Put Least Privilege on Autopilot
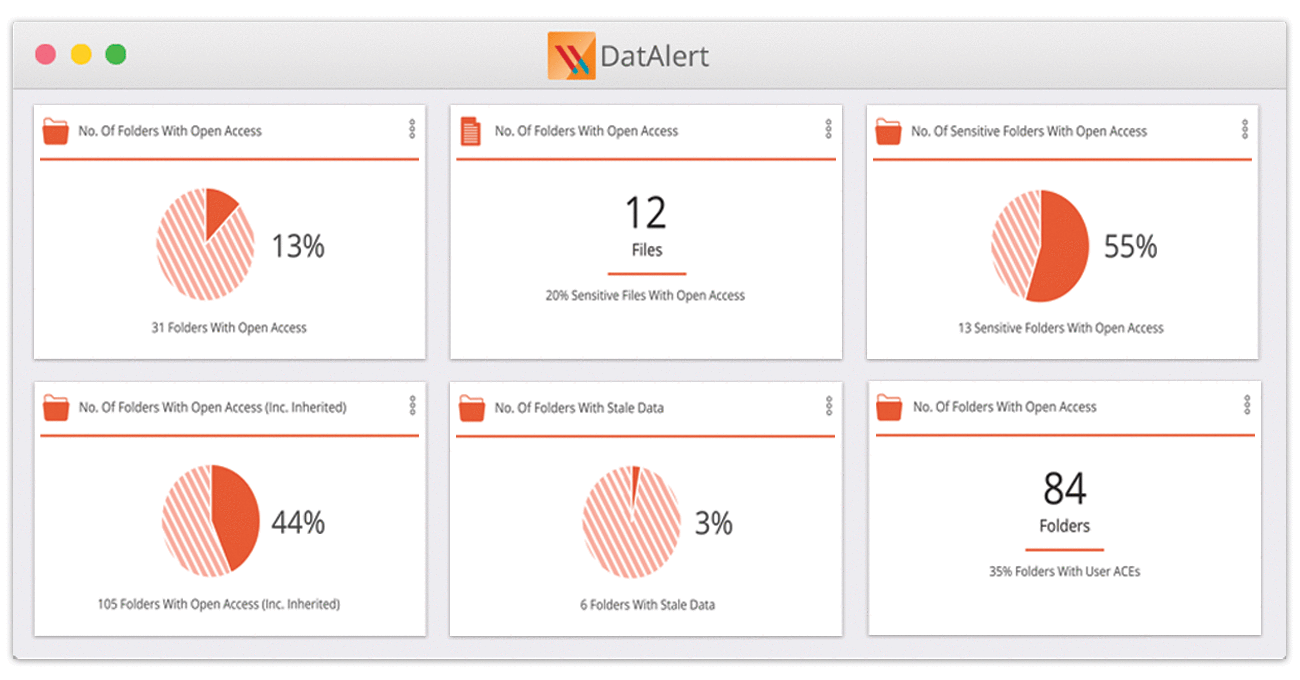
Getting to least privilege can be a nightmare. The first steps – tracking down inconsistent ACLs and remediating global access groups can turn even the most basic file share clean-up project into a huge to-do.
And so we’re thrilled to announce the upcoming availability of the Automation Engine, which will take the headache out of least privilege by discovering undetected security threats and fixing hidden vulnerabilities without all the manual legwork.
The Varonis Automation Engine automatically repairs and maintains file systems so that you’re less vulnerable to attacks, more compliant, and consistently enforcing a least privilege model.
- Fix hidden security vulnerabilities like inconsistent ACLs and global access.
- Revoke unnecessary access that users no longer need or use, reducing your risk profile.
- Accelerate and automate least privilege.
Interested? Get a demo now and be the first in line to try it.
What’s past is prologue
One of our earliest patents was our simulation capability in DatAdvantage – which our customers now use consistently to test access control changes against past access activity, highlighting users that would be disrupted or applications that might break if they had made those changes in the past.
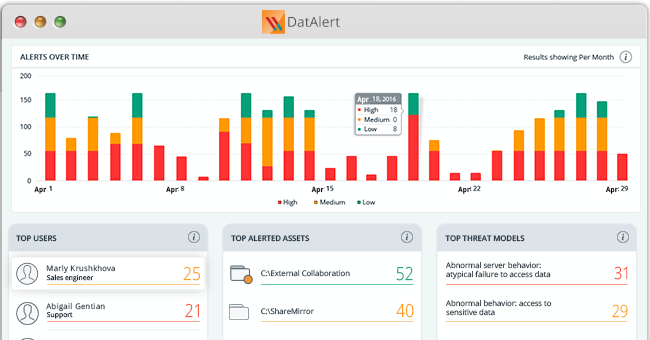
We’re extending our simulation capabilities with Analytics Rewind.
DatAlert Analytics Rewind allows customers with three or more months of data to analyze past user and data activity with DatAlert threat models, and identify alerts that they would have gotten in the past. You can not only pre-emptively tune out false positives, but also look back at your data activity history to identify breaches that may have already occurred.
New Threat Models for Exchange and DS
You asked, we listened. We’re adding more threat models to DatAlert Analytics to detect and prevent impersonation, exploitation, and account hijacking. The latest set keeps you aware of suspicious mailbox and Exchange behaviors, password resets and unusual activity from personal devices.
Email security and Exchange: New threat models flag abnormal amount of emails sent to accounts outside the organization, unusual mailbox activity from service accounts, and automated forwarding that might indicate an attacker trying to redirect and exfiltrate data.
Directory Services: New threat models detect suspicious password resets that may indicate attempts to hijack a user account, unusual access to personal devices, suspicious attempts to access an unusual amount of resources, and unusual login activity that may indicate a credential stuffing attack.
Want to see them in action? Get a demo our data security platform and see how you can stop data breaches.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.