As organizations increasingly migrate to the cloud and data breaches make headlines regularly, it has become paramount for organizations to ensure their cloud infrastructure and the sensitive data within remain secure.
Cloud Security Posture Management (CSPM) focuses on identifying and remediating misconfigurations within cloud environments, and Data Security Posture Management (DSPM) zeroes in on protecting sensitive data across various platforms. Understanding the distinct roles and complementary nature of DSPM and CSPM is crucial for building a robust cloud security strategy.
In this article, we'll delve into the core functions of both DSPM and CSPM, explore how they differ, and discuss how integrating these solutions can provide comprehensive protection for your organization's cloud assets and data.
DSPM and CSPM: How do they differ?
DSPM safeguards sensitive data across all environments, whether in SaaS applications, cloud platforms, or on-premises systems. Its core objective is to ensure data security and regulatory compliance wherever data resides. DSPM employs comprehensive strategies, including data discovery and classification, rigorous access controls, and continuous monitoring, to secure sensitive information.
In contrast, CSPM focuses on the cloud infrastructure itself, adopting a vulnerability-centric approach. CSPM tools actively scan and analyze cloud environments, identifying misconfigurations and security weaknesses that could expose organizations to risk. By assigning risk scores, CSPM prioritizes remediation efforts, automates patching processes, ensures infrastructure compliance, and proactively adapts to emerging threats.
Together, DSPM and CSPM form a robust security framework essential for protecting sensitive data and maintaining a resilient cloud infrastructure.
Key capabilities of DSPM
DSPM provides organizations with the tools and capabilities needed to identify, assess, monitor, and protect sensitive data throughout its lifecycle. This helps organizations understand where sensitive data is located, who has access to it, how it is being used, and whether it is adequately protected.
The core components of DSPM typically include:
- Data discovery and classification: DSPM automates scanning and discovery techniques to locate sensitive data wherever it resides and categorize the data based on its sensitivity and type, allowing organizations to prioritize security measures and better manage compliance efforts.
- Data access governance: DSPM maps permissions across the data estate and enables organizations to define and enforce access policies and permissions that ensure only authorized individuals can access sensitive data. DSPM also provides automated remediation of permissions to reduce data exposure and achieve a least privilege model.
- Data Risk Assessment: DSPM assesses data security risks by evaluating factors such as data exposure, vulnerabilities, and compliance with data protection regulations. These tools provide risk levels and recommendations for remediation.
- Compliance reporting and auditing: DSPM generates compliance reports and audit logs to help organizations stay compliant with various regulatory frameworks, such as GDPR, HIPAA, or CCPA. These reports are essential for regulatory audits and internal governance.
- Activity monitoring and threat detection: DSPM monitors data to identify unusual or suspicious activity like excessive or unauthorized access, encryption, and potential exfiltration. This helps organizations detect insider threats, ransomware, and advanced persistent threats.
- Incident response and remediation: DSPM provides incident response capabilities to address security incidents and data breaches quickly. These tools may automate response actions, such as removing access or shutting down affected systems and user sessions.
- AI security monitoring: DSPM solutions should monitor AI-assisted tools to ensure they don’t access or expose sensitive data inappropriately. Capabilities should include monitoring prompt activity, detecting anomalous behavior, and enforcing data access policies for AI and service accounts.
By implementing these core components across your ecosystem, a DSPM approach empowers businesses to identify and reduce data risk, maintain compliance, and mitigate the risk and impact of breaches.
Key capabilities of CSPM
A CSPM strategy helps organizations proactively reduce the risk of exploitation, automate remediation processes, ensure compliance, and adapt to evolving threats. This approach is crucial for maintaining a strong security posture in dynamic cloud environments.
The core components of CSPM typically include:
- Asset discovery: CSPM automatically discovers and inventory all assets within an organization's cloud environment. This includes virtual machines, storage buckets, databases, network configurations, and more. Accurate asset discovery is crucial for assessing the security of cloud resources.
- Configuration management: CSPM evaluates the security configurations of cloud assets against industry best practices and compliance standards, such as CIS benchmarks or cloud-specific security guidelines. This approach identifies misconfigurations that could expose assets to vulnerabilities or unauthorized access and provides the necessary steps for remediation.
- Vulnerability assessment: CSPM performs regular vulnerability scans of cloud resources to detect known weaknesses. These solutions provide organizations with vulnerability scores and can prioritize remediation efforts based on the severity of the issues.
- Remediation and reporting: CSPM provides guidance and recommendations for the remediation of identified security issues. These solutions offer reports and dashboards to help organizations track their security posture over time and demonstrate compliance to auditors. Certain solutions even provide automated remediation capabilities.
- Network security assessment: CSPM evaluates network security controls, including firewall rules, network segmentation, and traffic monitoring, to detect any potential security gaps or misconfigurations in the cloud network infrastructure.
- Compliance monitoring: CSPM continuously monitors cloud resources for compliance with industry-specific regulations and standards, such as GDPR, HIPAA, or SOC 2. It generates compliance reports and alerts organizations when non-compliance is detected through configuration drift.
