Effortlessly fix cloud security risks with a click of a button
With how quickly SaaS and IaaS apps add new features and functionality, it can be difficult to make sure they’re always configured properly. That’s why more teams are automating their posture management. Review insights from across your cloud environment and fix security risks and non-compliant configurations with the click of a button.
Manual oversight can’t keep up with cloud environments
Large companies deploy an average of 187 different SaaS apps, which means security and compliance teams can spend months just trying to locate and understand their cloud security risk.
New SaaS features appear weekly, identity and access settings evolve constantly, and infrastructure services introduce new controls all the time. Without continuous monitoring, it’s easy for misconfigurations to accumulate unnoticed. Attackers love finding open storage buckets and overly broad access roles.
Automated posture management goes beyond SSPM and CSPM
Automated posture management is a security approach that identifies and automatically remediates misconfigurations and risks in cloud environments like SaaS and IaaS. While traditional solutions like SSPM and CSPM only report issues, automated posture management provides the ability to fix security gaps directly from a unified interface, often with a single click. This streamlines the process of securing cloud applications and infrastructure.
Proactive design, comprehensive protection
A comprehensive posture management approach typically includes several key components:
- Understanding how cloud services, identities, permissions, and data are configured across the entire environment.
- Threat detection. Spotting configuration weaknesses or behavior patterns that could indicate emerging risks.
- Risk assessment. Evaluating how misconfigurations could be exploited and prioritizing issues by severity and impact.
- Taking action to correct insecure configurations — ideally through automated or guided workflows.
Unlike reactive security approaches that respond after an incident has occurred, automatic posture management is proactive by design. It helps teams identify issues before they can be exploited and reduces reliance on manual audits that may only happen quarterly or annually.
The Varonis approach: Insights Dashboard
Varonis’ Insights Dashboard continuously scans your SaaS and IaaS apps and identifies security gaps and misconfigurations. We alert you when issues arise and provide a clear and concise explanation of how these gaps put your organization at risk.
With the addition of our automated posture management capabilities, customers can now solve issues without ever leaving the Varonis UI. We’ll commit the change on your behalf.
No more complicated workflows or arduous step-by-step fixes
Simply review your Varonis Insights Dashboard, sort by severity or service, and begin automatically fixing critical misconfigurations with a single click.
You can also drill down from the insights widget on the dashboard, filter or search for the issues you’d like to remediate, and click fix. We’ll take care of the rest.
Quickly identify and fix configuration risks.
You can even bundle and fix multiple misconfigurations at a time if they are found across more than one instance of your environment.
Bundle Varonis Insights together to fix all security gaps at once.
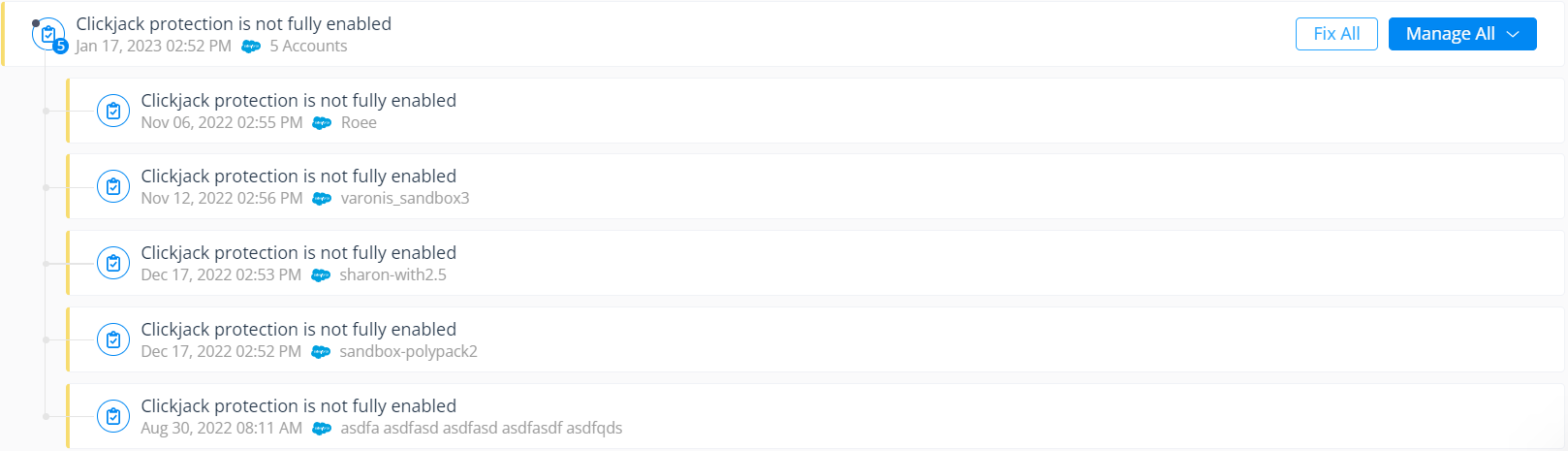
Bundle Varonis Insights together to fix all security gaps at once.
