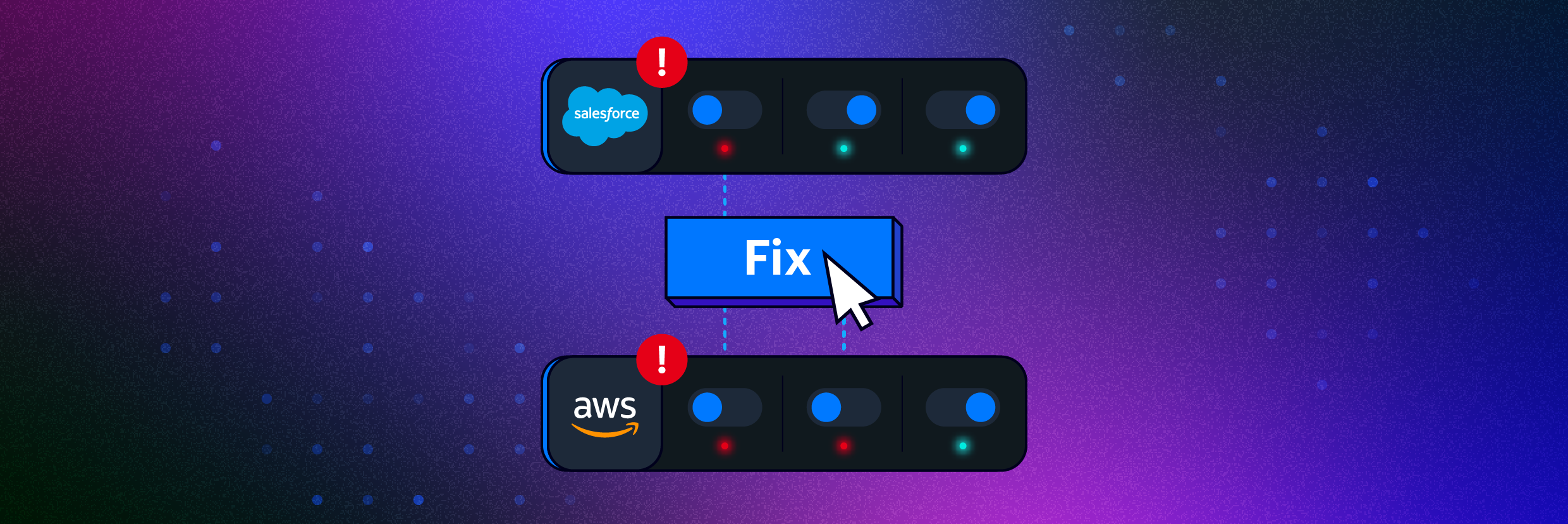
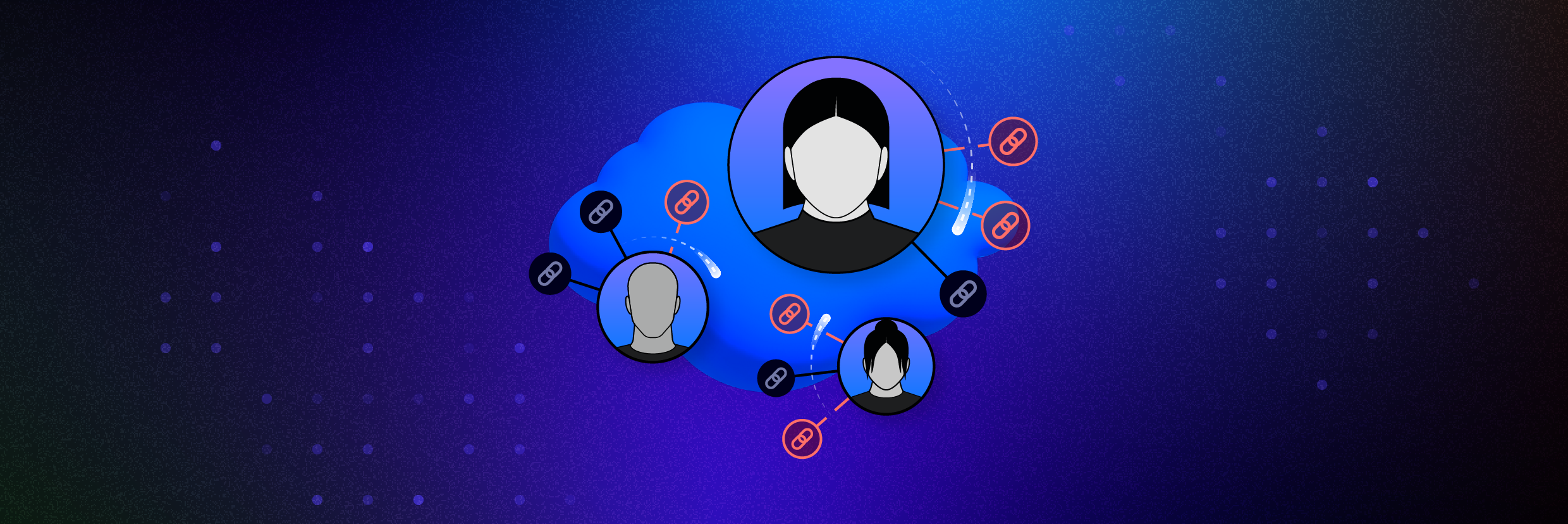
Continuously and automatically enforce your data security policies with Varonis. Eliminate risky permissions, misconfigurations, ghost users, sharing links, and more without manual effort.
- Cloud-native
- Automated
- Cross-platform

Partner with the leader in data security.
Don't just find security risk, fix it.
Remediate excessive permissions
- Remove public links to sensitive data
- Remove stale collaboration links
- Remove excessive group memberships
Fix risky misconfigurations and stale users
- Auto-enforce secure settings such as MFA enabled for admins
- Delete inactive and disabled users
- Disable risky and inactive third-party apps
Enforce data lifecycle policies
- Archive or delete stale data
- Enforce data residency policies
- Apply labels and enforce DLP policies
The DPO was happy, the COO was happy. The risk committees were happy. It felt really good and we went out and had a celebration. We are less likely to have breaches now.
Automated permissions remediation
Varonis makes intelligent decisions about who needs access to data and who doesn’t — continually reducing your blast radius without human intervention and without breaking the business.
Out-of-the-box and custom policies
Varonis comes with ready-made remediation policies that you can personalize for your organization. You define the guardrails and our automation will do the rest. Customize based on sensitivity, staleness, location, link type, and more. Preview results and review permissions affected by your policy before committing.
Continuous or one-time enforcement
Simulate changes in a sandbox to see exactly what the outcome will be ahead of time. Run your policies one-time, on a schedule, or continuously in the background. Monitor the status of your policies and rollback changes if needed.
Accurate and actionable MPIP labels
Varonis fully integrates with Microsoft Purview to enhance Microsoft's native classification in E3 and E5. Create granular policies to fit your needs, automatically fix manual gaps, and re-label files as your data changes — making downstream DLP controls more effective.
Tangible results to show leadership and auditors
Reports and dashboards clearly show meaningful risk reduction over time. Demonstrate blast radius reduction, data residency and lifecycle compliance, and overall data security posture improvement.
Our customers have spoken
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Policy Automation resources
Go beyond Policy Automation.
Varonis tackles hundreds of use cases, making it the ultimate platform to prevent data breaches and ensure compliance.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital







.png)