We recently uncovered GoIssue, a tool marketed on a cybercrime forum that allows attackers to extract email addresses from GitHub profiles and send bulk emails directly to users’ inboxes.
GoIssue signals a dangerous shift in targeted phishing that extends beyond individual developers to threaten entire organizations.
This sophisticated tool, potentially linked to the GitLoker extortion campaign, represents more than just another phishing threat – it's a gateway to source code theft, supply chain attacks, and corporate network breaches through compromised developer credentials.
For CISOs and security teams, its emergence highlights how development platforms have become security battlegrounds, especially concerning their connection to attacks using malicious OAuth apps to hijack repositories.
While GitHub users are the immediate targets, the implications ripple throughout organizations, turning trusted developer access into potential organizational vulnerabilities that could compromise entire digital transformation initiatives.
What GoIssue does
GoIssue represents a clear evolution in GitHub-focused attack tools, designed to orchestrate large-scale phishing campaigns while maintaining anonymity.
At its core, the tool systematically harvests email addresses from public GitHub profiles, using automated processes and GitHub tokens to collect data based on various criteria - from organization memberships to stargazer lists.
With this information, attackers can launch customized mass email campaigns to bypass spam filters and target specific developer communities. Schedule a demo to learn how to defend against GoIssue.
The official advertisement for Goissue
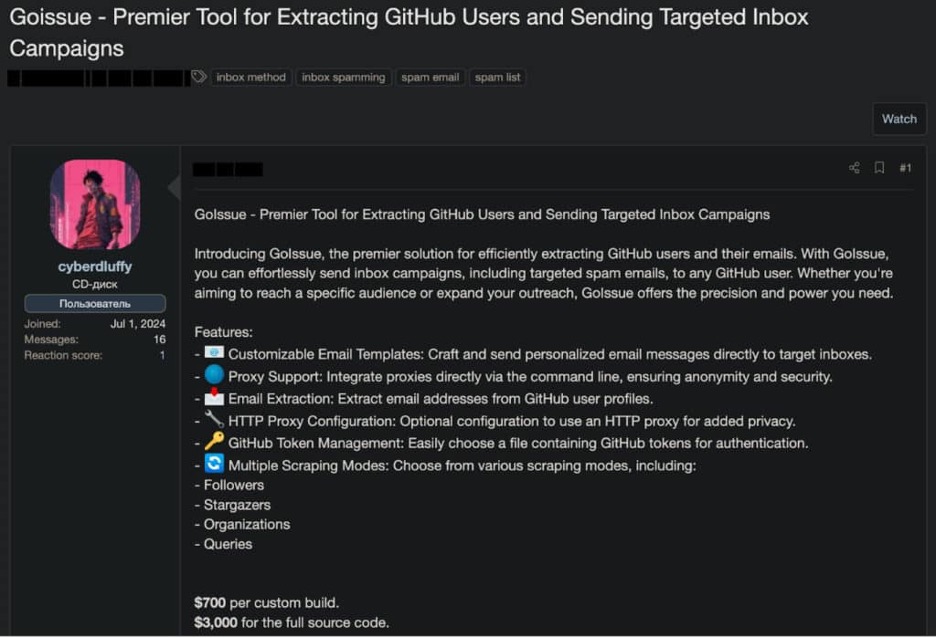
The official advertisement for Goissue
Marketed to potential attackers at $700 for a custom build (or $3,000 for full source code access), GoIssue combines bulk email capabilities with sophisticated data collection features while protecting the operator's identity through proxy networks.
This approach allows attackers to move beyond simple email scraping to execute complex, targeted campaigns against the GitHub developer community. Buyers are encouraged to contact the seller, cyberluffy, through private messages on the forum or via Telegram.
How attackers could use GoIssue
A typical GoIssue attack could begin with harvesting email addresses from public GitHub profiles and mass phishing campaigns using fake GitHub notification emails. These spam-filter-evading messages would target developers' inboxes with malicious links that could lead to:
- A phishing page designed to steal login credentials.
- A malware download that compromises the user’s device.
- A rogue OAuth app authorization prompt that grants attackers access to private repositories and data.
GoIssue’s ability to send these targeted emails in bulk allows attackers to scale up their campaigns, impacting thousands of developers simultaneously. This increases the risk of successful breaches, data theft, and compromised projects.
The link to GitLoker attacks
The contact information for GoIssue led us to Cyberluffy, whose Telegram profile states, “Cyber D' Luffy is a member of Gitloker Team.” This detail is significant because GitLoker is responsible for an ongoing campaign that uses GitHub notifications to push malicious OAuth apps.
