Today, we’re excited to announce new remediation capabilities for AWS that can help organizations create a self-securing cloud environment. Varonis automates actions that have high-security value and zero business impact, such as blocking public access to sensitive S3 buckets, removing stale users and roles, and deleting inactive access keys.
In this blog, we’ll outline our new updates to Varonis for AWS. If you happen to be at AWS re:Inforce this week, stop by booth 303 for a live demo!
Active vs. passive DSPM
Many organizations turn to DSPM to give them more visibility into where their sensitive data exists and where it’s at risk. But where most DSPM vendors stop is with surfacing findings – most can’t fix the issues they uncover. This passive DSPM approach burdens IT and security teams with more work to configure third-party workflows or even to manually sift through findings to fix them.
Varonis takes an active approach to DSPM, building remediation into our Data Security Platform. Varonis’ industry-first automation for AWS can remediate exposure from multiple angles:
- Misconfigurations (e.g., enforce encryption at rest)
- Identity-related exposures (e.g., remove stale access keys)
- Public data exposure (e.g., apply public access block on all sensitive buckets)
Automatically block public access to S3 buckets.
AWS gives organizations the flexibility and power to create and proliferate cloud data workloads faster than ever. However, with complicated access policies and complex configurations, it can be difficult for security teams to keep up.
With Varonis’ automated remediation, security teams can automatically apply public access blocks on all S3 buckets containing sensitive data. You can do this remediation in bulk, on a schedule, or continuously so that you automatically stay ahead of new exposures.
