SIEM is an industry poised to hit $11.3 billion by 2026, but only a small number of companies are getting value from their SIEM.
SIEM tools are an important part of the data security ecosystem: they aggregate data from multiple systems and analyze that data to catch abnormal behavior or potential cyberattacks. SIEM tools provide a central place to collect events and alerts – but can be expensive, resource intensive, and customers report that it is often difficult to resolve problems with SIEM data.
What is SIEM?
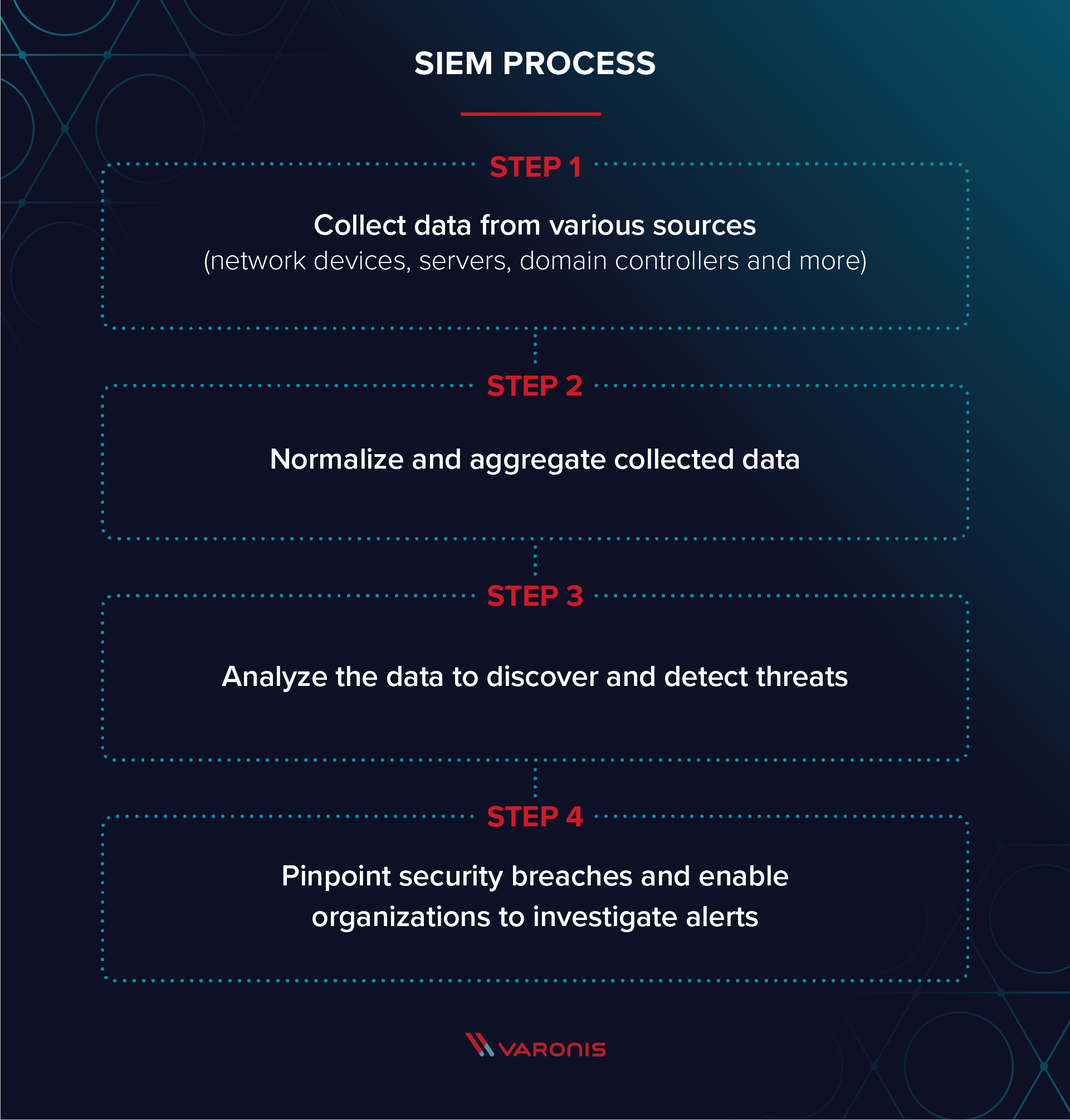
Security Information and Event Management (SIEM) is a software solution that aggregates and analyzes activity from many different resources across your entire IT infrastructure.
