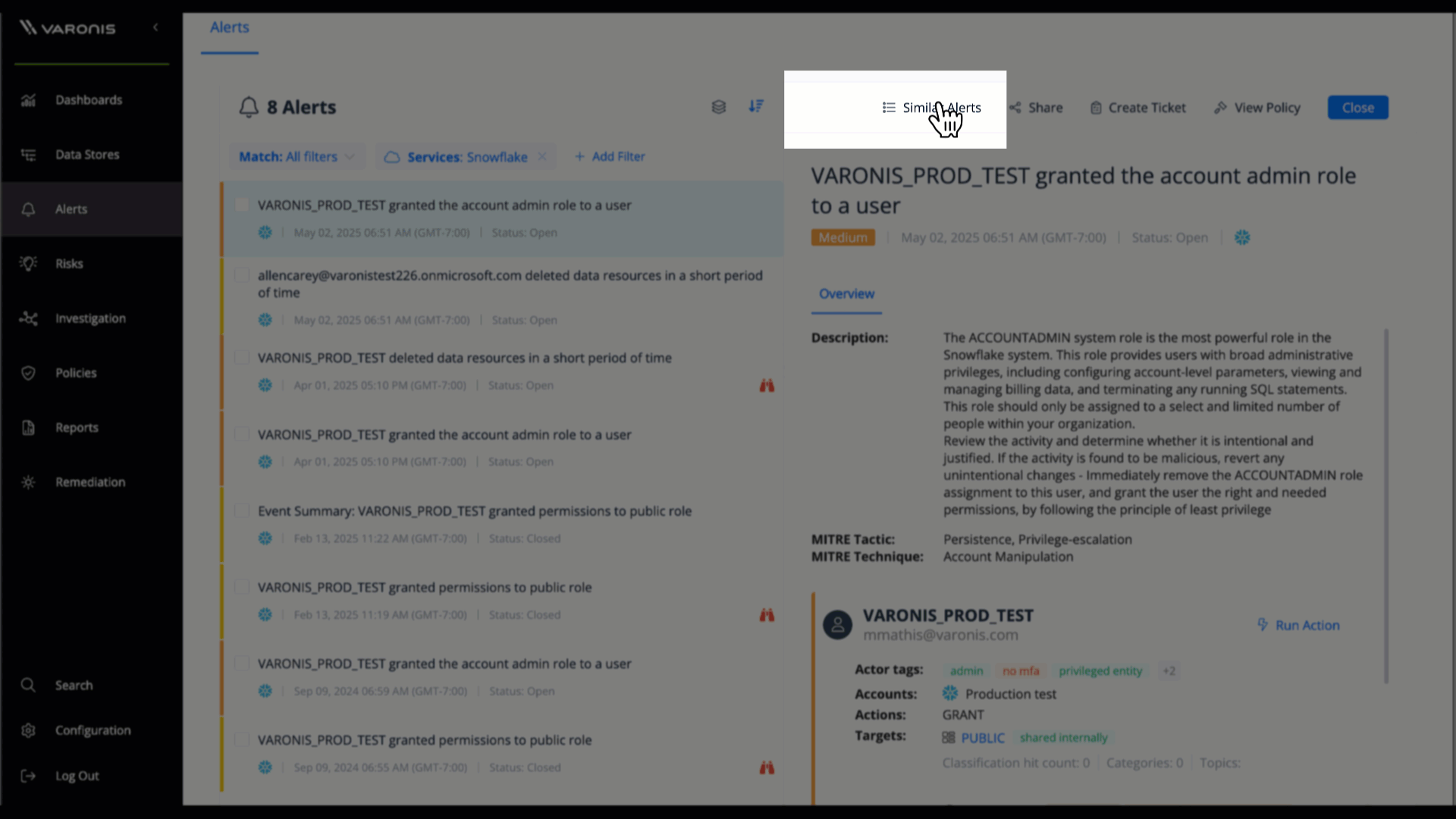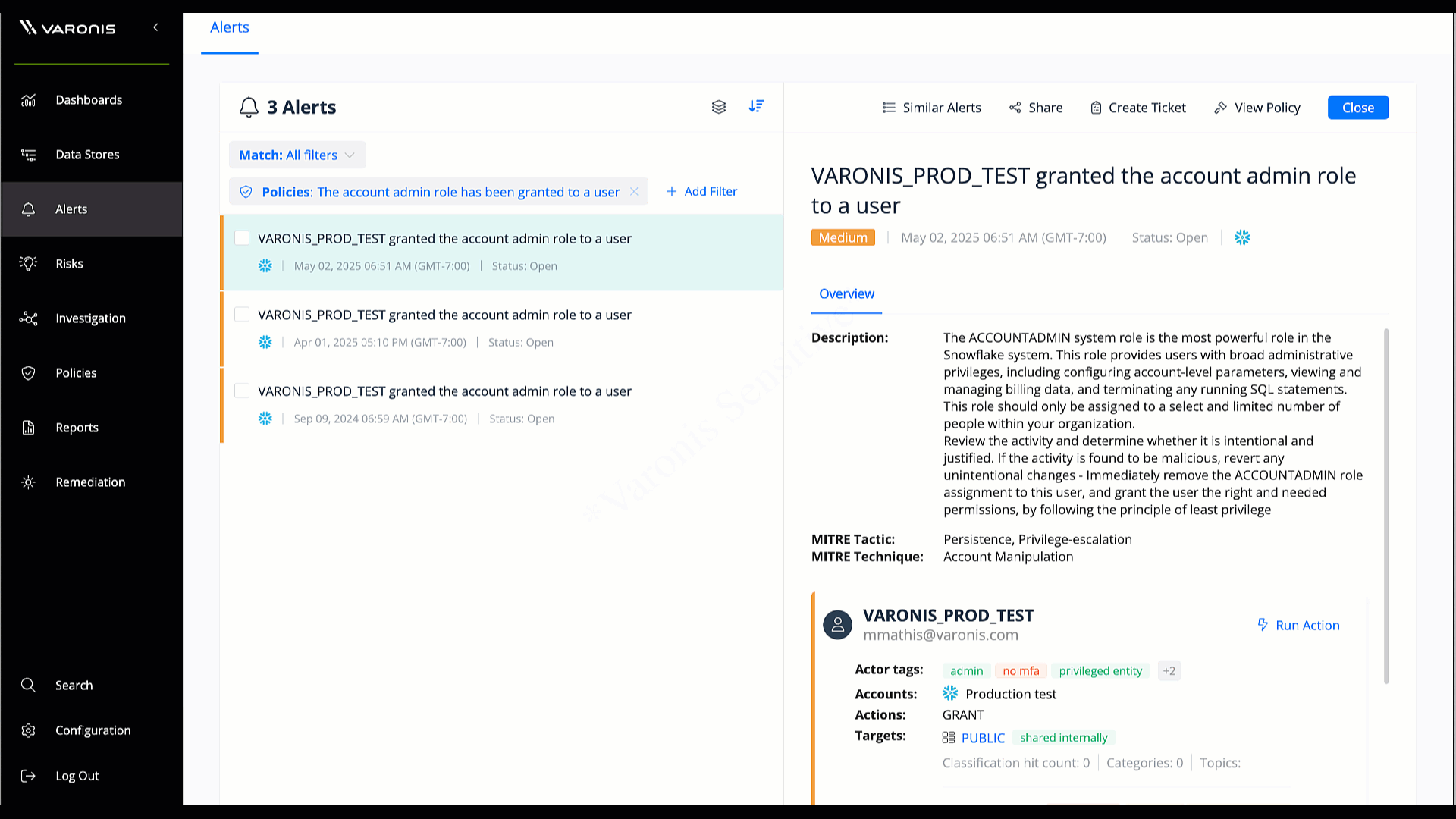
Monitor every query, transaction, and access event
Data discovery and classification
Understand which databases contain your most sensitive data and determine what’s exposed, at risk, or inactive.
