MatrixPDF turns ordinary PDF files into phishing and malware delivery tools. It uses overlays, clickable prompts, and embedded JavaScript to bypass email filters and fetch malicious payloads.
Cybercriminals don't need to look for new exploits when they can weaponize what people already trust. PDF files are a prime example; they slip past email filters, render inline in Gmail, and most recipients open them without hesitation.
MatrixPDF, found on cybercrime networks, exploits that trust.
It bundles phishing and malware features into a builder that alters legitimate PDF files with fake secure document prompts, embedded JavaScript actions, content blurring, and redirects. To the recipient, the file looks routine, yet opening it and following a prompt or link can result in credential theft or payload delivery.
Introduction and toolkit overview
MatrixPDF is a new phishing and malware deployment toolkit that transforms ordinary PDF files into deceptive attack vectors. Its builder allows an attacker to load a legitimate PDF document as bait and augment it with malicious features.
Users of MatrixPDF can specify a payload URL (an external link that the PDF will invoke), enabling URL redirection to malware or phishing sites after the victim interacts with the file.
The toolkit also provides options to modify the document’s appearance for social engineering, such as adding a convincing title (e.g., “Secure Document”), a custom icon (like a padlock or corporate logo), and content blur overlays that conceal the real document content until the user “unlocks” it.
MatrixPDF builder with options for payloads, custom icons, & overlays
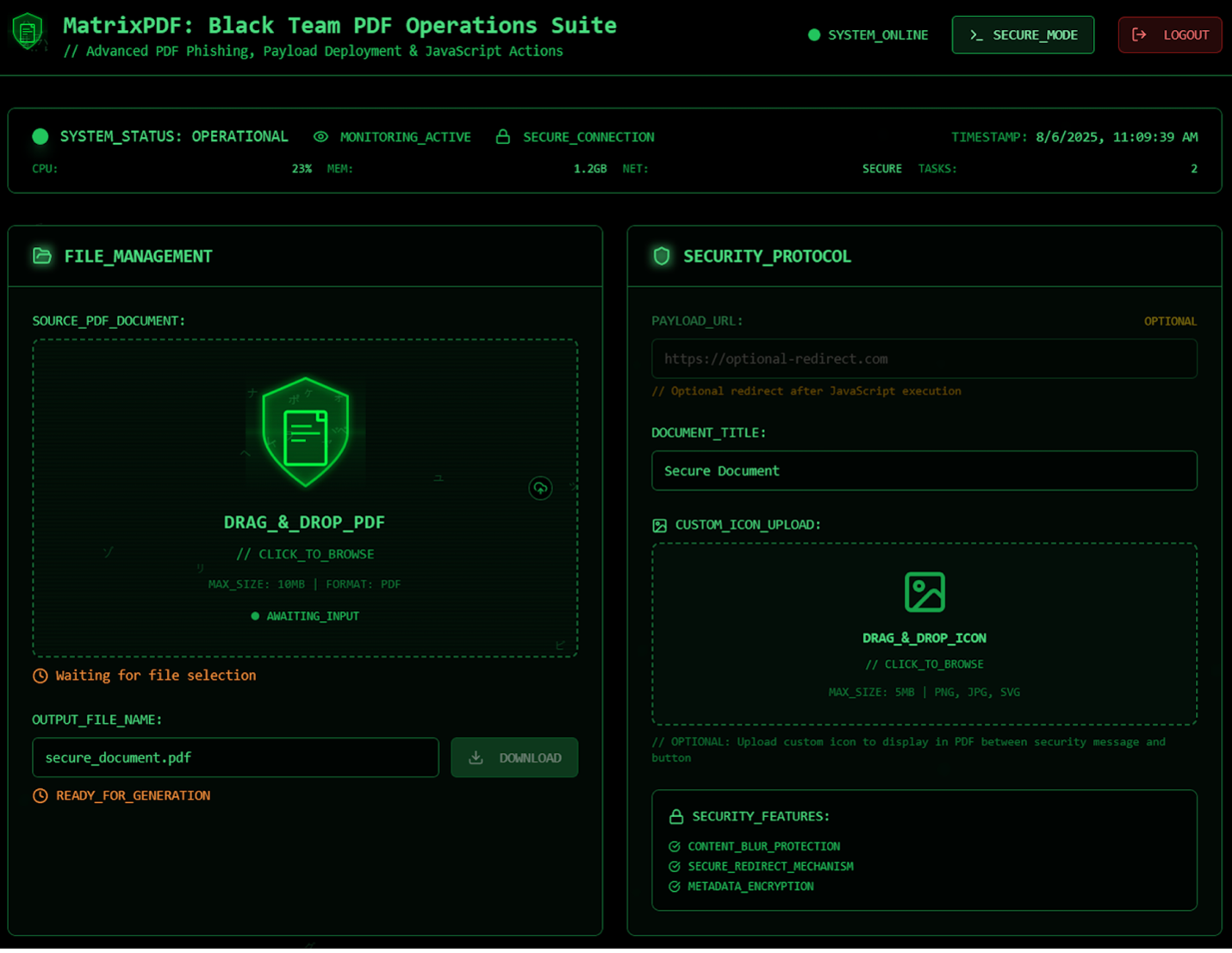
MatrixPDF builder with options for payloads, custom icons, & overlays
Beyond static content tweaks, MatrixPDF’s power lies in its ability to embed JavaScript into PDF files. Attackers can toggle on JavaScript actions within the document to execute code when the PDF is opened or clicked.
