
Michael Buckbee
Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.
-
 Privacy & Compliance
Privacy & ComplianceMar 29, 2020
What is FISMA Compliance? Regulations and Requirements
FISMA is the federal government’s security requirements. If you work for on with a federal agency read on to learn how to get (and stay) compliant.

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Kerberos Authentication Explained
Learn more about Kerberos Authentication, the widely-used authorization technology. Contact us today to learn how Varonis monitors Kerberos, and more.

Michael Buckbee
4 min read
-
 Data Security
Data SecurityMar 29, 2020
The Difference Between E3 and E5 Office365 Features
Microsoft’s Enterprise Mobility and Security offerings are additional sets of security services that can be purchased to help control, audit and protect the data and users of Microsoft’s Azure and...

Michael Buckbee
3 min read
-
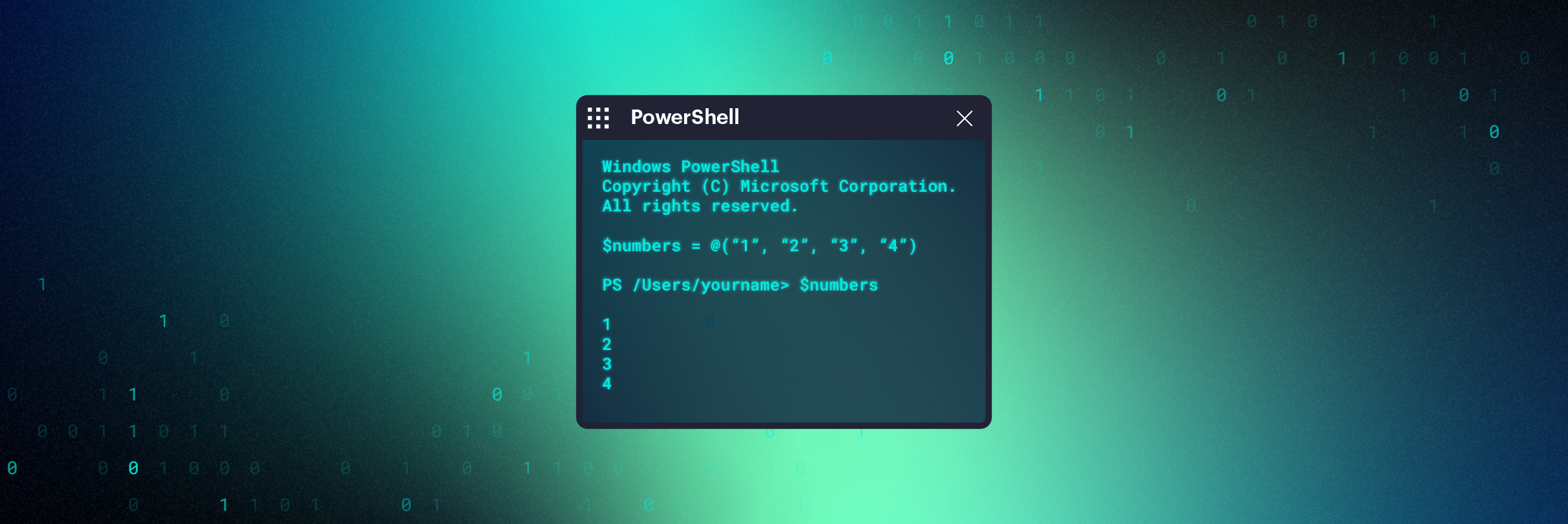 PowerShell
PowerShellMar 29, 2020
PowerShell Array Guide: How to Use and Create
Learn how to best use PowerShell arrays — we'll cover the basics of how to create them, work with them as well as some more advanced techniques.

Michael Buckbee
10 min read
-
 Data Security PowerShell
Data Security PowerShellMar 29, 2020
PowerShell Obfuscation: Stealth Through Confusion, Part II
Let’s step back a little from the last post’s exercise in jumbling PowerShell commands. Obfuscating code as a technique to avoid detection by malware and virus scanners (or prevent reverse...

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
A Guide on the Data Lifecycle: Identifying Where Your Data is Vulnerable
Data is a company’s most valuable asset. To maintain data’s value, it’s vital to identify where that data is vulnerable. According to data and ethics expert Dr. Gemma Galdon Clavell,...

Michael Buckbee
6 min read
-
 Data Security
Data SecurityMar 29, 2020
Solving The Cybersecurity Skills Shortage Within Your Organization
As technology evolves and cyberattacks increase so does the gap in the cybersecurity workforce, read on to see tech shortage solutions for your business

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
Automating Permissions Cleanup: An In-Depth ROI Analysis
Previously, we discussed automating data access requests to achieve incredible ROI by cutting down on help desk tickets. We also briefly mentioned the enormous amount of work involved in finding...

Michael Buckbee
4 min read
-
 Privacy & Compliance
Privacy & ComplianceMar 29, 2020
We Need to Talk About Gramm-Leach-Bliley (GLB): The Safeguards Rule Will Be Changing!
As a blogger following data security laws and regulations, I’m occasionally rewarded with an “I told you this law would be important” moment. Earlier this month with the news that...

Michael Buckbee
6 min read
-
 Data Security
Data SecurityMar 29, 2020
Koadic: Pen Testing, Pivoting, & JavaScripting, Part II
Mshta and rundll32, the Windows binaries that Koadic leverages, have been long known to hackers. If you take a peek at Mitre’s ATT&CK database, you’ll see that rundll32 has been...

Michael Buckbee
5 min read
-
 Active Directory Data Security
Active Directory Data SecurityMar 29, 2020
Active Directory Domain Services (AD DS): Overview and Functions
Active Directory Domain Services (AD DS) are the core functions that make AD work. Learn more about AD DS and how to defend AD against cyber attacks.

Michael Buckbee
3 min read
-
 Data Security
Data SecurityMar 29, 2020
The Difference between a Computer Virus and Computer Worm
Viruses and worms are often used interchangeably: there are a few key differences in how they work. Both viruses and worms are a type of malware: a worm is a...

Michael Buckbee
2 min read
SECURITY STACK NEWSLETTER
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital