Cyberattacks are not about firewalls or brute-force hacks anymore. They’re about credentials — and what those credentials can access once compromised.
Whether it’s a user, service account, or API key, attackers exploit identity to reach data. In fact, 57% of cyberattacks begin with compromised credentials, not malware or zero-days.
In this blog, we’ll build on insights from a recent Varonis webinar to expand on the importance of catching threats in cloud environments like AWS, Azure, Google Cloud, and hybrid environments.
Identity is the new perimeter
Most breaches start with a login.
Whether it’s a misconfigured IAM role in AWS, an over-permissioned service principal in Azure, or a forgotten Google service account, attackers are targeting identity first. Once inside, they exploit the blast radius: everything that identity can touch.
The problem? Most posture tools don’t connect the dots between identities and data. They show you where sensitive data lives and where configurations are weak, but they don’t tell you who can access what or how that access is being used.
In the Snowflake breach campaign, attackers used stolen credentials to access cloud environments and exfiltrate customer data. The breach didn’t rely on advanced exploits — just logins.
How Varonis identity protection is different
Varonis Identity Protection allows you to monitor identities across cloud data stores and applications with the most advanced identity threat detection and response capabilities on the market. Key features include:
- Resolving identities across AWS, Azure, GCP, and SaaS apps like Salesforce and Microsoft 365
- Mapping entitlements to actual data access, not just theoretical permissions
- Automating least privilege enforcement at scale, reducing exposure without breaking workflows
Without identity resolution, you’re flying blind. And in a world of federated access and single sign-on, one compromised identity can open the door to dozens of systems. Read more about Varonis’ GigaOm award for Identity Threat Detection and Response.
Posture isn’t protection
DSPM and CSPM tools are great at surfacing misconfigurations,but they don’t monitor behavior. They don’t know if a user is accessing sensitive data they’ve never touched before. They don’t detect lateral movement or privilege escalation. And they don’t alert you when an admin starts poking around in HR files the night before performance reviews.
The Codefinger ransomware campaign, which targeted AWS S3 buckets using stolen credentials, didn’t exploit an AWS vulnerability. Attackers used legitimate access to encrypt data with AES-256 keys, leaving no recovery path without ransom payment.
How Varonis handles DSPM
Varonis is different when it comes to DSPM — we focus on outcomes, not findings. Our #1 solution includes:
- Real-time monitoring of data access across the cloud and on-prem
- UEBA to detect anomalies like brute force, lateral movement, and insider threats
- Context-aware alerts that cut through the noise and prioritize real threats
This is the difference between knowing where your data is and knowing what’s happening to it. Varonis watches how identities interact with data and alerts you when something’s off.

Multi-cloud visibility without the headache
Each cloud platform has its own identity model, telemetry, and access control logic. AWS uses IAM roles and policies. Azure relies on AD groups and RBAC. Google Cloud has its own flavor of IAM. Stitching these together manually is a nightmare — and a major source of risk.
Multi-cloud security is difficult due to fragmented visibility and inconsistent policies across platforms lead to misconfigurations and compliance gaps. Without a solution to get centralized monitoring, threats can go undetected until it’s too late.
Navigate multi-clouds with Varonis
Only Varonis takes a holistic approach to cloud data security, securing your data, applications, and infrastructure with one unified platform. Features include:
- Building a unified access graph across platforms
- Enriching telemetry from AWS CloudTrail, Azure Monitor, and Google Cloud Audit Logs
- Automating remediation of risky access and misconfigurations
This isn’t just visibility. It’s clarity. And it’s the kind of clarity that lets you take action confidently — not guess what’s safe to fix.
Automation that works — and doesn’t break things
Security teams are stretched thin, making automation essential — but only if it’s smart.
Flipping a switch and hoping for the best isn’t a strategy. You need automation that understands context, respects business logic, and doesn’t interrupt workflows.
