Ready to hear something frightening? According to Deloitte, an estimated 91% of cyberattacks start with email.
Mailboxes are sensitive data goldmines that, without proper protection, can easily fall into the wrong hands. And despite emails being the source of several significant data breaches, protecting data in your inbox continues to be a blind spot for companies.
With the rise of Microsoft 365 Copilot and other generative AI tools that rely on user permissions, it is imperative that organizations lock down their email access on a need-to-know basis.
Enter Varonis for Exchange Online — a layer within our comprehensive Data Security Platform that provides comprehensive coverage not just within Microsoft 365 but across the broader cloud ecosystem. This integral part of our platform is specifically designed to continuously detect and prevent exposures in the world’s top cloud-based email service and enhance your overall data security.
We’ve extended Varonis’ patented data classification technology to email messages, attachments, and calendar events, which adds vital context to our best-in-class Exchange Online threat detection and exposure analysis capabilities.
With Varonis, security teams proactively reduce their email attack surface, stop data exfiltration, and curb generative AI risk with accurate and automated email security. Users can:
- Identify mailboxes exposed to guest and external users, non-mailbox owners, or delegates.
- Right-size and monitor access to sensitive mailboxes and calendars.
- Detect and flag data privacy violations or improper data handling.
- Validate data loss prevention (DLP) policy effectiveness and swiftly address gaps.
- Perform security investigations with an enriched audit trail of all email activity (send, receive, delete, etc.).
- Alert and auto-respond to anomalous email activity.
Let’s take an in-depth look at how each of these features helps protect your critical data in Exchange mailboxes.
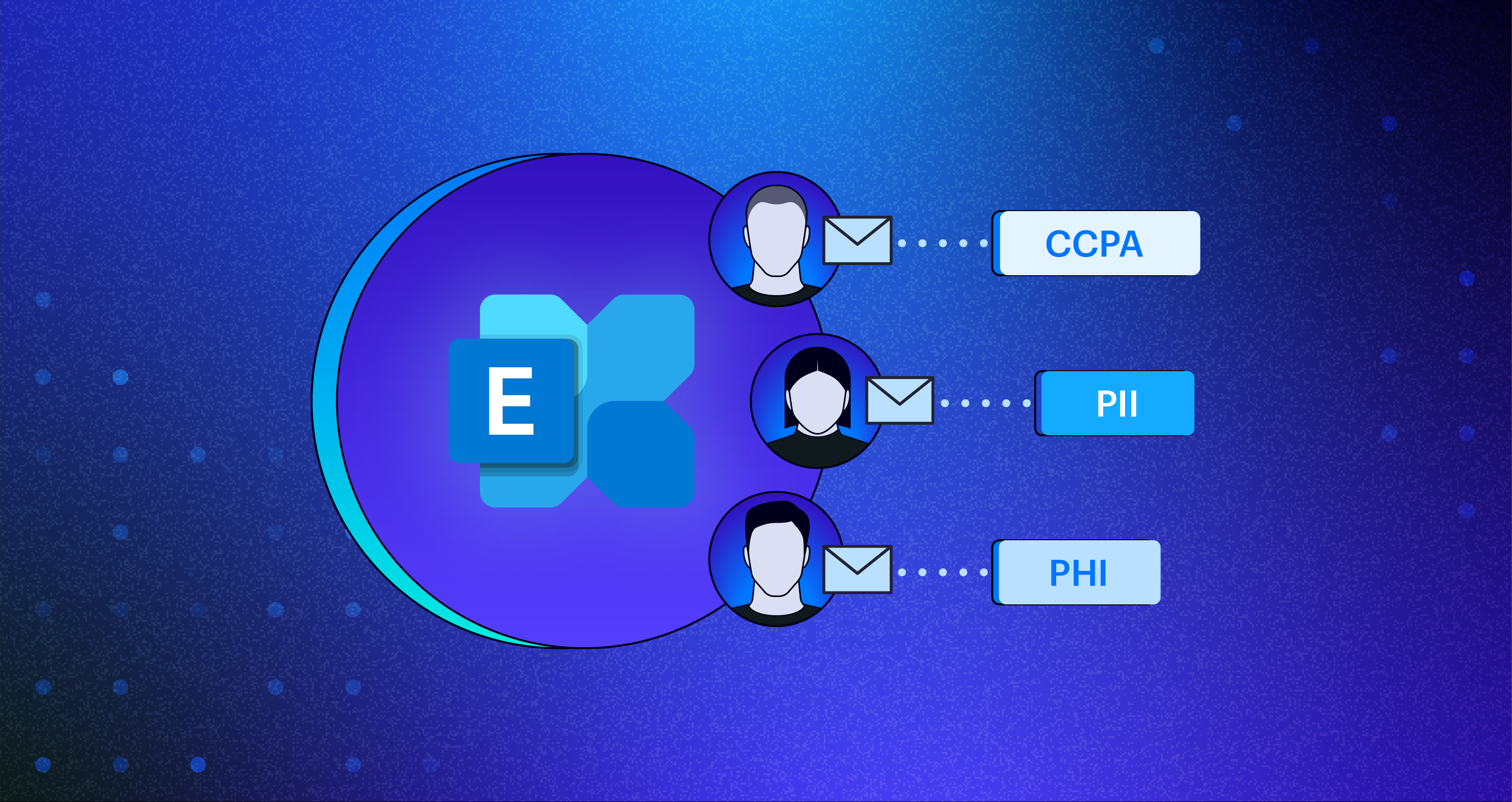
Classify sensitive data in Exchange Online.