The seller’s contact information, which aligns with Gitloker
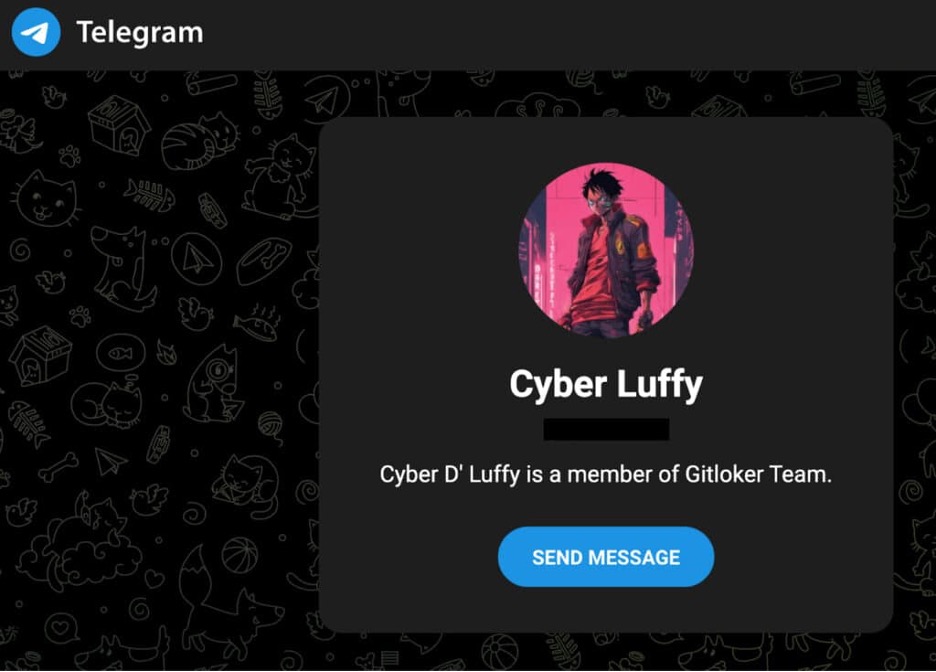
The seller’s contact information, which aligns with Gitloker
In the thread advertising GoIssue, the seller even links to high-profile security blogs that detail and validate GitLoker attack efficacy, which targeted developers using GitHub notifications and phishing emails.
The GoIssue forum thread referencing cybersecurity blog articles
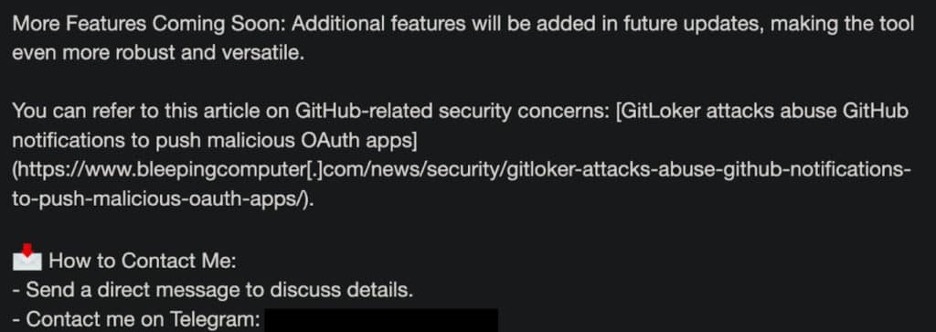
The GoIssue forum thread referencing cybersecurity blog articles
The connection between Cyberluffy and the GitLoker Team suggests that GoIssue could be an extension of the GitLoker campaign or an evolved version of the same tool.
Both tools share a similar target audience (GitHub users) and leverage email communication to initiate attacks. This overlap in purpose and personnel strongly supports the theory that they are either linked or variations of one another.
If you’re a developer using GitHub, GoIssue is a red flag. Attackers now have tools that make phishing easier and more effective. This isn’t just spam; it’s a potential entry point to taking over your account or projects. With GoIssue potentially linked to GitLoker, the threat is bigger than ever.
Defeat phishing with Varonis
Attackers can quietly access your most sensitive data with just one stolen credential. Varonis helps you shut down these threats quickly by automatically fixing exposures, detecting abnormal behavior, and reducing risk without manual effort.
See how Varonis stops threats before they become breaches — request your demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








-1.png)