A detailed activity audit trail can also help you detect when users make buckets public so you can address risk as soon as it happens.
Automatically apply public access blocks to S3 buckets.
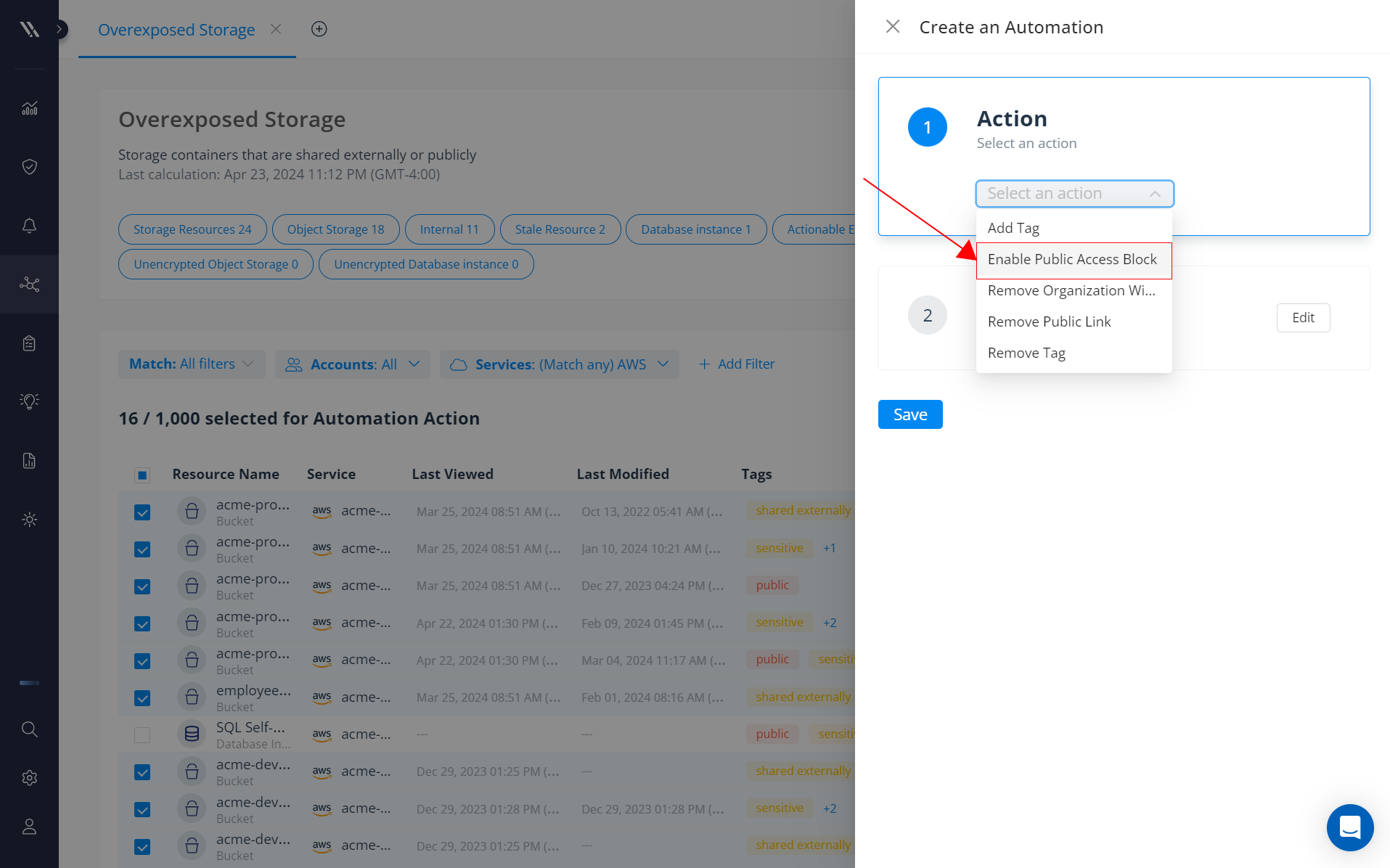
Automatically apply public access blocks to S3 buckets.
Remove stale users, roles, and access keys.
Once an attacker has an identity, they have access to data, so it’s important to eliminate stale or unneeded users, roles, and access keys to close off that attack path.
Varonis maintains a complete inventory of users, roles, and access keys in your AWS environment and identifies which are stale based on a customizable inactivity period. Varonis then surfaces the stale entities in the IaaS dashboard and creates reports for easy review.
From the dashboard, you can drill down and select the stale entities you want to remove from your environment. You can then use Varonis' remediation capabilities to promptly eliminate them from your AWS account. Set up reports to send to your cloud security architects on a regular basis to review and approve entities for removal by Varonis.
This granular control helps close offboarding gaps, identify identity-related threats, and quickly reduce your blast radius.
Get a centralized overview of your AWS environment's stale users, roles, and access keys.
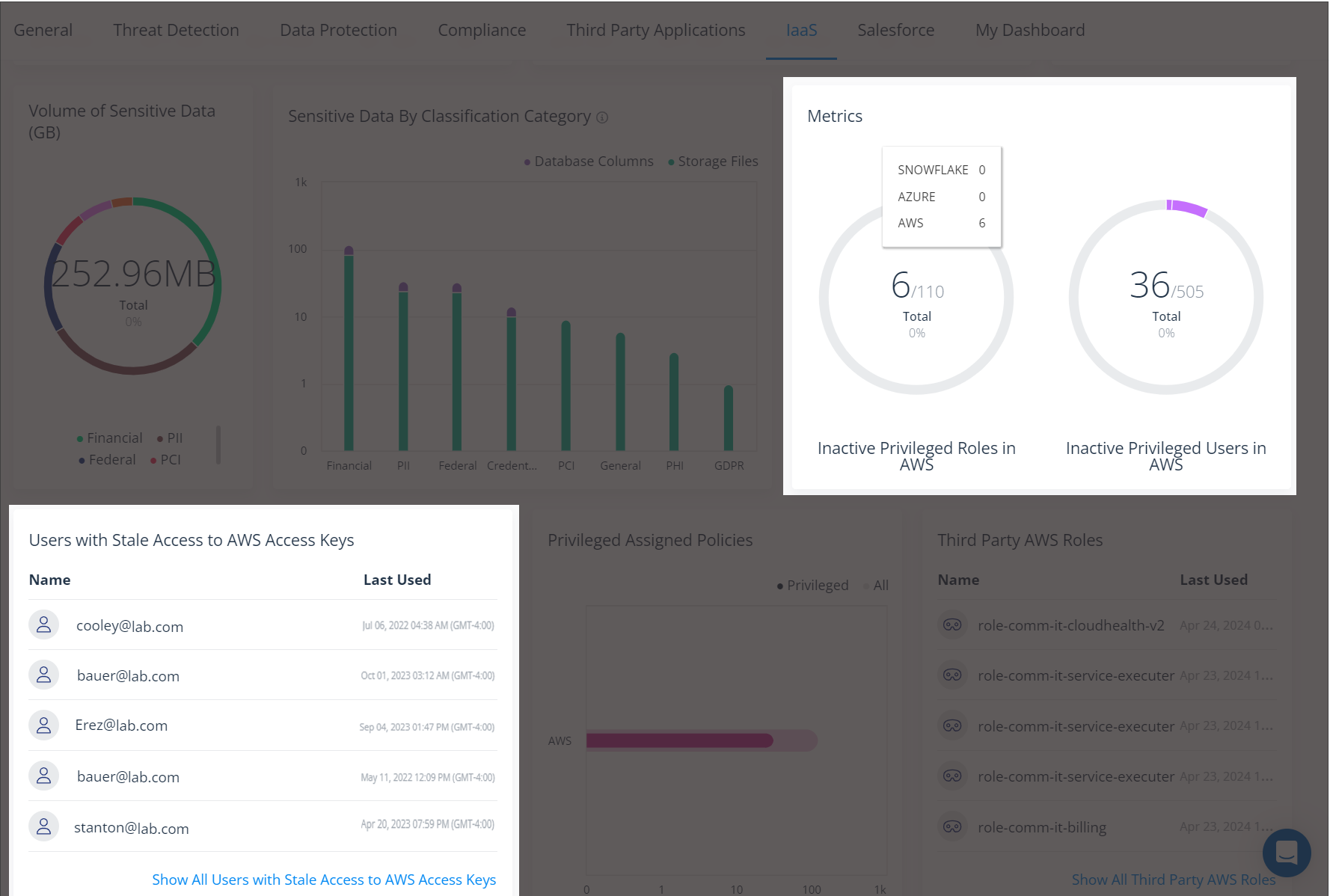
Get a centralized overview of your AWS environment's stale users, roles, and access keys.
Automatically remediate critical AWS misconfigurations.
