Data privacy or information privacy is a branch of data security concerned with the proper handling of data – consent, notice, and regulatory obligations. More specifically, practical data privacy concerns often revolve around:
- Whether or how data is shared with third parties.
- How data is legally collected or stored.
- Regulatory restrictions such as GDPR, HIPAA, GLBA, or CCPA.
In this guide, we’ll look at why data privacy is important, and how it is linked to data security. Then we’ll take a look at the legislation that covers data privacy in several key countries, and In several key industries. Finally, we’ll give you some ways to improve your data privacy in both personal and business environments.
Get the Free Essential Guide to US Data Protection Compliance and Regulations
As we’ll see, the security and privacy of data are intimately connected, and so ensuring data privacy means making use of a complete security solution like that offered by Varonis.
- Data Privacy vs. Data Security
- Different Definitions of Data Privacy
- Data Privacy Laws, Acts and Timeline
- Data Privacy Best Practices
- Varonis and Data Privacy
- Data Privacy News and Resources
- Data Privacy FAQ
Why is Data Privacy Important?
There are two drivers for why data privacy is one of the most significant issues in our industry.
Data is one of the most important assets a company has. With the rise of the data economy, companies find enormous value in collecting, sharing and using data. Companies such as Google, Facebook, and Amazon have all built empires atop the data economy. Transparency in how businesses request consent, abide by their privacy policies, and manage the data that they’ve collected is vital to building trust and accountability with customers and partners who expect privacy. Many companies have learned the importance of privacy the hard way, through highly publicized privacy fails.
Second, privacy is the right of an individual to be free from uninvited surveillance. To safely exist in one’s space and freely express one’s opinions behind closed doors is critical to living in a democratic society.
“Privacy forms the basis of our freedom. You have to have moments of reserve, reflection, intimacy, and solitude,” says Dr. Ann Cavoukian, former Information & Privacy Commissioner of Ontario, Canada.
Dr. Cavoukian knows a thing or two about data privacy. She is best known for her leadership in the development of Privacy by Design (PbD), which now serves as a cornerstone for many pieces of contemporary data privacy legislation.
Data Privacy vs. Data Security
Organizations commonly believe that keeping sensitive data secure from hackers means they’re automatically compliant with data privacy regulations. This is not the case.
Data Security and data privacy are often used interchangeably, but there are distinct differences:
- Data Security protects data from compromise by external attackers and malicious insiders.
- Data Privacy governs how data is collected, shared and used.
Consider a scenario where you’ve gone to great lengths to secure personally identifiable information (PII). The data is encrypted, access is restricted, and multiple overlapping monitoring systems are in place. However, if that PII was collected without proper consent, you could be violating a data privacy regulation even though the data is secure.
Data Protection is the Force Behind Our Right to Privacy
Despite recent advances in data privacy legislation and practice, consumer’s privacy is regularly invaded or compromised by companies and governments. That has led some to argue that consumers have already lost the privacy war.
While you can have data protection without data privacy, you cannot have data privacy without data protection.
Ensuring data privacy means that you’re not the creepy company that greedily collects all of your customer’s personal data – whether it is with passive location tracking, apps secretly absorbing your personal address book, or websites recording your every keystroke.
Instead, employees should be regularly trained on data protection so they understand the processes and procedures necessary to ensure proper collection, sharing, and use of sensitive data as part of a data security portfolio.
Information privacy also includes the regulations required for companies to protect data. And as more data protection regulation grows worldwide, global privacy requirements and demands will also expand and change. However, the one constant is adequate data protection: it’s the best way to ensure that companies are both complying with the law and guaranteeing information privacy.
Varonis’ products are some of the most advanced data protection available. Because of this, our systems are used to protect consumer privacy all over the world.
Different Definitions of Data Privacy
Though most people agree on the importance of data privacy, and everyone is agreed that data protection is at the heart of ensuring privacy, the definition of “data privacy” itself is notoriously complex.
None of the laws we mention in this article – the GDPR, the CCPA, or the HIPAA – define precisely what they mean by data privacy. Instead, the provisions they contain suggest a number of best practices, and spell out the rights of consumers and businesses. Since every piece of legislation is different, trying to define exactly what is meant by “privacy” can be extremely difficult.
The situation doesn’t get any better if we limit our scope to one piece of legislation. Europe’s GDPR is arguably the most wide-ranging, comprehensive piece of data privacy legislation. Unfortunately, it is also confusing: the New York Times, back in May 2018, called it a “big, confusing mess”. The law grants citizens a number of rights, including the right to data portability (which allows people to move their data between platforms), and the right not to be subject to decisions based on automated data processing (prohibiting, for example, the use of an algorithm to reject applicants for jobs or loans).