Identify sensitive data automatically
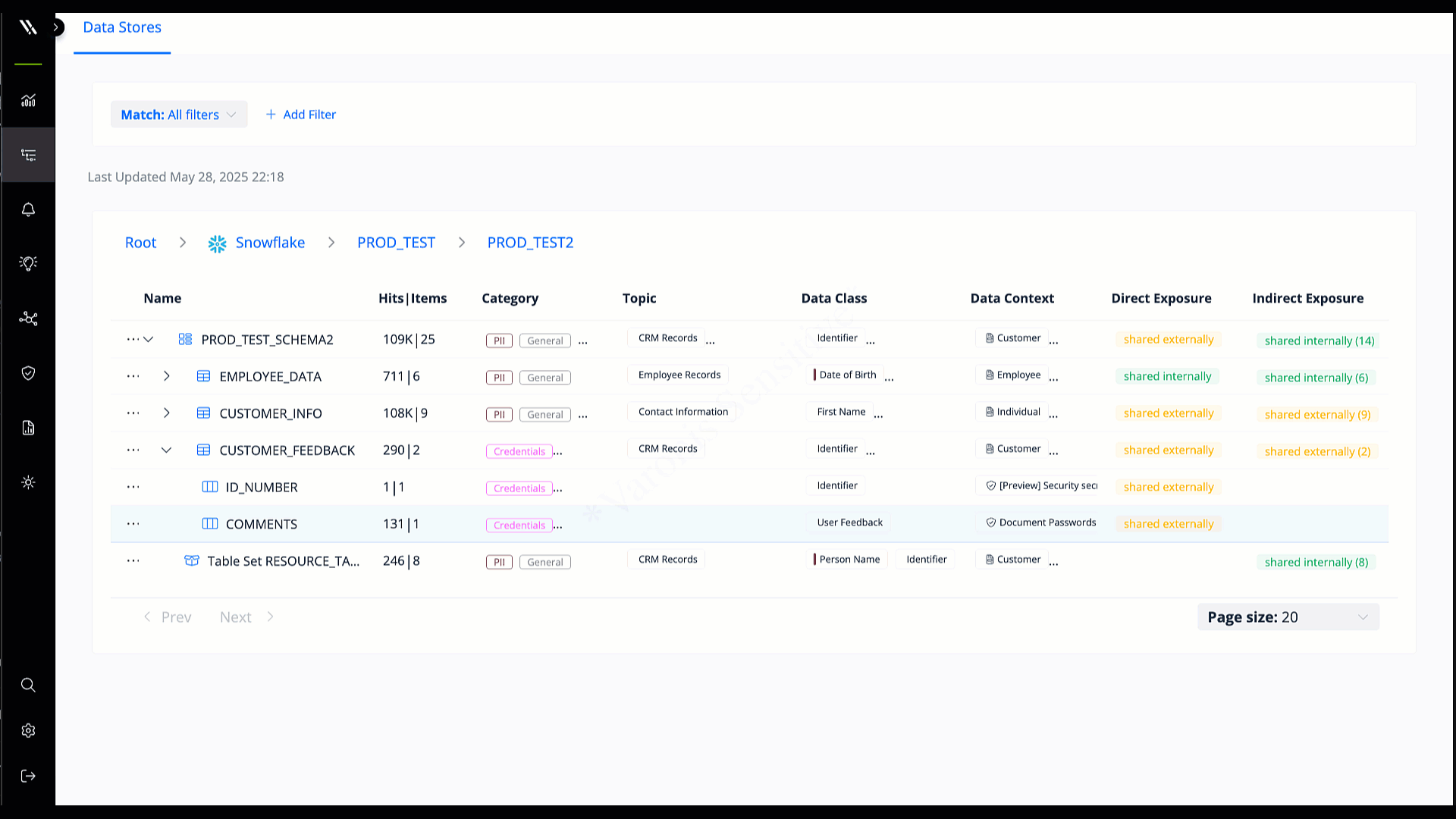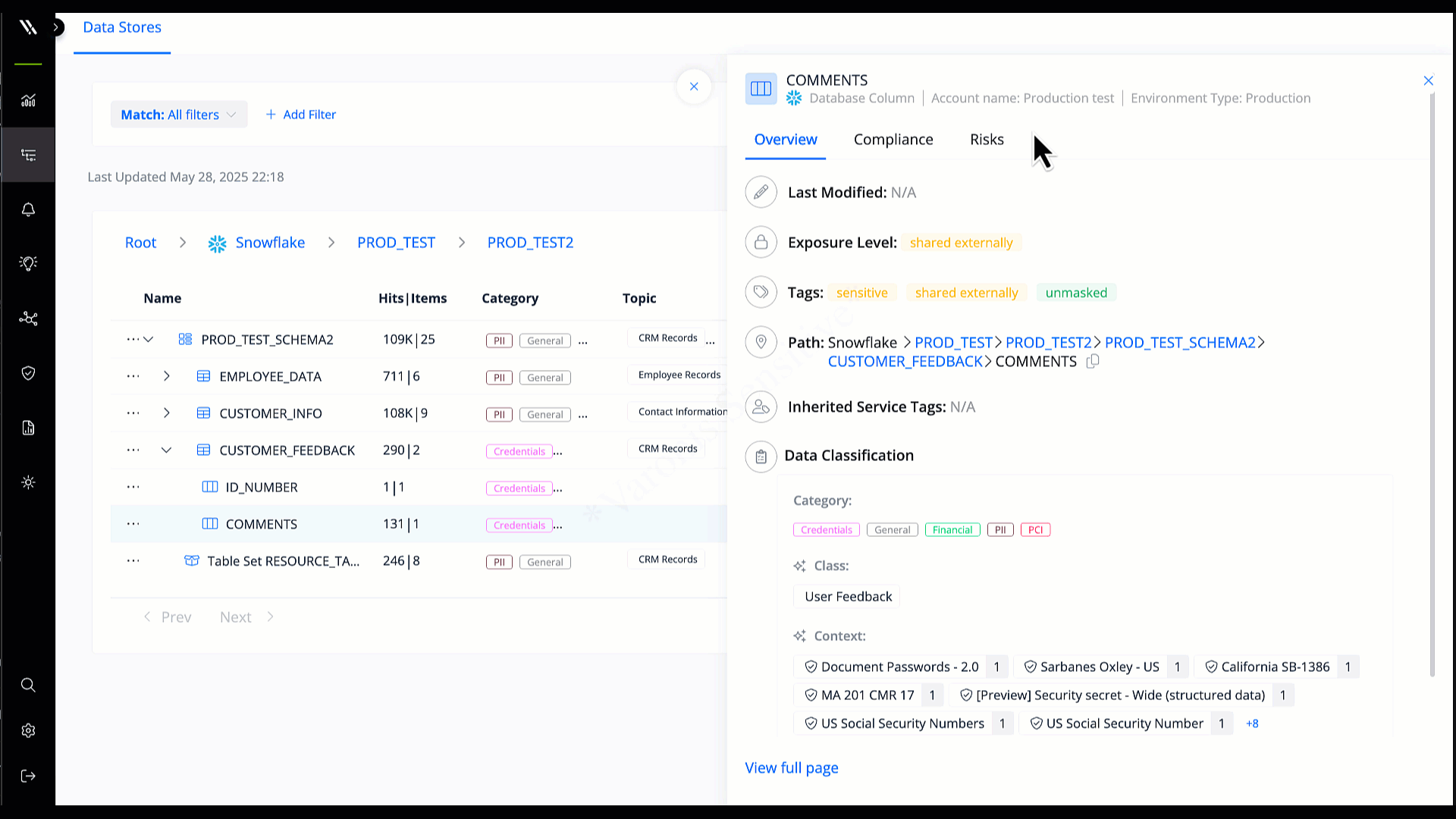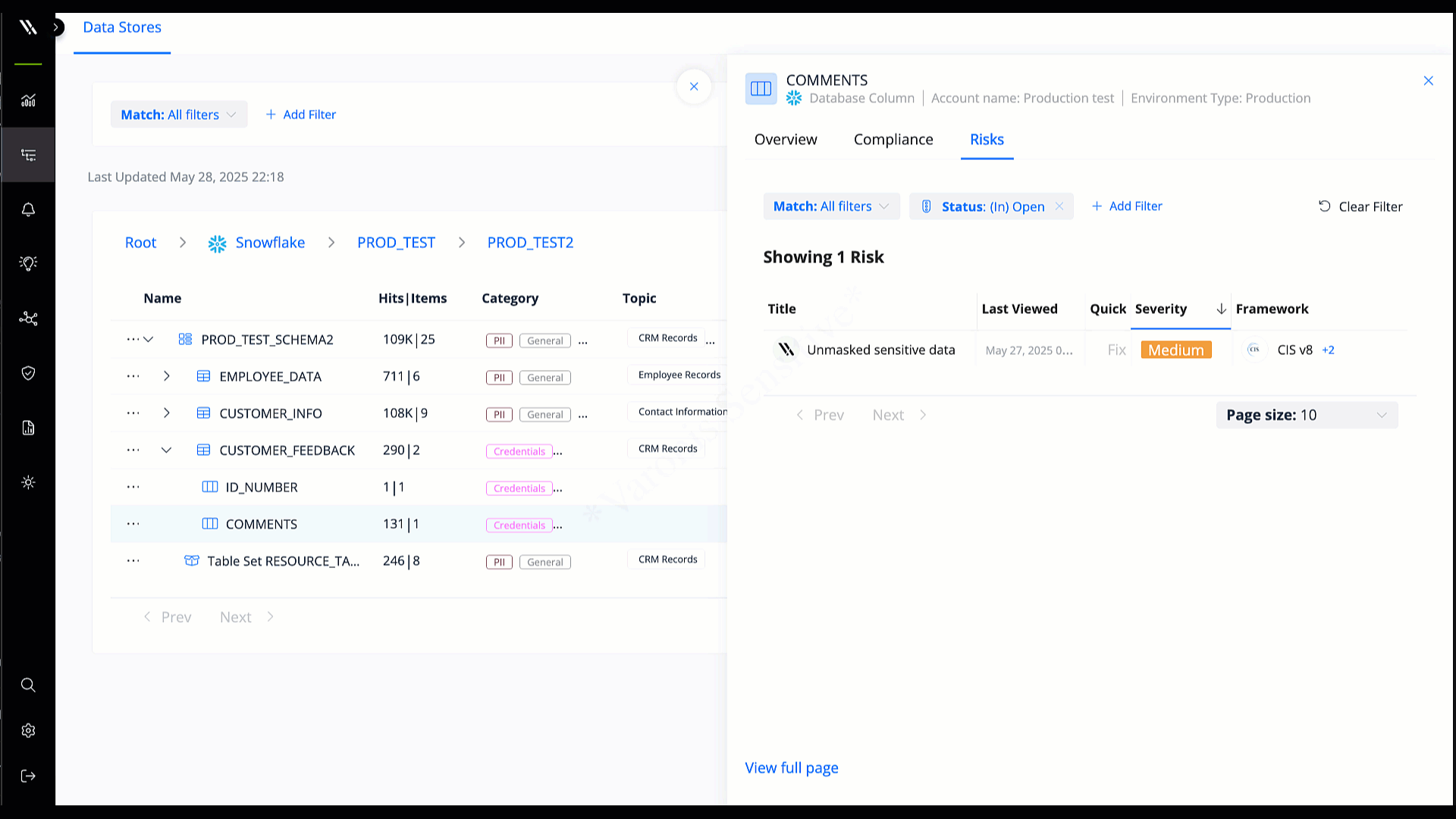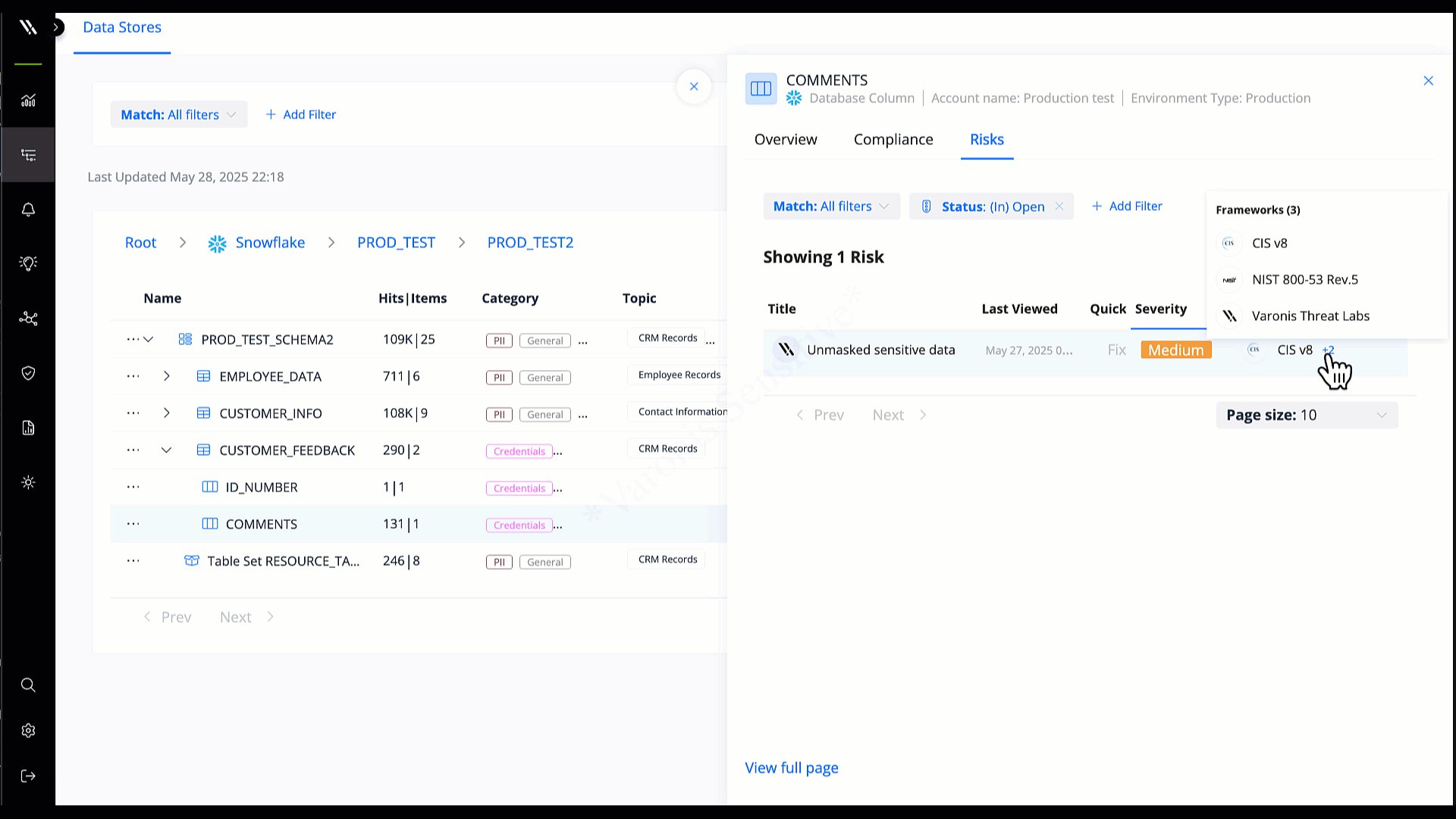
Identify sensitive data automatically
Identity protection & access control
