Researchers recently uncovered a vulnerability in Exchange that allows any domain user to obtain Domain admin privileges that allow them to compromise AD and connected hosts.
Here’s how the attack works:
- Attacker uses a compromised mail-enabled domain user to subscribe to the exchange push notification feature
- Attacker uses an NTLM relay to impersonate the exchange server:
- The Exchange server authenticates to the compromised user’s host using NTLM over HTTP, which the attacker users to authenticate to the domain controller via LDAP with the exchange account’s credentials
- Attacker then uses the exchange account’s permissions to change permissions on the domain object*
The attacker can then run a DCSync to get hashed passwords of all domain users – which enables them to execute different types of attacks – from golden ticket attacks to pass the hash.
Our research team has investigated and built a guide for our customers to detect this type of attack – and to see if they’ve been compromised already.
Here’s what you need to know.
*This last step could also be by a rogue admin, who has legitimate access to make that permission change: by creating a rule to detect on that activity, you’ll be covered either way.
How to detect domain privilege escalation
In DatAlert, create a custom rule to monitor specific permission changes on an object – this will trigger when a Directory Services object permission is added on the domain object.
- Set the rule name
- Set the alert category to “privilege escalation”
- Set resource type to “all values selected”
- Define the affected Object:
- File Server = DirectoryServices
- Choose the Domain object
- Create filter for DS object permission added
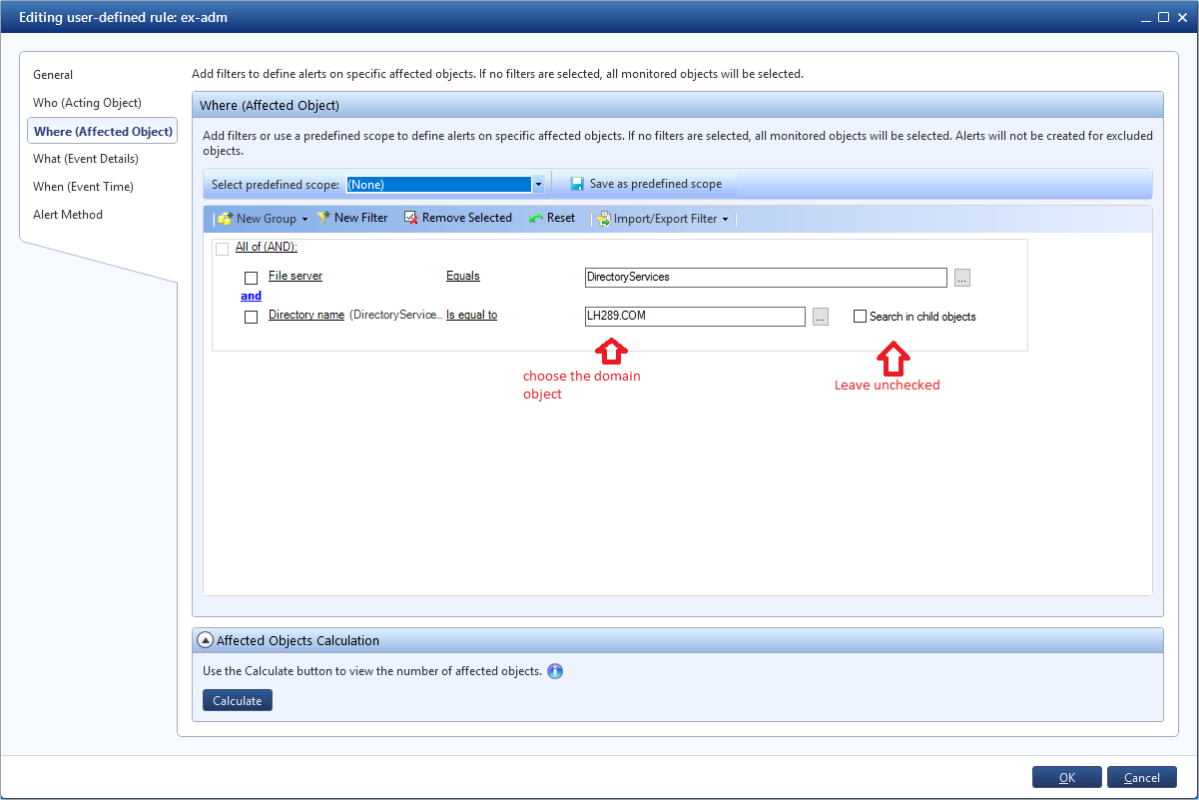
Running the report: How to detect permission change on the domain object
Permission changes on the domain object shouldn’t be common; anything that triggers this alert should be investigated. Keep in mind, this is only a checkbox away from alerting on any DS permissions change (don’t forget to leave the “search in child objects unchecked!) – so generate a report to validate the alert before you deploy.