The problem is that the practical implications of these rules are incredibly complex. The GDPR – like a lot of EU law – seeks to present a compromise between the different systems and values of many varied nation states. Because of this, “many scientists and data managers who will be subject to the law find it incomprehensible,” and doubt that absolute compliance is even possible.
For businesses in the USA, this is likely to become a huge problem. Being subject to both the GDPR and CCPA is an issue because the definition of data privacy that the two pieces of legislation use, and the way that they define “fair use” of data, are very different. Here are the key differences:
- Firstly, you should recognize that the CCPA applies to residents of California (albeit defined in a slightly strange way), no matter where your company is based. Similarly, the GDPR protects the rights of EU citizens, again no matter where your company is based. If you deal with citizens of the EU or California, you are covered.

- The CCPA protects the rights of Californians to not have their data sold by companies. Companies dealing with Californians (that is, all companies with a website) must include a “do not sell my personal information” link on their website home pages to give consumers the right to opt out of allowing their information to be sold. The GDPR, on the other hand, doesn’t deal with this issue.
- Another key difference is that under Article 6 of the GDPR, companies must demonstrate that they have a legal basis for processing customer information. The CCPA, on the other hand, doesn’t require that you justify collecting or processing private data.

- The GDPR also contains specific rules about how health data can be collected and stored. The GDPR defines “biometric data” and “genetic data” as two separate types of personal data, whereas under CCPA, such information is encompassed under the single category of “personal information.”
- The GDPR applies to all companies who work with data, whereas the CCPA only applies to for-profit businesses.
- In some ways, the GDPR is stricter when it comes to the managerial processes required to achieve compliance. The legislation requires that “data protection officers” be appointed within companies. The CCPA doesn’t require this, as long as the other provisions in the regulation are being adhered to.
- In terms of the fines that can be levied under both pieces of legislation, there are also huge differences. The GDPR’s Article 83 states that companies can be subject to fines of up to €20 million or 4% of total worldwide turnover. That can be a huge amount for some companies, and Google has already been fined €50 million for data privacy violations in France. The CCPA, on the other hand, is much more lenient: companies are given a grace period of 30 days to fix the violation, and then are only fined $2500 per violation.
In short, the different definitions of data privacy used in just these two pieces of legislation (to say nothing of HIPAA or other pieces of legislation) are extremely confusing. What is deemed “reasonable” differs significantly in each law, and so do the penalties for breaking them.
In practice, this means that companies who work with private data need to exceed the law in order to ensure that their data practices are well above those expected in the legislation. We’ll come on to how to do that shortly, but first let’s take a closer look at the pieces of legislation we’ve already mentioned.
Data Privacy Laws and Acts
Fortunately, lawmakers have recognized the importance of having data privacy regulation and the need to hold companies responsible for end-user data.
Companies are now required to determine what data privacy acts and laws affect their users. For instance, you must know where the data originated (country and state), what personally identifiable information it might contain and usage methodology.
Let’s take a closer look at how the most recent data privacy regulations impact users and companies. Here are the four most important pieces of data privacy legislation.
The GDPR: EU Data Privacy Laws
Enacted in May 2018, the GDPR aims to protect EU citizens’ personal data, and is already having major affects on companies in Europe. There are many aspects of the GDPR, and many tasks that companies have to undertake to achieve and maintain compliance with the GDPR. These include, but are not limited to:
- Explicit opt-in consent from users
- The right to request data from companies
- The right to have your data deleted
GDPR gives consumers certain rights over their data while also placing security obligations on companies holding their data. For companies, one challenging aspect of the legislation is the requirement to respond to subject access requests.
The reality is that most organizations can’t easily locate, provide, or delete an individual’s personal data on request. Many CIOs and data privacy officers rely on GDPR compliance software that automatically discovers and classifies personal data in order to keep it protected and to help expedite data subject access requests.
Data Privacy in Healthcare
While the EU has GDPR, one of the most prominent US data protection and privacy laws at the federal level is HIPAA—a data privacy regulation that was put in place to safeguard patient personal health information.
Healthcare providers have always been an attractive target for data breaches. In fact, health records are extremely valuable—approximately 10-20 times more valuable than credit card numbers. That’s why they should ensure they are compliant with HIPAA.
Even though Congress passed HIPAA in 1996, calls for even greater data privacy protection have increased with data breaches at an all-time high and the rate at which companies use and sell the data they collect on their patients rising fast.