Once you remedy an issue, you’ll see it reflected in your dashboard under the Fixed Insights widget. Click on the widget to get a detailed report of everything Varonis has taken care of and when the fix occurred.
Over time, customers will have the option to auto-fix a wider variety of misconfigurations. Some issues, however, can’t be auto-fixed yet because the app vendor doesn’t provide API to make the required change.
Expert-created, continuously updated insights
Our team of experts continuously update Varonis’ insights library with the latest configuration risks and best practices as SaaS and IaaS platforms evolve and add new configuration options. We employ world-class domain experts in Salesforce, AWS, Google, Okta, and more, so you don’t have to. We develop, test, and automatically push new insight definitions to all customers.
What’s more, our elite cybersecurity research team, Varonis Threat Labs (VTL), constantly discovers new attack vectors and ways threat actors abuse misconfigurations in the world’s most critical SaaS apps. Our learnings from VTL create new and unique cloud security insights that keep you safe.

Automated data security with Varonis
Varonis’ mission is to deliver effortless outcomes to customers. That’s why we’re building automation into every part of our platform. In addition to finding and fixing org-wide configuration issues, Varonis enables you to automatically:
- Discover and classify sensitive data. We automatically discover and classify sensitive data and secrets no matter where they live, showing you who has access and where your critical data is overexposed.
- Remove excessive access to sensitive data. With least privilege automation, we remove sharing links and direct permissions that expose your data org-wide, externally, and publicly in Box, Google Drive, and Microsoft 365. All without you having to lift a finger.
- Detect sophisticated threats. Varonis continuously monitors data activity to detect suspicious or risky behavior and stop incidents before they become breaches.
Interested in improving your security posture in 15 minutes?
Configuration gaps open your organization up to risks you can’t afford to take.
Varonis’ expert-led risk assessments are 100% complimentary and take just minutes to set up. Instantly assess your security posture and start closing your cloud security gaps.
Request a free Data Disk Assessment today.
FAQs about automated posture management
What is automated posture management?
Automated posture management is a security approach that identifies and automatically remediates misconfigurations and risks in cloud environments like SaaS and IaaS. Unlike solutions that only report issues, it provides the ability to fix security gaps directly from a unified interface, often with a single click. This streamlines the process of securing cloud applications and infrastructure.
How does automated posture management differ from traditional CSPM?
Traditional Cloud Security Posture Management (CSPM) solutions are primarily designed to detect and report on configuration drifts and security risks, providing recommendations for manual fixes. Automated posture management evolves this capability by integrating remediation directly into the platform. This eliminates the need for security teams to follow complex, step-by-step instructions in different systems, enabling them to resolve identified issues much more efficiently.
Why is automation essential for managing security posture today?
With organizations using an average of 187 different SaaS applications, manually tracking and correcting configurations is nearly impossible. Cloud environments are dynamic, with new features and settings being added constantly, increasing the chance of human error and misconfiguration. Automation allows security teams to manage this complexity at scale, ensuring that risks are identified and remediated quickly before they can be exploited.
What types of security risks can automated posture management fix?
Automated posture management is designed to address a wide range of preventable security risks stemming from misconfigurations in cloud services. This includes correcting non-compliant settings, closing security gaps in SaaS applications, and fixing errors that could expose sensitive data. By continuously scanning for these issues, it helps organizations maintain a strong and consistent security posture across their entire cloud ecosystem.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