You’ll be able to see in this report if you’ve already been compromised by this attack as well.
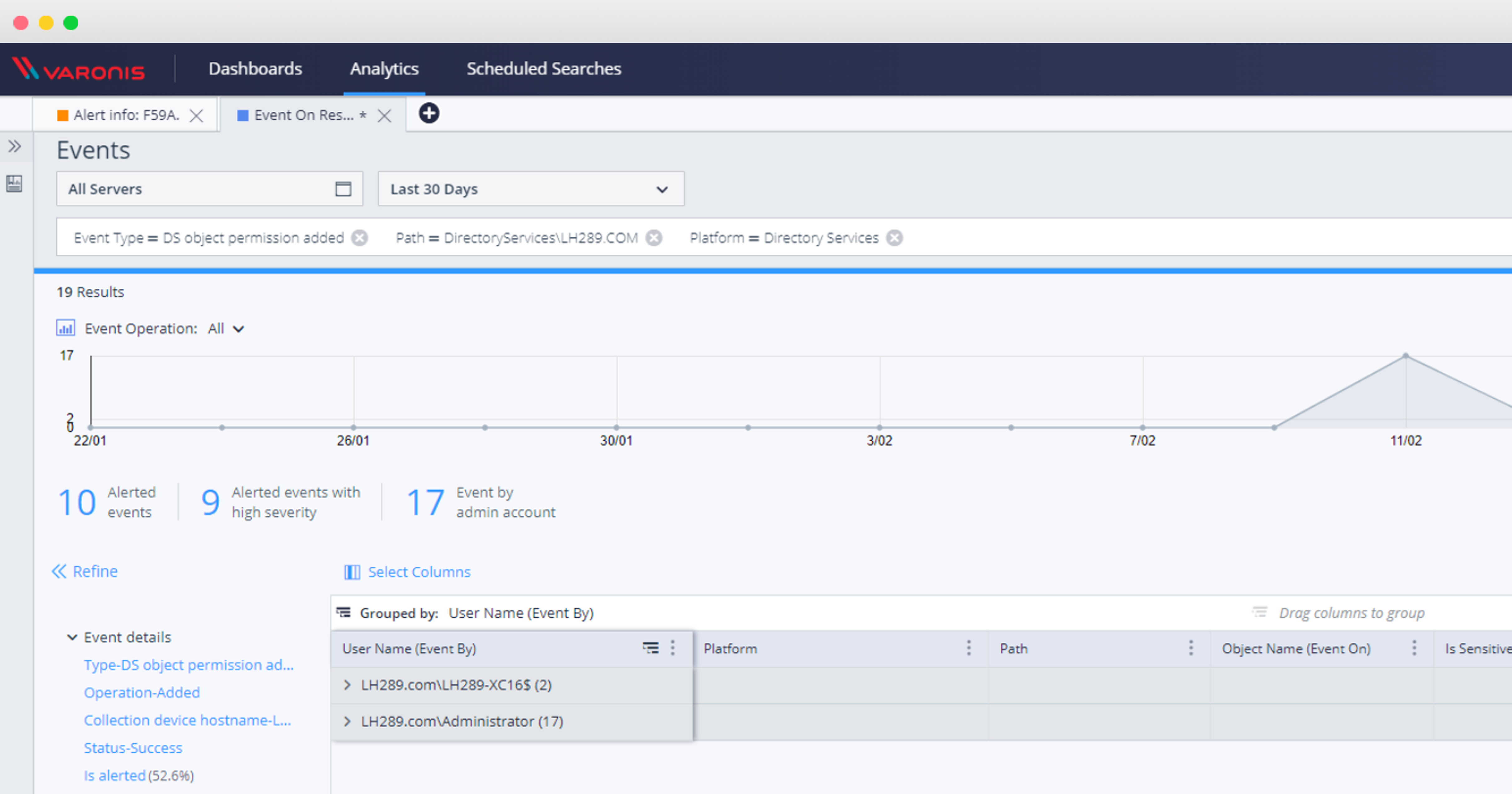
Once the rule is deployed, you can investigate this type of privilege escalation through the web UI:
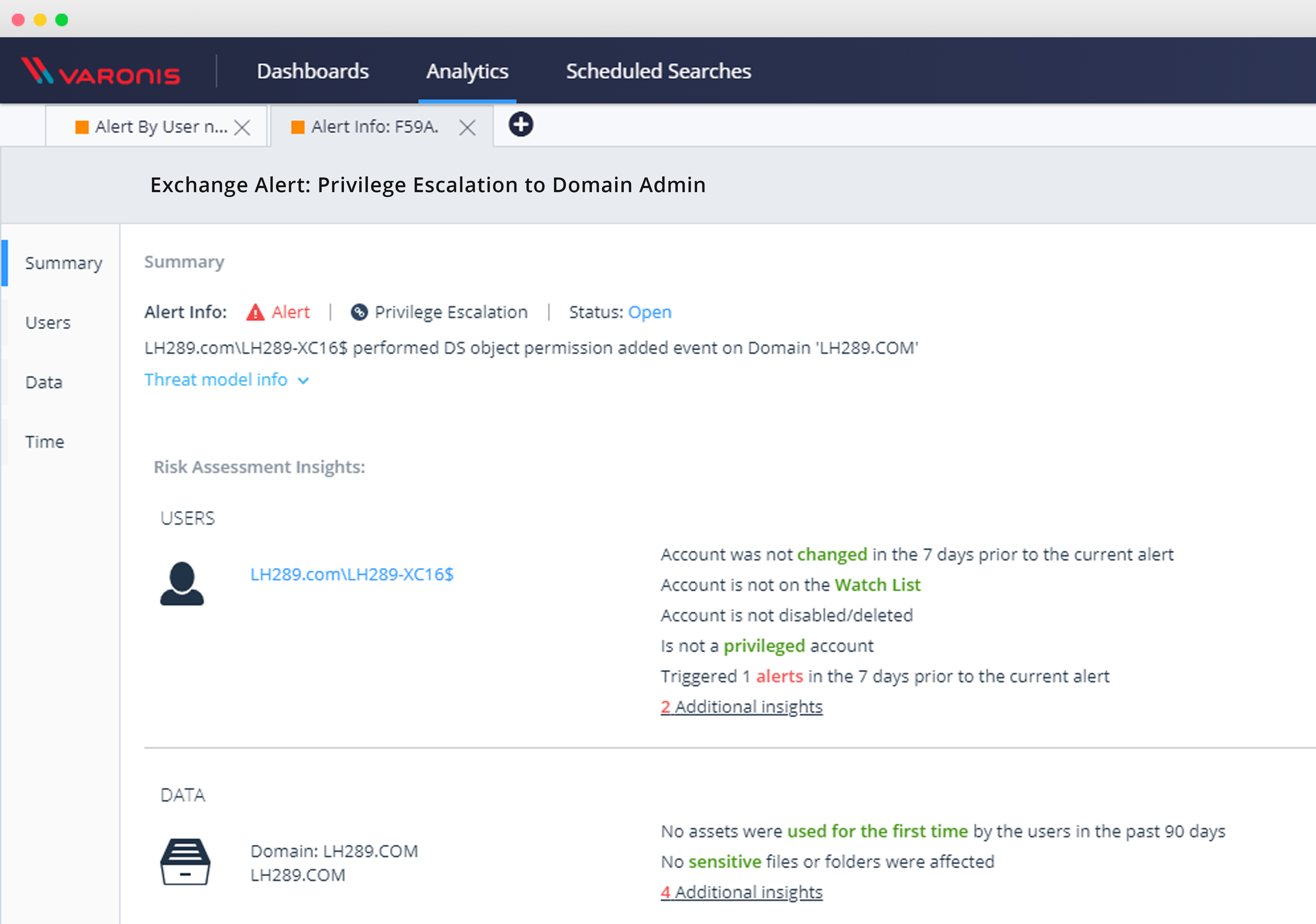
Once that rule is set up, you’ll be able to monitor and protect against these types of security vulnerabilities, investigate Directory Services object events, and verify whether or not you’ve been affected by this vulnerability.
Check out the Microsoft security update as well – and reach out to your SE if you have any questions.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.