SIEM collects security data from network devices, servers, domain controllers, and more. SIEM stores, normalizes, aggregates, and applies analytics to that data to discover trends, detect threats, and enable organizations to investigate any alerts.
How Does SIEM Work?
SIEM provides two primary capabilities to an Incident Response team:
- Reporting and forensics about security incidents
- Alerts based on analytics that match a certain rule set, indicating a security issue
At its core, SIEM is a data aggregator, search, and reporting system. SIEM gathers immense amounts of data from your entire networked environment, consolidates and makes that data human accessible. With the data categorized and laid out at your fingertips, you can research data security breaches with as much detail as needed.
Security Information and Event Management Capabilities
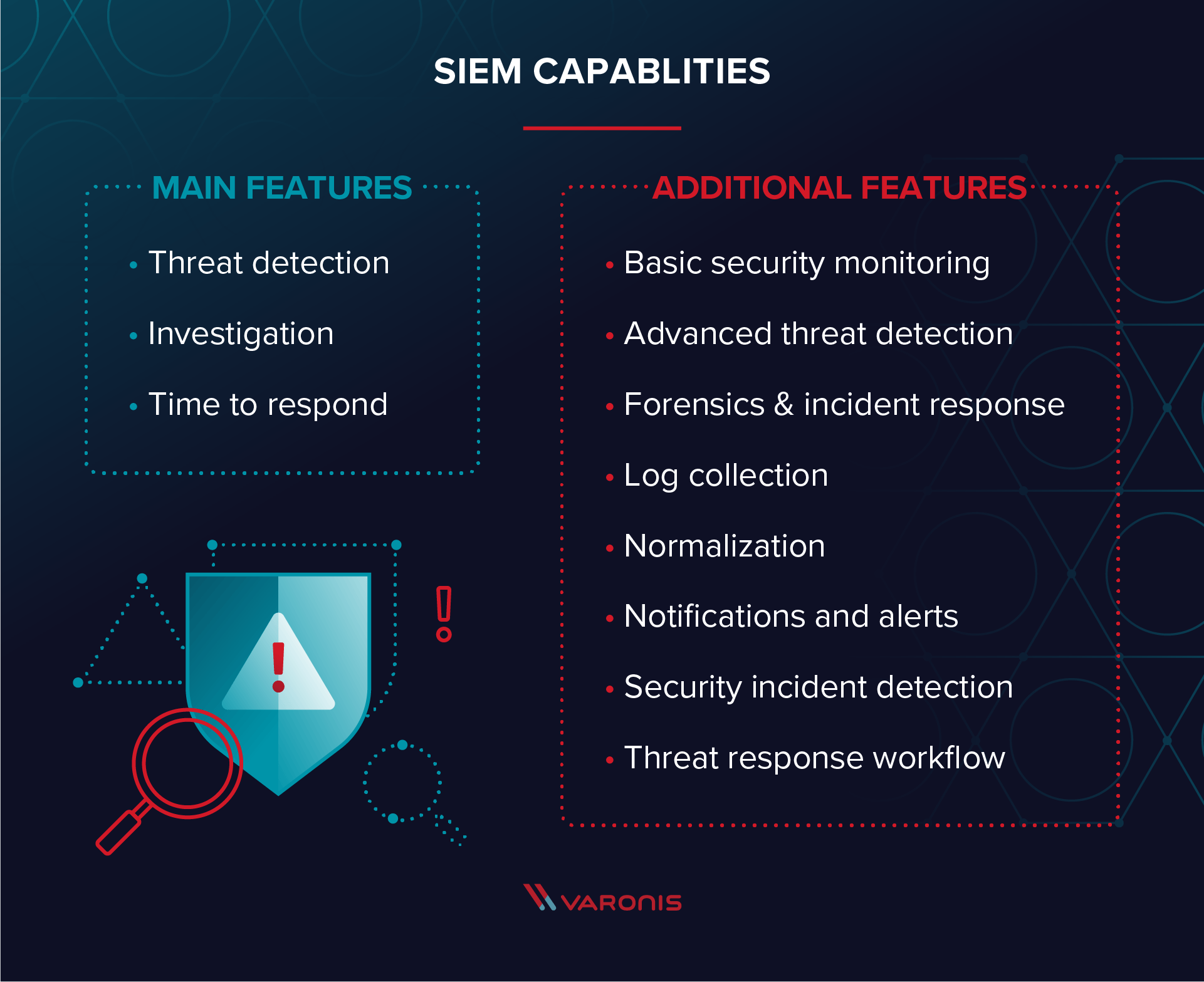
Gartner identifies three critical capabilities for SIEM (threat detection, investigation and time to respond) — there are other features and functionality that you commonly see in the SIEM market, including:
- Basic security monitoring
- Advanced threat detection
- Forensics & incident response
- Log collection
- Normalization
- Notifications and alerts
- Security incident detection
- Threat response workflow
Top SIEM Tools
These are some of the top players in the SIEM space:
Splunk
Splunk is a full on-prem SIEM solution that Gartner rates as a leader in the space. Splunk supports security monitoring and can provide advanced threat detection capabilities.
Varonis integrates with Splunk through the Varonis DatAlert App for Splunk.
IBM QRadar
QRadar is another popular SIEM that you can deploy as a hardware appliance, a virtual appliance, or a software appliance, depending on your organization’s needs and capacity.
QRadar can integrate with Varonis to add Advanced Threat Detection capabilities. Look for the Varonis App for QRadar.
LogRhythm
LogRhythm is a good SIEM for smaller organizations. You can integrate LogRhythm with Varonis to get threat detection and response capabilities.
SIEM in the enterprise
Some customers have found that they need to maintain two separate SIEM solutions to get the most value for each purpose since the SIEM can be incredibly noisy and resource intensive: they usually prefer one for data security and one for compliance.
Beyond SIEM’s primary use case of logging and log management, enterprises use their SIEM for other purposes. One alternate use case is to help demonstrate compliance for regulations like HIPAA, PCI, SOX, and GDPR.