- Threat detection and response: Some CSPM solutions offer threat detection capabilities by analyzing cloud logs and network traffic patterns to identify suspicious activities or potential security incidents. These solutions may also provide automated response actions.
CSPM is essential for organizations adopting cloud services to ensure that their cloud environments are secure, compliant, and resilient to threats. This approach helps organizations proactively manage security risks and maintain a strong security posture as they leverage cloud technologies for their business operations.

DSPM vs. CSPM: Two essential components for a complete cloud security strategy
The complexities of securing both cloud environments and the data within underscore the need for a security strategy that implements both DSPM and CSPM solutions, ensuring they work in unison.
DSPM solutions enable organizations to monitor and protect sensitive data wherever it resides, while CSPM focuses on securing the cloud infrastructure itself and closing the pathways to the data within. These two solutions complement each other, providing comprehensive security coverage in an era where cyber threats are constantly evolving.
Unified visibility
Together, DSPM and CSPM solutions can provide a holistic view of an organization's entire security landscape, including both data and cloud assets. By integrating data discovery and asset discovery, organizations gain a unified understanding of where their sensitive data resides and how it is stored, accessed, and protected within their cloud environments.
Configuration and exposure management
CSPM solutions can help identify misconfigurations or vulnerabilities within cloud environments that may expose sensitive data to security risks. When such risks are identified, DSPM solutions can determine if sensitive data is at risk and provide insights into its exposure, thereby enabling timely remediation.
Compliance management
Both DSPM and CSPM are instrumental in ensuring compliance with regulatory standards and security best practices. These strategies work together to monitor and enforce compliance policies across data and cloud assets, providing a comprehensive approach to compliance management to help reduce the risks of penalties and fines.
Incident response
In the event of a security incident in the cloud, CSPM can quickly detect the breach and initiate response actions. Simultaneously, DSPM can detect if sensitive data has been compromised and provide the tools and guidance needed to investigate and contain the breach, mitigate risks, and report any potential data leaks.
Security automation
Integrating DSPM and CSPM solutions can facilitate automated responses to identified security issues. When vulnerabilities or misconfigurations are detected in the cloud environment, automated actions can be initiated to minimize potential data exposure.
Enhanced reporting and auditing
Organizations can use DSPM and CSPM to generate comprehensive reports that not only demonstrate compliance with data protection regulations but also provide insights into the security of data and cloud resources. This reporting can be crucial for internal governance and regulatory audits.
By integrating CSPM and DSPM solutions, organizations create a unified security strategy that bridges the gap between data and cloud security, offering a comprehensive approach to protecting sensitive data in an increasingly cloud-centric world. This collaboration ensures that data remains secure and compliant, regardless of where it's stored or how it's accessed.
Strengthen your security posture with Varonis.
The Varonis Data Security Platform offers a comprehensive solution for data and cloud security by discovering and classifying sensitive data across your hybrid environment, whether in the cloud, across clouds, or on-premises. Varonis uses highly accurate classification policies tailored to meet regulations, such as NIST, HIPAA, SOX, and GDPR, to identify and manage potential data risks.
Varonis continuously assesses your cloud and data security posture across your infrastructure with a real-time, customizable DSPM dashboard. This dashboard helps you identify unnecessary pathways to sensitive data, whether through excessive access, third-party app connections, or misconfigurations.
