Cloud service providers (CSPs) host a wide array of mission-critical data such as medical documents, military defense information, and unstructured datasets for training large language models (LLMs). Misconfigured or overly permissive cloud data stores have been the source of countless data breaches, exposing sensitive information to the internet and providing footholds for attackers.
Varonis’ cloud-native platform gives customers holistic data security across their entire data estate: SaaS apps, email, hybrid file storage, databases, and beyond. The latest enhancements to Varonis’ IaaS coverage help customers continuously discover regulated data, remediate misconfigurations and excessive access, and stop attacks on data in services such as Azure Blob and AWS S3, RDS, and unmanaged databases in EC2.
With Varonis, you can:
- Gain a centralized overview of your data and cloud security posture.
- Discover and classify sensitive data stored in Azure Blob and AWS databases.
- Identify and remediate exposure risk through excessive access, misconfiguration, and third-party applications.
- Monitor activity to detect and investigate threats across the cloud ecosystem.
Monitor your cloud security posture.
Our IaaS dashboard provides a centralized overview of your cloud and data security posture across AWS and Azure environments, including Azure Blob, AWS IAM, S3, RDS, and EC2 instances. Easily identify where your sensitive data may be at risk and if there are any gaps in your security posture — all from a single pane of glass view.
Monitor your cloud security posture with key risk indicators, including:
- Overexposed and stale sensitive resources
- Unencrypted storage
- Users with stale access keys
- Inactive privileged roles and users
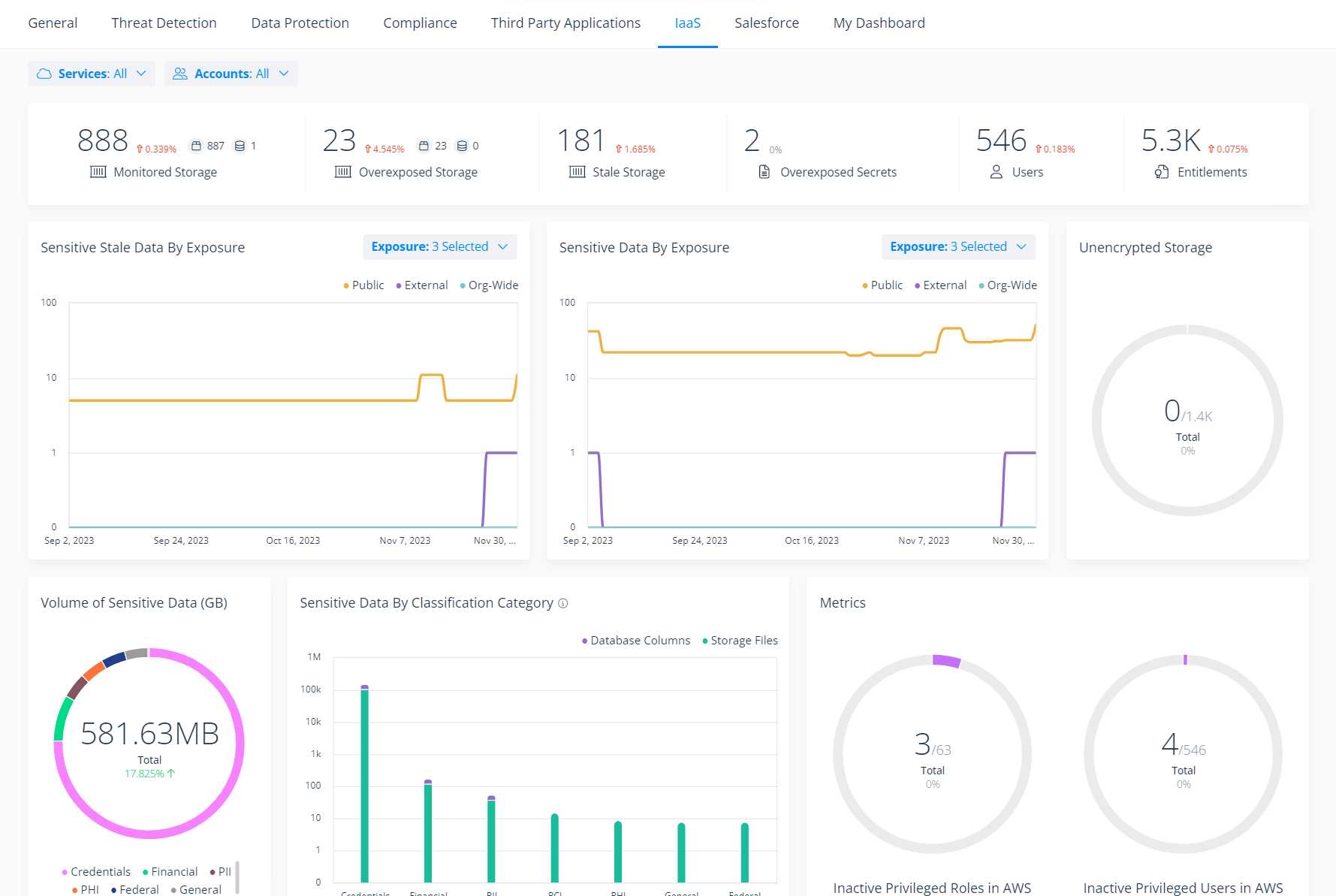 Monitor your overall cloud security posture with the Varonis IaaS dashboard.