SIEM tools also aggregate data you can use for capacity management projects. You can track bandwidth and data growth over time to plan for growth and budgeting purposes. In the capacity-planning world, data is key, and understanding your current usage and trends over time allows you to manage growth and avoid large capital expenditures as a reactionary measure versus prevention.
Limitations of SIEM applications as a full data security ecosystem
SIEM applications provide limited contextual information about their native events, and SIEMs are known for their blind spot on unstructured data and emails. For example, you might see a rise in network activity from an IP address, but not the user that created that traffic or which files were accessed.
In this case, context can be everything.
What looks like a significant transfer of data could be completely benign and warranted behavior, or it could be a theft of petabytes of sensitive and critical data. A lack of context in security alerts leads to a ‘boy that cried wolf’ paradigm: eventually, your security will be desensitized to the alarm bells going off every time an event is triggered.
SIEM applications are unable to classify data as sensitive or non-sensitive and therefore are unable to distinguish between sanctioned file activity from suspicious activity that can be damaging to customer data, intellectual property, or company security.
Ultimately, SIEM applications are only as capable as the data they receive. Without additional context on that data, IT is often left chasing down false alarms or otherwise insignificant issues. Context is key in the data security world to know which battles to fight.
The biggest issue we hear from customers when they use SIEM is that it’s extremely difficult to diagnose and research security events. The volume of low-level data and the high number of alerts cause a ‘needle in a haystack’ effect: users get an alert but often lack the clarity and context to act on that alert immediately.
How Varonis complements SIEM
The context that Varonis brings to SIEM can be the difference between a snipe hunt or preventing a major data security breach.
And that’s where Varonis comes in. Varonis provides additional context to the data that a SIEM collects: making it easier to get more value out of a SIEM by building in-depth context, insight, and adding threat intelligence into security investigations and defenses.