Varonis scans every user and shared mailbox and calendar, flagging the sensitive data in both the body and attachments to show you exactly where it lives and who has access to it, all in an easy-to-read file tree.
Our data classification capabilities go beyond regular expressions and include pre-built databases of known valid values, proximity-matching, negative keywords, and algorithmic verification to generate accurate results.
Varonis also simplifies compliance and ensures DLP policies are effective with a comprehensive library covering regulations such as GDPR and HIPAA, helping you find and secure your sensitive data that may be improperly stored or shared.
An easy-to-read file tree view gives you all the important information you need.
Monitor email security posture.
The Varonis Exchange risk dashboard provides a centralized overview of your email security posture.
You can easily see where there are large concentrations of sensitive data in Exchange mailboxes or where mailboxes are exposed with drill-down widgets that allow you to easily see the scope of each mailbox’s permissions and limit the risk.
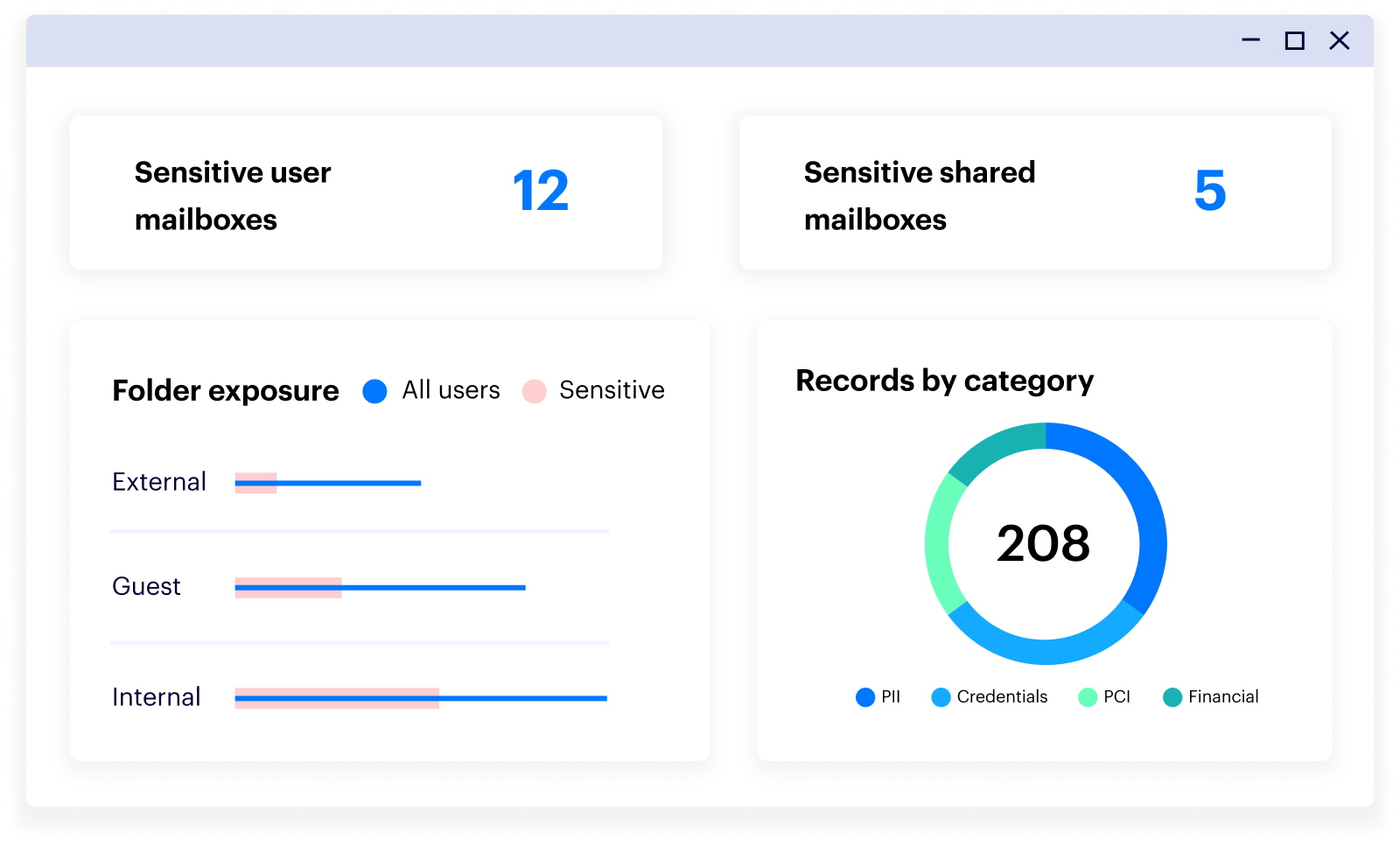 Monitor your email security posture with an intuitive, customizable dashboard.