Varonis DSPM dashboards provide real-time, prioritized views of data risk and how it changes over time.
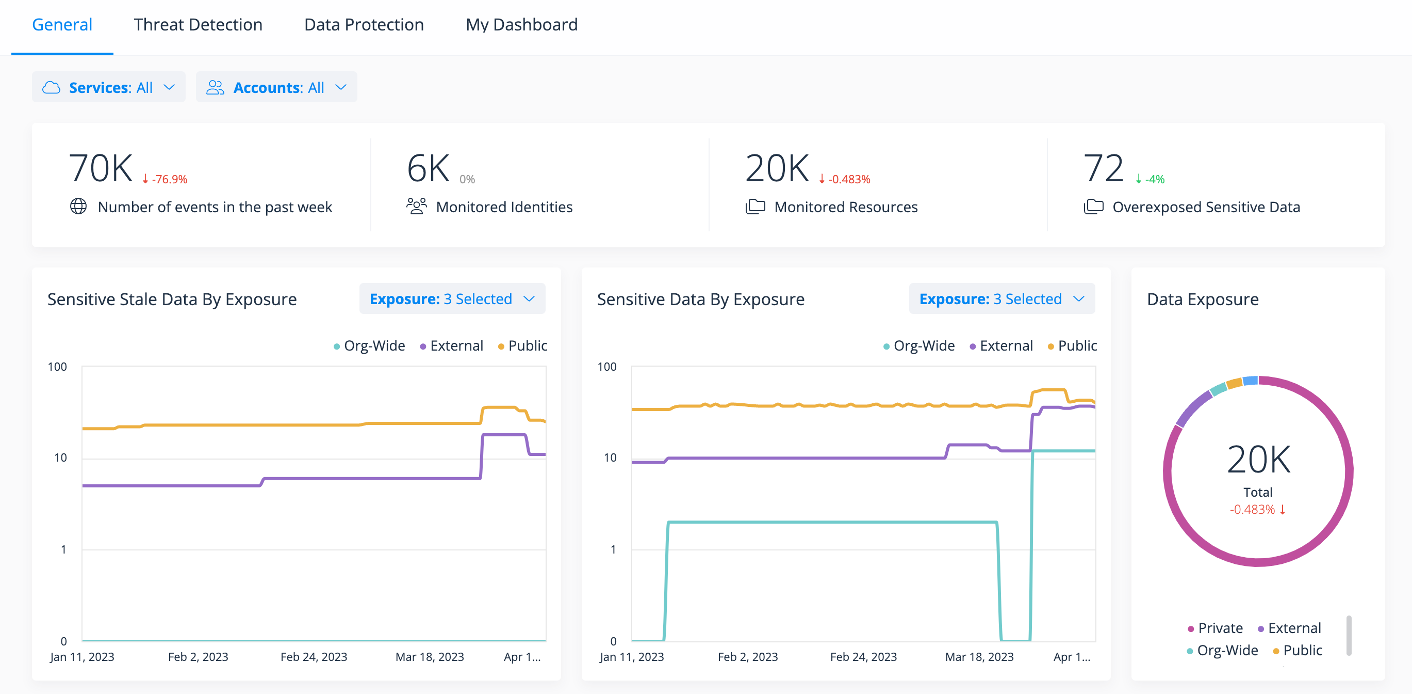
Varonis DSPM dashboards provide real-time, prioritized views of data risk and how it changes over time.
Our SaaS platform automatically detects misconfigurations that could expose your cloud environment and data to risks, such as publicly exposed buckets, weak password policies, and overly permissive IAM settings. Varonis assigns each misconfiguration a severity level and provides immediate steps for remediation. Users can even fix certain misconfigurations automatically with a simple click of a button, right from the Varonis interface.
Varonis dives deep into data, continuously analyzing permissions across various data stores, from SaaS and IaaS to on-premises—with support for multi-cloud and hybrid cloud infrastructure. This granular analysis reveals where sensitive data is exposed internally, externally, or publicly, showing who has access, what level of access they have, and how they obtained it. Varonis excels at automated remediation, enabling you to continuously remediate excessive and stale access to data at scale to limit the impact of a potential breach.
Data activity is also monitored and normalized, creating a human-readable, cross-cloud audit trail of events. You'll receive alerts about abnormal or risky activities, such as unusual or excessive access to sensitive data, potential exfiltration events, privilege escalations, and changes to critical configurations.
Varonis will automatically alert you and limit unusual activity that could lead to a data breach.
Varonis will automatically alert you and limit unusual activity that could lead to a data breach.
Every Varonis customer gains access to our Managed Data Detection & Response (MDDR) team, which provides a dedicated cybersecurity expert to monitor data for threats, investigate alerts, and only surface genuine incidents requiring immediate attention. This proactive approach means Varonis can help you quickly detect and respond to threats before they take hold, mitigating the potential impact of a breach and enhancing your overall security posture.
DSPM vs. CSPM FAQs
What is the goal of DSPM?
While DSPM is often associated with data discovery, its ultimate purpose is to proactively prevent data breaches by securing sensitive data and reducing risk.
What is the goal of CSPM?
CSPM is a security practice that continuously scans cloud infrastructure to detect and remediate misconfigurations, vulnerabilities, and compliance gaps.
Is DSPM focused on infrastructure as a service (IaaS)?
DSPM goes beyond just IaaS. An effective solution provides visibility into where sensitive data resides across your entire cloud environment, including IaaS, SaaS applications, databases, and cloud file storage, ensuring comprehensive protection regardless of where the data lives.
What’s the difference between CSPM and DSPM?
CSPM focuses on securing the cloud infrastructure. DSPM focuses on the security of the data itself by examining sensitivity, access, identity, and activity.
How does DSPM support compliance requirements?
DSPM maps exposures and security posture to relevant compliance frameworks like CMMC, GDPR, and HIPAA. It provides continuous monitoring of sensitive data locations and access controls to maintain ongoing compliance. This is increasingly important as global data privacy regulations become more stringent and penalties increase.
What role does automation play in DSPM?
Automation makes it possible to scale security operations. Manual remediation of a single misconfigured file can take hours. Effective DSPM automatically discovers new sensitive data as it's created and continuously monitors changing permissions. Without automation, organizations cannot realistically keep pace with cloud data sprawl and evolving security threats.
How does DSPM help secure AI tools like copilots and chat assistants?
Modern DSPM solutions extend data protection to AI-assisted tools by monitoring how they access and interact with sensitive data. This includes tracking prompt activity, detecting unusual behavior from AI accounts, and enforcing strict data access controls to prevent misuse or unintended data exposure.
Get started with Varonis





.png)