Monitor your overall cloud security posture with the Varonis IaaS dashboard.
Drill down into widgets to begin remediating risks and improving your data security posture across your cloud resources.
Automatically discover and classify sensitive data across your cloud ecosystem.
Varonis automatically maps your cloud data estate, discovering and classifying sensitive data stored across AWS databases — whether managed (RDS) or unmanaged (EC2) — AWS S3, and Azure Blob.
Hundreds of built-in patterns help you understand where you have regulated data and where it’s at risk. This includes PII, financial data, intellectual property, and other types of sensitive information that need to be locked down and protected.
You can customize your classification scope to optimize speed and processing power and save on costs.
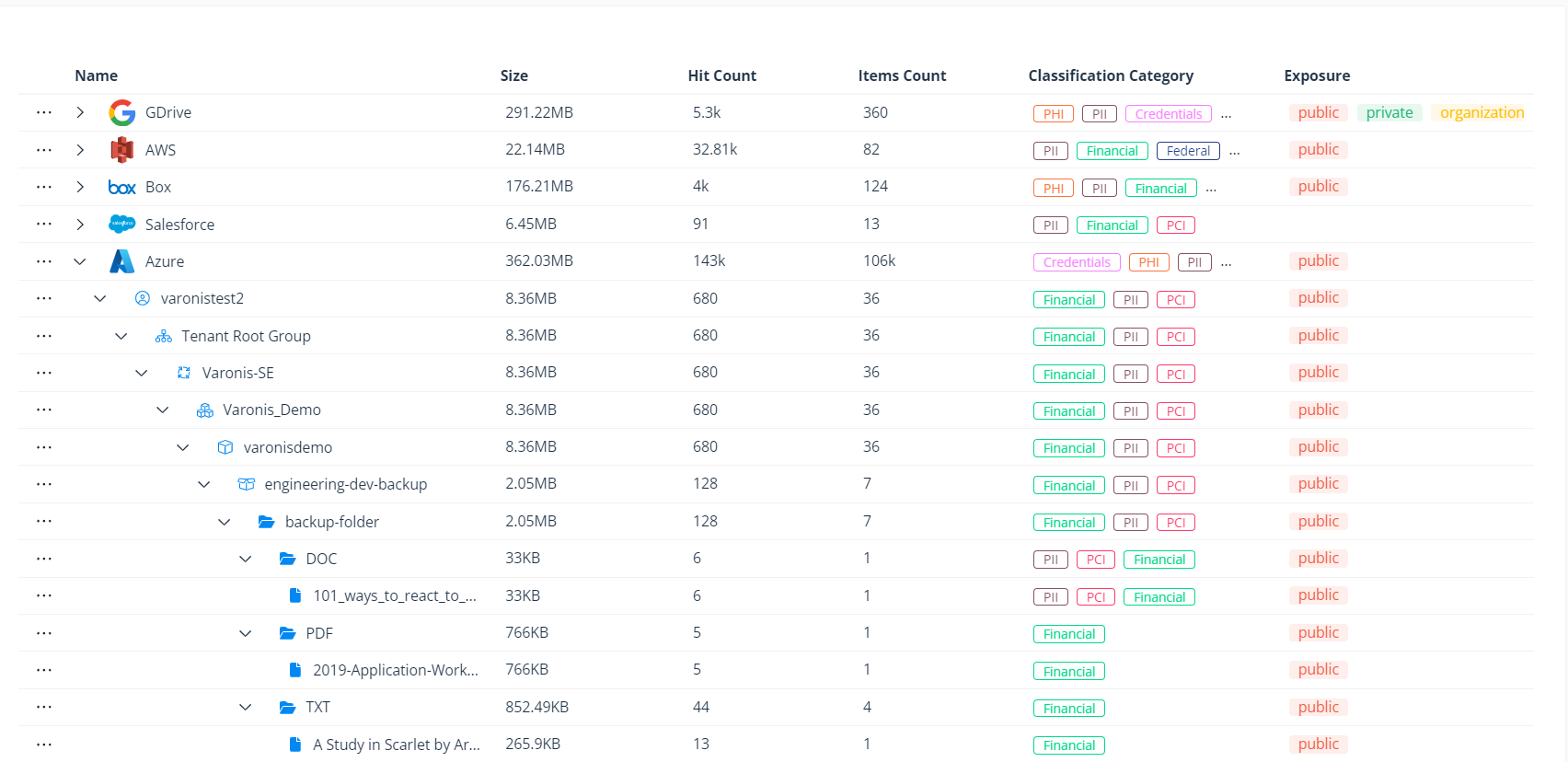 Automatically discover and classify sensitive data stored across the cloud and view results in an intuitive file tree format.