Fortunately, in December 2000, the U.S. Department of Health and Human Services(HHS) issued the Privacy Rule to carry out HIPAA’s mandate to safeguard the privacy of individually identifiable health information.
If you’re curious how GDPR and HIPAA compare, keep in mind that GDPR covers an even broader scope than HIPAA and does not focus exclusively on health data. GDPR calls for protecting “sensitive personal data” which includes protecting health data. Bottom line: GDPR is comparable to HIPAA’s regulatory requirements.
Data Privacy for Financial Institutions
Another regulation that should be on your radar is the Gramm-Leach-Bliley Act (GLBA). The GLBA requires financial institutions to safeguard consumer financial data. To do this, leverage classification to quickly identify where your sensitive financial data is stored.
The benefits of achieving GLBA compliance is multi-fold. It reduces potential fines and reputational harm due to the unauthorized sharing or loss of sensitive financial data. Sure, the GLBA isn’t the same as the EU’s GDPR, but it won’t be long before America gets their own.
Innovative US Data Privacy Laws
In the US, data privacy is also regulated under a number of further laws. Some of these operate at a state level, and some apply to the whole country. These laws represent an innovative approach to ensuring data privacy in the country, and in some cases go much further than the current legislation that deals with individual sectors.
The CCPA, for instance, is a law in California that extends data privacy protections in that state. Businesses operating in the state of California need to be ready on January 1, 2020 for the CCPA to identify and discover personal information, fulfill data subject access requests, and protect consumer data. The CCPA gives consumers a right to control how companies collect and use their personal data. This means that companies need to be able to quickly and accurately find and classify sensitive data so that they can identify data that falls under the CCPA and fulfill data subject access requests (DSARs).
Similarly, the COPPA, the Children’s Online Privacy Protection Act, aims to protect the privacy of children under 13, and was adopted back in 1998. This law stipulates that companies must ask for parents’ permission to collect data on children, and also specifies the way that this data can then be held and processed.
Several states are considering similar laws to California’s, and there appears to be an appetite among lawmakers to improve data security and privacy in further sectors. Some have even suggested that a Federal Department of Cybersecurity could be set up to standardize these laws across the country, but at the moment the situation remains a patchwork of different regulations.
Other Data Privacy Laws
Though the laws mentioned above are the most high-profile regulatory frameworks when it comes to data privacy, you should also be aware that there are data privacy laws that apply to particular kinds of companies, or for particular kinds of data.
Which of these apply to your business will depend both on your sector and how you store and process data, but it’s worth checking the provisions for ISO 27001 compliance, FISMA compliance, and Sox compliance.
Varonis can help you work toward compliance with all these frameworks by providing full data protection solutions, which will ensure that your data is both safe and fully compliant with the relevant legislation. If you want to discuss your data privacy requirements, give us a call today.
Data Privacy Tips
If you’ve read through the above, you’re probably wondering how you can ensure data privacy. In this section, we’ll give you some tips on how to do that, whether you are a business or merely a concerned consumer.
Business-Focused Data Privacy Tips
We have previously written about how businesses can ensure data security, and because of the link between data security and data privacy our advice there will also help you to ensure the privacy of the data you hold as a business.
These techniques include:
- Ensuring awareness of data security and privacy concerns and techniques for every employee at your company. You should integrate training on data privacy into your general training program, and it should be part of the onboarding process for new staff.
- Make sure that you take advantage of the free security tools that are out there. This includes encrypted storage solutions, password managers, and VPNs. These small tools can dramatically decrease your vulnerability to attack, and are easy to use and install.
- Monitor your network for suspicious activity, so that you can catch on to an attack early enough to reduce the damage.
- Don’t underestimate hackers’ interest in your company because it’s smaller or just starting out — breaches and attacks affect organizations of all sizes, including start-ups and small businesses.
- Implement the zero trust model. As Sivan Tehila, founder of Leading Cyber Ladies and Cyber19w, tells us, “Zero Trust restricts access to the entire network by isolating applications and segmenting network access based on user permissions, authentication and user verification. With Zero Trust policy enforcement and protection are easily implemented for all users, devices, applications and data, regardless of where users are connecting from. This user-centric approach makes the verification of authorized entities mandatory, not optional. This ‘trust, but verify’ mindset is absolutely essential for today’s organizations.”
