PeStudio is a tool used for statically analyzing malware and is one of my favourite tools for malware analysis.
Whenever I begin analysing a piece of malware, I will always load it into PeStudio first. It provides so much information about the sample and gives me a wealth of information for me to start building out my report. This is great for the initial triage of a malware sample.
In this article, I will cover what PeStudio is, some of the key features and how you can use it to begin analyzing malware.
Get a Free Data Risk Assessment
Basic Structure and Features of PeStudio
What I love about PeStudio is how easy it is to use and the clear, simple layout of the tool. Double-clicking the desktop icon opens the tool, to start investigating a piece of malware simply drag the malware sample into the tool.

The user is then presented with a number of tabs that provide varying information that PeStudio has pulled out of the sample
Main Tab
Upon opening a malware sample in PeStudio the user is presented with the Main' tab.

Here we are presented with information such as hashes of the sample, if you are dealing with a malware-related incident in your organization you could use this information to start blocking and looking for devices that have these hashes on the filesystem.
PeStudio also provides the first bytes in hexadecimal, in the image above we can see this is '4D 5A'. This is useful because it is confirming that the file is indeed a Windows Executable. The first bytes in the header of a file will always have the same byte pattern depending on the type of file. As Windows users, we typically identify a file by the extension appended to the file name i.e. '.exe'. However, the operating system recognizes each type of file by the byte pattern in the header, a Windows executable will always begin with '4D 5A' in hex, this equates to the values 'MZ' in ASCII.
The entropy of the file is also listed, this is useful because the value of the entropy can help identify if the malware is packed or not. Malware is often packed so that the code written by the malware author is obfuscated, the bad guys have taken time to write some malicious code and don't want it to be an easy task for somebody to take a quick look at the malware and in a short space of time identify what it does and how to stop it.
Entropy is measured on a scale of 0-8, the higher the value the more likely it is that the malware is packed with values of 7-8 pretty much confirming the sample is packed. This is useful because PeStudio is telling us that we will need to unpack the malware in order to pull out some useful IOC's.
In the image below, we can see that PeStudio has identified a signature for UPX which is a common packer used by malware authors. So by using PeStudio we can start to work out whether a sample is packed or not.

Indicators Tab
The next tab in PeStudio is the indicators tab, this highlights data within the sample that may be malicious and of interest to a malware analyst.

The above image shows how PeStudio has identified a number of indicators and classified them on a scale of 1-3, with 1 being a confident malicious indicator. In this example, it has identified some malicious strings, sections, imports and has found another file within the sample.
This is all useful information as PeStudio has tabs on the left-hand side for strings, sections, and imports that allows us to delve deeper into these suspicious indicators.
Sections Tab
The sections tab displays the various sections which make up the executable file.

In the image above we can see the section names associated with the UPX packer again confirming from using PeStudio that the malware is indeed packed. We can also see that section UPX1 contains the file that was first mentioned in the indicators tab, notice that this section makes up nearly 88% of the file and also has a high level of entropy. This indicates that the unpacked malware is being stored in this location. Once unpacked we can see sections that are more typical of an executable.

The above image shows how the section names have changed once the malware has been unpacked. Sections names can be anything however there are some common sections that you will come across.
The '.text' section contains executable code, looking at the columns of the section names we can see an 'x' next to the permission pane indicating that this section has executable permissions.
The '.rdata' and '.data' section store data, we can see that PeStudio has identified that the data section is writable.
The '.idata' section stores the Import Address Table, the IAT is covered later in the article.
The '.rsrc' section stores resources that can be used by the malware such as strings and additional files.
Libraries Tab
The libraries tab is useful as it displays what DLL's (Dynamic Link Library) are being imported by the malware.

The above image shows that PeStudio has blacklisted some of the DLL's meaning that they may be being used for malicious purposes by the malware. Looking at the names and descriptions it's safe to surmise that urlmon.dll, wininet.dll and ws2_32.dll relate to network functionality. It's not instantly clear what winmm.dll does, however, a quick google of the DLL may shed some light.