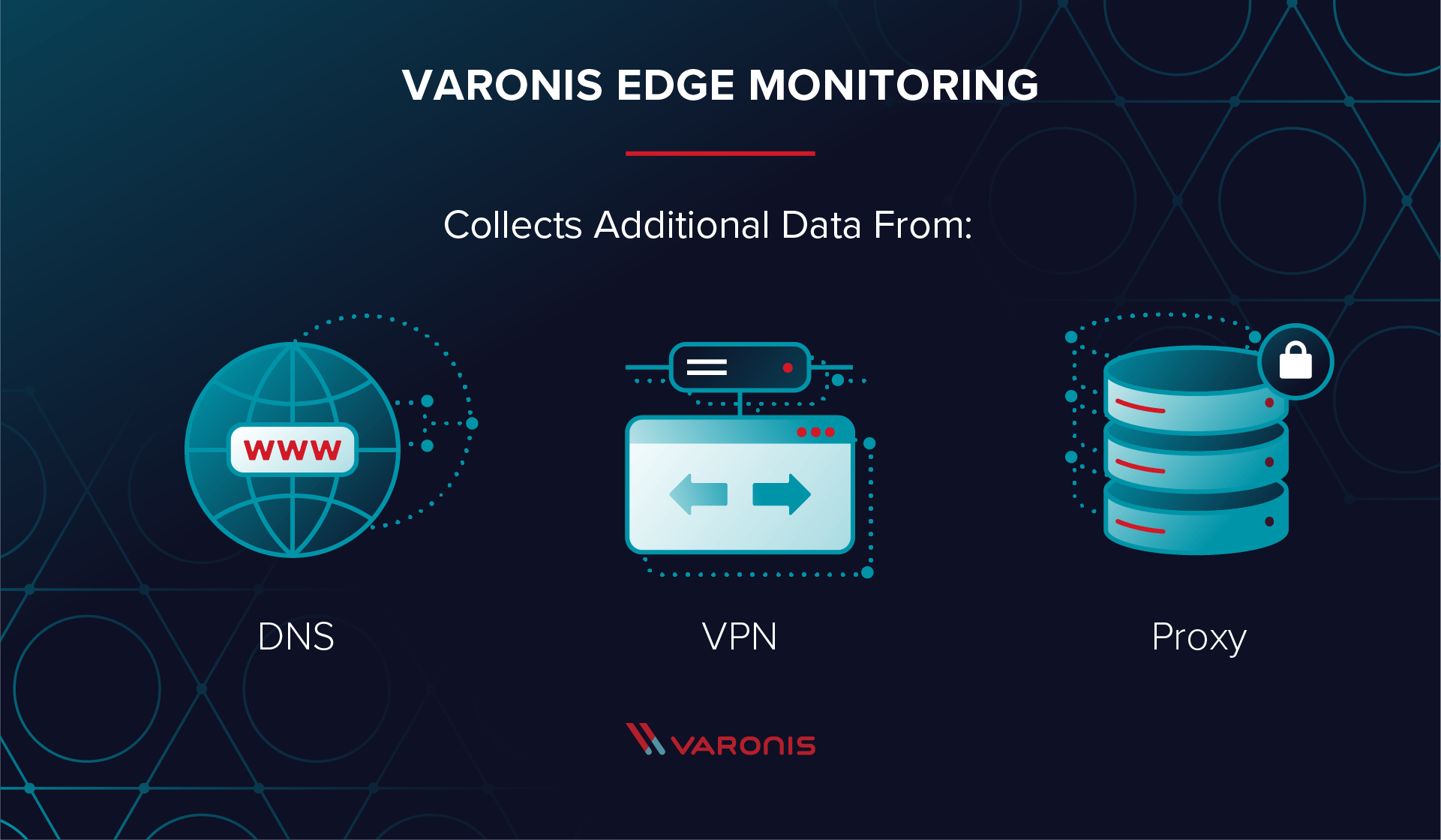
Varonis captures file event data from various data stores – on-premises and in the cloud – to give the who, what, when, and where of each file accessed on the network. With Varonis Edge monitoring, Varonis will also collect DNS, VPN, and web proxy activity. You’ll be able to correlate the network activity with the data store activity to paint a complete picture of an attack from infiltration through file access to exfiltration.
