AI has enabled a new breed of email threats that are more deceptive than ever. By mimicking tone, language, branding, and even voice and video, attackers are unleashing automated phishing campaigns that are virtually impossible for humans — or traditional email security tools — to detect.
Email threats are more clever than ever
Email has always been a common channel for cyberattacks, but the latest wave of threats is far more deceptive than traditional spam or generic phishing attempts. Modern attackers use AI to mimic writing style, tone, branding, and even conversation history, making their messages difficult for both humans and legacy security tools to detect. These threats also blend text, images, links, and behavioral cues in ways that require more sophisticated, layered defenses.
Below are some of the most significant email-based threats facing organizations in 2026:
Business Email Compromise (BEC)
BEC attacks rely on impersonation — typically of executives, vendors, or trusted business partners — to manipulate employees into transferring funds or sharing sensitive information.
Modern BEC campaigns often:
- Use language and tone that closely match the impersonated sender
- Target individuals based on role, authority, or financial access
- Contain few or no links, making them harder for traditional filters to flag
- Leverage compromised inboxes to continue legitimate-looking conversations
Attackers increasingly use AI to generate believable messages, making manual detection almost impossible.
Phishing and spear phishing
Phishing attacks attempt to trick recipients into sharing credentials, financial data, or personal information by directing them to deceptive websites or prompting them to open malicious content.
Spear phishing is a more targeted version, crafted for a specific individual or group using details gathered from breached inboxes, social media, or public data.
Variants such as conversation hijacking occur when attackers gain access to a real mailbox, insert themselves into ongoing threads, and send fraudulent replies that appear entirely legitimate.
Common phishing tactics include:
- Fake login pages designed to capture credentials
- Emails that impersonate cloud services or IT teams
- Image-based messages that bypass text-based detection
- QR codes embedded in attachments or PDFs
These attacks have become harder to detect as adversaries use AI to refine grammar, context, and formatting.
Ransomware delivery
Email remains a primary channel for delivering ransomware payloads. Attackers often send:
- Malicious attachments disguised as invoices, contracts, or HR documents
- Links to compromised websites hosting ransomware installers
- PDFs or images that contain embedded links or scripts
Once executed, ransomware can encrypt data, disable systems, and disrupt operations. Recent campaigns frequently begin with a phishing email that establishes the attacker’s initial foothold.
The landscape has changed. Has your defense?
The first generation of AI-powered email security tools relies too heavily on NLP as a catch-all, and other solutions fail to incorporate behavioral analysis or fully analyze the visual elements of an email for anomalies using AI computer vision. Sophisticated phishing and social engineering threats require a layered approach.
Varonis Interceptor replaces ineffective API-based solutions and augments legacy SEGs with a true multimodal AI strategy. It combines numerous sources of AI-powered analysis to achieve a higher rate of detection and deliver superior protection.
How multimodal AI tools keep bad actors out
Robust email security solutions must adopt a multimodal approach to effectively detect modern threats. Attackers increasingly use varied techniques — like text manipulation, image-based phishing, and embedded malicious links — to evade traditional filters.
By combining signals from visual, linguistic, and behavioral analysis, Interceptor can accurately identify and block AI-generated threats. As a result, security teams experience fewer false negatives and positives, eliminating busywork and noise.