Automatically discover and classify sensitive data stored across the cloud and view results in an intuitive file tree format.
Easily confirm classification results with file analysis, which shows you exactly where the classification results appear within the resource.
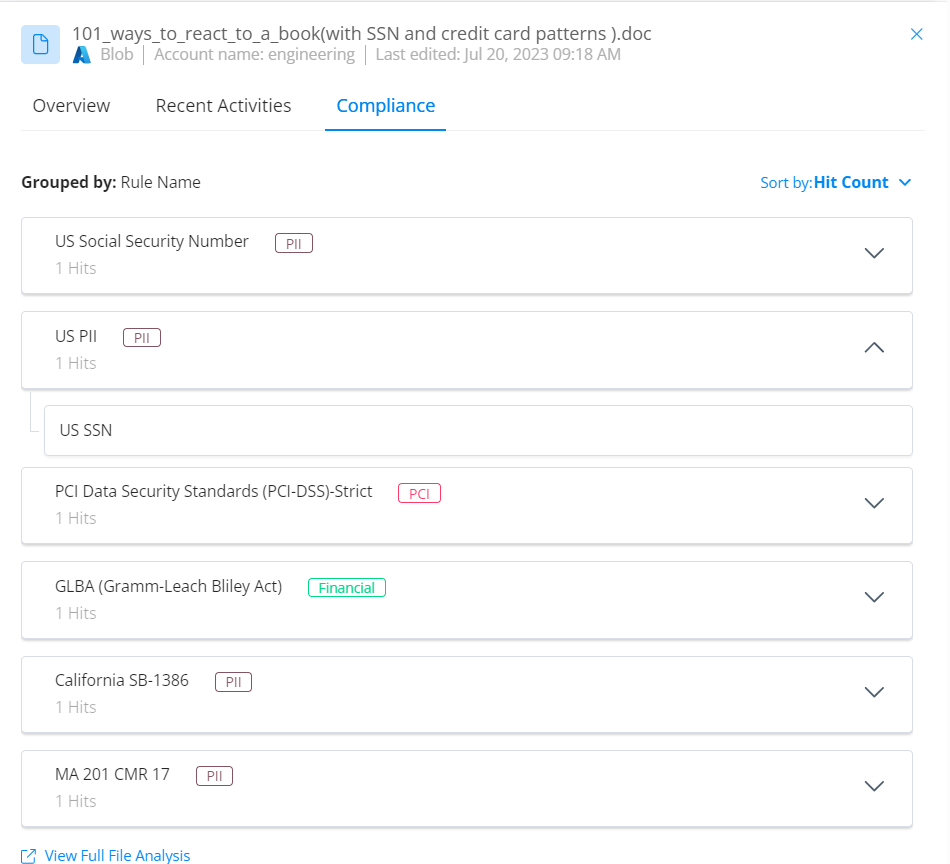
Review classification results to see the exact types of sensitive data that exist in your environment.
Automatically find and fix misconfiguration.
Varonis continuously scans your cloud infrastructure and identifies security gaps and misconfigurations that could put your data at risk or break compliance.
Varonis surfaces misconfigurations in a centralized dashboard, sorted by severity, so you can begin prioritizing and remediating.
We’ll surface security risks such as:
- Publicly exposed containers, blobs, buckets, and database instances
- Azure group owners can consent to apps on behalf of group members
- Broad guest invitation permissions
- Missing password policies
- Default users can create security groups
Easily compare the posture of your environment against standard rules and regulations like CIS, ISO, NIST, and HIPPA, and identify where your configurations drift out of compliance.