Monitor your email security posture with an intuitive, customizable dashboard.
See data exposure with deep permissions analysis.
Being able to monitor mailbox permissions in Exchange Online is essential to ensure security and compliance. Unauthorized access can lead to can lead to someone reading sensitive emails, altering permissions, or — even worse — moving sensitive data elsewhere, like external mailboxes. Knowing who has access to your mailboxes to prevent potential data leaks is crucial.
Using PowerShell to check mailbox permissions in Exchange Online can be complex and slow. Varonis simplifies this by automatically tracking who has access to mailboxes and calendars, including guests and external users.
Easily limit access change permissions to a small group of admins, archive and delete stale users to enforce least privilege, and correct guest permissions associated with shared mailboxes and calendars containing sensitive data.
View all user and shared mailbox permissions.
Quickly detect suspicious email behavior.
Knowing where you have sensitive data and who can access it is a critical first step in securing your environment, but to detect threats, you need to monitor what users are doing with your data.
Our platform enhances built-in Exchange alerting by combining activity from Microsoft 365 and Entra ID with on-premises and perimeter telemetry.
With Varonis’ behavior-based threat models, you can spot anomalous email activity that could indicate data exfiltration and other email-based attacks or abuse. This includes detecting unusual permission changes, automatic forwarding, malicious attachments in real time, and other activities that could put your data at risk of compromise.

![]()
View details about the risky activity happening in your environment.
Investigate alerts across your entire ecosystem.
Varonis’ alerts make it easy to dive into a cross-cloud investigation.
You can drill down into a user's activity, both in Exchange, across Microsoft 365, and on-premises environments, to see what data was accessed.
Varonis provides an enriched audit trail of all email activity — send, receive, delete, etc. —correlated with events in Active Directory, Microsoft 365, and corporate file shares. This gives your team the ability to easily perform security investigations and identify the actions taken on emails like who sent what and when — along with a host of other useful information, such as IP addresses, countries, and action types.
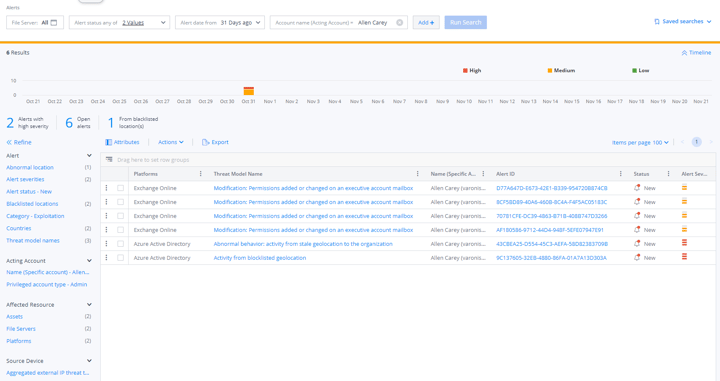
Investigate incidents faster with a complete audit trail of activity.
See Varonis for Exchange in action.
At Varonis, we see the world of cybersecurity differently and our innovative security measures for Exchange Online accelerate our ability to protect your data at all costs with unprecedented exposure analysis features and data classification capabilities.
Knowing where your sensitive data exists, who can access it, and what users are doing with it are all critical questions that need answers to protect your organization from today's cyberattacks. Varonis uniquely combines these key security aspects in one solution.
At Varonis, we’re on a mission to deliver automated security outcomes and offer robust capabilities. Varonis for Microsoft 365 installs in just minutes and protects your sensitive data across OneDrive, SharePoint Online, Exchange Online, and Teams.
Are you curious to see what risks may exist in your SaaS environment? Get started today for free, no strings attached. We can have you up and running in minutes.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.