Amazon Web Services (AWS) is one of the world's most comprehensive and broadly adopted cloud platforms. Organizations rely on AWS to host their cloud infrastructure and Simple Storage Service (S3) to house swaths of sensitive and critical data.
With so many options for identity management, permission levels, and access controls, AWS environments and the data within can be extremely difficult to secure at scale — even with Amazon's built-in security capabilities.
That's where Varonis for AWS comes in. As an AWS partner, we augment AWS' native security and provide a single pane of glass for securing AWS S3, EC2, and IAM, plus your broader SaaS and IaaS ecosystems.
With Varonis for AWS, you can see where sensitive data is stored in your S3 buckets, where that data is overexposed (either through excessive permissions/sharing or by a misconfiguration), and whether it's at risk.
The latest release of our platform brings exciting features, including the ability to:
- Discover and classify sensitive data stored in S3 buckets:
Automatically discover where sensitive and regulated data exists in your AWS S3 buckets. - Prevent data exposure in AWS:
Easily see where sensitive data is exposed to too many users — including external users — and effectively limit excessive access. - Pinpoint AWS misconfigurations:
Detect org-wide settings issues and spot vulnerabilities that put your organization at risk. - Detect and investigate threats in AWS and across the cloud ecosystem:
Get alerts on suspicious user behavior such as excessive bucket deletions or MFA deactivation.
Read on to learn more about how each of these features can help you secure AWS at scale.
Get a Free Data Risk Assessment
Classify sensitive data stored in S3 buckets.
