What is CDM?
The Continuous Diagnostics and Mitigation (CDM) program is a United States government cybersecurity initiative led by the Department of Homeland Security (DHS). The Cybersecurity and Infrastructure Security Agency (CISA) leads CDM with the stated purpose of:
- Reducing agency threat surface
- Increasing visibility into the federal cybersecurity posture
- Improving federal cybersecurity response capabilities
- Streamlining Federal Information Security Modernization Act (FISMA) reporting
In this blog, we will dig into how CDM helps accomplish those goals, and how Varonis supports a CDM strategy.
Get the Free Pen Testing Active Directory Environments EBook
The Four Phases of CDM
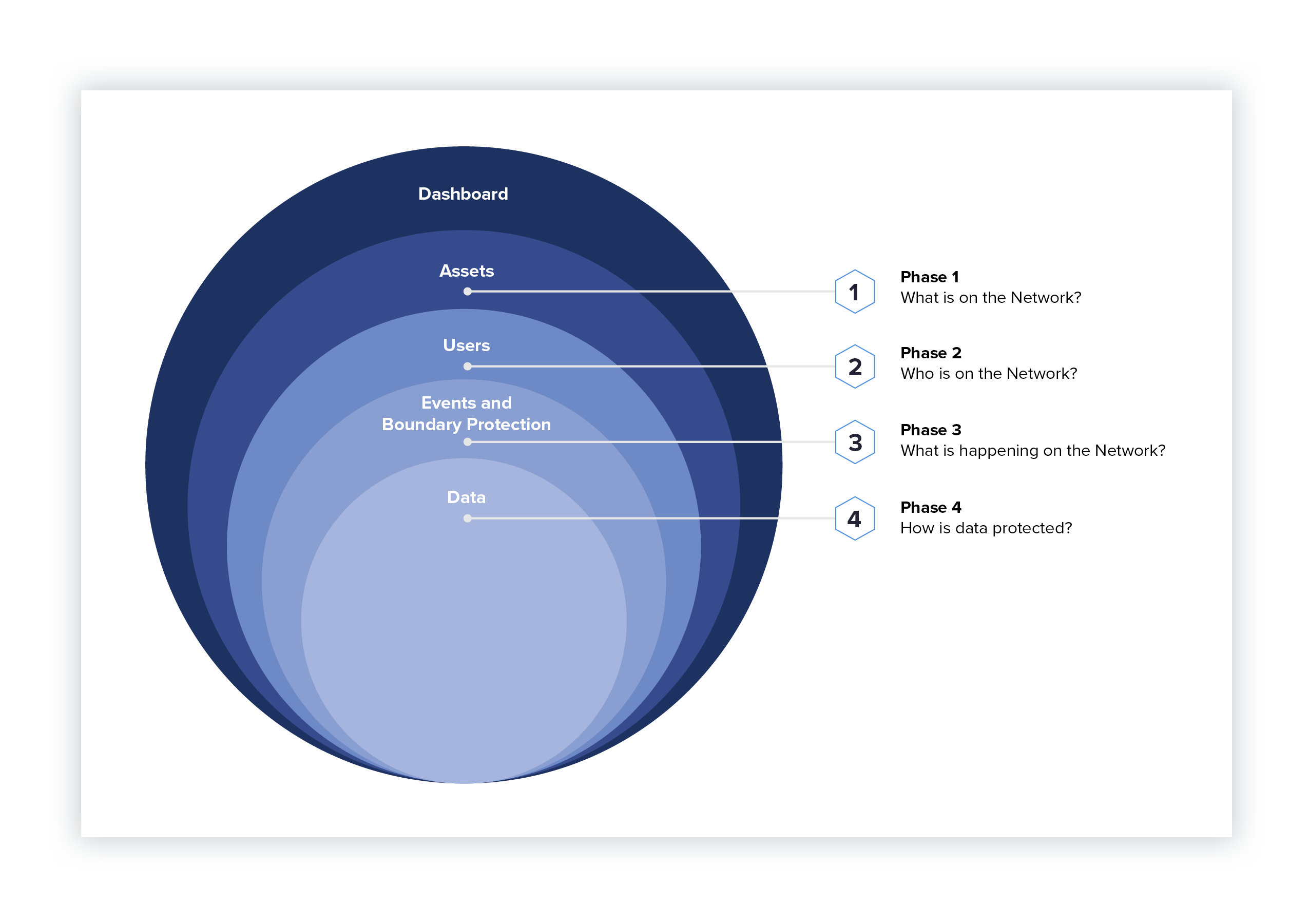 To help agencies improve their cybersecurity posture, CISA defined four phases for agencies and private organizations to use as a model for their cybersecurity strategy.
To help agencies improve their cybersecurity posture, CISA defined four phases for agencies and private organizations to use as a model for their cybersecurity strategy.
Phase 1: What is on the Network?
In phase 1 of CDM, agencies are required to catalog and list the basic details of hardware, software, and configurations that live on their networks. In order to defend their entire network, each agency has to know exactly what computer, devices, and software they have to defend.
- Hardware Asset Management (HWAM)
- Software Asset Management (SWAM)
- Configuration Settings Management (CSM)
- Vulnerability Management (VUL)
Phase 2: Who is on the Network?