Connect database permissions to corporate identities for a complete picture of which users, apps, and agents can read, modify, or delete critical data.
Determine effective access in one click and right-size automatically
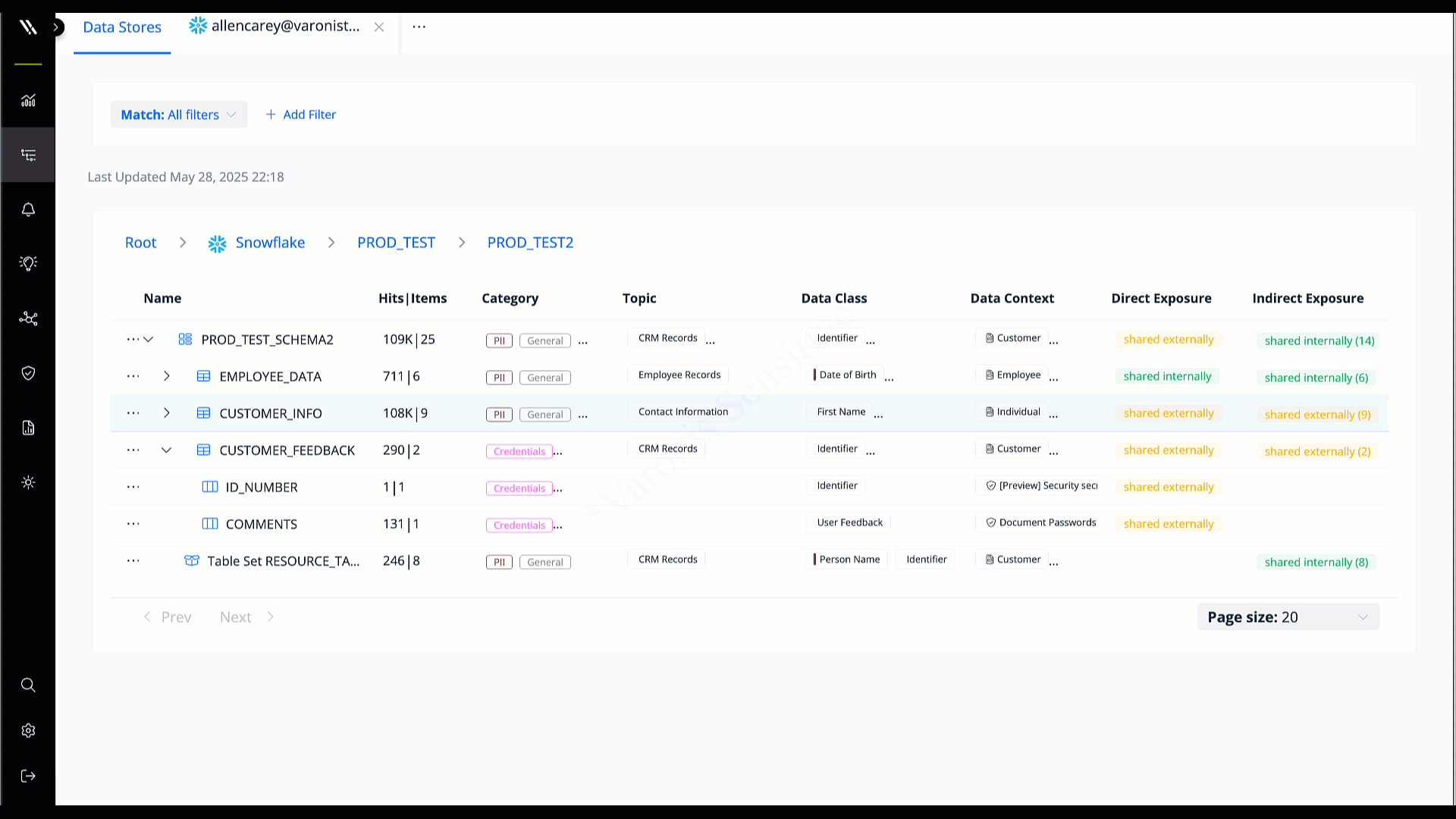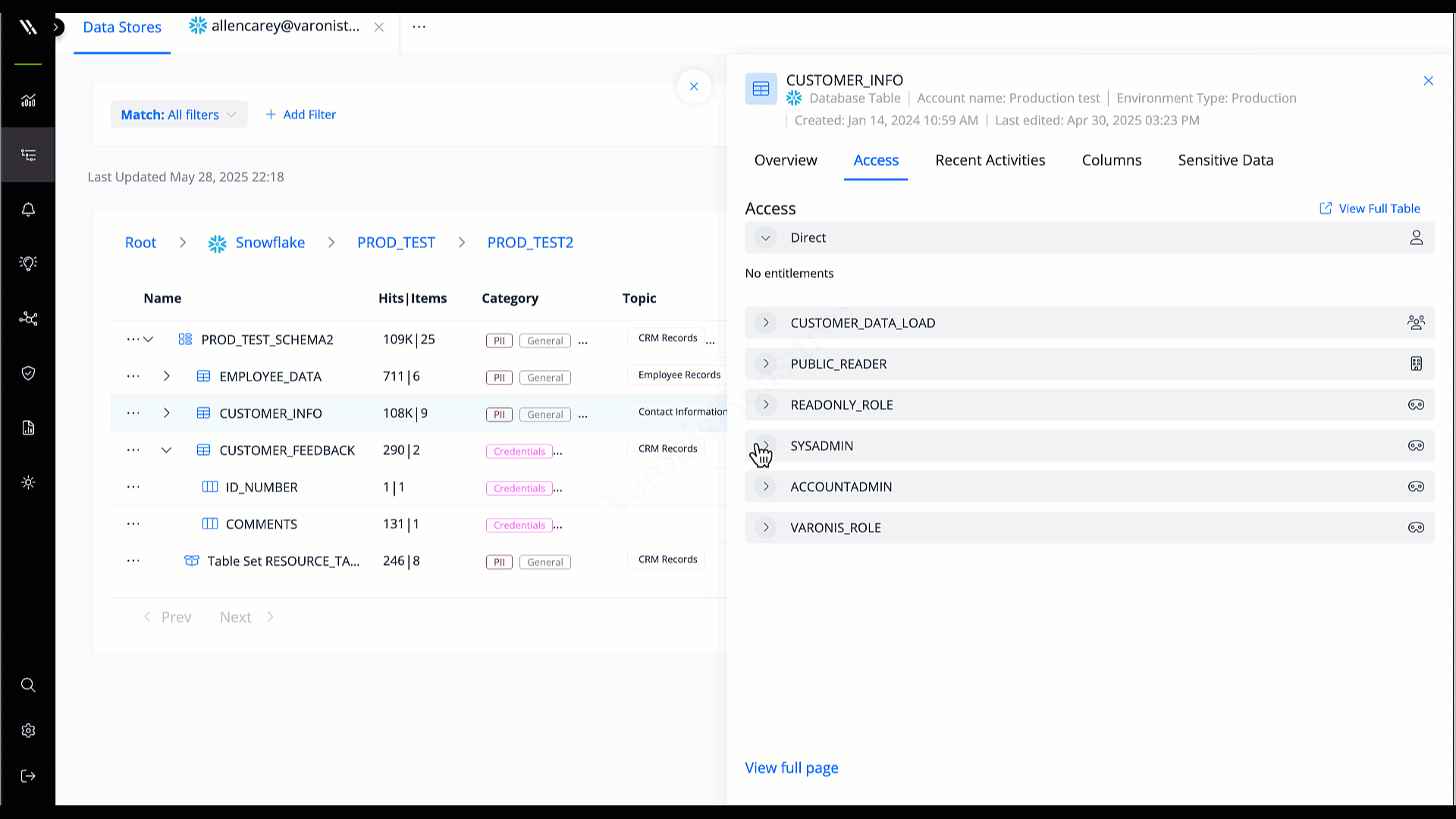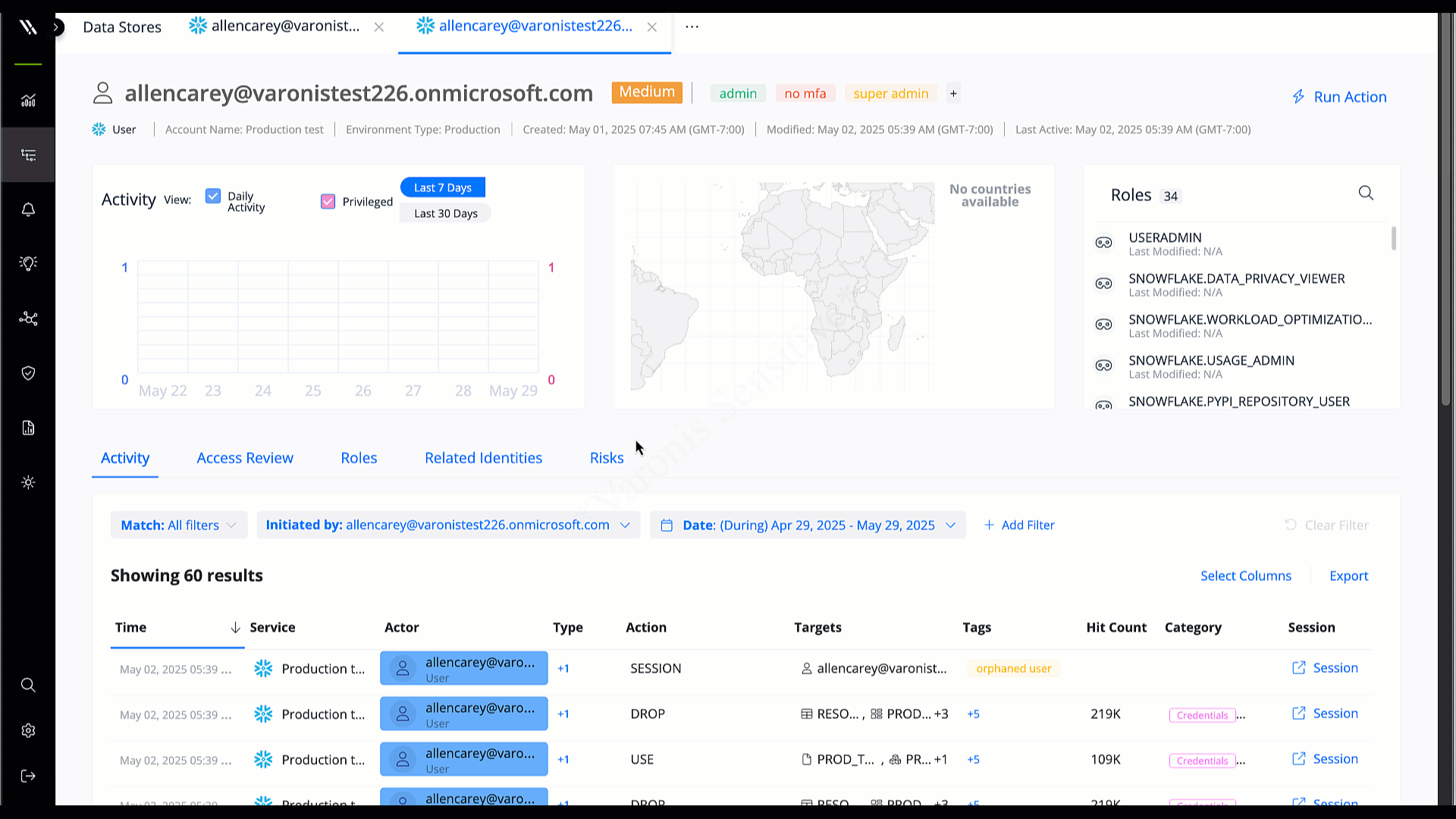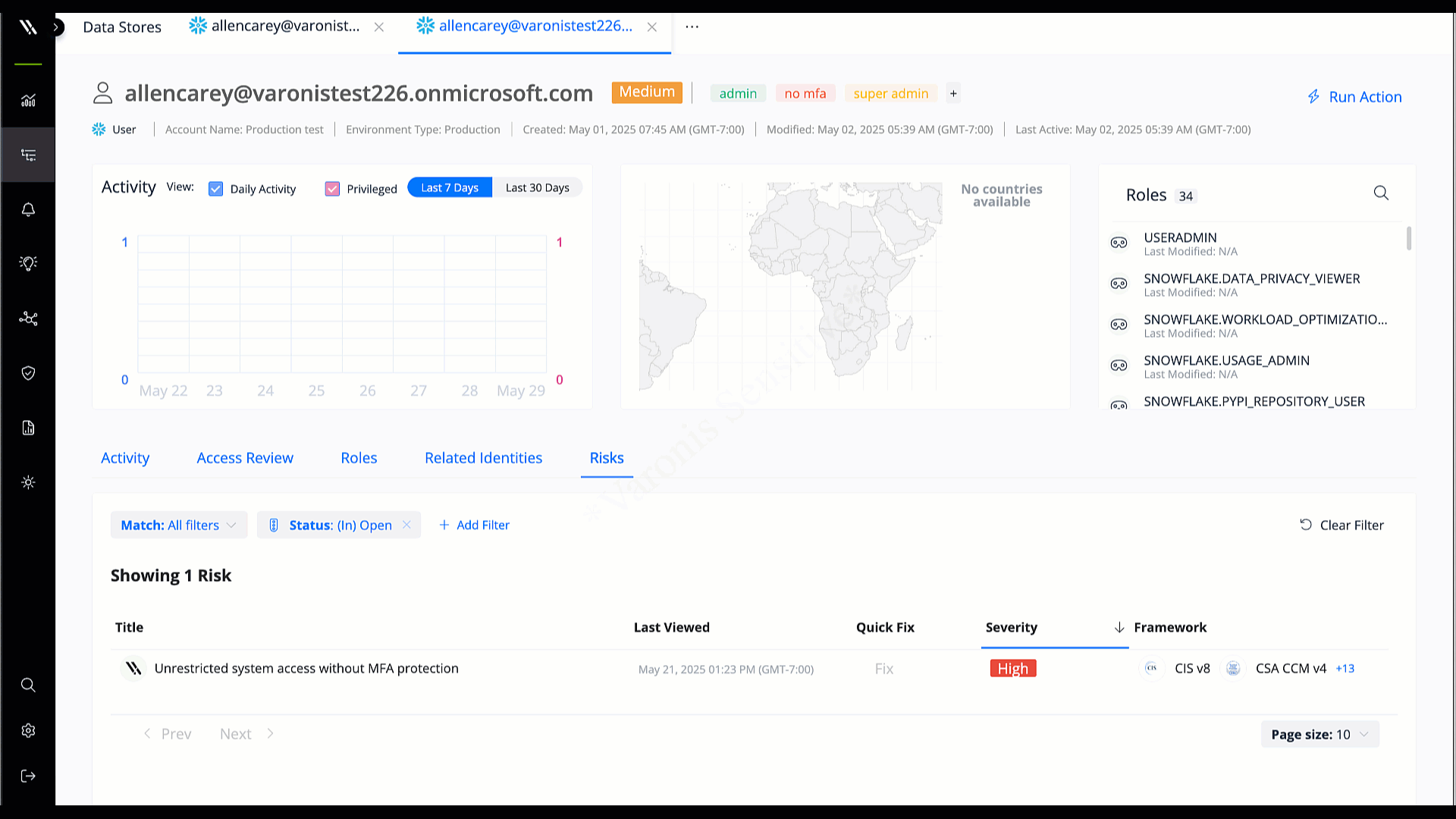