How Varonis uses automation
Varonis has least privilege automation for Microsoft 365, Google Drive, Box, and more solutions. It intelligently removes stale group memberships, risky sharing links, and excessive permissions — all without disrupting collaboration. Our automation capabilities also include:
- Using behavior analytics and access telemetry to drive intelligent automation
- Safely removing unused permissions and enforcing least privilege
- Quantifying data risk and tracking progress with real-time dashboards
This isn’t just cleanup — it’s continuous, intelligent enforcement of least privilege.
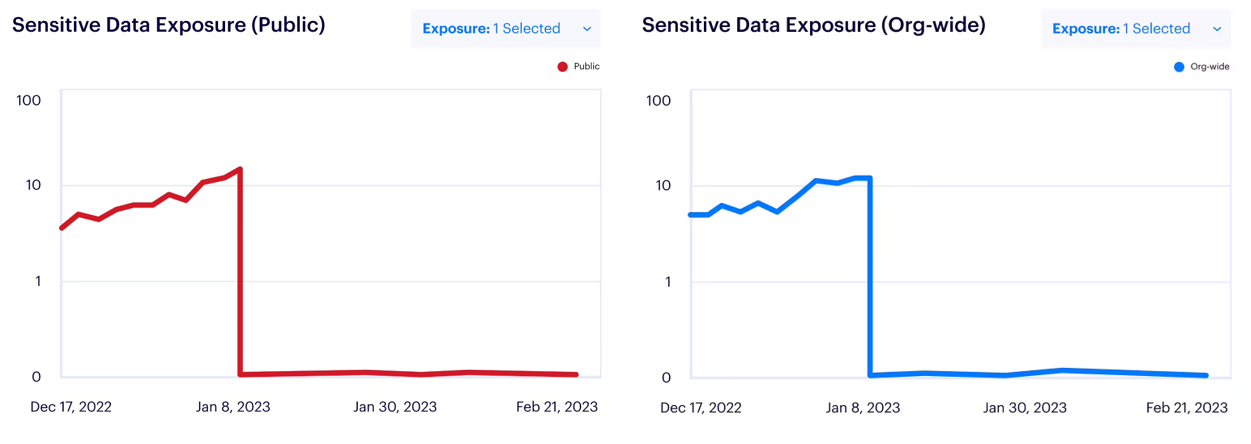
Forensics that answers the hard questions
When a breach happens, the first question isn’t, “How did they get in?” It’s “What did they touch?” Infrastructure can be rebuilt. Data can’t be unbreached.
In the LockBit ransomware attack, Varonis’ MDDR team uncovered 45 days of attacker persistence before encryption. They traced lateral movement, privilege escalation, and exfiltration paths — enabling rapid containment and recovery.
Why rapid response to threats matters
Whether it’s a ransomware event or an insider threat, Varonis helps you answer the questions that matter most — and prove it with evidence. With our MDDR service, you get:
- A dedicated forensics expert to ensure your data is secure 24x7x365
- Quick investigations with full forensic context
- Support with compliance and reporting for regulations like GDPR, HIPAA, and CCPA
- Help in responding to incidents with confidence — not guesswork
A platform that sees what others miss
Posture tools are necessary, but they’re not sufficient. To truly protect your data, you need a platform that connects identity, access, behavior, and sensitivity across your AWS, Azure, Google Cloud, and SaaS environments.
That’s what you get with Varonis. Our platform is not just posture. It’s protection, detection, and response — all in one.
“Trying to catch a threat by throwing more logs at it is like trying to find a needle in a haystack by throwing more hay at it.”
Brian Vecci, Varonis Field CTO
Get your free Cloud Data Risk Assessment
How do you stop a malicious insider or an attacker with valid AWS credentials from exfiltrating your most sensitive data? Take a deeper dive into AWS threats by watching our on-demand AWS Threat Playbook webinar.
Want to see where your blind spots are in the cloud?
Our complimentary Cloud Data Risk Assessment will map your sensitive data across cloud providers, identify excessive access and misconfigurations, and show you how to fix them automatically. The findings are also yours to keep after the assessment.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:






