Data Security Posture Management (DSPM) is a proactive approach that provides continuous visibility, risk assessment, and management of sensitive data.
Historically, DSPM has been straightforward in an on-premises environment, where data lives within clear boundaries. However, cloud adoption forces organizations to rethink their traditional DSPM practices.
The dynamic, scalable, and distributed nature of cloud environments introduces complexities that alter data security considerations. In this blog, we will explore how DSPM in the cloud differs from the traditional approach.
Traditional DSPM: Less dynamic, more easily defined
In the traditional settings, data resides within clearly defined perimeters, making security management relatively straightforward. Key components of traditional DSPM include:
- Data discovery and classification: Identifying sensitive or regulated data such as personally identifiable information (PII), financial records, or intellectual property, and classifying it based on its sensitivity and compliance requirements.
- Risk assessment and monitoring: Regularly evaluating the security risks associated with data storage, access, and transfer, often using manual audits or scheduled scans.
- Access controls: Implementing and enforcing data access policies to ensure only authorized users and systems can access sensitive information, generally through static permissions and predefined roles.
- Compliance management: Ensuring ongoing compliance with regulatory frameworks and standards, such as GDPR, HIPAA, PCI DSS, and ISO 2700, by continuously monitoring and reporting the organization's posture.
However, traditional DSPM has notable limitations, including reliance on manual processes or periodic security reviews, which can cause delays, inaccuracies, or incomplete visibility.
The shift to cloud
Unlike on-prem environments with fixed perimeters and static infrastructure, the cloud is dynamic and decentralized. Data moves freely across platforms, regions, and services, introducing new challenges for maintaining security and visibility.
Shared responsibility
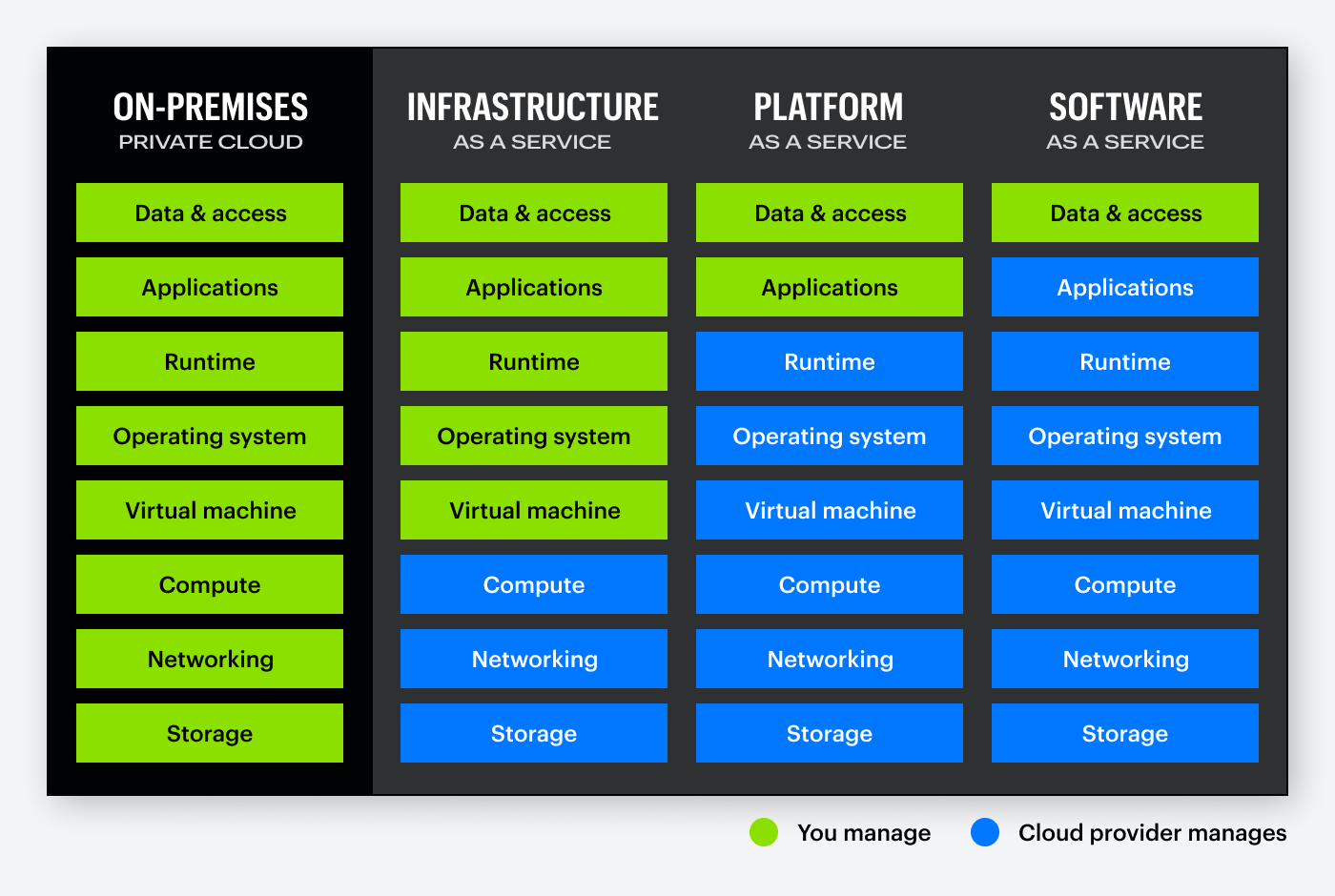
A key difference in the cloud is the shared responsibility model, where cloud providers secure the infrastructure, but customers are responsible for protecting their data and configurations. This division often leads to misconfigurations, one of the most common causes of cloud data breaches.
Increased agility, increased risk
The agility of the cloud allows rapid scaling and deployment, but also increases the risk of data sprawl, shadow data, and inconsistent access controls. Traditional DSPM approaches, which rely on periodic audits and manual processes, struggle to keep up with the pace and complexity of cloud environments.
To secure data effectively in the cloud, organizations must adopt real-time, automated DSPM strategies that offer continuous visibility, consistent policy enforcement, and adaptability across diverse and ever-changing ecosystems.

What changes with DSPM in the cloud?
Moving DSPM to the cloud isn’t just a shift in location: it’s a shift in complexity, scale, and speed. Several factors change how DSPM must operate:
Continuous discovery becomes essential
In traditional environments, data was relatively static. In the cloud, data stores, backups, and services can be spun up or retired in minutes. DSPM must move from periodic scans to continuous, automated discovery to keep track of where sensitive data lives at all times.
Managing identity and access is more complex
Cloud infrastructures rely heavily on dynamic identities, such as users, services, and roles, across different accounts and regions. Managing who has access to what becomes exponentially harder. DSPM solutions must integrate deeply with cloud-native IAM systems to monitor and enforce least-privilege access in real time.
Shadow data grows quickly
Shadow data, copies of sensitive information in unknown or unmanaged locations, proliferate in the cloud due to rapid scaling and easy sharing. Without visibility, organizations risk exposure: cloud DSPM must be able to detect and map shadow data wherever it appears.
Compliance pressures are heightened
Cloud data often crosses geographic and regulatory boundaries, complicating compliance with laws like GDPR, HIPAA, and CCPA. Cloud DSPM must be able to track data residency, ensure encryption, and demonstrate compliance dynamically, not just during annual audits.
Shared responsibility changes the risk model
In the cloud, security is no longer fully in the organization's control. The shared responsibility model means DSPM must continuously assess not just internal practices, but also how cloud services are configured and used, spotting misconfigurations before they become vulnerabilities.
Advantages of DSPM in the cloud
While the cloud introduces new challenges for data security, it also unlocks powerful advantages for organizations that adapt their DSPM strategies accordingly. Done right, cloud-based DSPM can be even more effective than traditional approaches.
Real-time visibility and monitoring
Cloud-native DSPM tools can continuously scan and monitor data environments without the lag of scheduled audits. This enables real-time visibility into where sensitive data lives, how it moves, and who accesses it: a critical advantage for detecting risks and responding faster to incidents.
Automation at scale
In the cloud, automation is a core capability. DSPM can leverage automated discovery, classification, risk analysis, and even remediation workflows. This reduces manual work, eliminates blind spots, and allows security teams to scale their efforts across vast and growing cloud environments.
Easier integration with modern architectures
Cloud DSPM solutions are designed to integrate natively with cloud services like AWS S3, Azure Blob Storage, Google Cloud BigQuery, Kubernetes clusters, and others. This tight integration provides deeper insights and stronger control over complex, distributed environments without heavy custom configuration.
Faster incident detection and response
With real-time monitoring and automation, cloud DSPM helps organizations detect and contain data security threats much more quickly. Rapid identification of misconfigurations, suspicious access patterns, or unauthorized data movement dramatically reduces potential breach windows.
Enhanced compliance management
Cloud DSPM tools can automate compliance checks, generate real-time audit trails, and ensure that sensitive data stays in the right locations, encrypted, and accessed appropriately. This makes it easier to prove ongoing compliance with regulations like GDPR, HIPAA, and SOC2, even in complex, multi-cloud environments.
Varonis solves common DSPM challenges
Managing data security posture in the cloud doesn’t have to be overwhelming, especially with the right partner.
Varonis delivers a powerful, automated approach to DSPM, helping organizations gain deep, real-time visibility into sensitive data across cloud and hybrid environments.
Varonis solves common DSPM challenges by continuously discovering and classifying sensitive data, enforcing least-privilege access, and detecting threats in real time. As highlighted on our coverage page, our platform protects data across SaaS, IaaS, and on-prem environments — including Box, Salesforce, AWS, and more.
Want to see how it works? Watch our webinar to learn how Varonis helps organizations do more with DSPM in the cloud. Our cloud security experts share how you can use your DSPM to build scalable cloud data security efforts that evolve with the constant changes in the cybersecurity landscape.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.