Determine effective access in one click and right-size automatically
Automated remediation
Revoke excessive permissions, mask sensitive data, and enforce other security policies automatically. Reduce time to resolution and ensure that your data is secure.
Fix misconfigurations with a few clicks or automatically
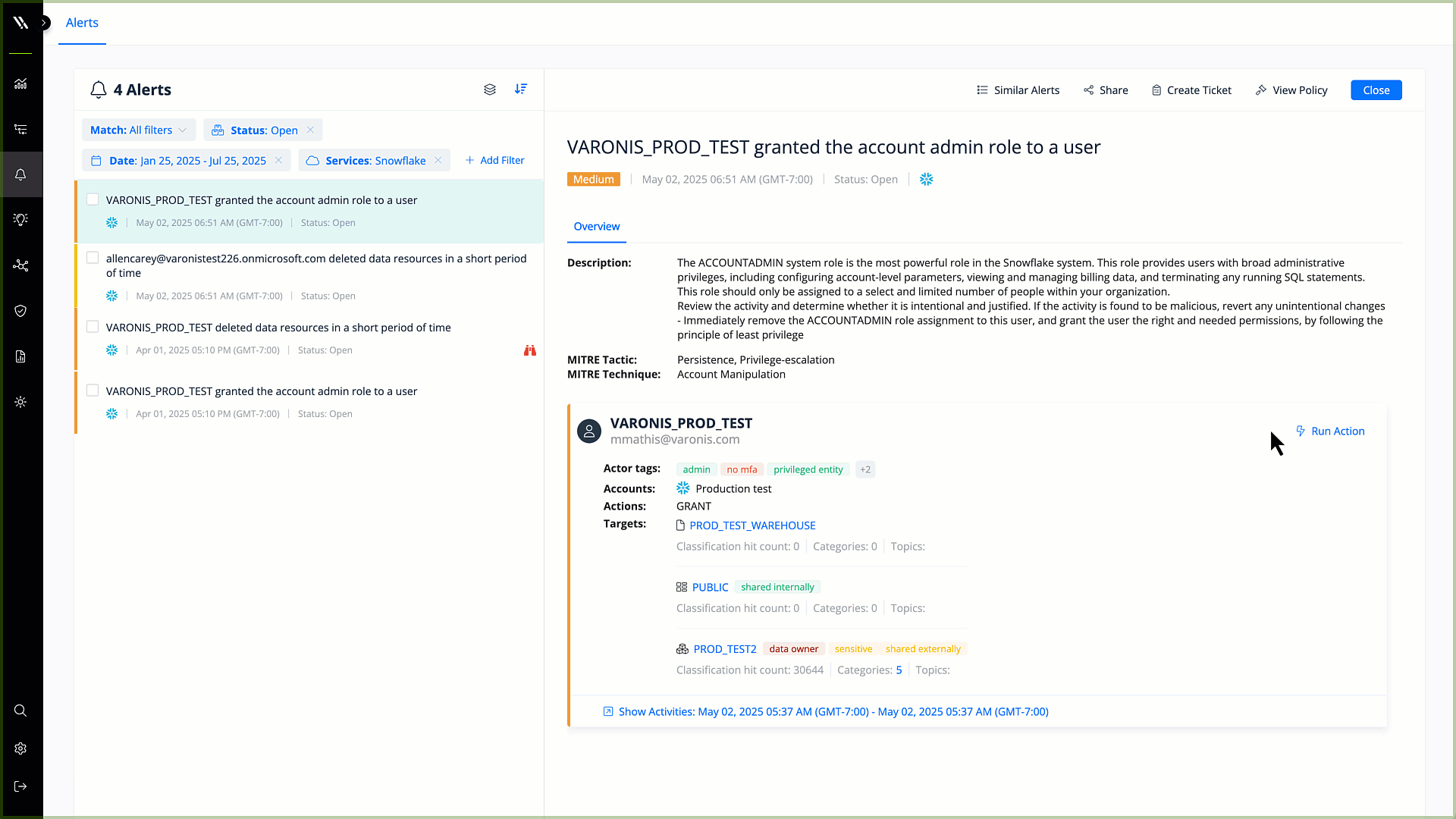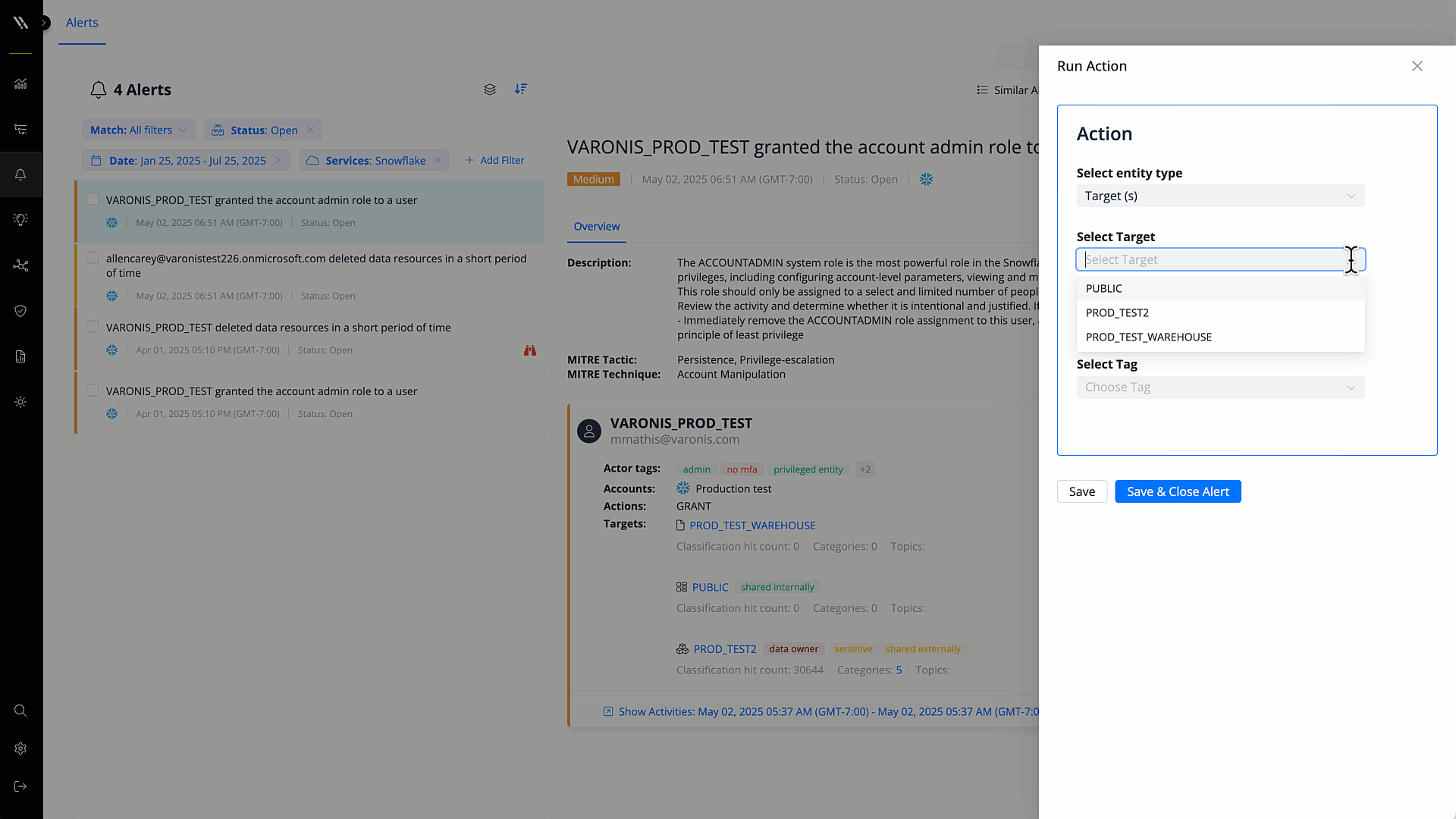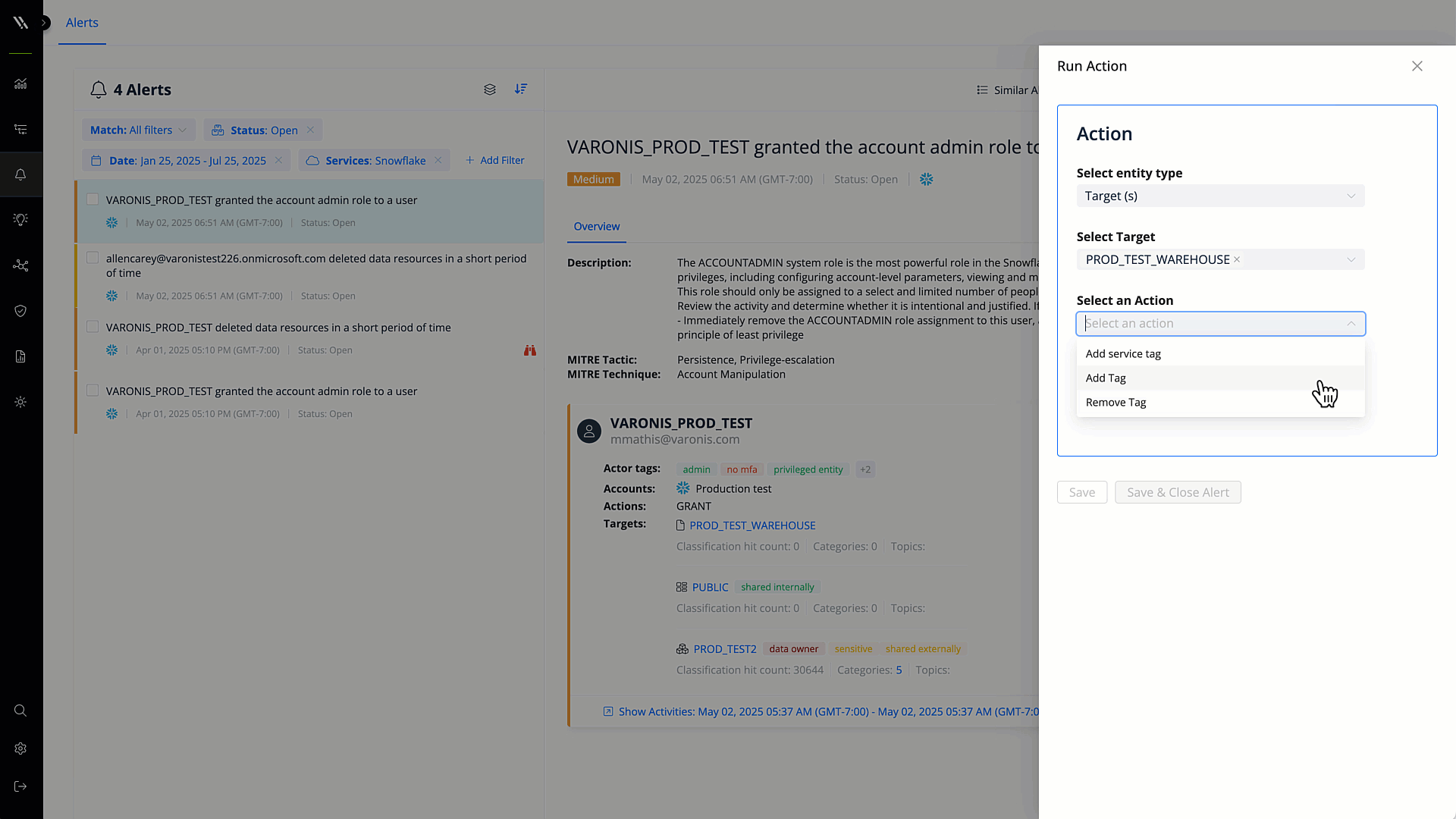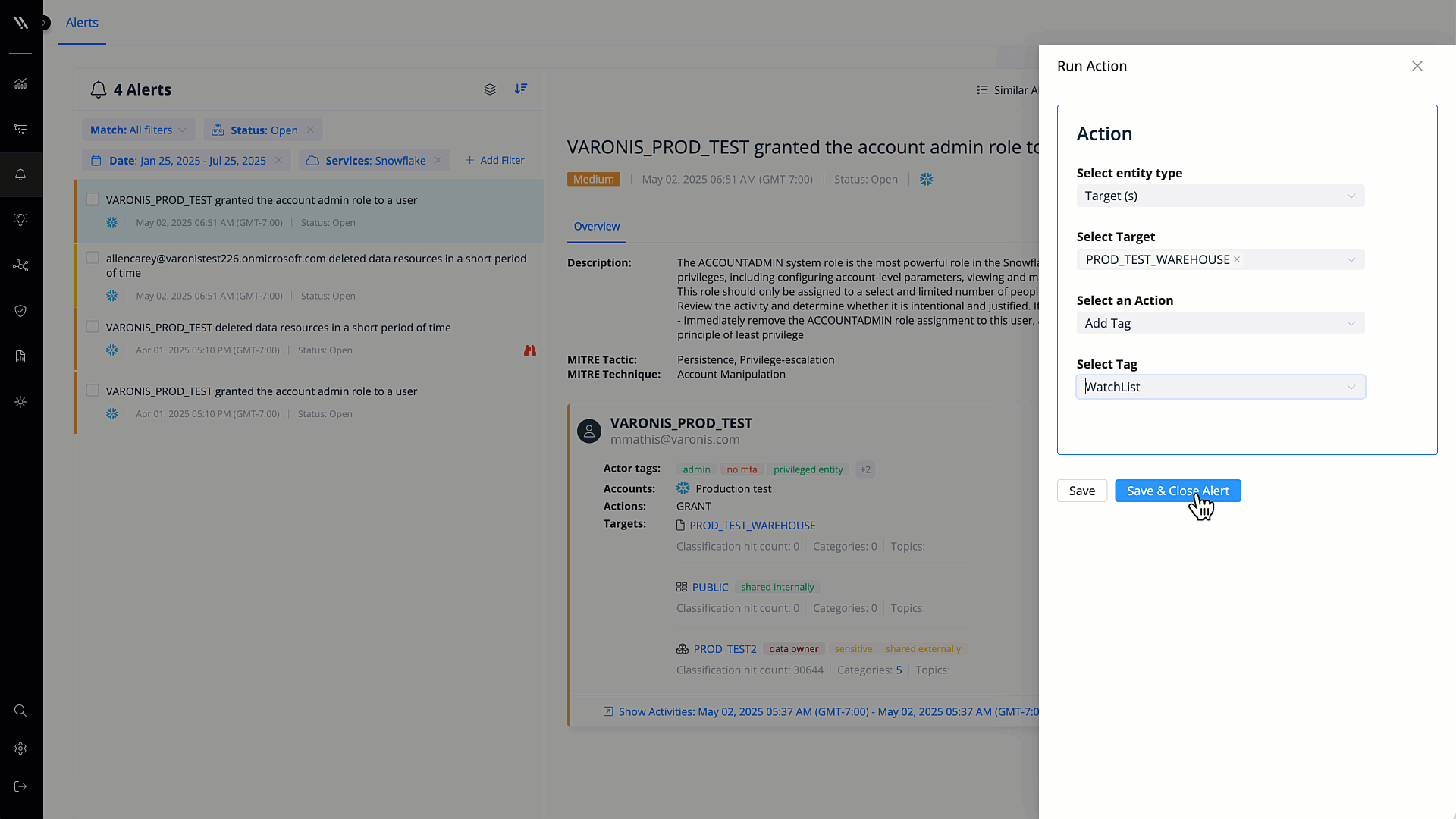
Fix misconfigurations with a few clicks or automatically
User and entity behavior analytics
UEBA creates a behavioral baseline for user activity to detect abnormal behavior and insider threats. Only UEBA can detect high-fidelity threats, like when a bad actor with stolen credentials is moving laterally across the environment and block suspicious activity and sensitive data exfiltration attempts.