It looks like the malware may be potentially importing some functionality to record audio from a compromised device. Each DLL will contain a unique set of API, these are legitimate Windows functions that can be imported and used by the malware. By clicking on the imports tab we can take a look at what these functions are.
Imports Tab
The imports tab is the list of functions/API that have been imported by the malware, this is also known as the IAT (Import Address Table). By clicking on the blacklist tab PeStudio will sort the API by moving all the blacklisted functions to the top.

This is useful because from this information it's possible to get an understanding of how the malware may behave once it compromises a host. The above image shows what API has been imported.
What I think is useful is that next to each API name PeStudio will tell you what type of activity the API is related to under the 'group' column, from the above screenshot we can see the malware has imported some functionality relating to the registry so may use 'RegCreateKeyA' to create a run key which will launch the malware at startup.
We can also see some API that PeStudio is associating with network activity, 'URLDownloadToFileA' tells us quite clearly that the malware has the capability to download additional files from the internet. This type of information is extremely useful as before we run the malware in a malware analysis lab we can start to get an idea of how the malware may behave.
This information is also useful if we later begin to reverse engineer the malware using a tool such as x64dbg as we have already identified some interesting functionality that we can set some breakpoints on and see what values are being passed to these API by the malware.
Strings Tab
The strings tab lists any human-readable strings that PeStudio has identified within the binary. PeStudio will tell you what type of string has been found, where it resides in the binary but what I find useful is the blacklist, hint, and group columns within this part of the tool.
Blacklisted strings are strings that PeStudio has previously found in malware samples, the hint section gives the user some clues as to what the string relates to along with the group column.

The image above shows PeStudio has pulled out some interesting strings.
PeStudio confirms that the string 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)' is a user-agent. This is an old sample used for the example of this blog, however, if a unique user-agent was identified as part of a cyber-security incident this would be a valuable piece of information as the IR team could then start searching for this user-agent within the organizations proxy logs to identify any additional compromised hosts.
The next interesting string is 'Software\Microsoft\Windows\CurrentVersion\Run'. This is a common run key used by malware authors to automatically launch the malware if the device is rebooted. This is known as a persistence mechanism and the malware is making use of a legitimate Windows feature.
Legitimate software will use this technique so that your favourite software will automatically start when a device is powered on. Launching Registry Editor by typing 'regedit' into the Windows search bar will allow you to check what software has a run key in this location of the registry to start automatically.
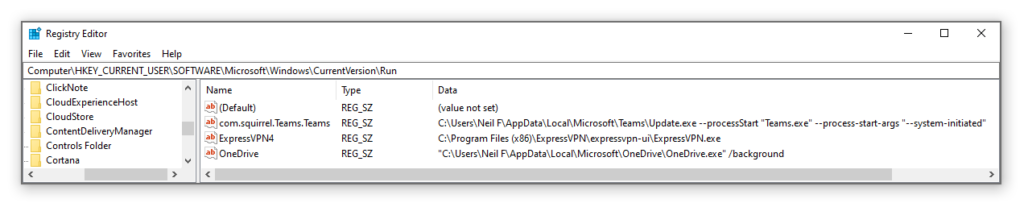
In the above image I have navigated to 'HKLM\Software\Microsoft\Windows\CurrentVersion\Run' on my host device and can see the software that will launch on startup. On my malware analysis lab, I could also use this technique when I have detonated a piece of malware to see if this persistence mechanism is being used and then identify where the persistence location of the malware is on disk.
PeStudio Setup
PeStudio is super easy to install, simply go to https://www.winitor.com/ and you will be presented with the following page.

Click the 'download' tab and you will be able to download the free version of PeStudio by clicking 'Download pestudio'.
You will then be prompted to download the latest version as a zip file.

Simply unzip the file and PeStudio will work as a standalone application. Be sure to keep an eye out as marc ochsenmeier who is the author of PeStudio provides regular updates to the tool.
Conclusion
Whether you are learning to analyze malware, triaging a malware incident or writing a YARA rule PeStudio is a great tool to use and has a great amount of depth to it. Whenever I need to build a new malware analysis lab it is the first tool I install and is the first tool I always use when I begin to look at a piece of malware.
If you are looking to mature your organization's security posture then check out Varonis' Edge: Perimeter Detection and Data Security Platform.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.