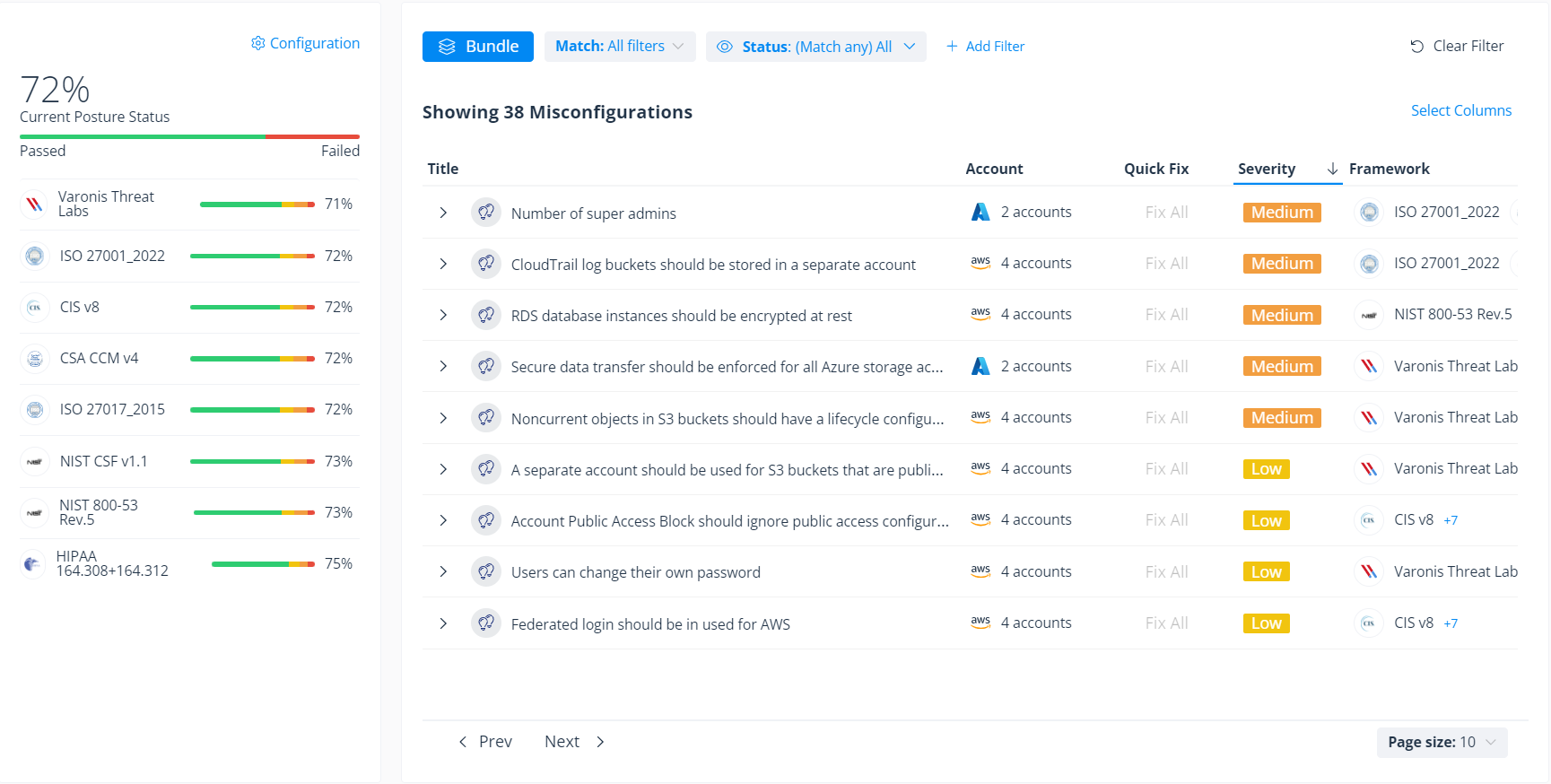 View misconfigurations sorted by severity in the Varonis posture dashboard and identify configuration drift across your cloud environment.
View misconfigurations sorted by severity in the Varonis posture dashboard and identify configuration drift across your cloud environment.
Each configuration insight provides a severity level to help you prioritize remediation efforts. Additional context explains why the misconfigurations are a security risk and provides detailed recommendations on how to fix the issue.
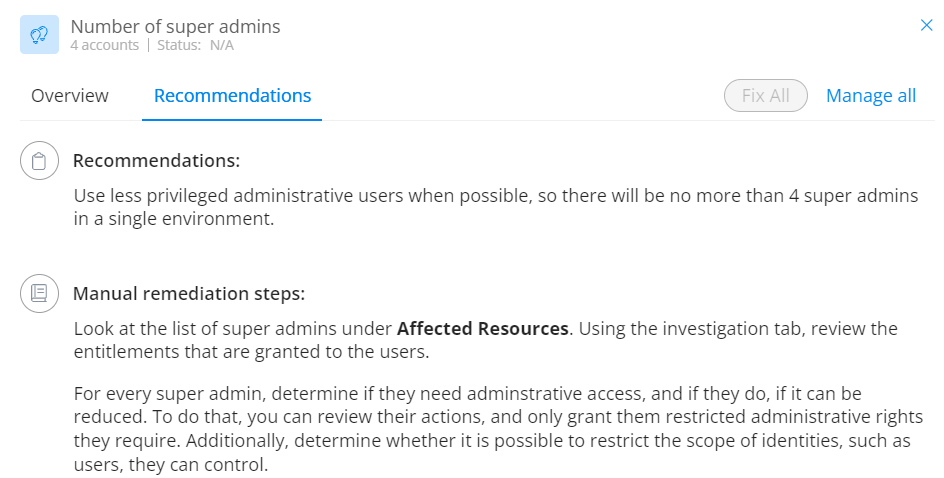
Expand each insight to review Varonis’ recommendations on how to fix the issue.
