Protecting your company's data is increasingly difficult as more and more data is created across your organization.
You're doing everything you can to prevent breaches, or even worse, have had a data breach and need to work out how it happened.
On top of that, you've got laws and regulations to comply with — both broader laws like GDPR, as well as regulations specific to your area (CCPA) or industry (HIPAA).
This is why it's so important to have the right tools in place to make this as easy as possible for you.
A good DSPM can solve a lot of these problems!
Why is DSPM important?
DSPM is designed to protect sensitive data and ensure compliance with regulations across various environments, including SaaS, cloud-based, and on-premises platforms.
The primary objective of DSPM is to ensure the security and compliance of data, regardless of where it resides. DSPM implements comprehensive measures such as data discovery, classification, access controls, and continuous monitoring.
Organizations are rapidly adopting DSPM solutions for three main reasons:
Breach avoidance
As a CISO, it's your responsibility to not only protect against breaches, but also report back to management exactly how you're protecting the company.
This applies just the same if you're a SOC analyst or in a GRC role within your company. You need to reassure the stakeholders that you've got everything under control.
But this is an uphill battle. Your users are creating more data all the time, and with cloud collaboration and sharing, your data security posture is getting worse, not better.
If an employee decides to go rogue and grab sensitive data out of Microsoft 365, how would you know? Or if an attacker compromises a user or system, would you have an audit trail to identify what data was affected?
There are two sides of breach avoidance that are important to consider:
- How can I quickly detect suspicious behavior that could lead to a data breach?
- If the network is compromised (or maybe the bad actor is an insider), how can we limit the damage?
DSPM solutions should help you by using data-activity monitoring to detect a breach early, and also provide access control capabilities that can help you proactively limit the damage a bad actor could do.
Post-breach
Sometimes, it's just too late. When a breach happens, you need to be able to answer a few key questions:
- How did it happen?
- What was stolen?
- How can we prevent it from happening again?
And the last thing you want to hear when you're in the middle of an incident is "I don't know" to any of those questions.
Even the best investigators in the world need the right visibility. The best DSPM solutions will have an audit trail across both cloud and on-prem data to give you the fullest picture of what happened.
Compliance
Another vital reason for using a DSPM tool is to both ensure compliance and prove it.
From GDPR to the SEC, every company has data laws and regulations they must adhere to, and many of those regulations can be broken down into knowing where sensitive data is, limiting who can access it, and monitoring it for threats. Sound familiar?
You're not just answerable to management here, either. Auditors will come in and expect to see you're making progress, and prove you know where all your customer data is.
For example, healthcare organizations have to carry out frequent HIPAA audits, making sure their sensitive data is only accessible to the right people.
Failure to do so can have catastrophic ramifications, with HIPAA penalties reaching as high as $16 million.
Whatever the regulation, DSPM can be a critical component to complying.
Picking the right DSPM solution
Considering the significant impact this could have on your company, it's clear that it's not just important to use a DSPM tool, but it's also vital to choose the right DSPM solution.
There are three dimensions of data your DSPM tool needs to address:
- Sensitivity
- Permissions
- Activity
If any of these are missing, it's hard to make much progress with securing data, and it becomes impossible to automate.
As more DSPM tools pop up, there are several key areas to look at to help you make the right decision.
Coverage
One of the first things you need to consider is where your organization has the highest concentrations of sensitive data and where that data is most exposed. For many organizations, this can be Microsoft 365, AWS, Box, Google Drive, GitHub, etc.
Of course, you'll want to choose a tool that covers your most used platforms.
But it's not quite that simple.
Many DSPM tools stop at the infrastructure storage level (AWS, Azure, Google Cloud Platform), but your data doesn’t stop there. Sensitive data sprawls across SaaS and IaaS storage platforms alike, and the more collaborative the platform, the more likely you are to have sensitive data exposed to risk.
Our philosophy at Varonis is to focus on the platforms where our customers have most of their sensitive data (Google Drive, Microsoft 365, Salesforce, etc.) and provide deep coverage for those specific tools.