While AWS offers flexibility, setting up a secure environment can be challenging, leading to significant security and compliance risks if not properly addressed. Even after initial setup, ongoing vigilance is critical as configuration drift can occur.
Varonis continuously monitors your AWS environment to proactively surface misconfigurations that may expose your sensitive data to risk and non-compliance. Rather than being left with a list of issues to fix yourself, Varonis enables you to automatically and continuously fix configuration issues as they arise.
Use Varonis to find and automatically remediate critical misconfigurations across AWS, such as:
- Missing password policies
- S3 object ownership enforcement
- Missing encryption at rest
With these remediation capabilities, you can proactively maintain a secure AWS environment and prevent configuration drift.
Automatically fix critical AWS misconfigurations
Automatically fix critical AWS misconfigurations
Discover shadow databases with Elastic Block Store support.
Spinning up an unmanaged database on EBS volumes attached to EC2 instances is relatively simple. However, these databases are often created without the security team’s knowledge. With no way to uncover shadow databases and understand what sensitive data resides in them, these databases go unseen, waiting to be breached.
Varonis now supports sensitive data discovery and monitoring for EBS. Now, you can:
- Discover shadow databases running on EC2 instances
- Surface orphaned snapshots
- Identify backups and dumps stored in S3 and link them to the relevant database
Customers now have a clear view of all their databases, including unmanaged shadow databases.
See an overview of the databases in your environment from a single console.