Remediate excessive permissions to AWS databases.
Varonis analyzes and maps user permissions in AWS databases and S3 to identify where your sensitive data is at risk through excessive privileges and public exposure.
We help simplify complicated IAM access policies by normalizing permissions into a simple CRUDS model (create, read, update, delete, and share).
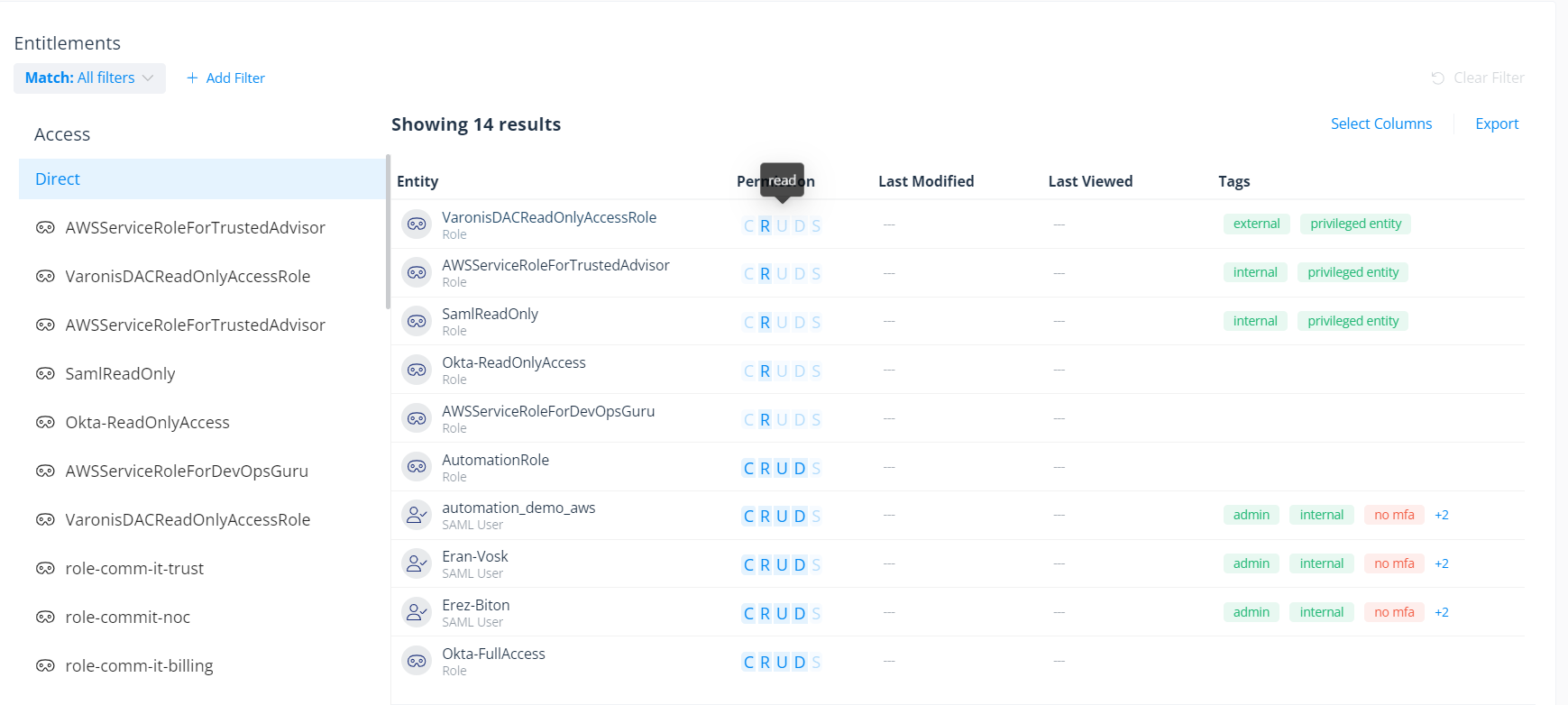
Map user and role permissions across your AWS database instances.
We not only show you what permissions each user has but also how they got them. Varonis enables you to visualize which policies and roles grant users access to your cloud resources through our access reasoning graph, making it simple to understand how users can access and use your data without having to be an expert in AWS’s permissions models.
