I’ve been on a mission the last few months to bring basic knowledge about data security to the upper reaches of the organization. Our C-level readers and other executives, who haven’t already, should review this video explaining how easy it is for hackers to do their work. And this post showing how hackers can leverage legitimate Windows software for non-legitimate activities.
There’s another part of the security-verse that doesn’t get nearly the attention it deserves. It goes under the name of Open Source Intelligence, or OSINT, which can be described as passive reconnaissance or background information gathering from public sources.
Get the Free Pentesting Active
Directory Environments e-book
With a new generation of OSINT-ware, attackers can quickly learn amazing details about your organization and employees even before formally launching an attack. And in fact, the OSINT itself can help steer the attacker’s planning.
Let me re-emphasize: with OSINT, the attacker’s foreknowledge about an organization is based on publicly available information.
Of course, anyone can find factoids on the web by doing clever ad-hoc searches. But as with everything in infosec, new powerful apps have changed the way we go about our jobs. OSINT can now boast several freeware (or freemium) tools that can be used for good, by security defenders, pen testers, and analysts, but also for evil by APT groups and national security agencies.
The objective in this post is to present to high-level executives a few of the more popular of these OSINT tools. And show that even an inexperienced hacker (or infosec blogger) can with little effort learn about the perimeter network, gain knowledge of security holes, and discover enough about your employees to hack into their work accounts!
SpiderFoot and Public Data
SpiderFoot is a good introduction to the capabilities of OSINT software. It’s described as a “reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gathers intelligence on IP addresses, domain names, e-mail addresses.”
Fair enough. It requires the user — pen tester or attacker — to specify an explicit IP address of a potential target to then launch a scan. In addition to gathering domain info — including registration contact data — and IP addresses from the corporate perimeter, SpiderFoot captures other data (and metadata) by crawling the site. By the way, here’s a good read about SpiderFoot’s developer, Steve Micallef, and more background on the tool.
Beside scanning web page content, SpiderFoot looks at HTTP headers from which can be parsed out OS and web software names, and version numbers.
Why is this useful? For the attackers, knowing that an older version of Windows, Apache, or PHP is being used and exposed on the Internet makes it an excellent target. SpiderFoot, along with Maltego (below), also has integrations with other OSINT databases. So it’s possible to then search a software version against a known vulnerability database, and then work out the details of leveraging the security hole. Devious!
SpiderFoot provides a reasonably useful graphic interface showing the connections between various entities. Sure this can get a little overwhelming, and I found Maltego (further below) better at this. Still, SpiderFoot can help attackers view and understand relationships.
The larger point for defenders is that adversaries are being assisted with powerful technology — the kind once exclusively the domain of state-run intelligence agencies.
Executives should keep in mind that SpiderFoot is also helpful to defenders. Security analysts and pentesters can tell what’s exposed, whether your organization is unnecessarily giving away useful information, and perhaps finding outdated software. Bottomline: either the pentesters do this necessary intelligence work, or attackers will do it for you, and at a much higher price!
Shodan and Hacking
The next OSINT tool is far more menacing, and C-levels and executives should be aware of its evil power. Let me say that I have very mixed feelings about Shodan. Its claim to fame (infamy?) is that, unlike SpiderFoot it has already indexed a lot of the internet or as they put it, “the search engine for the Internet of Things.”
Some also call it, not unjustifiably, Google for Hackers.
I wrote about Shodan here in explaining the potential for BlueKeep to cause worldwide damage. Sure Shodan is wonderful for researchers and pentesters, but it has a very dark side to it. In my own wanderings through the IOT-verse with Shodan, I was able to find unguarded webcams or quickly spot poorly protected web sites and more. It’s creepy.
Note to Shodan overlords: you may want to do more of a background check on potential users before giving them access to this dangerous data. Just a thought. In the spirit of “do no evil”, I’m not even going to show any of the commands I used to get my Shodan results.
Shodan’s strength is in collecting and indexing banners: it’s the text that is displayed to users when a service is contacted. SpiderFoot will let you scan for banners as well, but for a specific website. Shodan has collected and indexed banners on a global scale. Yikes!
One interesting Shodan search for attackers is to look for banners that … wait for it … reveal information about passwords! Hard to believe, but companies can get careless about passwords and often are not aware that an IP port is open to everyone.
For example, telnet is the legacy protocol for communicating with devices through a simple text-based command line. Admins use it to gain remote access to servers, routers, and other IOT devices. Often there’s a text banner that displays a message welcoming you to the service.
Here’s where Shodan gets evil: it lets attackers search for those telnet connections — on port 23 — for which the banner might say something like “No password required” or “Use admin and 1234.” I know, but it does happen! This doesn’t necessarily mean that the telnet password hasn’t been changed, but that’s the hacking business: telnet ports with these revealing banners would certainly be a good candidate to probe.