Varonis classifies unstructured files based on hundreds of possible pattern matches, including PII, government ID numbers, credit card numbers, addresses, and more. That classification can be extended to search for company-specific intellectual property, discover vulnerable, sensitive information, and help meet compliance for regulated data. Varonis reads files in place without any impact to end users.
Varonis also performs user behavior analytics (UBA) to provide meaningful alerts based upon learned behavior patterns of users, along with advanced data analysis against threat models that inspect patterns for insider threats (such as exfiltration, lateral movement, account elevation) and outsider threats (like ransomware).
Integration highlights
Varonis integrates with SIEM applications to give security analytics with deep data context so that organizations can be confident in their data security strategy. Benefits include:
- Out of the box analytics
- Integrated Varonis dashboards and alerts for streamlined investigation
- Alert specific investigation pages
- Critical information highlighted at a glance, with actionable insights and rich context
- Integration into your SIEM workflow
How to investigate an attack with SIEM and Varonis
This contextual data that Varonis brings gives security teams meaningful analysis and alerts about the infrastructure, without the additional overhead or signal noise to the SIEM. SOC teams can investigate more quickly by leveraging SIEM with Varonis and get insight into the most critical assets they need to protect: unstructured data and email. With the added visibility provided by Varonis, you get an at-a-glance overview of what’s happening on your core data