Phase 2 is all about the user accounts and how users interact with and use the agency’s network. Just as important as phase 1, phase 2 is about discovering what users and groups exist in Active Directory, Azure, local computer accounts, etc. When agencies map user accounts to file and folder access, they get a better picture of where sensitive data is exposed.
- Manage Privileges (PRIV)
- Manage Trust in People Granted Access (TRUST)
- Manage Credentials and Authentication (CRED)
- Manage Security Related Behavior (BEHAVE)
Phase 3: What is Happening on the Network?
In Phase 3, agencies need to monitor network and perimeter components, host and device components, data at rest and in transit, and user behavior and activities. Monitoring combined with the correct analytics is the best way to detect threats to data.
- Manage Events (MNGEVT)
- Operate, Monitor, and Improve (OMI)
- Design and Build-in Security (DBS)
- Boundary Protection (BOUND)
- Supply Chain Risk Management (SCRM)
Phase 4: How is Data Protected?
Phase 4 requires agencies to enable several data protections. These controls are fundamental to any cybersecurity strategy because they allow organizations to answer questions like, “has sensitive data been compromised?” Without data classification and a forensic audit trail of how data has been accessed, agencies wouldn’t necessarily know if data breach included sensitive material, for example.
- Data Discovery/Classification (DISC)
- Data Protection (PROT)
- Data Loss Prevention (DLP)
- Data Breach/Spillage Mitigation (MIT)
- Information Rights Management (IRM)
Dashboard
To help agencies track their progress through all four phases of the program, CISA created custom dashboards. These dashboards provide a picture of an agency’s cybersecurity posture and assets through a single pane of glass. They gather data from automated feeds – including Varonis – to ensure security controls and allow for prioritization of risk mitigation and remediation. There are web-based training about these dashboards on the CDM website.
How Does Varonis Help With CDM?
Varonis is a DHS-approved product that provides the core functionality needed to achieve the requirements set forth by the CDM across all phases. Phases 3 and 4 are underway right now, which are phases where Varonis can deliver significant value.
Varonis is a data-centric security suite that identifies permissions, classifies sensitive data, and detects threats to data. One of the core tenents of CDM is protecting data, and Varonis protects data first.
Phase 1: Asset Management
What is on the network?
In addition to understanding what hardware and software exists on the network, it’s critical for agencies to understand where their most sensitive data is. With this visibility, agencies can ensure they have the proper controls in place to limit sensitive data exposure. Varonis builds a map of unstructured data across the cloud and on-premises data stores and email systems. We automatically discover and classify sensitive data that hides across the network and stale data that’s no longer needed to help visualize where data is most at-risk and enable action to limit that risk.
Phase 2: Identity and Access Management
Who is on the network?
Limiting access to sensitive data is a critical next step for agencies to undertake in order to minimize their threat surface. Varonis creates a searchable inventory of all users, groups, and computers in Active Directory, Azure AD, and all local system directories that agencies can use to review and remediate over-permissive and unneeded permissions. From the Varonis platform, agencies can resolve all user & group memberships and access levels, including complex and deeply nested relationships to align with a least privilege access model.Varonis learns typical behaviors for users, including usual locations, working hours, and user-device matches. and can alert on instances where behavior seems suspicious or consistent with a cyberattack.
Phase 3: Network Security Management
What is happening on the network?
For agencies to be proactive in responding to threats, they need to understand what is happening on their network. From a data perspective, that means knowing when data has been accessed, changed, moved, or deleted. This knowledge of how data is being used combined with known threat models and indications of attacks can help agencies proactively identify and respond to threats before impact. Compromised users do things they don’t usually do, like login at odd times from unusual geo locations, access data they never tried to access before, or touch new systems. Varonis detects these abnormal behaviors and compares them to known threat models to warn of potentially dangerous user activity proactively.
Phase 4: Data Protection Management
How is data protected?
The last and arguably most challenging phase of CDM involves protecting data. Several security solutions can help agencies gain greater visibility into their users, permissions, etc., but few can help them take action to actually protect data. Varonis limits agencies’ threat surface by automatically removing Global Access and fixing broken ACLs with just a few button presses. These changes can be sandboxed before committing them to ensure they don’t negatively impact users. In addition to these massive remediation efforts, Varonis can help keep risk low over time by scanning and classifying data as it’s created and implementing controls for managing access on an ongoing basis. Data that’s classified as sensitive can be automatically quarantined to ensure only the right people have access to it. Agencies can implement a user access approval model to put data owners in charge of access to their data and maintain oversight with regular audits.
Using Varonis to Succeed with CDM
Varonis is a DHS-approved product for helping organizations succeed with CDM. Using the Varonis Data Security Platform, agencies can monitor how data is flowing through their file and email systems, alert on anomalous user behavior, and quickly respond to suspicious activity. Varonis captures, normalizes, and analyzes data access events and combines access activity with additional context, like file content and sensitivity, permissions, and user profiles and behaviors with respect to systems and data. With that information as a baseline, Varonis determines what is normal behavior and detects anomalies which could indicate a threat. This proactive approach to data security can help agencies limit sensitive data exposure, identify potential issues in real time, and quickly remediate them.
Curious to see how Varonis can help detect threats?
Check out the Varonis Live Cyber Attack Lab to see Varonis in action as we demonstrate a real-world cyber attack.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.