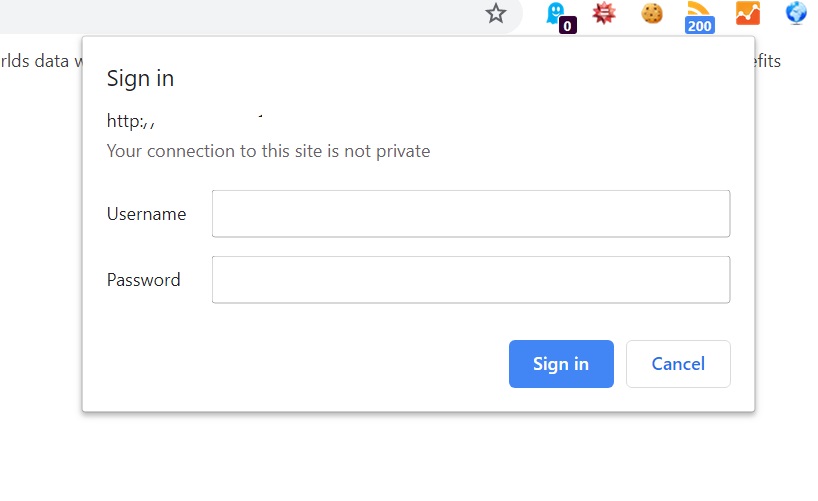
Another low-hanging fruit for attackers are websites that require a login through a form. We’ve all seen these forms (above). However, sometimes buried in the HTTP “header” information is … wait for it … the user name and password for the form! Like what Shodan has captured here:
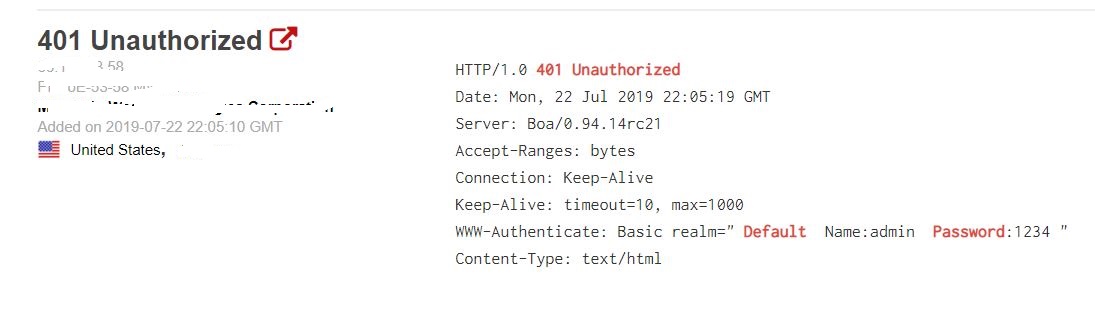
Shodan has scanned and indexed all these forms, which can be easily searched using its query syntax. Again, this hidden metadata with a password reference may have been a temporary convenience or the form meant to be used internally. In any case, it’s been located by Shodan and can be used against organizations.
The larger point is that OSINT tools, such as Shodan and also Censys, lets attackers pounce on these types of oversights by make the OSINT available to the rest of the world. Let me say it again: it’s important that people at the top of the company to realize that OSINT tools are readily available and easy to use.
Putting it All Together With Maltego
I’ll end this scary post — you’re not scared yet? — with an incredibly powerful app at the top of the OSINT food-chain. Maltego is a wonderful aggregator of interfaces to various OSINT databases. The company behind Maltego has even formed its own OSINT ecosystem. Like SpiderFoot, Malego can scan a target website. But then it lets its users effortlessly apply what it calls “transforms” from its ecosystem to connect the web information to various databases.
It also excels at displaying OSINT and enabling the user to draw connections as they gaze upon the graphical output.
For executives who are not seeing the big picture. Here’s a simple example that will bring it all back home.
With Maltego, attackers don’t necessarily need to master complex exploits. Instead it lets adversaries directly learn about employees credentials. We know that passwords are often reused by workers on their non-work Internet sites. Hold that thought.
Maltego lets users set up a structure for discovering employee email addresses. First, Maltego can discover the domain associated with a company website, and then by using various transforms to search social media, web pages, and other OSINT sources to find employee emails that reference that domain.
I tested this out quickly on the website of Paterva, the company behind Maltego. (No, they don’t mind.) I speedily picked up a few email addresses from the DNS registrations, and I would have easily gathered up more if I had paid for the Bing transform. In any case, it graphically organizes this information (below).
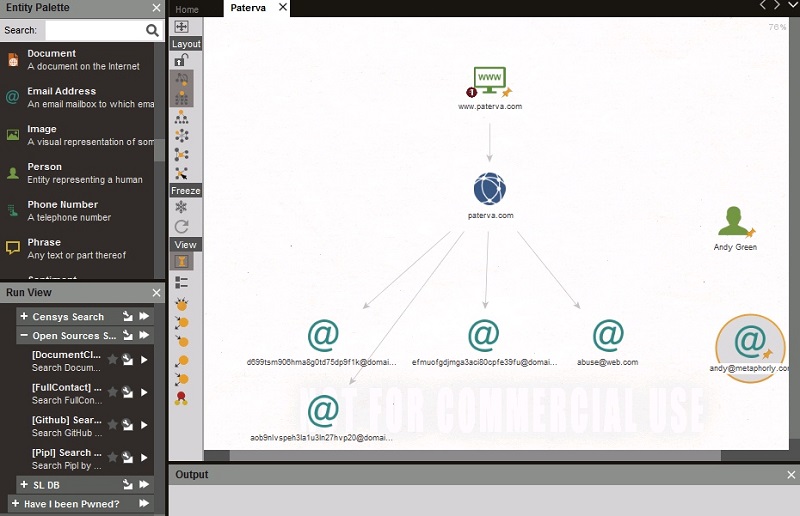
The next step is crucial. Maltego provides a transform to Have I Been Pwned, a database of emails that have been previously involved in a password breach. You see where this is going? I’ll now stop the example for security reasons! I’m a little concerned I’m giving away too much dark information.
Let’s just say that it’s possible for the attackers to find these passwords or learn something about the lazy security habits of employees, and then try out high-yield passwords on their work accounts.
Here’s the takeaway for C-levels: With Maltego, attackers don’t need to be very sophisticated about exploits or zero-day vulnerabilities, instead the tool lets them directly target employees and their web activities outside of work.
I’ve been blogging about infosec for years, and even I’m nervous about Maltego’s capabilities. With OSINT, knowledge is truly power.
Nervous as I am? Learn more about how Varonis can protect you from super-smart attackers!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)