Accuracy
Accuracy is also a big factor when you're dealing with alerts.
This might sound obvious, but if a DSPM tool surfaces findings that aren't accurate, it can do more harm than good.
For example, if a DSPM tool audited AWS and reported that a certain bucket held patient records, but on further inspection, you found it didn't, you'd lose trust. And without this trust, you have to spot-check the results, which defeats the point.
If alerts are triggered incorrectly, you'll soon have alert fatigue. Like the boy who cried wolf.
Some DSPM vendors will only offer basic policy-based alerts, which are rife with false positives. Instead, look for a DSPM vendor who can learn and baseline normal behavior and trigger alerts based on abnormal activity.
It’s definitely a bonus if the vendor also offers support for tuning alerts to ensure you’re optimizing the signal-to-noise ratio.
Scale
There's a huge difference between auditing a terabyte of storage at a startup versus auditing Bank of America's six petabytes of data.
This is why scale is such an important factor and can cause a lot of problems if the DSPM tool isn't built for it.
If you're running classification or permission scans on huge amounts of data, it needs to reliably cover everything. But if the scan can't finish for whatever reason, you end up with only half the picture, and half the protection.
Remediation
The point of finding these issues in the first place is to resolve them, so you want a DSPM tool that actually helps you do this.
Built-in remediation means issues can be resolved at the push of a button, or sometimes even without any action at all. Unfortunately, many DSPM tools only provide you with remediation workflows that require you to manually resolve the issue yourself, rather than fix it for you.
You don’t want your DSPM solution to just surface findings — you want them to be able to fix the problems they find, too.
A data-first approach with Varonis
Our philosophy at Varonis is not to just churn out a list of issues, filling you with findings fatigue — rather, our goal is to surface meaningful, detailed alerts that you can act on and even automatically remediate with Varonis.
Even if you haven't logged in, Varonis will still find and solve data security issues.
Real-time visibility
It's important to see the status of your data, as it is at the moment you're looking.
This not only keeps you up to date, but also means you can be proactive in addressing and fixing risk.
We deliver this with several features and functions.
Continuous data discovery
Varonis is constantly scanning your data, stored both on-premise and in the cloud, even surfacing instances that you may not know you had.
You can then view the results of these scans on real-time dashboards, showing discovery insights, concentrations of sensitive data, and where that data is exposed.
This gives you a clear view of all the key information at a glance, so it’s easy to digest the insights and prioritize risk reduction.
Automated data classification
A key part of staying compliant is being able to see exactly what sensitive data is stored and where.
Our automatic data classification has a built-in library of rules, and more than 700 patterns, so you can accurately classify your data and drastically reduce false positives.
This includes all common regulations and standards like GDPR, SOX, PCI, and HIPAA.
On-demand compliance reports help you track compliance with relevant regulations and can be given straight to auditors and compliance teams.
One-click analysis
Using our real-time file analysis, it just takes one click to see what sensitive data is in a certain file and confirm the results.
To make it easier to view, the sensitive data is highlighted, and color-coded to match the different categories of sensitive data (PII, GDPR, etc.)
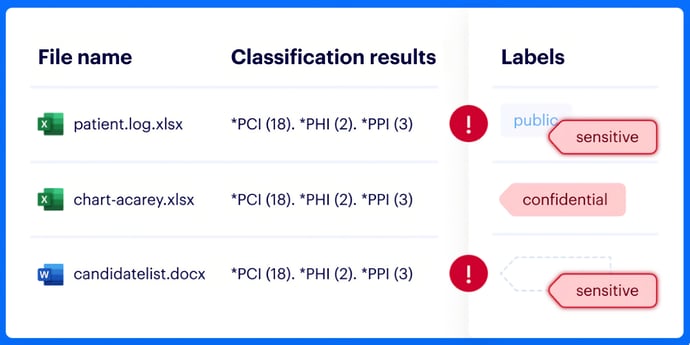
Sensitivity labels
Instead of manually labeling data yourself, you just need to create policies, and we'll label it for you.
If a policy changes, files that no longer match the policy will be automatically relabeled.