The toolkit can automatically open a specified website (the payload URL) when the victim clicks a prompt in the PDF, or even immediately upon document opening, depending on the configuration.
JavaScript actions in MatrixPDF, including fake prompts & redirect buttons
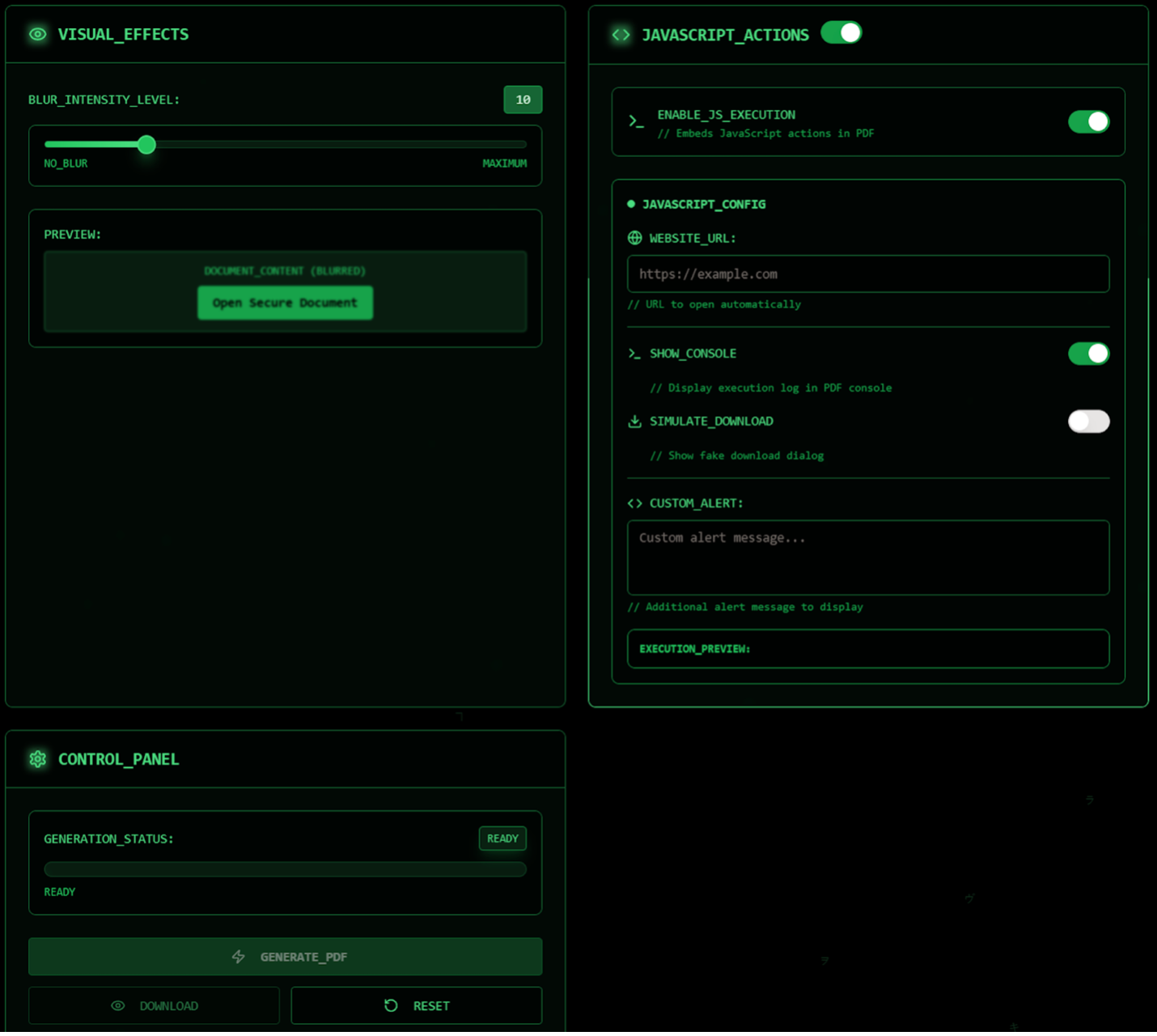
JavaScript actions in MatrixPDF, including fake prompts & redirect buttons
Other options include simulating system dialogs (e.g., a fake "download required" pop-up) and displaying custom alert messages to guide the user. These scripts effectively turn the PDF into an interactive lure.