Detect and remediate threats automatically
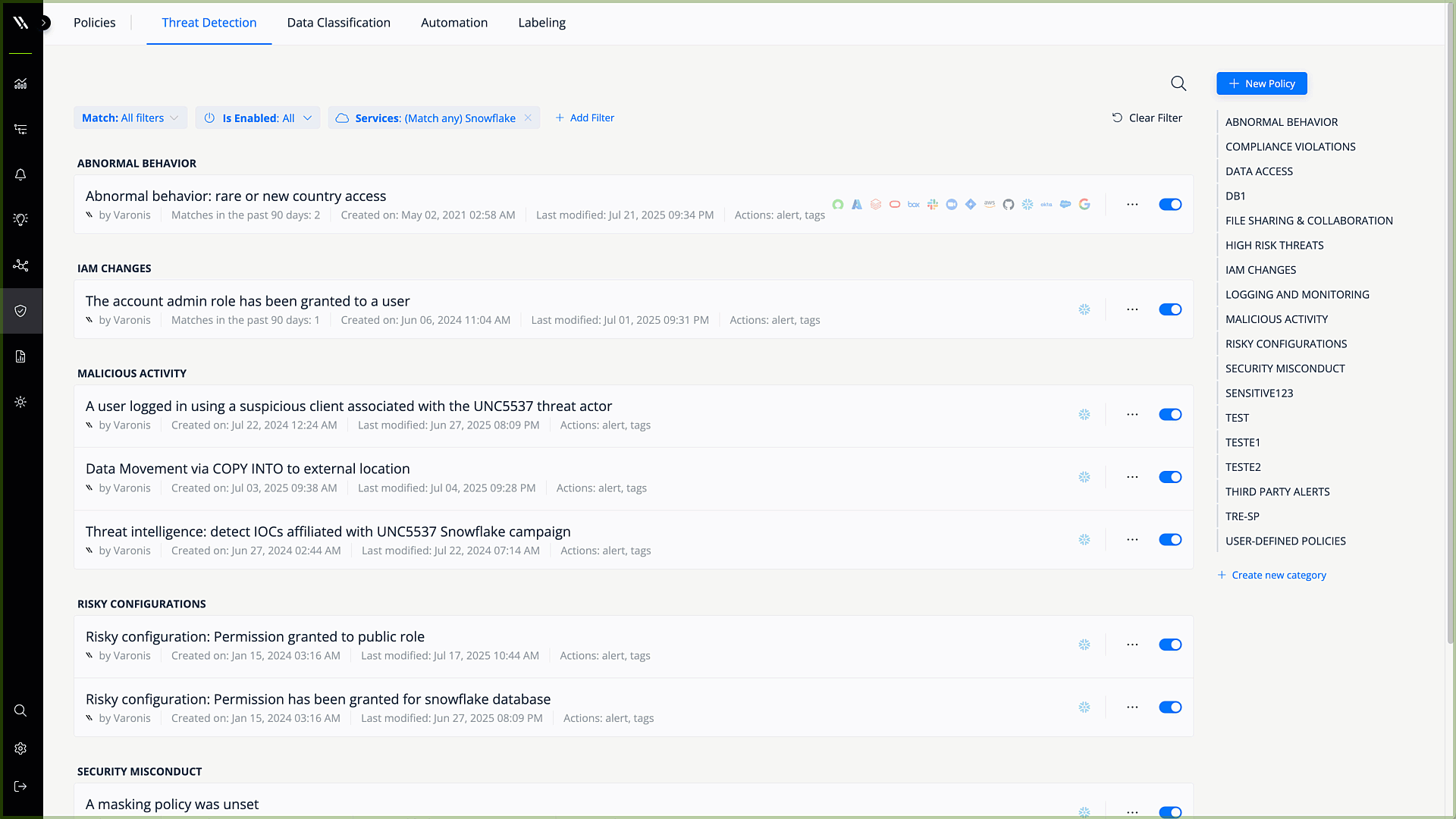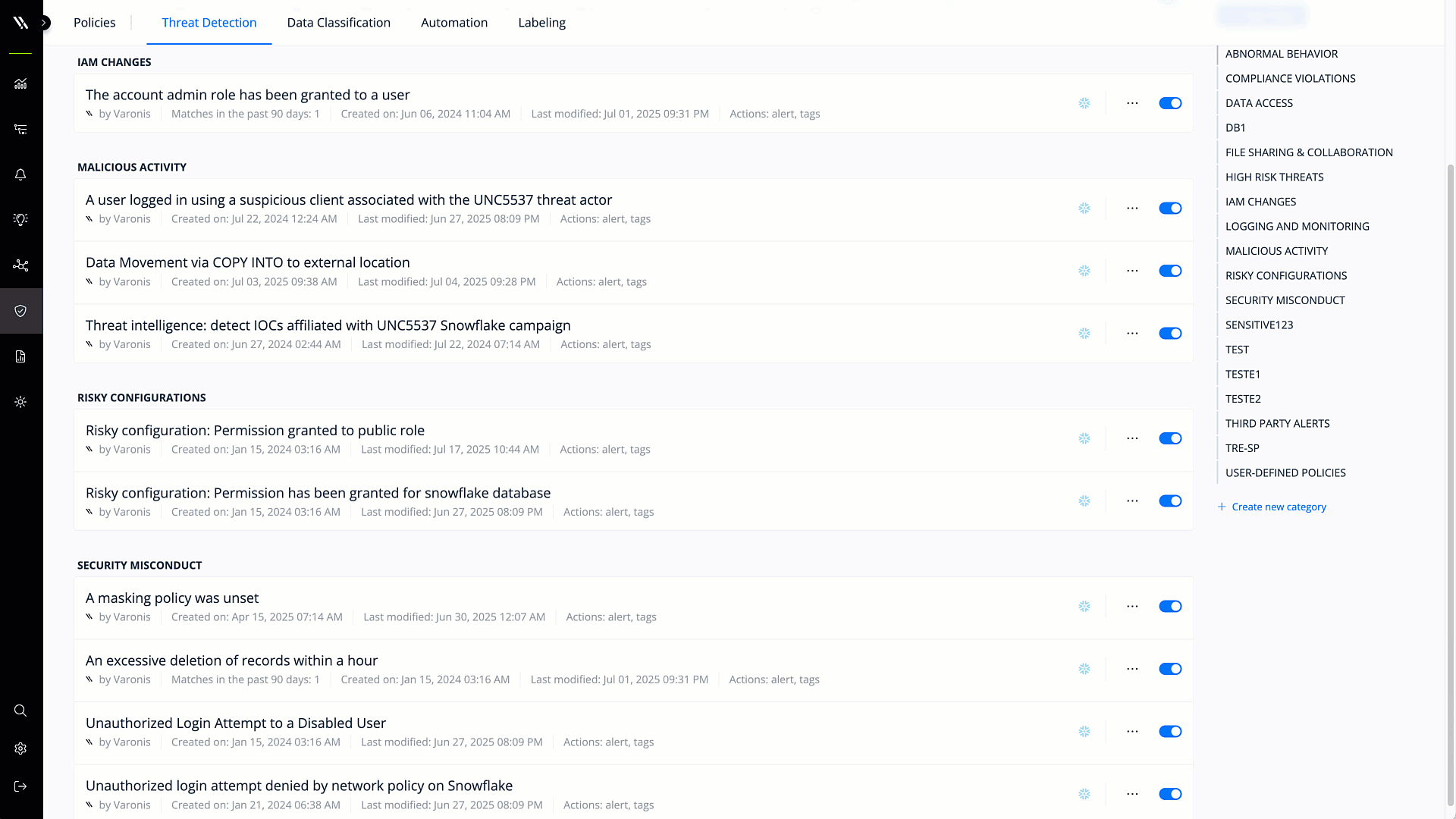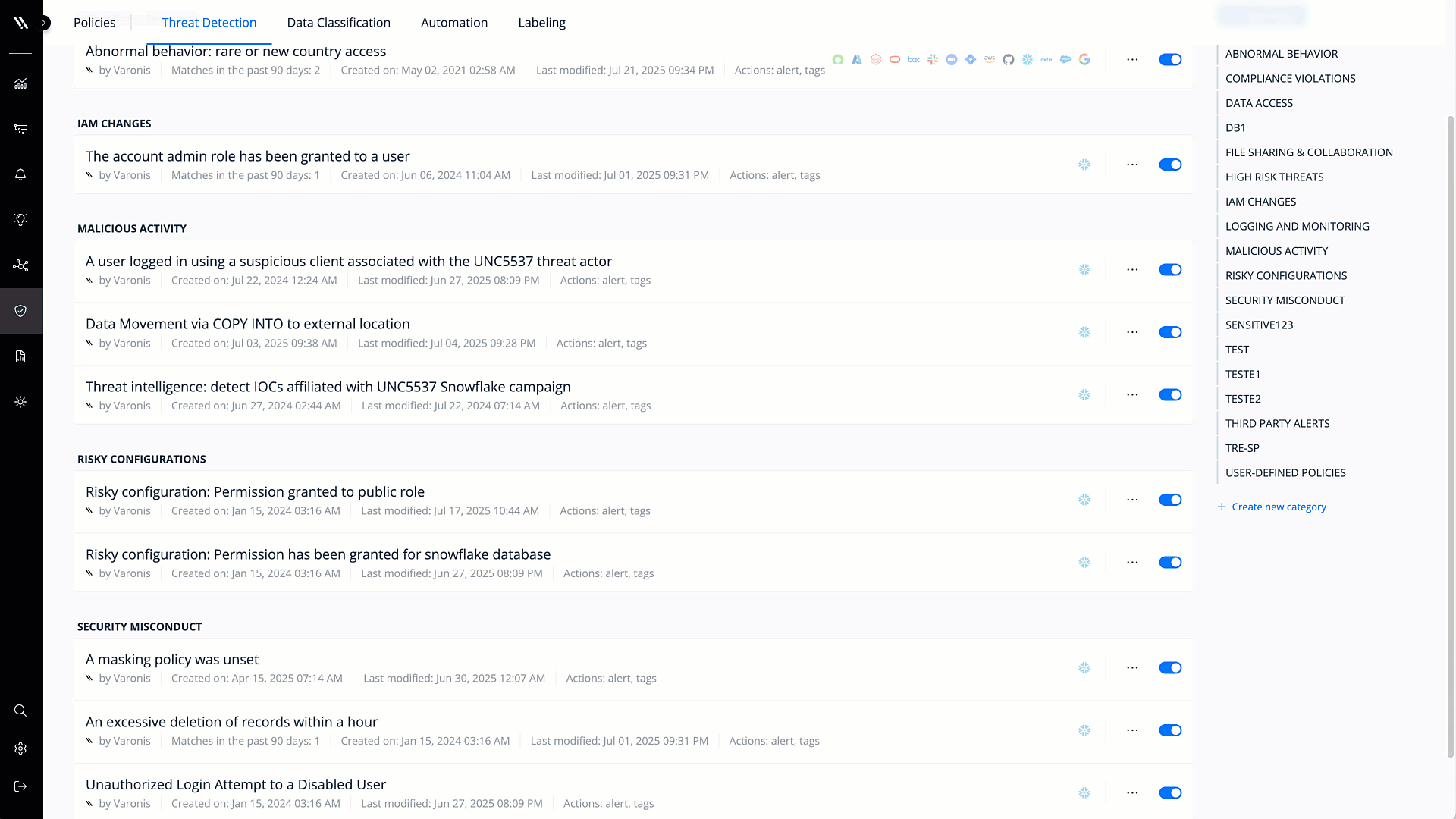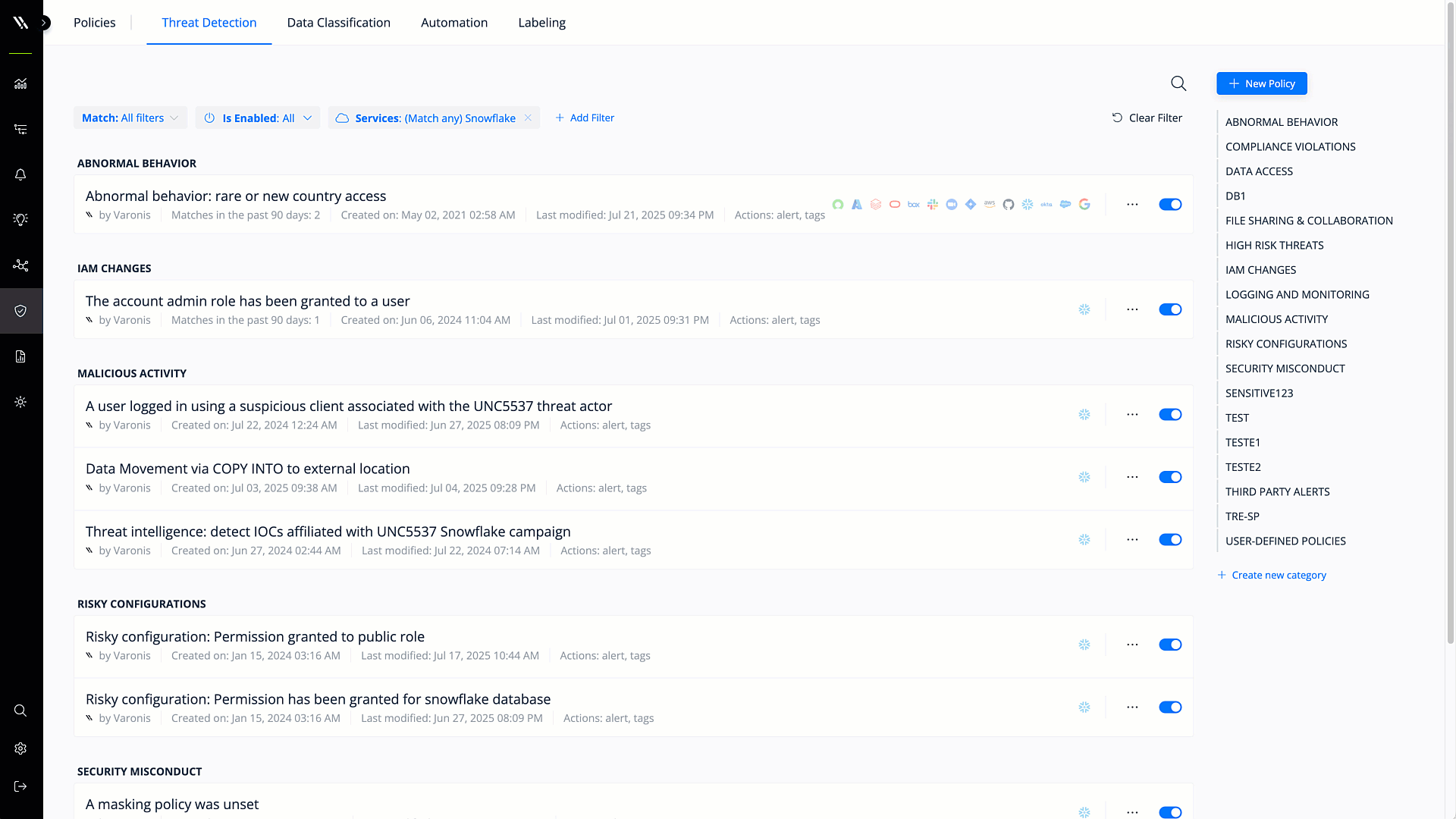
Detect and remediate threats automatically
Unified data security
Varonis Next-Gen DAM provides unified visibility, security, and control across all data stores and applications as part of our broader Data Security Platform. With Varonis Next-Gen DAM, database security is no longer the domain of DBAs and a blind spot for security teams. Instead, security teams have a single pane of glass to understand the security of their data wherever it resides: structured or unstructured, in the cloud or on-premises, and across dozens of business-critical applications.
Want to see Varonis Next-Gen DAM in action? Schedule a demo today.
FAQs about database activity monitoring (DAM) solutions
How does next-gen Database Activity Monitoring (DAM) differ from legacy solutions?
Next-gen DAM offers a modern, agentless approach that overcomes the complexity and high overhead of legacy systems. Unlike traditional DAM, which can take years to deploy and requires dedicated hardware, next-generation solutions are cloud-native, scalable, and deploy in weeks. This allows for faster implementation and provides unified visibility across the entire data estate, not just isolated databases.
What are the main benefits of an agentless DAM solution?