Vision model
The AI model simulates how users visually experience each email or website to detect subtle signs of deception in the layout, images, and other visual elements. This can include:
- Authenticity of the logo in an email signature or website
- Attackers' attempting to hide text by dropping it in as an image
- QR codes embedded in a PDF or obfuscated as text to avoid image processing
Language model
Models are grounded in the tone and linguistic patterns of each sender, including external parties such as vendors and internal communications. Interceptor also analyzes the topic, tone, and intent of messages to detect manipulation triggers common in social engineering attacks. Varonis’s Interceptor model is specifically tuned for scenarios where other NLPs struggle:
- Short messages with very little body or context
- Mail containing several incoherent topics aimed at deceiving AI
- Link-less BEC attempts
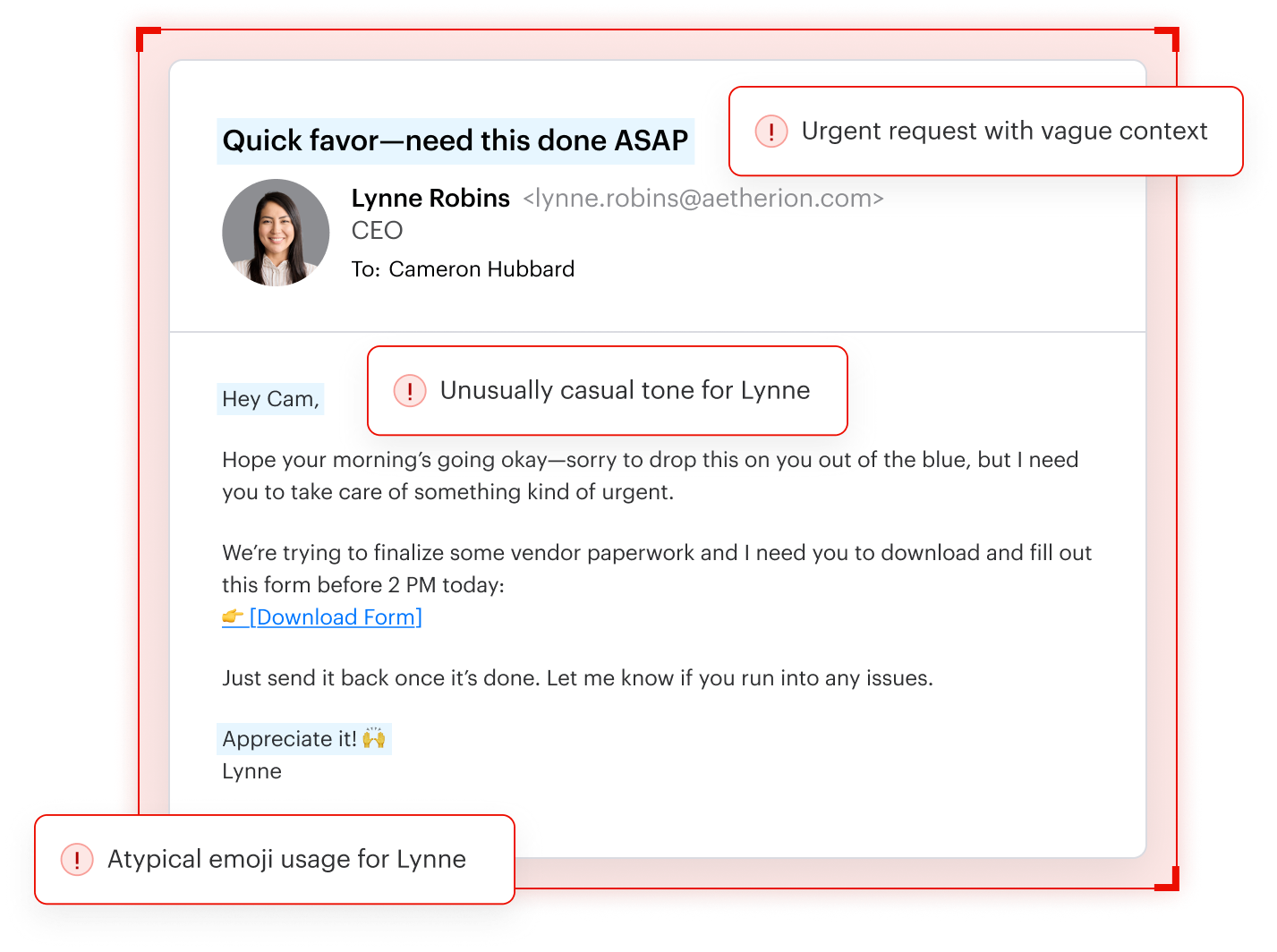
Behavior model
Behavioral models use the sender and recipient’s relationship graph and known communication patterns and conversation styles to detect deviations from their baseline. Interceptor can understand a full spectrum of social dynamics:
- Relationship graph and social patterns for internal and external parties
- Organizational structure and context
- Conversational styles and common topics
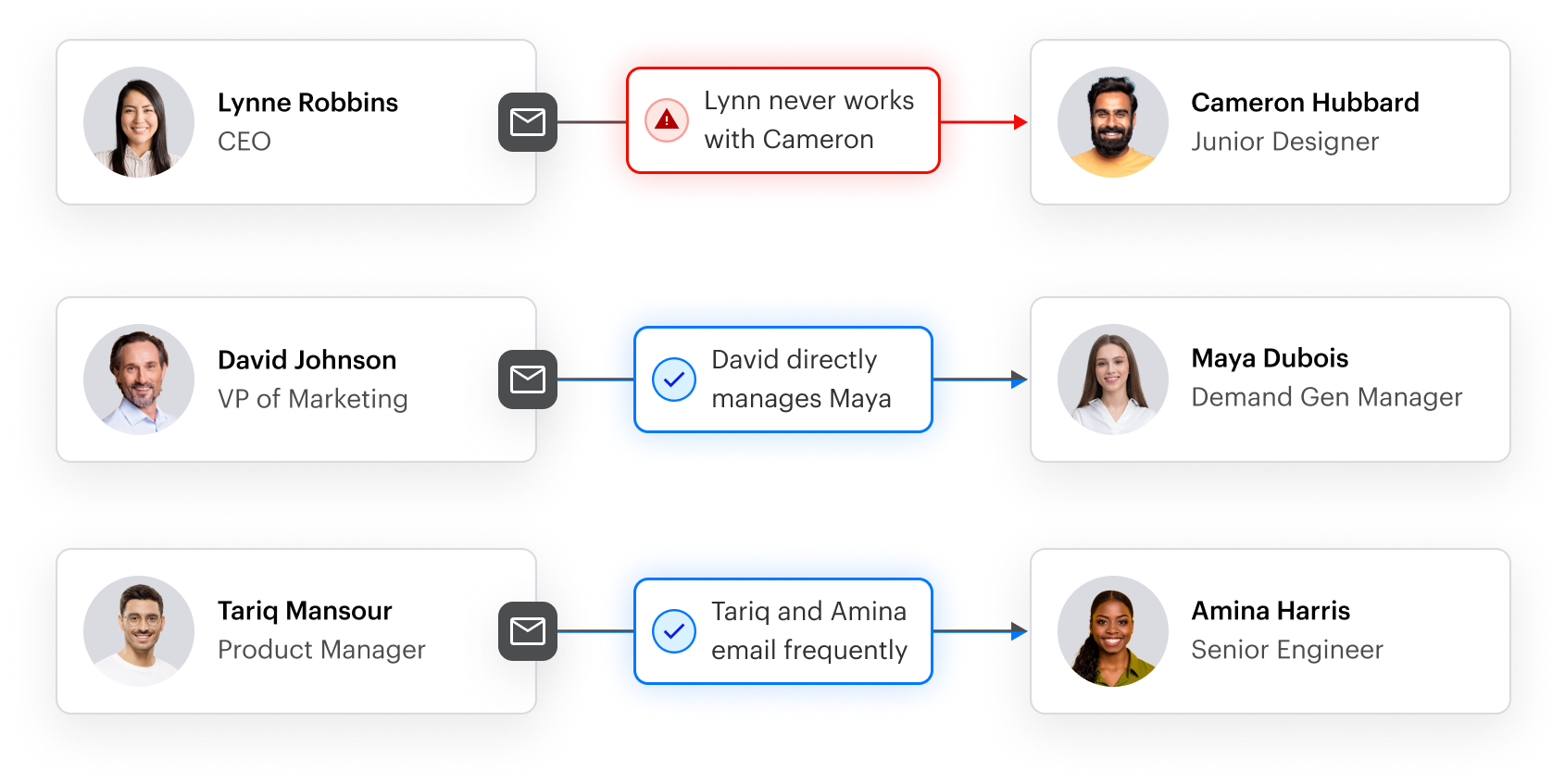
Applying this layered approach to identifying threats in real time has been proven to outperform other leading providers, such as Abnormal Security and Mimecast. Security teams prioritize detection quality above all else. Varonis Interceptor gives leaders confidence in their defenses and users trust in the inbox.