With this new release, we're bringing Varonis' battle-tested classification engine and highly accurate results to your S3 buckets.
Varonis makes it easy to understand where your sensitive data exists within S3 by breaking down the contents of your buckets into an easy-to-navigate file tree. We show you exactly which buckets belong to which user, what kind of sensitive data is inside, and how much sensitive data is in each bucket.
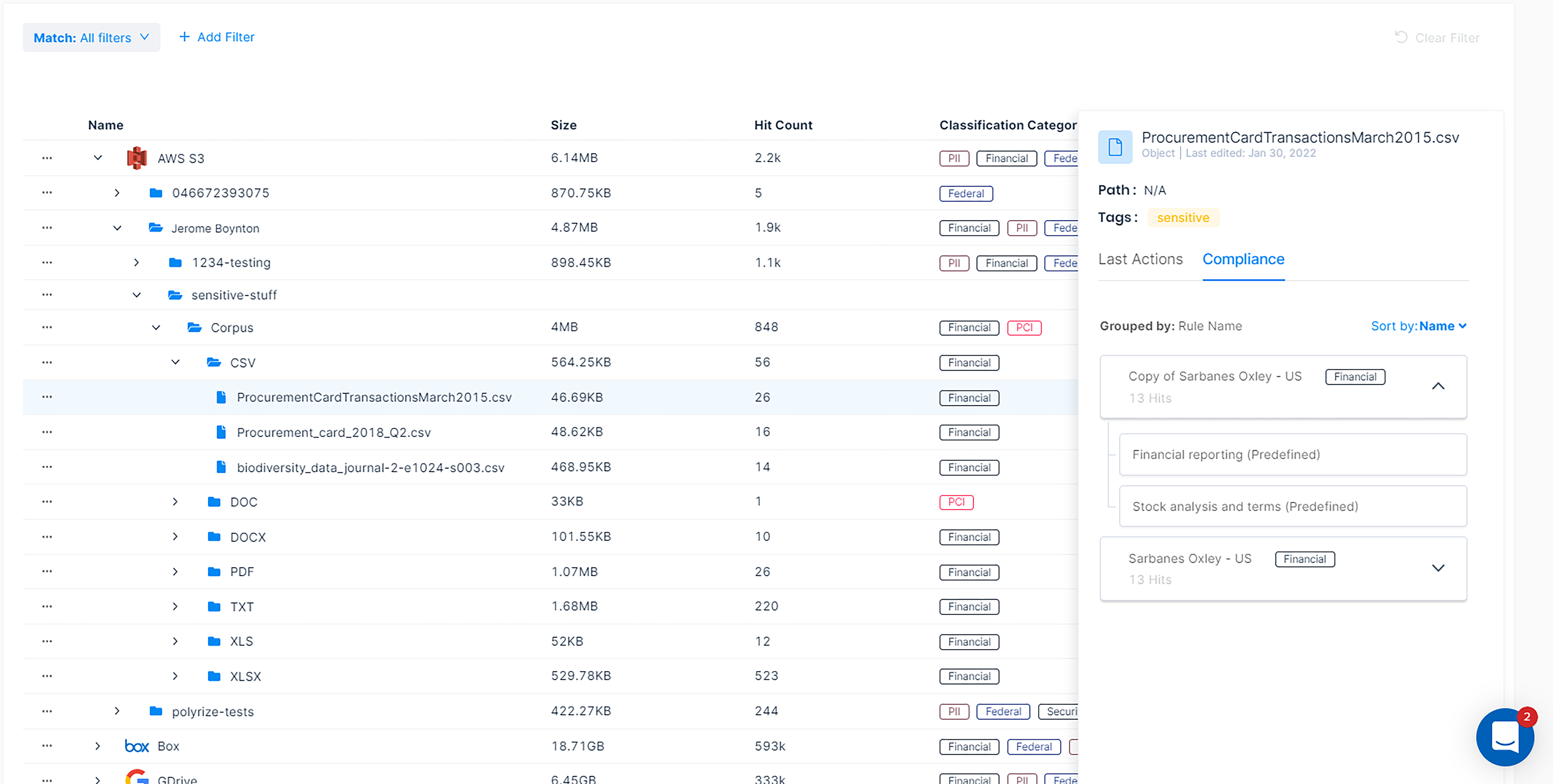 S3 bucket file tree view and classification results
S3 bucket file tree view and classification results
Varonis' classification goes beyond regular expressions and includes pre-built databases of known valid values, proximity-matching, negative keywords, and an algorithmic verification to generate accurate results. You can see not only that there is financial data in a file, for example, but also what kind of financial data.
In addition to a large pattern library that spans multiple regulations such as, GDPR, SOX, HIPAA, PCI-DSS, GLBA, and CCPA (to name a few), we also have the correlated, built-in policies that take the guesswork out of piecing each identifier together.
You can even dive into a specific file to determine exactly where we see sensitive data. We fetch the contents of the file with a click of a button, highlight classification results with easy-to-see color coding and filtering, and then shred the contents of the file after you've had a chance to inspect the results.
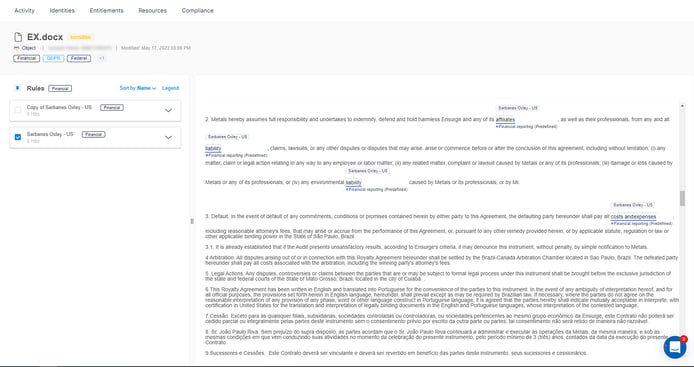 See exactly where sensitive data lives in your S3 buckets.
See exactly where sensitive data lives in your S3 buckets.
Configure your classification scope.
S3 buckets can be massive — and they can grow at unpredictable rates. Varonis now enables you to control the scope of what you want to classify for even speedier results and lower processing loads.