We will look at two primary methods promoted with this toolkit below.
Method 1: Phishing link redirection via email PDF preview
In the first scenario, MatrixPDF-generated PDF files are designed to bypass email gateway filters and exploit the email client’s PDF preview to deploy malware. The attacker sends the backdoored PDF as an attachment. Email services like Gmail scan attached PDF files for known malware, but because the file contains no binary payload, only scripts and an external link, it often goes unflagged.
Gmail inbox showing the malicious PDF attachment passing initial scans
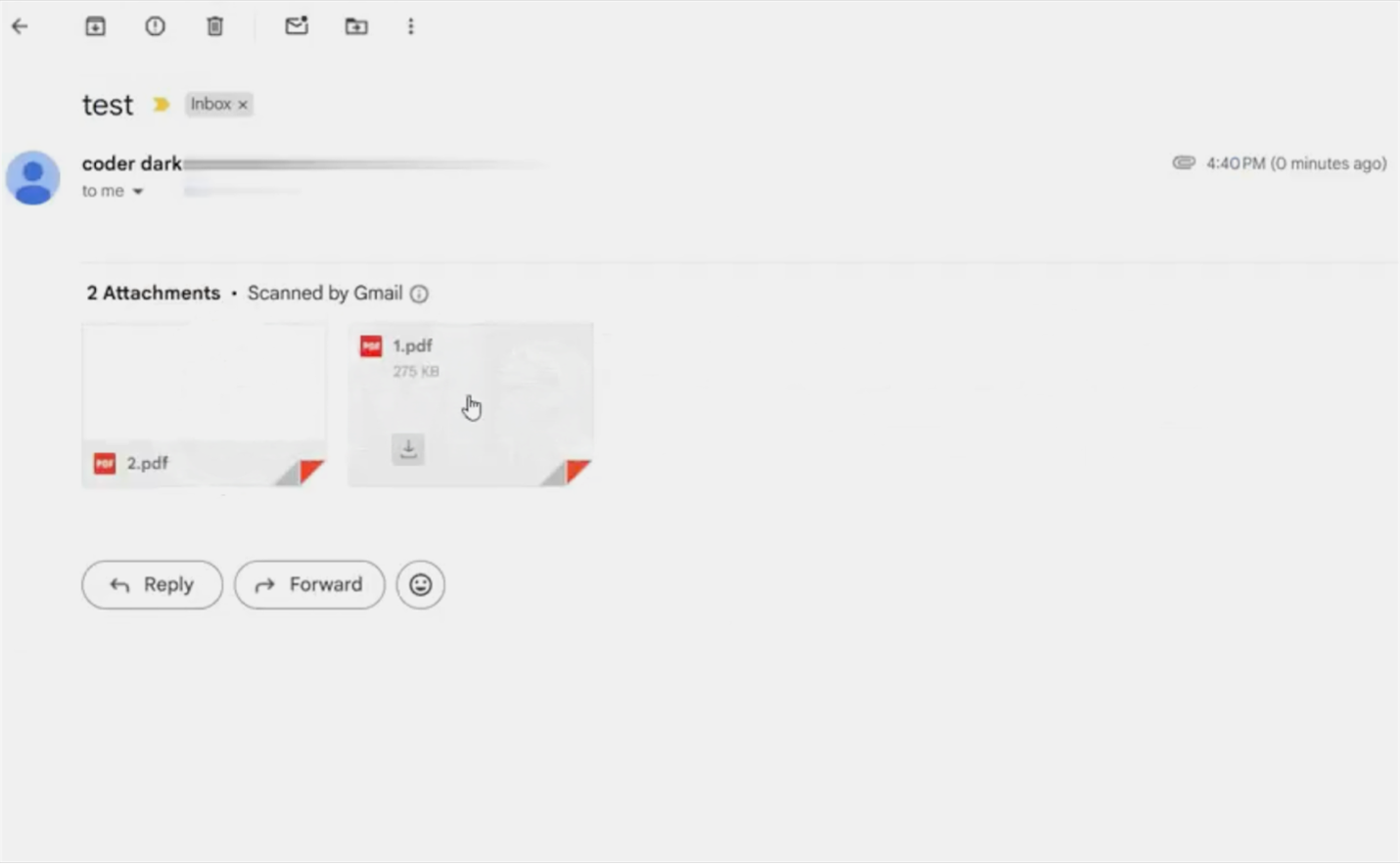
Gmail inbox showing the malicious PDF attachment passing initial scans