Detecting zero-hour threats
In addition to AI analysis conducted on messages, Varonis Interceptor proactively scans nearly every newly registered domain and published URL in its phishing sandbox, providing swift and in-depth analysis.
Interceptor’s Phishing Sandbox follows the user’s path to the very end, going past every form fill, CAPTCHA, Cloudflare authentication, and more. As a result, Varonis uncovers any potential attempt to trick users and steal secrets or credentials.
Interceptor is often the first AI to see and analyze the site before any other agent or human in the world. As a result, Varonis blocks malicious domains and URLs 12-24 hours before other solutions in the market and automatically removes mail containing them.
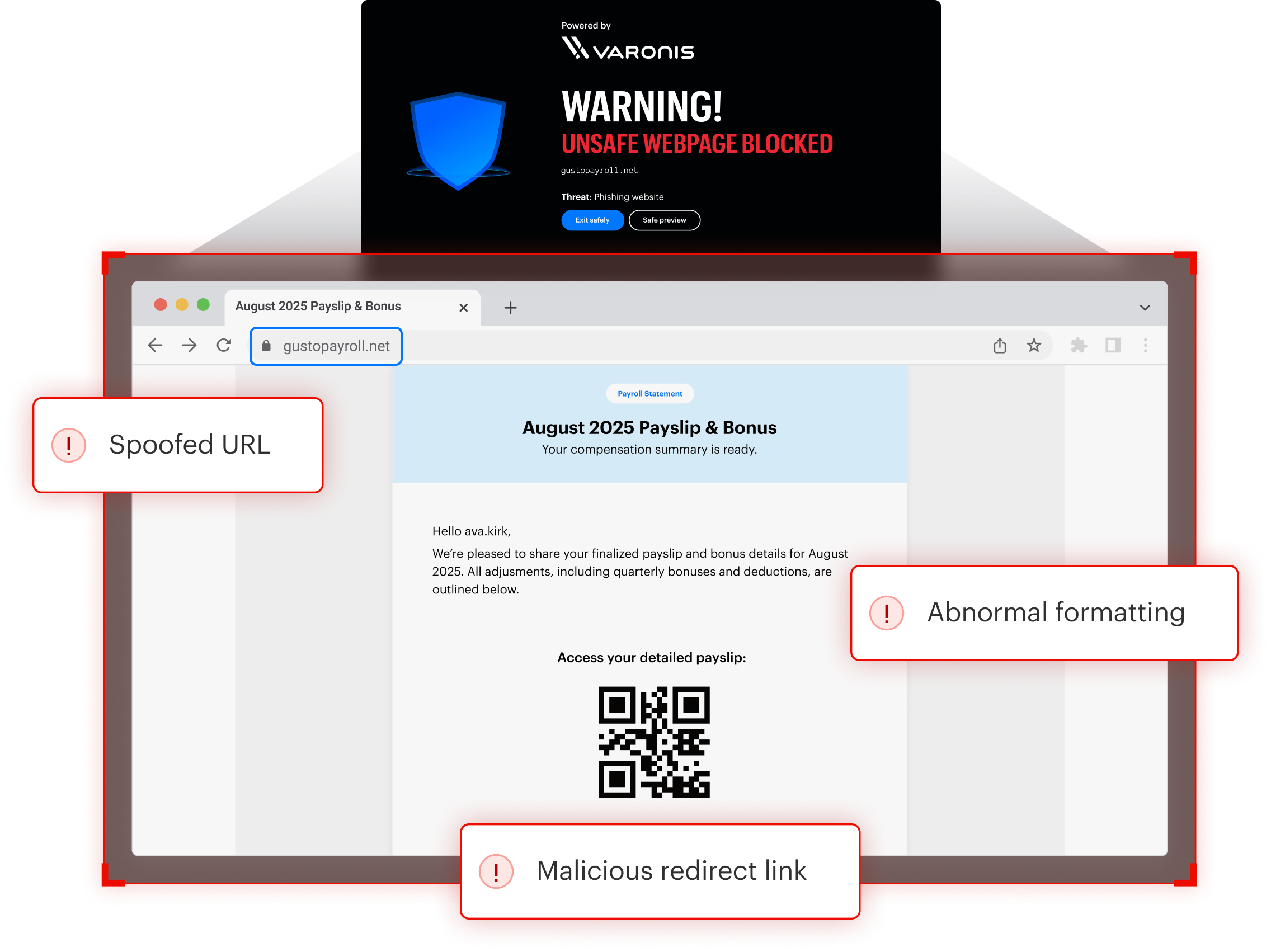
Multichannel protection beyond the inbox with Browser Security
Hackers are also flooding users with social engineering attacks across email, messaging, collaboration, and social apps. This requires a solution that spans multiple channels beyond email alone. Interceptor extends to the browser and blocks malicious websites, no matter where the link-based attack originates.
Most malicious links will slip past controls relying on known threat feeds. Interceptor receives advanced notice from its phishing sandbox and live threat database to stop threats as fast as they start. Interceptor Browser Security shields employees from live phishing sites with a lightweight browser extension available for all major browsers.
End-to-end approach to stop breaches
By offering Varonis Interceptor’s unmatched threat detection with the Varonis Data Security Platform and MDDR service, we are speeding up our ability to stop data breach attempts earlier in the attack chain.
Varonis integrates directly with email services like Microsoft Exchange Online to classify inbound and outbound traffic containing sensitive information, remediate posture issues on exposed mailboxes, and monitor anomalous email traffic for insider risks using industry-leading behavior analytics.
The addition of Varonis Interceptor represents a significant advancement in end-to-end email and browser security. By harnessing the power of multimodal AI, it more effectively identifies and mitigates phishing threats than current solutions in the market. Varonis Interceptor allows businesses to confidently protect their inboxes and, subsequently, the sensitive data in their digital estate.