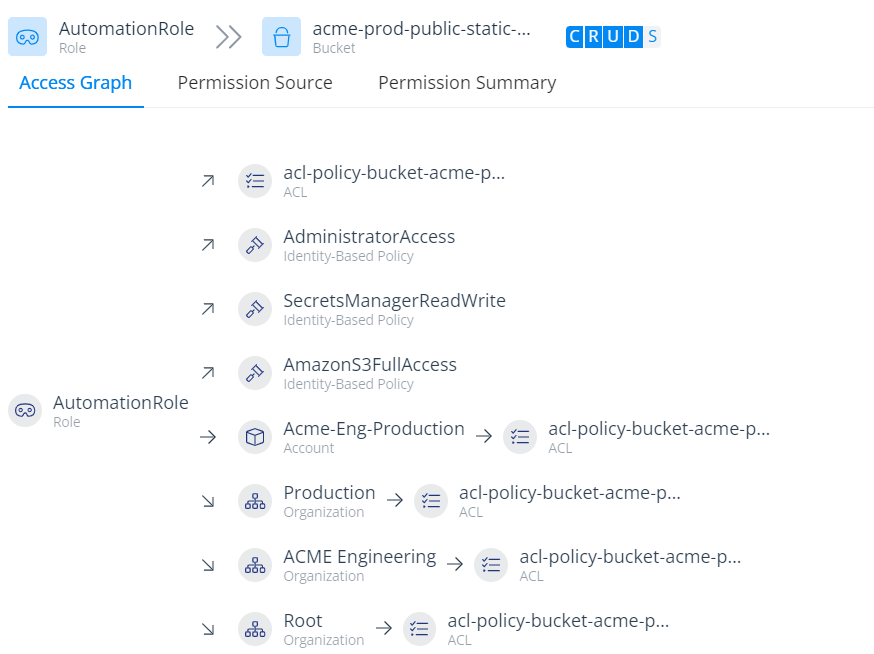 Understand how users gain access to critical cloud resources.
Understand how users gain access to critical cloud resources.
Use Varonis to understand exposure and enforce the principle of least privilege, helping ensure that only the right people have access to the right data in your AWS resources.
Monitor activity and catch threats.
Varonis monitors your cloud infrastructure and data for abnormal or risky activity that could indicate a threat. We can see activity such as abnormal asset deletions, dormant accounts becoming active, or privilege escalation.
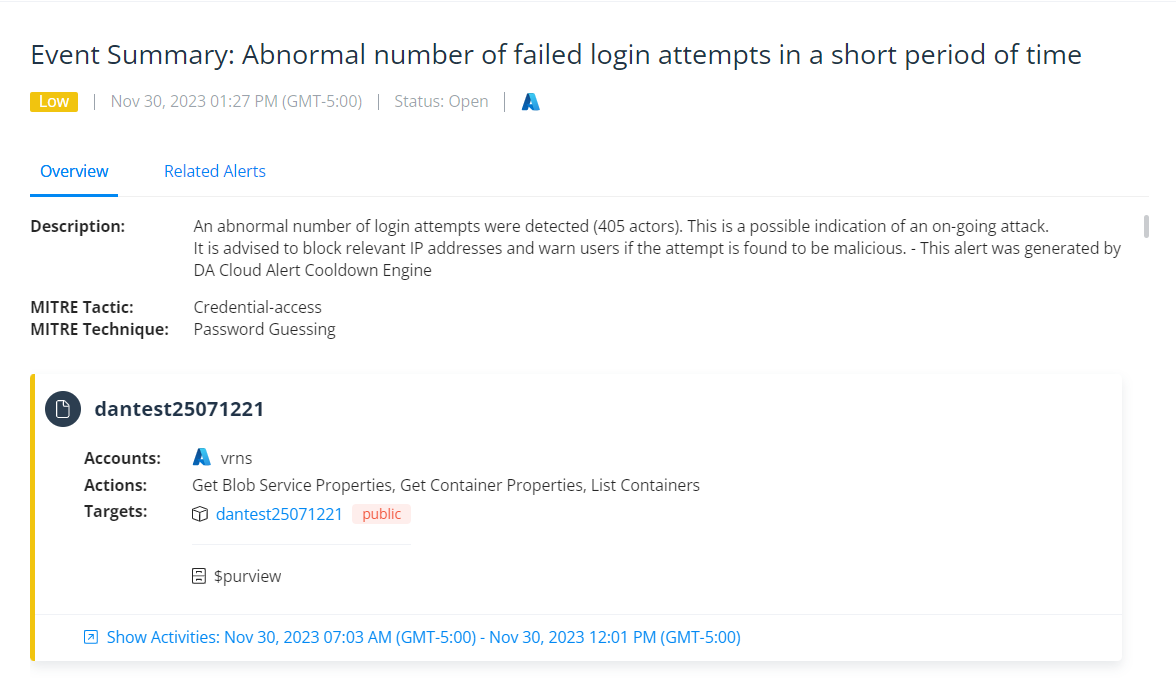 Varonis automatically detects risky or suspicious behavior and provides additional context to accelerate investigations.