stores – both on-premises and in the cloud. You can easily investigate users, threats, and devices – and even automate responses.
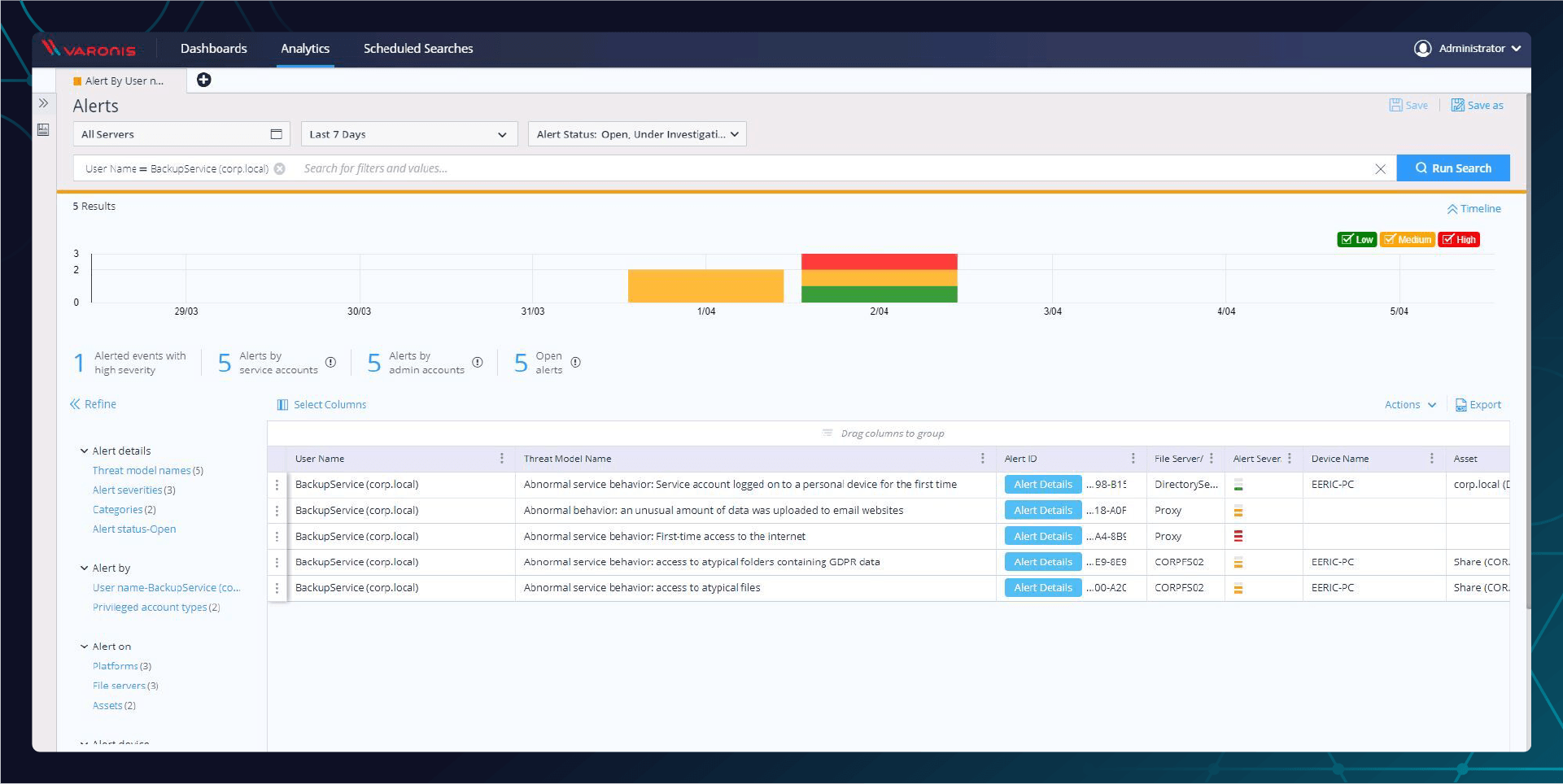
When you click on the Varonis Alert Event in your SIEM, you are taken to the Varonis Alert Dashboard for the alert you are investigating. From here, you can see that this alert is related to four other alerts. Any one of them is troublesome, but since they are all connected, it’s a much clearer and well laid out picture of a cyberattack.
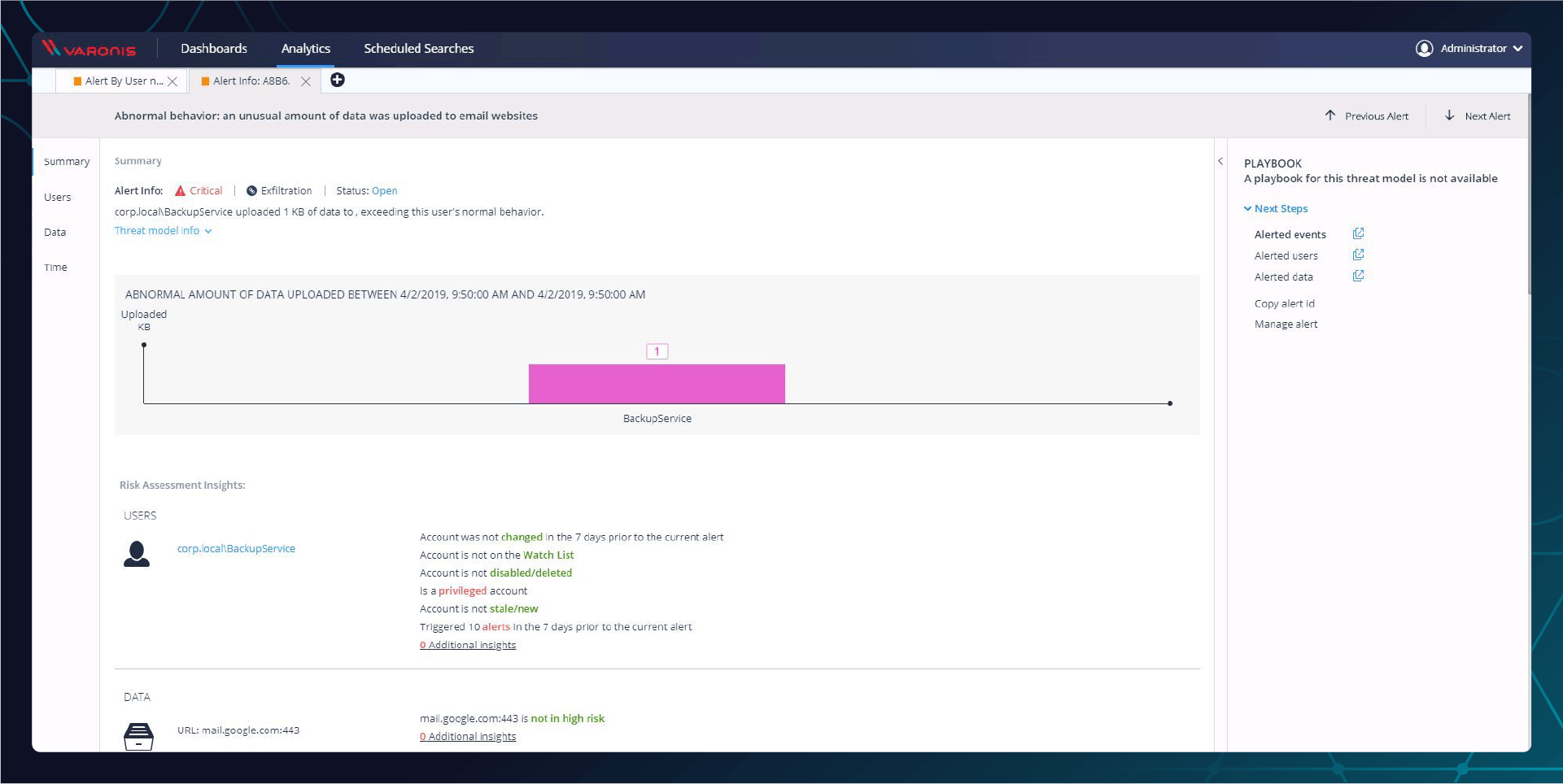
This alert tells us that this BackupService account uploaded data to an external email website.
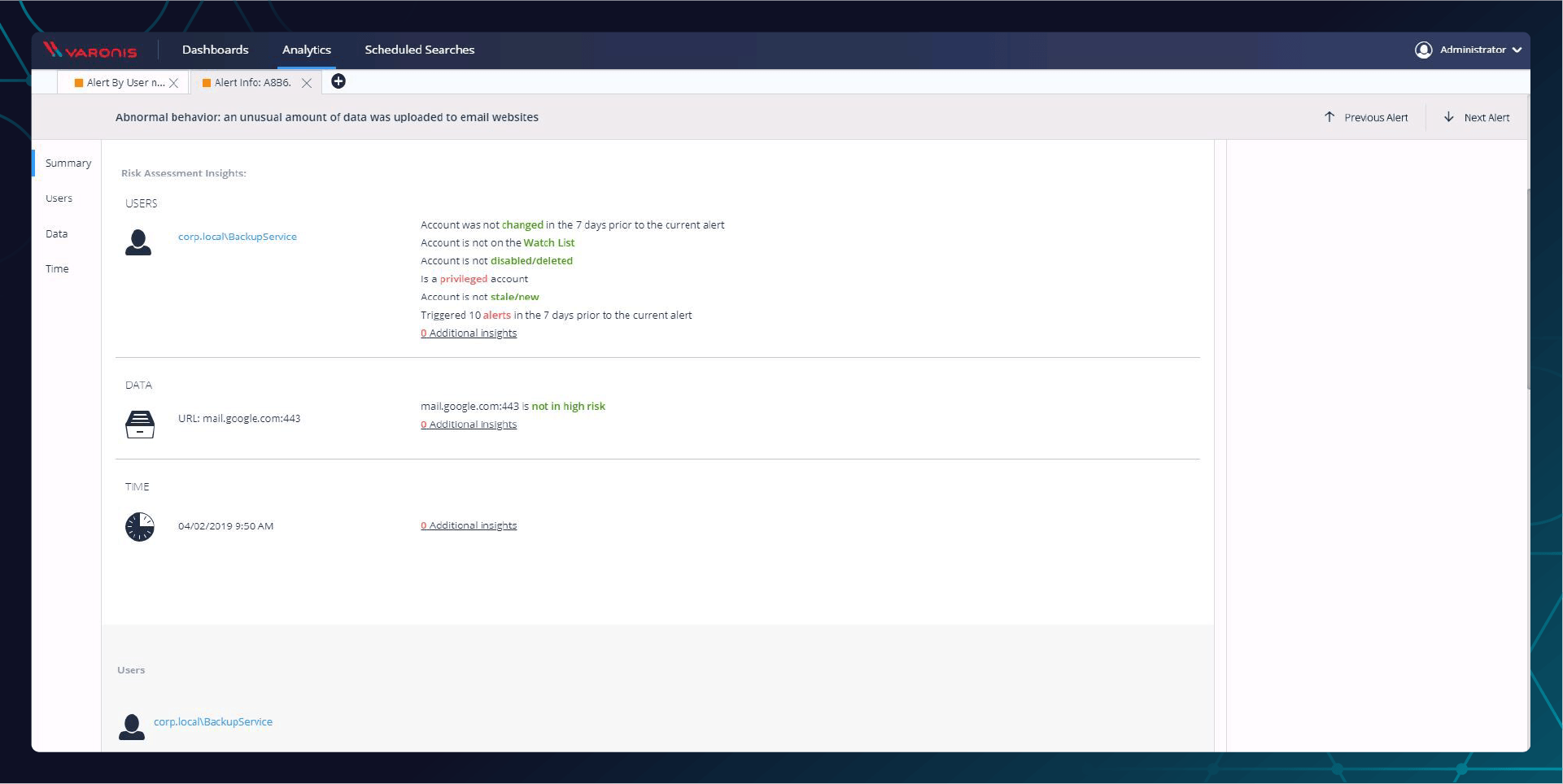
This alert tells us that the BackupService account has never accessed the internet before, making the fact that the account uploaded data to email much more suspicious.