You can limit your scans based on:
- Certain buckets
- Certain objects
- Certain regions
- File type
- File size
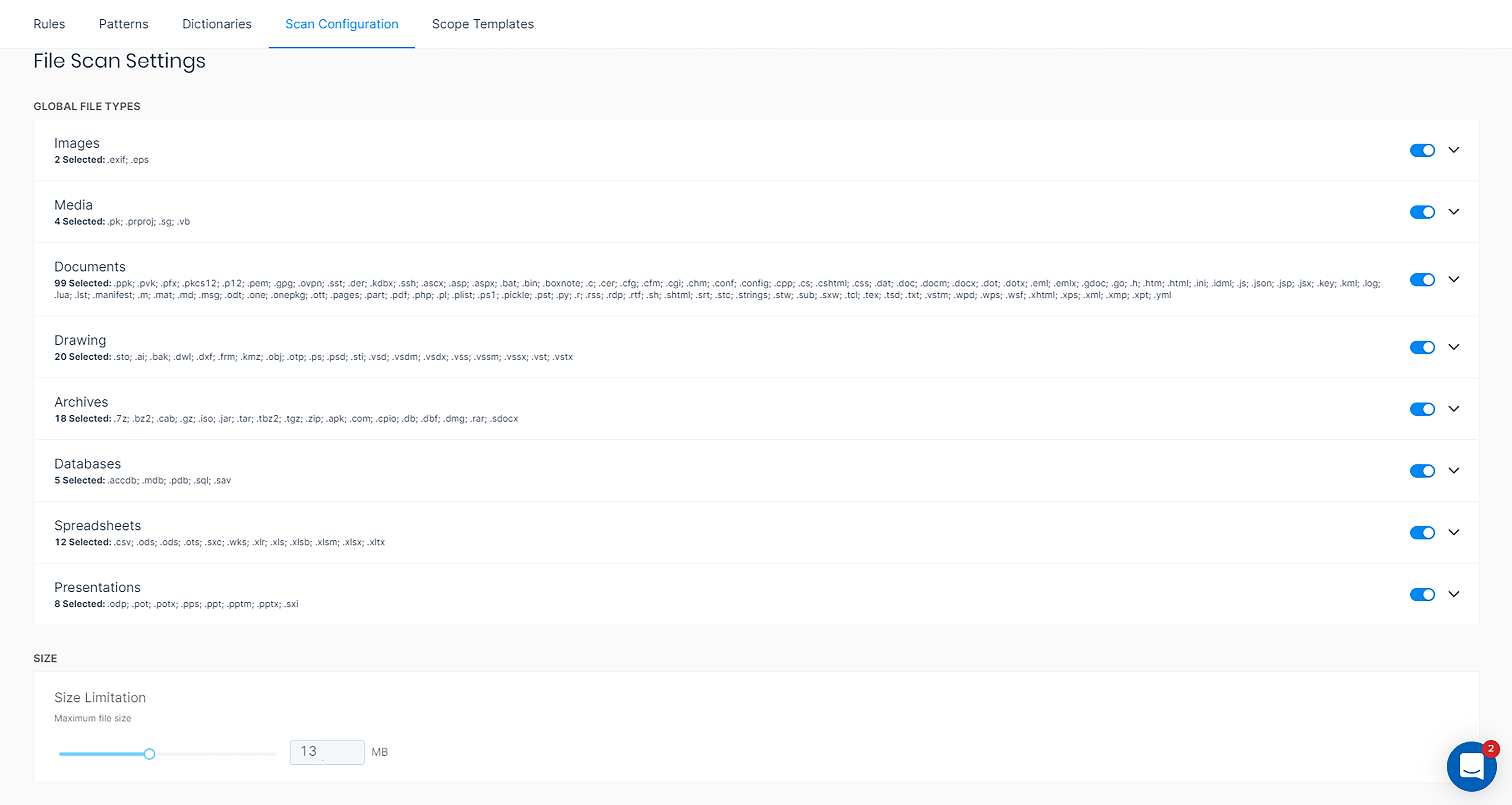 Configure your classification scope by file type or size.
Configure your classification scope by file type or size.
Varonis vs. Amazon Macie
AWS' built-in classification tool, Amazon Macie, can be a great classification tool, but depending on your use-case it may not be enough. Amazon Macie is exclusive to classifying data in AWS S3 and does not extend to additional cloud services like Google Workspace, Box, or Salesforce. If you are in need of classification for any of those other platforms, you would need another classification tool.
With Macie alone, it can be difficult to understand where buckets are overexposed — the software can identify if a bucket has been publicly exposed, but to understand exactly who has access to a bucket and what they can do, you would need to spend time cross-correlating with accounts and roles in AWS IAM.
Varonis makes it simple to understand who has access to your sensitive data across your cloud ecosystem. With a simple click of a button, you can visualize where sensitive data is concentrated in your S3 buckets, who has access, and what they are doing with this data.
Prevent data exposure in AWS.
AWS provides admins the ability to manage roles and control access through Access Control Lists (ACL) and Role-Based Access Controls (RBAC). But with several roles and permissions sets, configuring data access can become incredibly complex, making it difficult to spot excessive data access.
Varonis takes the manual work out of identifying who has access to your critical AWS data and what their net effective permissions are. Quickly discover externally shared and publicly exposed AWS buckets or EC2 instances without having to manually sift through countless users, roles, groups, and policies.