Varonis automatically detects risky or suspicious behavior and provides additional context to accelerate investigations.
Varonis maps each alert to the relevant MITRE ATT&CK tactics and techniques to help security teams better understand the alert’s context, impact, and phase, enabling them to better investigate and respond to threats.
A granular cross-cloud audit trail of events makes it simple to understand how your data is being used and by whom, so you can easily investigate threats, including lateral movement, across your IaaS and SaaS environments. Speed up investigations by filtering the audit trail by privileged users, sensitivity, activity type, and more.
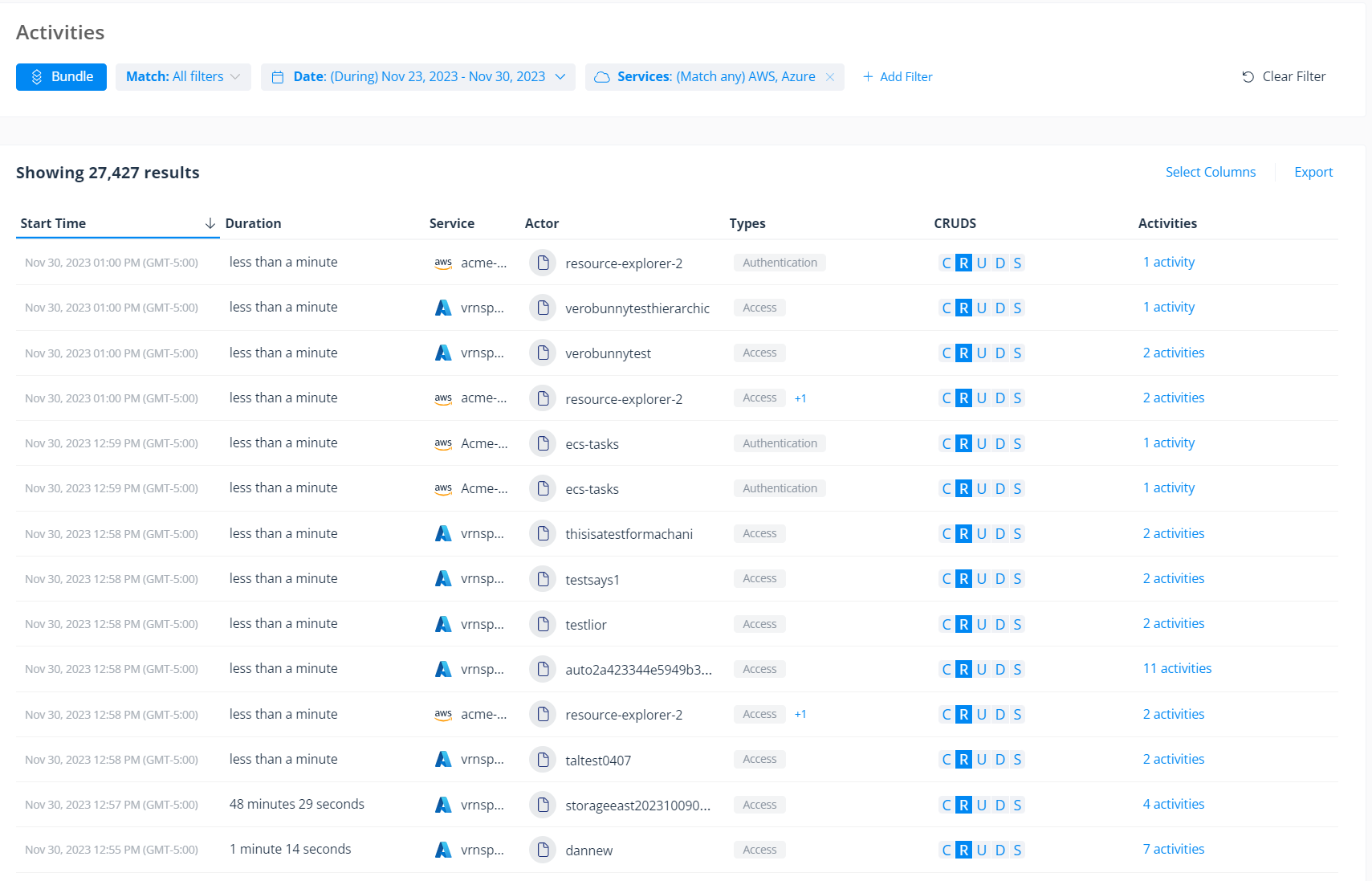 Varonis provides a complete cross-cloud audit trail to facilitate investigations and identify lateral movement.
Varonis provides a complete cross-cloud audit trail to facilitate investigations and identify lateral movement.
