The Varonis Threat Labs team uncovered an attack that began as a routine Business Email Compromise (BEC) investigation and also leveraged Microsoft 365 administration tools against the very organization they were meant to serve.
This incident revealed a concerning evolution in attacker methodologies within M365 environments and demonstrates how threat actors are moving beyond simple credential harvesting to systematically exploiting administrative privileges and platform features for large-scale malicious operations.
Understanding inbound connectors
At their core, inbound connectors in Exchange Online serve as specialized mail flow rules designed to authenticate and route emails from predetermined external sources. These configurations facilitate reliable communication with trusted partners or cloud services by exempting specified traffic from standard spam filtering mechanisms.
While this functionality proves invaluable for legitimate business operations, it simultaneously creates an attractive exploitation vector for threat actors. The very features that ensure seamless business communications, namely the bypassing of spam filters and sender authentication requirements, can be subverted to establish unfiltered channels for malicious email delivery.
Mail Flow Diagram by Microsoft
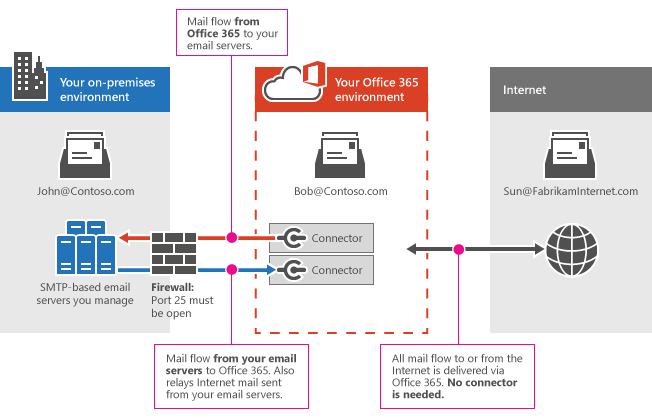
Mail Flow Diagram by Microsoft
Initial Access
The attack chain commenced with the compromise of a M365 account that was likely obtained through either a sophisticated phishing campaign or a credential stuffing attack.
This compromise was possible due to a lack of MFA for the user in question. Forensic timelines suggest the credentials were harvested days before active exploitation began, indicating a patient reconnaissance phase.
The targeted account possessed moderate administrative privileges, sufficient to create new users and modify certain configurations, but not global administrator rights.
The attackers' careful selection of a mid-privileged account reflects their operational security awareness, choosing a target that could facilitate escalation while flying under the radar of privilege monitoring solutions.
Establishing a persistent foothold
Upon gaining initial access, the threat actor immediately created a new admin account with naming conventions mimicking legitimate service accounts. This backdoor account then became the foundation for more sophisticated control as the attacker proceeded to register a malicious third-party application within Azure AD.
The application registration served multiple purposes — granting extensive access via the Graph API while establishing an alternative access method that would survive potential credential resets for the newly created user or initially compromised account. This dual-layer persistence strategy demonstrated the attackers' understanding of cloud identity management and their preparation for potential remediation attempts by the victim organization.
Privilege escalation and environmental control
With application-based access secured, the attackers began systematically expanding their control through calculated privilege escalation.
They first elevated their created account to global administrator status, then moved to disable critical security controls, including MFA requirements for privileged accounts.
Perhaps most concerning was their modification of audit log retention policies, a clear indication of their intent to operate undetected for extended periods. These actions revealed not only their technical capability but also a sophisticated understanding of Microsoft 365's security model and common enterprise monitoring practices.
The attackers demonstrated particular interest in maintaining operational security while methodically removing potential obstacles to their objectives.
A Varonis export of events where the malicious application was set up and an inbound connector shortly after.
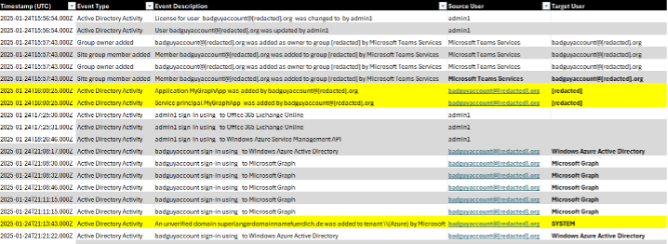
A Varonis export of events where the malicious application was set up and an inbound connector shortly after.