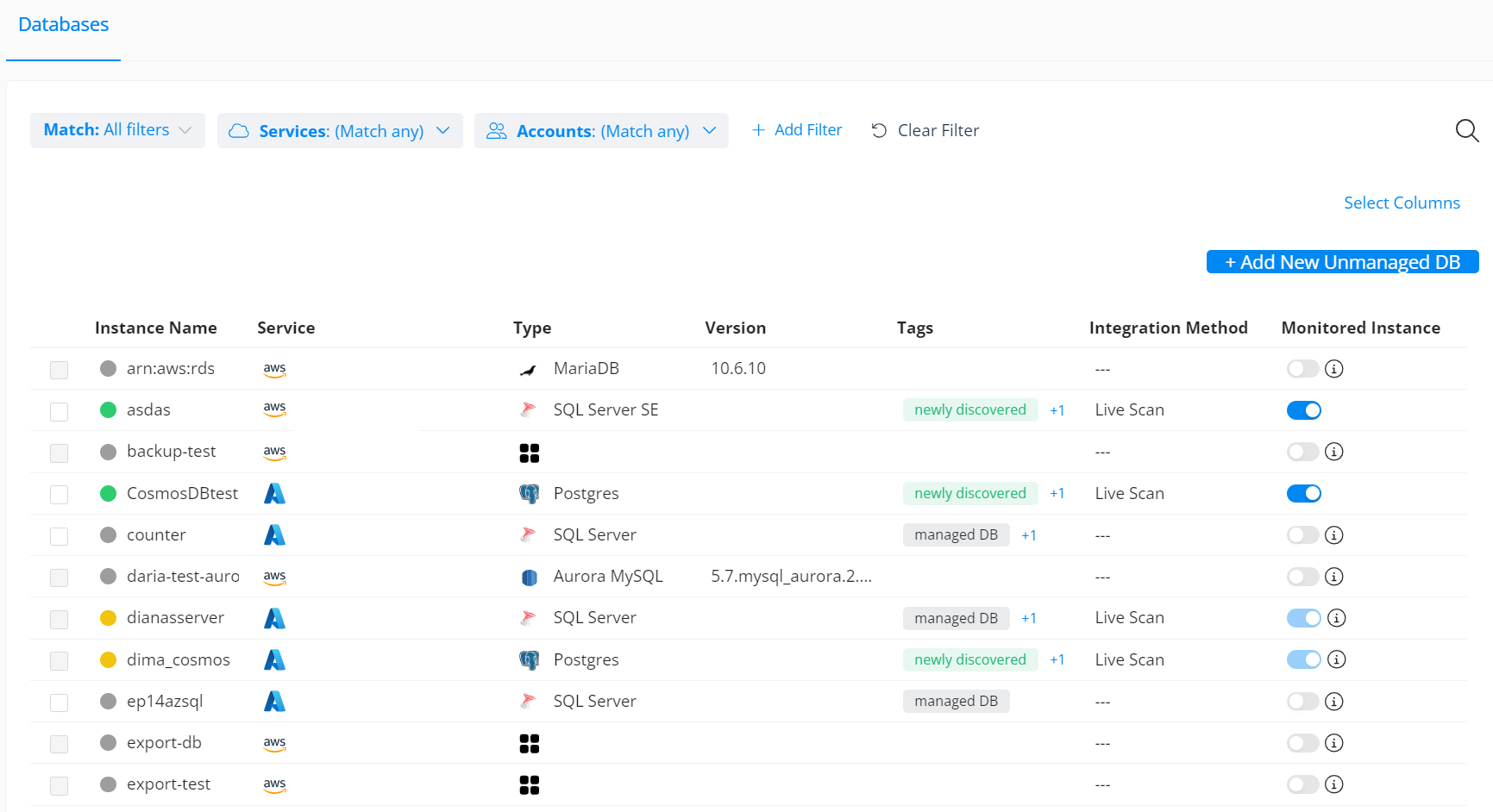
See an overview of the databases in your environment from a single console.
Maintain comprehensive coverage with Amazon Redshift support.
Many enterprises rely on Amazon Redshift to analyze critical business data, but it can be difficult to understand where sensitive data lives, where it's at risk, and how it’s being used within the data warehouse.
By expanding Varonis’ support for structured data to data found within AWS Redshift, organizations can be confident their critical data warehouses are secure. Varonis enables:
- Data discovery and classification
- Permissions and exposure analysis
- Misconfiguration management
- Activity monitoring and threat detection
With user and role permissions mapped across all Amazon Redshift warehouse instances, you can easily understand and reduce your AWS blast radius.