That’s just the beginning of investigating cybersecurity alerts with Varonis and your SIEM. Varonis can kick off a script to disable the user account and shut down the attack as soon as it’s detected – in which case, that hacker might not have been able to get to the payroll files at all!
With the context you have at your disposal, you can quickly respond to – and manage – the alerts that you receive in your SIEM.
Security analysts spend countless hours to get meaningful alerts from SIEM: fine-tuning use cases, building rules, and adding in data sources – Varonis gives a head start with out-of-the-box analytics models, intuitive dashboards, and intelligent alerting.
OK, I’m ready to get started!
If you’re already using a SIEM, it’s simple to add Varonis and get more out of your SIEM investment. If you’re looking to start your data security plan, start with Varonis, and then add your SIEM.
Once you have Varonis in place, you can then add your SIEM for data aggregation and additional monitoring and alerting. Varonis gives you more initial data security coverage, and adding a SIEM will make Varonis and your SIEM better able to correlate and store data for analysis and auditing.
Check out a Live Cyberattack Webinar to see how Varonis brings context to your SIEM data.
FAQs about SIEM
What is SIEM?
SIEM stands for Security Information and Event Management. It's a comprehensive cybersecurity solution that acts as the central nervous system for your organization's security operations.
How does SIEM work?
SIEM platforms collect security data from across your entire IT environment, including:
- Network devices (firewalls, routers, switches)
- Servers and workstations
- Domain controllers
- Applications and databases
- Cloud services
- Security tools (antivirus, intrusion detection systems)
What are the common limitations or challenges of SIEM?
While powerful, SIEM applications often face challenges like limited context, especially for unstructured data and emails. They can struggle to classify data sensitivity, leading to a high volume of alerts that may lack actionable insights. This can create a "needle in a haystack" problem, making it difficult for security teams to efficiently diagnose and research security events amidst noise.
How has SIEM technology evolved over time?
Initially focused on log management and compliance reporting, SIEM solutions have significantly advanced. They now incorporate real-time monitoring, advanced analytics, and machine learning capabilities. Modern SIEM platforms also integrate with security orchestration, automation, and response (SOAR) systems and extended detection and response (XDR) to streamline incident management and enhance detection.
How does SIEM relate to other cybersecurity technologies like SOAR or XDR?
SIEM aggregates and analyzes security data to provide visibility and alert on potential threats. SOAR (Security Orchestration, Automation, and Response) systems automate responses to these threats, working in tandem with SIEM to accelerate incident resolution. XDR (Extended Detection and Response) offers a broader view by collecting telemetry across endpoints, networks, and cloud environments, complementing SIEM by providing deep context for specific areas.
How does SIEM leverage artificial intelligence and machine learning?
Modern SIEM solutions use AI and machine learning to enhance their analytical capabilities and improve threat detection. These technologies help identify anomalous behaviors and indicators of advanced threats by learning normal patterns and highlighting deviations. This advanced analysis reduces false positives, allows for more complex threat identification, and supports predictive security insights.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)