Varonis also compares existing labels with our classification results, so you can identify misclassified data.
Simplify permissions management.
In addition to getting a good view of your data, it's also important to look at who can access what data.
We map permissions across your data stores and normalize them into a simplified permissions model, making it quick to understand data access without having to be an expert on how each platform’s permissions work.
We pair classification results with permissions to identify stale permissions and where data is exposed org-wide, externally, and publicly.
Reduce your blast radius.
When we talk about reducing the blast radius, the focus is on correlating people with permissions and activity to identify where sensitive data is overexposed and at risk. That way, you can proactively make informed decisions that limit who can access sensitive data.
Varonis analyzes data access and activity across your business, and can automatically remove excessive, external, public, and stale permissions without interrupting business.
You can either use the ready-made policies Varonis gives you or personalize them for your organization.
Sensitivity, location, link type, and staleness are just a few factors you can use to build your rules. And once you’re done, Varonis automatically and continuously enforces your new rules, keeping your data as secure as possible.
Least privilege automation
As we mentioned before, a DSPM isn't particularly useful unless it helps you resolve the issues. This is where our autonomous remediation comes in.
Least privilege automation automatically analyzes data access across your business, and intelligently decides who needs access to what data.
This continuously reduces your blast radius without any human input, and with no risk to the business.
Threat detection and response
Our behavioral-based threat models are refined using large datasets, which means they are accurate and improve over time as we analyze more data.
We baseline standard user behavior, enabling us to detect abnormal behavior and deploy automated responses to stop threats before they take hold.
Audit trail of events
It can be overwhelming trying to keep on top of everything. We make this easier by aggregating, normalizing, and enriching your events.
Our searchable data activity log makes it easy to investigate incidents, whether by your team or ours.
You can search files, folders, emails, and objects, and see everything that's been created, updated, uploaded, or deleted.
The events are enriched with helpful contexts like device name, geolocation, etc., to make it even simpler and help you make better decisions.
Incident response team
Our team proactively monitors your alerts, so we can help you as soon as something comes up and work with you to immediately investigate and respond. We watch your data, so you don’t have to.
Posture management
We proactively surface and alert to misconfigurations that could expose sensitive data to risk. The Varonis posture management dashboard provides a concise explanation of what risk each misconfiguration poses and enables you to remediate the security gap right from the Varonis UI to strengthen your data security posture.
Third-party app risk management
With Varonis, security teams can easily discover all the third-party apps connected to their corporate SaaS platforms and gain a clear view of the risks they pose.
We help you better understand each app's blast radius, monitor app activity, and reduce the attack surface by removing unsanctioned or unused app connections — right from a single console.
Connect cross-cloud identities and close off-boarding gaps.
Automatically link user accounts, including personal accounts, across all your services into a single identity. Use these insights to safely offboard stale users and ex-contractors who no longer need access to your corporate cloud environments.
Uncover high-risk, over-privileged shadow identities (human and non-human) that may put your sensitive data at risk and begin removing them from your environment.
DSPM dashboards
By combining your classification results, permissions, and user access activity, we give you a comprehensive and centralized view of your data with out-of-the-box and customizable dashboards.
The Varonis DSPM dashboards can serve as your organization's real-time view of data risk. Use these dashboards to continuously visualize and assess your security posture and track progress over time.
See where there are unnecessary pathways to data and monitor changes to risk over time so you can reduce threats to your sensitive data as your environments evolve.
Read more:
In closing
For any organization prioritizing data security, DSPM is a concept to pay attention to.
Picking the right DSPM solution can prevent breaches, help you investigate incidents quickly, and ensure you're meeting increasingly stringent regulations. By focusing on coverage, accuracy, and scale, you can get a good idea of which DSPM tools are a good fit for your company.
We are confident that our DSPM features are the best in the market, and deliver true value across four areas:
- Real-time visibility
- Simplify compliance
- Reducing the blast radius
- Threat detection and response
Curious to learn more? Explore the DSPM features built into our Data Security Platform today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.





-1.png)