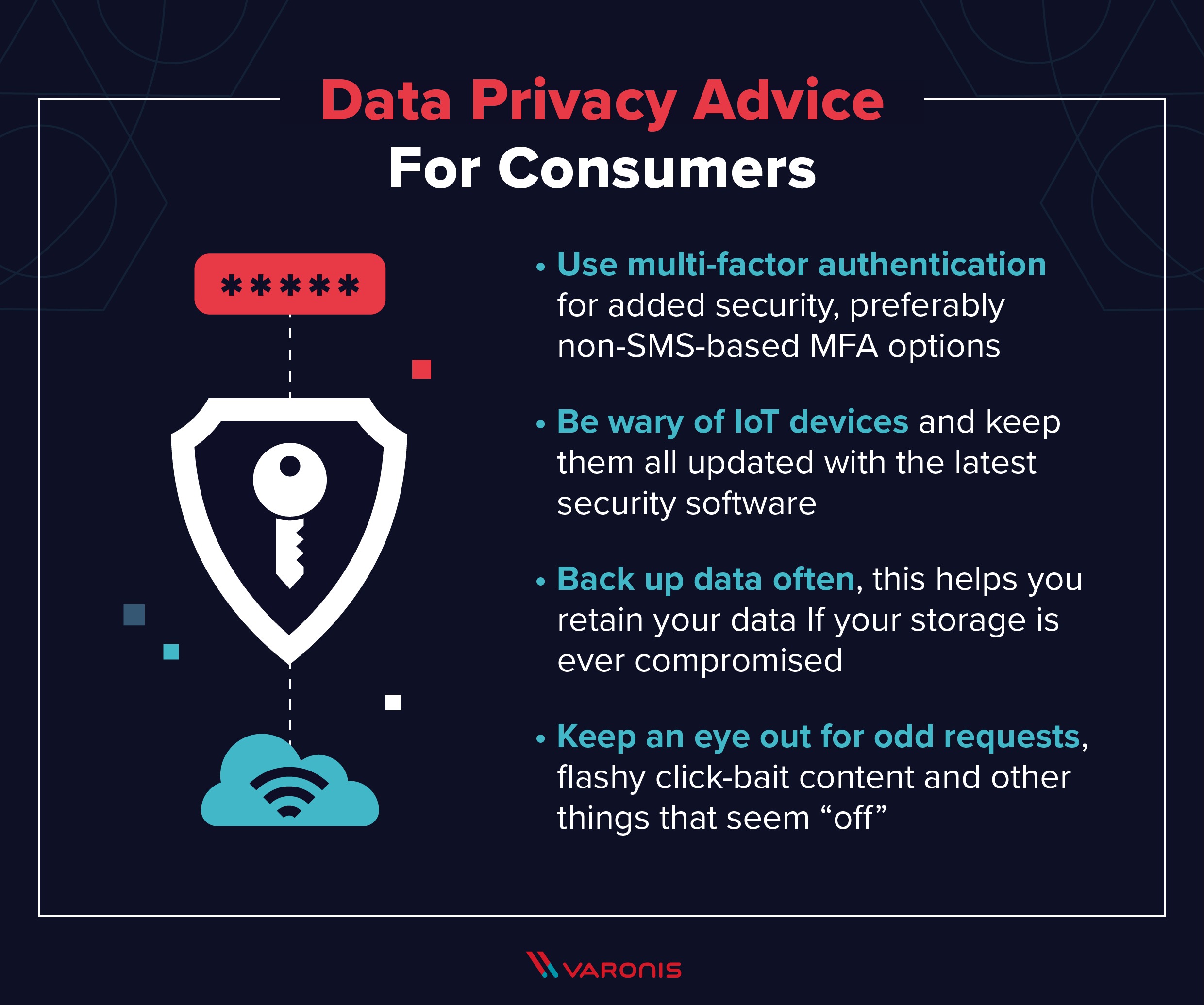
Consumers-Focused Data Privacy Tips
As a consumer, you don’t have all that much control over how companies are storing your data, and how well they are keeping it private. That said, there are a number of easy steps you can take that can improve the privacy of your data. A good first step is to familiarize yourself with the privacy tools that are available. This means at minimum a VPN to encrypt your internet connection, and a password manager to improve the security of your online accounts.
- Use multi-factor authentication for additional layers of security and to make sure important accounts aren’t easily hacked if the passwords are cracked. Preferentially use non-SMS-based MFA options. Many online companies now offer multi-factor authentication for free, so request that they implement it on your account.
- Be aware of what spyware in the IoT means for data privacy: this has been one of the biggest cybersecurity stories of the last year, and points to the importance of keeping all of your IoT devices updated with the latest security software.