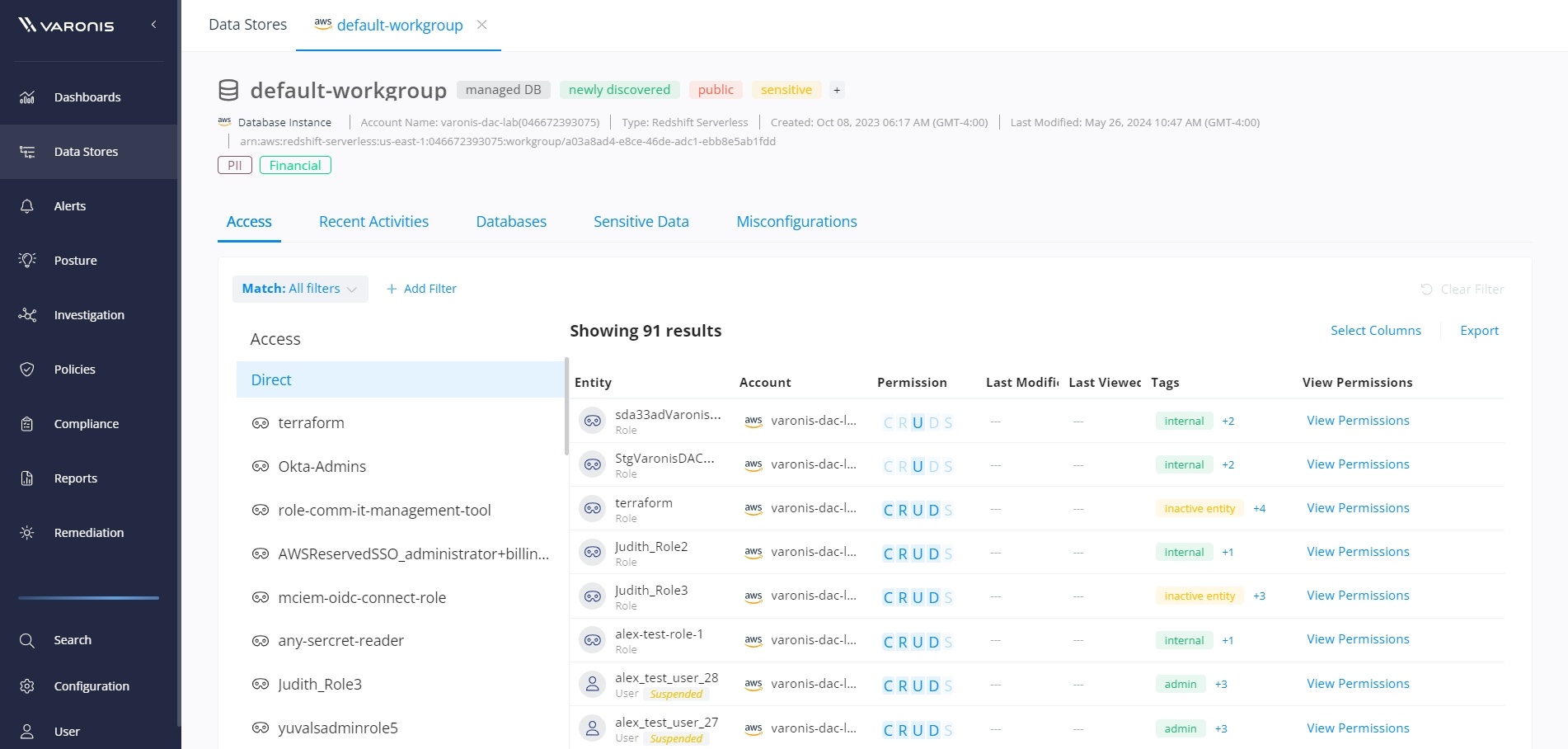
With user and role permissions mapped across all Amazon Redshift warehouse instances, you can easily understand and reduce your AWS blast radius.
Try Varonis for AWS for free.
Available on the AWS Marketplace, the Varonis Data Security Platform helps security teams continuously monitor and improve their data security posture in real time.
Request a demo today and visit us at AWS re:Inforce to see the solution in action.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