The PDF renders normally in Gmail’s web viewer, so the recipient sees no warning; the document text is blurred, and an overlay prompts the user to "Open Secure Document." That overlay is a phishing lure, implying the file is protected and convincing the user to click a link that can lead to credential theft or payload delivery.
Malicious PDF rendered in Gmail’s viewer with blurred content
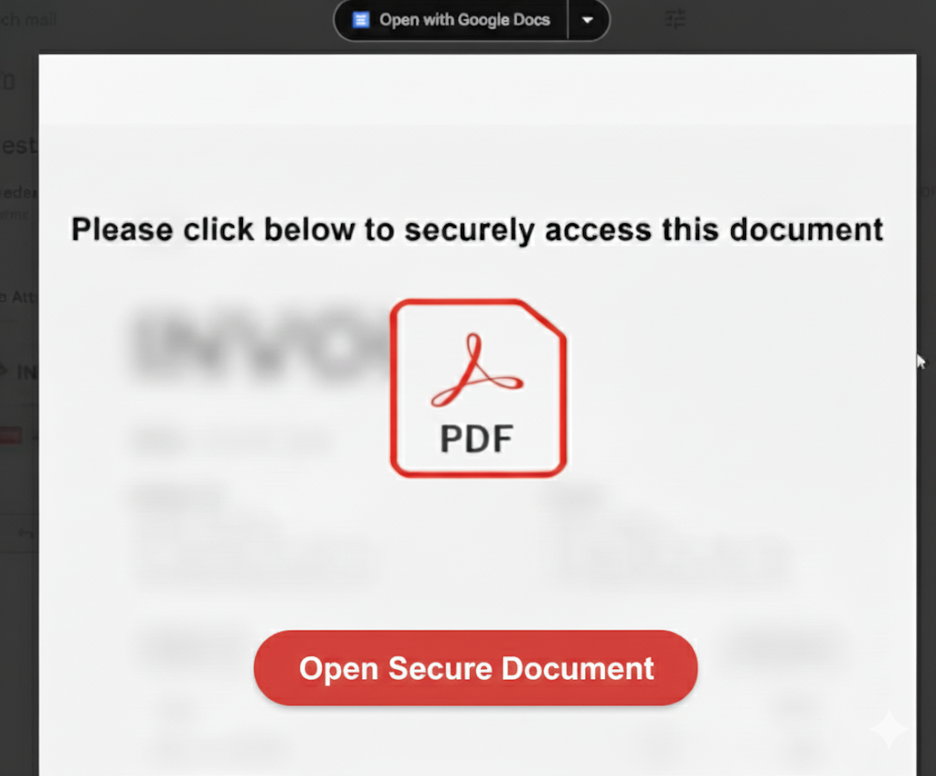
Malicious PDF rendered in Gmail’s viewer with blurred content
The malicious action is triggered when the victim clicks the Open Secure Document button in the PDF preview. In this scenario, MatrixPDF has configured the PDF to redirect the user to an external URL directly. Typically, this is achieved by embedding a clickable link or a script-driven button in the PDF rather than using a standard URL hyperlink object (a subtle evasion technique).