Watch our Interceptor webinar to see how Varonis enables true AI-powered security outcomes.
Want to see what Interceptor can do faster? Request a demo today.
FAQs about AI-powered email security
How does AI email security detect new or "zero-hour" phishing threats?
AI-powered email security identifies zero-hour threats by proactively analyzing newly registered domains and URLs in a secure phishing sandbox. This allows the system to detonate links and follow them to their final destination, uncovering malicious intent before the threat is widely known or added to traditional blocklists. As a result, malicious sites can be blocked hours before other solutions become aware of them.
Can AI-powered security protect against malicious links outside of email?
Yes, comprehensive AI security solutions often extend protection beyond the inbox with browser security features. Through a lightweight browser extension, the system can block users from accessing malicious websites, regardless of whether the link was clicked in an email, a messaging app, or a social media platform. This creates a consistent layer of defense across multiple communication channels.
How does AI distinguish between legitimate and impersonated senders?
AI-powered systems build behavioral and linguistic profiles for each sender, analyzing patterns such as writing style, tone, typical recipients, and communication frequency. When a message deviates from these established norms—such as an unusual request, an unexpected contact, or an unfamiliar tone—the system flags it as potentially suspicious. This helps identify impersonation attempts that would appear legitimate based on content alone.
Can AI email security reduce false positives and alert fatigue?
Yes. By combining visual, linguistic, and behavioral signals, AI can more accurately determine whether a message is benign or malicious. This multimodal approach reduces the number of harmless emails incorrectly flagged as threats and limits the volume of alerts security teams must review. Fewer false positives means analysts can focus on higher-risk activity and respond more quickly to real threats.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









-1.png)