Third-party app risk management
With Varonis, security teams can easily discover all the third-party apps connected to their Azure environment — including unsanctioned applications added by users without IT approval — and gain a clear view of the risks they pose. Varonis enables organizations to better understand each app’s blast radius by mapping the permissions granted by users, monitoring app activity, and removing unsanctioned or unused app connections — right from a single console.
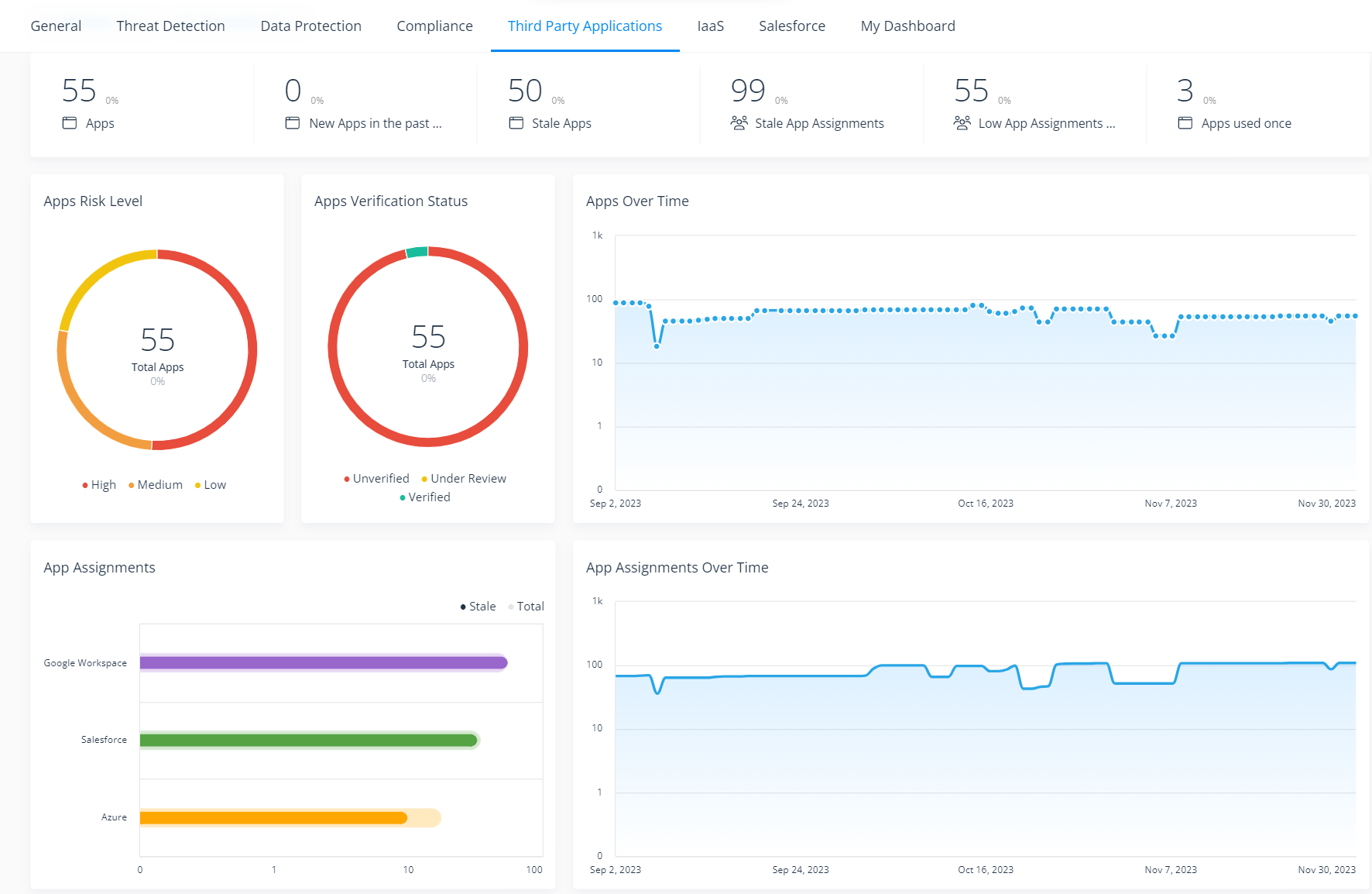 The third-party application risk dashboard provides an overview of third-party apps in your environment.
The third-party application risk dashboard provides an overview of third-party apps in your environment.
Drill down from this dashboard for a closer look at each app and the risks they pose; see what users are connected to them and whose connections to these apps are stale.
Comprehensive cloud and data security
Instead of siloed solutions that provide partial visibility, Varonis offers comprehensive data security across your IaaS and SaaS environments. This unified console helps your team easily monitor and manage data security posture and minimize data risk.
Try Varonis for free.
Ready to start improving your cloud and data security posture and secure your most sensitive cloud data? Request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