- Back up data often. If data storage is ever compromised, you’ll have the best chance of hanging on to that data if you have a secure backup.
- Keep an eye out for strange requests, spelling and grammar mistakes, flashy click-bait content and other things that may seem “off.”
How Varonis Helps with Data Privacy
To achieve data privacy nirvana, organizations need a data security solution that protects enterprise data, prevents data breaches, reduces risk, and helps achieve compliance. At Varonis, our approach to data security as it relates to enhancing data privacy includes:
Manage access to sensitive and regulated data
You’ll never hear anyone complain of having too much access. That’s why regular entitlement reviews with DatAdvantage and DataPrivilege ensure that only the right people have access to the right data: unrestrained access leave companies at risk of a data breach, theft or misuse. If you want to achieve least privilege and compliance faster, the Automation Engine helps you get there – so that you can automatically remediate global access and fix file system permissions.
Follow proper compliance requirements
Love it or hate it, compliance requirements hold a baseline that enforces data privacy goals to sustain freedom, intimacy, and solitude. With Data Classification Engine, you’ll find and classify regulated and sensitive content. After, you’ll have the option to automatically transport data to where it needs to be and also fulfill data subject access requests as needed.
Monitor and detect suspicious behavior on sensitive data
Arming your organization with DatAlert means that you’ll have continuous monitoring and alerting on all your organization’s data. This means companies can identify and monitor consumer personal data, track who is accessing it, highlight unusual activity and report on odd behavior that’s regulated and sensitive. Ultimately, knowing that your data is always safe and secure also ensures data privacy.
Data Privacy News and Resources
Data privacy has become a mainstream concern over the past year, and coverage of the issue has appeared in all the major newspapers. If you want to stay on top of breaking news in the data privacy field, though, it’s also worth checking the specialized media: WIRED will often report on data privacy stories, as will HackerNoon and InfoSecurity Magazine.
Here are some of the biggest stories in data privacy at the moment:
California’s CCPA Comes Into Effect
As 2019 comes to a close, all eyes are on next year, when California’s CCPA will go into effect in the State. This law represents the strongest data privacy protections in the USA at the moment, and companies have been preparing to implement it for years. The key question is whether this kind of law can eventually be applied across the country.
Google’s Project Nightingale Raises Data Privacy Concerns
On the consumer side of the equation, much of the debate of late has been dominated by the exposure of “project nightingale”, a data-sharing agreement between Google and Ascension, the USA’s second-largest healthcare provider. Though this data exchange was completely legal, it has given people a renewed awareness of just how much personal data they are sharing, and how it is being processed.
India Rolls Out New Data Privacy Law
In news from further afield, India is now passing national legislation to control what companies can do with personal data. The new law is inspired by similar frameworks in the EU and US, and will potentially have a huge impact on the country’s growing tech sector.
FAQs About Data Privacy
Even after all that information, you might still have some questions about data privacy. We’re here to help.
Q: Is There a Global Data Privacy Law?
A: No. Data privacy laws are relatively new in any case, and there is no worldwide standard. That said, many companies look to the GDPR – Europe’s data protection law – as a guide for how to store and manage data privacy correctly, even if they are not doing business in the EU. Different laws will apply to your business depending on your sector and location, so make sure you check your responsibilities.
Q: Can We Protect Our Data in Other Countries?
A: Again, because of the fragmentary nature of data privacy laws, it can be extremely difficult to ensure the security of your data if you send it abroad. The key, as a concerned consumer, is only to share information with companies who are open and honest about their data privacy policies, and who won’t sell your information to the highest bidder.
Q: How Can Companies Ensure That They Have Data Privacy When Using Public Clouds?
Choose the correct cloud provider. In truth, most companies will not have the time or resources to employ a dedicated cloud security specialist. The best solution for most will, therefore, be to choose a cloud provider who also provides you with security features, and who can advise you about your legal responsibilities.
A Final Word
Data privacy is important for a number of reasons. As a consumer, you need to be aware that your data is being stored and used by a whole host of companies, and make sure that you don’t share more than you have to. Privacy is, after all, a fundamental right.
As a company, data privacy is arguable even more important. You may have to meet legal responsibilities about how you collect, store, and process personal data, and non-compliance could lead to a hefty fine. If you fall victim to a hack, the consequences in terms of lost revenue and lost customer trust could be even worse.
That’s why we’ve built a complete security solution that provides advanced data security features. DatAdvantage and DataPrivilege ensure that only those people who should have access to your data do, and so you can work toward data privacy compliance easily and effectively.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.