Weaponizing the environment
The attack reached its operational climax with the strategic weaponization of mail flow configurations. The creation of an inbound connector to an attacker-controlled domain established a trusted channel for unfiltered email delivery, effectively bypassing all the organization's email security measures.
Simultaneously, the threat actor executed several parallel actions to maximize impact and hinder response efforts. They created numerous distribution groups populated with an extraordinary volume of external addresses — over 250,000 entries — while removing administrative privileges from legitimate users.
The final act of deleting the initially compromised account completed their control of the environment, leaving the organization locked out of its own tenant while the attackers maintained full access through their established persistence mechanisms.
Illustrating the amount of distribution groups stood up by the attacker, about 250,000 users in total.
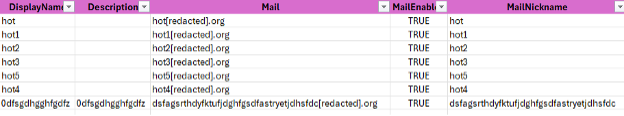
Illustrating the amount of distribution groups stood up by the attacker, about 250,000 users in total.
A second intrusion attempt
Following the initial investigation and remediation recommendations, the client's failure to remove the malicious inbound connector in a timely manner created an unfortunate security gap that the threat actors quickly exploited.
The compromise began again with the establishment of two global administrator accounts bearing deceptive naming conventions designed to resemble legitimate Microsoft service accounts. This deliberate obfuscation represented an evolution in their tactics, showing an understanding of common detection methodologies. These new accounts immediately began accessing sensitive areas of the administration panel, with particular focus on the Compliance Center.
Their activities within the Compliance Center revealed a methodical approach to reconnaissance. Focused searches targeted mail flow forwarding configurations, connector status reports, and transport rule audits. These actions suggested either an attempt to verify the status of their previously established attack infrastructure or to identify new vectors for data exfiltration.
**/
/DataInsights/DataInsightsService.svc/Find/MailflowForwardingData?tenantid=[redacted]&PageSize=1500&Filter=StartTime eq 2025-02-12T15:28:33.4560000Z and EndTime eq 2025-02-19T15:28:33.4560000Z and ReportType eq 'ForwardingType'
/DataInsights/DataInsightsService.svc/Find/ConnectorReportData?tenantid=[redacted]&PageSize=30&Filter=StartTime eq 2025-02-12T15:28:33.4580000Z and EndTime eq 2025-02-19T15:28:33.4580000Z and ReportType eq 'MailFlow' and ReportDataType eq 'Detail'
The searches were kicked off in the environment after the attacker came back in.
Conclusion and security implications
This incident emphasizes how administrative interfaces themselves can become tools for reconnaissance and attack preparation.
Activities that might appear as routine administrative work — running reports, checking configurations — can serve as the foundation for more destructive actions when performed by compromised accounts.
This reality reinforces the need for a security approach that treats all privileged access as potentially compromised and evaluates actions based on contextual factors rather than surface legitimacy.
Implications from this investigation underscore several critical security imperatives, beginning with the need for comprehensive privilege access management that extends beyond simple credential protection. Organizations must implement robust monitoring for application registrations and API permissions, coupled with approval workflows for critical configuration changes.
Most importantly, this attack demonstrates that in cloud security, the distinction between legitimate administrative functions and potential vulnerabilities often becomes dangerously blurred, requiring security teams to adopt a more nuanced approach to monitoring and control.
The reality of modern cloud administration demands that every configuration option be evaluated not just for its business utility, but for its potential exploitation by determined adversaries.
Recommendations
-
Get proactive with Varonis MDDR: License the Varonis Managed Data Detection and Response (MDDR) service to stay ahead of threats. It continuously monitors your environment and helps catch risks before they turn into real problems.
-
Require MFA: Turn on multifactor authentication for all admin accounts. It’s one of the simplest ways to block unauthorized access.
-
Keep an eye on app registrations: Regularly review third-party app registrations in your tenant. It’s a great way to spot anything suspicious early and shut it down fast.
-
Audit admin activity: Continuously track key admin actions — like creating new accounts, changing permissions, or tweaking mail flow settings. These changes can signal trouble if left unchecked.
-
Tighten connector policies: Set clear rules for creating and modifying mail flow connectors. This helps prevent attackers from sneaking in through misconfigured settings.
-
Stick to least privilege: Make sure admin accounts only have the access they truly need. The less access, the smaller the blast radius if something goes wrong.
To learn more about Varonis MDDR, schedule a demo with our team.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