It eliminates the need to install and manage fragile agents on every database, significantly reducing operational overhead. Agentless DAM also simplifies deployment across thousands of databases, whether they are on-premises, in the cloud, or managed services. As a result, organizations can scale their security efforts more efficiently without coordinating database upgrades or dedicating specialized teams to manage the monitoring infrastructure.
What security capabilities does next-gen DAM provide beyond basic monitoring?
Next-gen DAM goes beyond activity monitoring by delivering advanced, integrated security capabilities.
- Automated data discovery and classification. Identifies where sensitive data resides and highlights what’s exposed or at risk.
- User and Entity Behavior Analytics (UEBA). Detects abnormal behavior and insider threats by establishing a baseline of normal activity.
- Automated remediation. Automatically revokes excessive permissions and blocks suspicious activity in real-time to reduce data risk.
Together, these capabilities strengthen database security and reduce the window of exposure.
How does modern DAM help organizations meet compliance requirements?
Modern DAM solutions provide a complete and unalterable audit trail of all database activities, capturing every query, transaction, and access event. This detailed visibility helps organizations prove compliance with regulations like SOX, HIPAA, and GDPR. By integrating with a broader Data Security Platform, it also helps enforce policies automatically. Access controls and data handling procedures align more reliably with regulatory mandates as a result.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company: