Advanced Persistent Threats (APTs) are long-term operations designed to infiltrate and/or exfiltrate as much valuable data as possible without being discovered. It’s not yet possible to estimate exactly how much data actors were able to access with Slingshot, but Kaspersky’s data says that Slingshot affected approximately 100 individuals across Africa and the Middle East, with most of the targets in Yemen and Kenya. As we saw with the Stuxnet APT, Slingshot appears to have originated from a nation-state. As an APT, it doesn’t get much better than 6 years undetected.
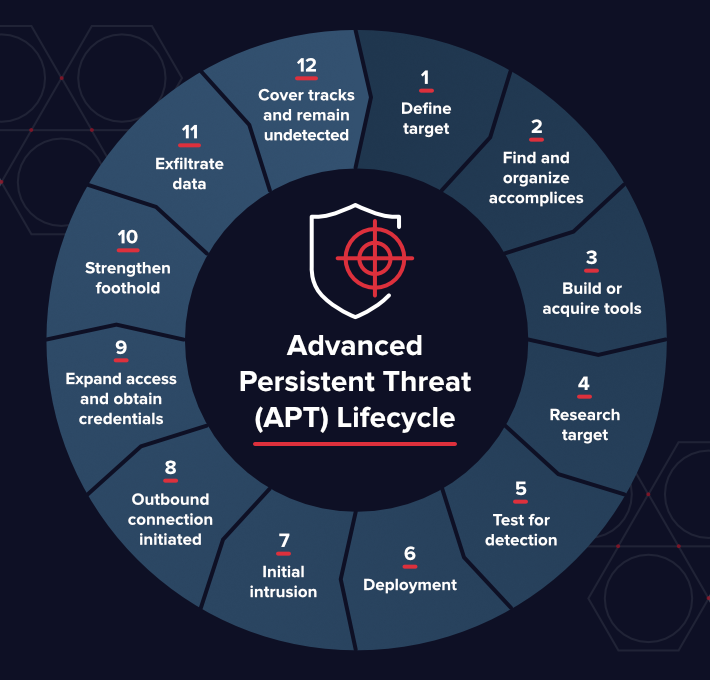
Advanced Persistent Threat (APT) Lifecycle
Get the Free Pen Testing Active Directory Environments EBook
The lifecycle of an APT is much longer and more complex than other kinds of attacks.
Stuxnet, for example, led a strategic attack on a high-value target: the programmers wrote code to attack a specific control board by a specific manufacturer that Iran used to enrich uranium. And they wrote it in such a way that it would be hard to find, so it had as much time to do as much damage as possible. The lifecycle of an APT is much longer and more complicated than other kinds of attacks.
- Define target: Determine who you’re targeting, what you hope to accomplish – and why.
- Find and organize accomplices: Select team members, identify required skills, and pursue insider access.
- Build or acquire tools: Find currently available tools, or create new applications to get the right tools for the job.
- Research target: Discover who has access you need, what hardware and software the target uses, and how to best engineer the attack.
- Test for detection: Deploy a small reconnaissance version of your software, test communications and alarms, identify any weak spots.
- Deployment: The dance begins. Deploy the full suite and begin infiltration.
- Initial intrusion: Once you’re inside the network, figure out where to go and find your target.
- Outbound connection initiated: Target acquired, requesting evac. Create a tunnel to begin sending data from the target.
- Expand access and obtain credentials: Create a “ghost network” under your control inside the target network, leveraging your access to gain more movement.
- Strengthen foothold: Exploit other vulnerabilities to establish more zombies or extend your access to other valuable locations.
- Exfiltrate data: Once you find what you were looking for, get it back to base.
- Cover tracks and remain undetected: The entire operation hinges upon your ability to stay hidden on the network. Keep rolling high on your stealth checks and make sure to clean up after yourself.
Toolbox: Advanced Persistent Threat
APT operations, with many steps and people involved, require a massive amount of coordination. There are a few tried and true tactics that reappear across different APT operations:
- Social engineering: The oldest and most successful of all infiltration methods is plain old social engineering. It’s much easier to convince somebody to provide you the access you need than it is to steal or engineer it on your own. The majority of APT attacks have a social engineering component, either at the beginning during the target research phase or towards the end to cover your tracks.
- Spear phishing: Spear phishing is a targeted attempt to steal credentials from a specific individual. The individual is typically scouted during target research and identified as a possible asset for infiltration. Like shotgun phishing attack, Spear phishing attempts use malware, keylogger, or email to get the individual to give away the credentials.
- Rootkits: Because Rootkits live close to the root of the computer systems they are difficult to detect. Rootkits do a good job of hiding themselves and granting access to the infected system. Once installed, the operators can access the target company through the rootkit. They can continue to infiltrate other systems once they are on the network, making it much more difficult for security teams to contain the threat.
- Exploits: An easy target for APTs is zero-day bugs or other known security exploits. An unpatched security flaw allowed the APT operation at Equifax to go on for several months undetected.
- Other tools: While the above is the most common, there are a seemingly endless amount of potential tools: Infected downloads, DNS tunneling, rogue WI-FI, and more. And who knows what the next generation of hackers will develop, or what is already out there undiscovered?
Who is Behind Advanced Persistent Threats (APT)?
Operators who lead APT attacks tend to be motivated and committed. They have a goal in mind and are organized, capable, and intent on carrying out that goal. Some of these operations live under a larger organization, like a nation-state or corporation.
These groups are engaged in espionage with the sole purpose of gathering intelligence or undermining their targets capabilities.
Some examples of well-known APT groups include:
- APT28 (or Fancy Bear)
- Deep Panda
- Equation
- OilRig
Corporations will engage in industrial espionage with APTs, and Hacktivists will use APTs to steal incriminating information about their targets. Some lower level APTs are designed just to steal money.
These are by far the most prevalent, but their actors are not as sophisticated or capable as the actors sponsored by nation-states.
Typical motives for APTs are espionage, gaining a financial or competitive advantage over a rival, or simple theft and exploitation.
What are Common Targets for Advanced Persistent Threats (APT)?
In general, APTs target higher-value targets like other nation-states or rival corporations. However, any individual can ultimately be a target of an APT.
Two telling characteristics of an APT attack are an extended period, and consistent attempts at concealment.
Any (and all) sensitive data is a target for an APT, as is cash or or cash equivalents like bank account data or bitcoin wallet keys. Potential targets include:
- Intellectual property (e.g., inventions, trade secrets, patents, designs, processes)
- Classified data
- Personally identifiable information (PII)
- Infrastructure data (i.e., reconnaissance data)
- Access credentials
- Sensitive or incriminating communications (i.e., Sony)
How to Manage Advanced Persistent Threats (APT)?
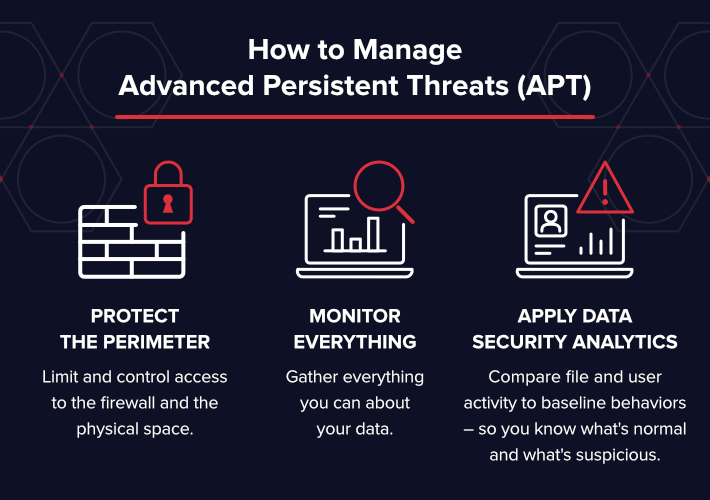
Protecting yourself from APTs requires a layered security approach:
- Monitor everything: Gather everything you can about your data. Where does your data live? Who has access to that data? Who makes changes to the firewall? Who makes changes to credentials? Who is accessing sensitive data? Who is accessing our network and where are they coming from? You should know everything that happens within your network and to your data. The files themselves are the targets. If you know what is happening to your files, you can react to and prevent APTs from damaging your organization.
- Apply data security analytics: Compare file and user activity to baseline behaviors – so you know what’s normal and what’s suspicious. Track and analyze potential security vulnerabilities and suspicious activity so that you can stop a threat before it’s too late. Create an action plan to manage threats as you get the alerts. Different threats will require a different response plan: your teams need to know how to proceed and investigate each threat and security incident.
- Protect the perimeter: Limit and control access to the firewall and the physical space. Any access points are potential points of entry in an APT attack. Unpatched servers, open WIFI routers, unlocked server room doors, and insecure firewall allow the opportunity for infiltration. While you can’t ignore the perimeter, if we had to do data security all over again we would monitor the data first.
APT attacks can be difficult (or impossible) to detect without monitoring. The attackers are actively working against you to remain undetected but still able to operate. Once they’re inside the perimeter, they may look like any other remote user – making it difficult to detect when they’re stealing data or damaging your systems.
The Varonis Data Security Platform provides the monitoring and analytics capabilities you need to detect and thwart APTs against your organization – even once they’re inside.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