Gmail’s PDF viewer does not execute PDF JavaScript but allows clickable links/annotations. Thus, the attacker’s PDF is created so the button press simply opens an external site in the user’s browser. This somewhat clever design works around Gmail’s security: any malware scanning of the PDF itself finds nothing incriminating, and the actual malicious content is only fetched once the user actively clicks, appearing to Gmail as a user-initiated web request.
User redirected from PDF to an external download (example: PuTTY client)
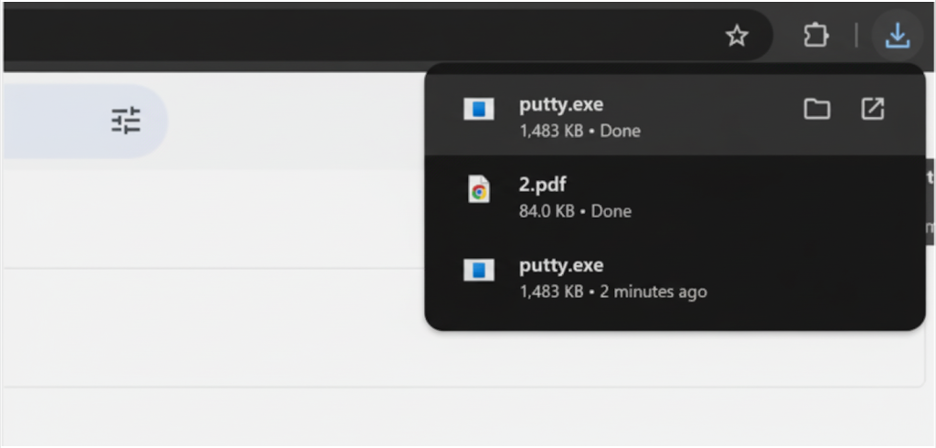
User redirected from PDF to an external download (example: PuTTY client)
In our example, the PDF’s embedded link points to a download for PuTTY (a legitimate SSH client) hosted on a public site. This download is a stand-in for a malware payload, a malware-laden executable under the attacker’s control in a real attack.
Importantly, because the user clicked a link in the PDF, the file download happens outside the email platform’s regular antivirus sandbox. Gmail’s viewer hands off the request to the web browser, so any file fetched is treated like a direct download initiated by the user. The email security filters that normally might block an attachment like an .exe never get a chance to intervene.
From the victim’s perspective, the workflow seems plausible: they clicked a button in what looked like a secure document process, and a file started downloading. Without careful attention, they may not realize that this file is malicious. This technique capitalizes on user trust in PDF files and their email service, and it shows how attackers can split an attack across an email (for delivery) and the web (for payload retrieval) to evade detection.
Method 2: Malicious PDF JavaScript action on documentopen
The second attack method supported by MatrixPDF involves a more direct use of PDF-embedded JavaScript to deliver malware. In this scenario, the victim downloads or opens the PDF in a desktop PDF reader (e.g., Adobe Acrobat) or a browser’s native PDF viewer that allows script execution.
MatrixPDF can insert a document-level script or interactive form action that runs when the PDF is opened or when a user clicks within it. Typically, the PDF will attempt to connect to the attacker’s payload URL automatically and fetch a file.
When the victim opens the backdoored PDF, most PDF readers will display a security warning informing the user that the document is trying to access an external resource. In our scenario, the PDF was configured to reach a short URL.
Using an innocuous-looking short domain (ln.run, for example) can be a social engineering ploy. The domain might not immediately raise an alarm or may, in fact, look vaguely legitimate. As shown below, the victim is confronted with a pop-up dialog asking for permission.
Desktop PDF reader displaying a warning of an external connection
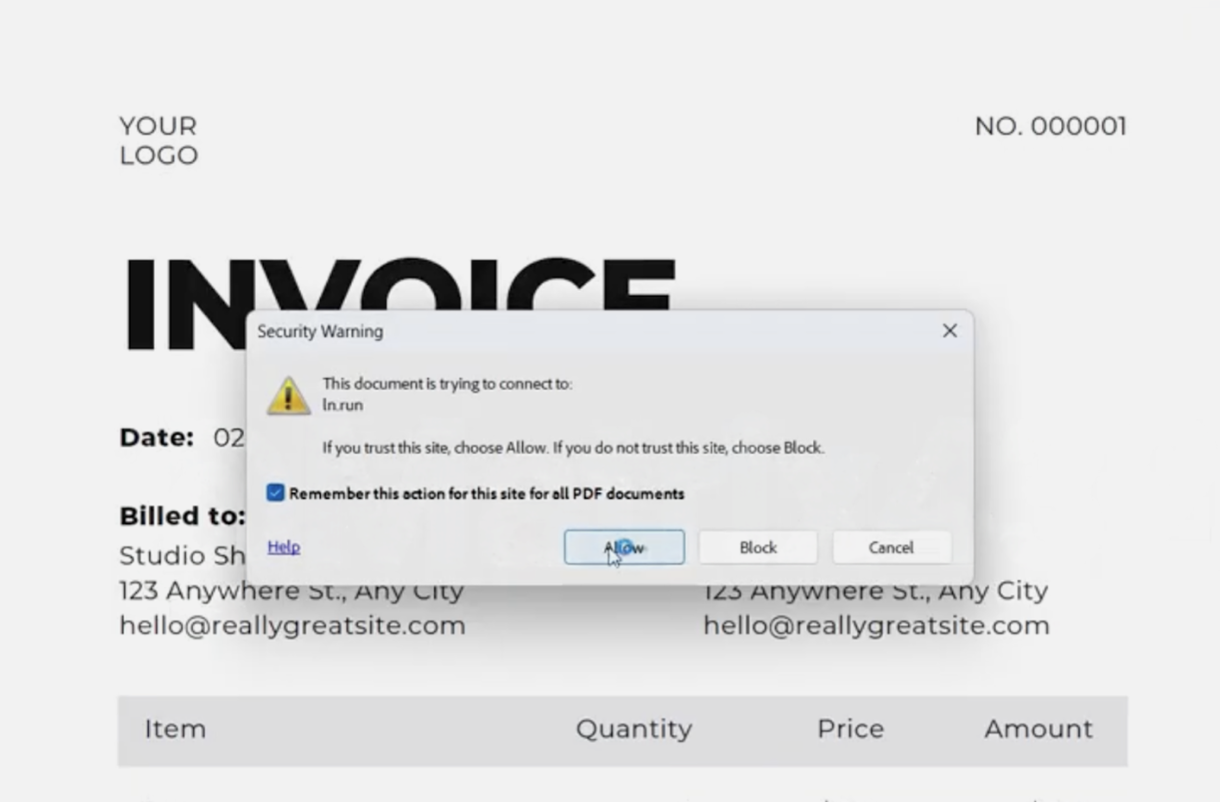
Desktop PDF reader displaying a warning of an external connection
If the user clicks “Allow,” the PDF’s embedded script fetches the payload from the specified URL. Under the hood, this might be implemented via an Acrobat JavaScript API call (e.g., app.launchURL() or a form submission action) that initiates a download. Once allowed, the malicious file will be retrieved from the internet and saved to the user’s device.
At this point, the attack is identical to any drive-by download. The victim has a malware executable on their system, delivered under the pretense of accessing a secure document. In our example, approving the connection led to downloading the same putty.exe file.
Payload downloaded after the user allows the connection

Payload downloaded after the user allows the connection
This method is potent because it doesn’t rely on the user clicking a link in a browser; instead, the PDF actively initiates the download. However, it does hinge on the user granting permission in the security dialog.
Unfortunately, many users are accustomed to clicking “Allow” when prompted, especially if the prompt and the document’s context convince them it’s necessary to view a secure file. The phrase “document is trying to connect...” can be misunderstood by non-technical users, who might approve it out of trust.
Stopping PDF-based attacks with AI email security
AI-powered email security solutions can stop attacks like MatrixPDF by analyzing attachments and links for intent rather than relying on signatures. These systems inspect the structure of a PDF, flagging anomalies like blurred content, fake secure document prompts, or buttons tied to hidden links. Suspicious connection attempts and domains are extracted and tested in isolation, making it far more challenging for malicious files to pass as safe in traditional filters.
They also go beyond static checks by safely simulating the attack in a cloud sandbox. Every embedded URL is opened in a virtual browser, with the page fully rendered and scripts allowed to run. This reveals tactics like the “Open Secure Document” redirect to a payload site or JavaScript actions that try to fetch malware.
AI-powered defenses can detect and block the entire attack process before it reaches your inbox, using tools like natural language processing and advanced analysis.
Interested in using Varonis for email security? Schedule a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