Effective permissions
Varonis automatically maps access to your AWS data and normalizes permissions across all your supported SaaS and IaaS platforms into a simple CRUDS (create, read, update, delete, and share) model, providing a real-time view into effective permissions — including those granted to external users.
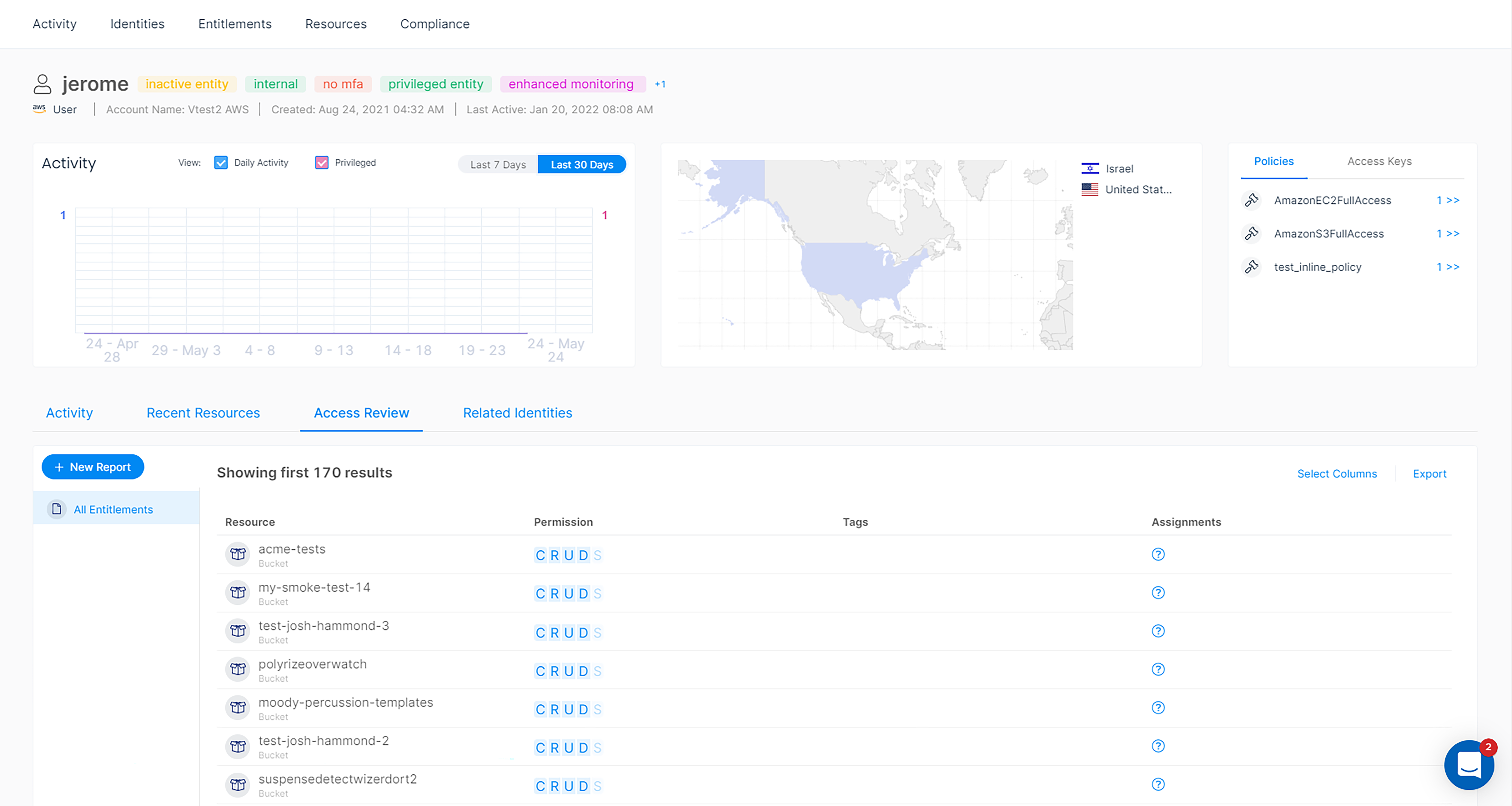 Easily see everything a user can access in AWS.
Easily see everything a user can access in AWS.
With a bi-directional view of permissions, a simple click of a button allows you to see not only see all the data a single user has access to, but also view who can access an individual bucket.
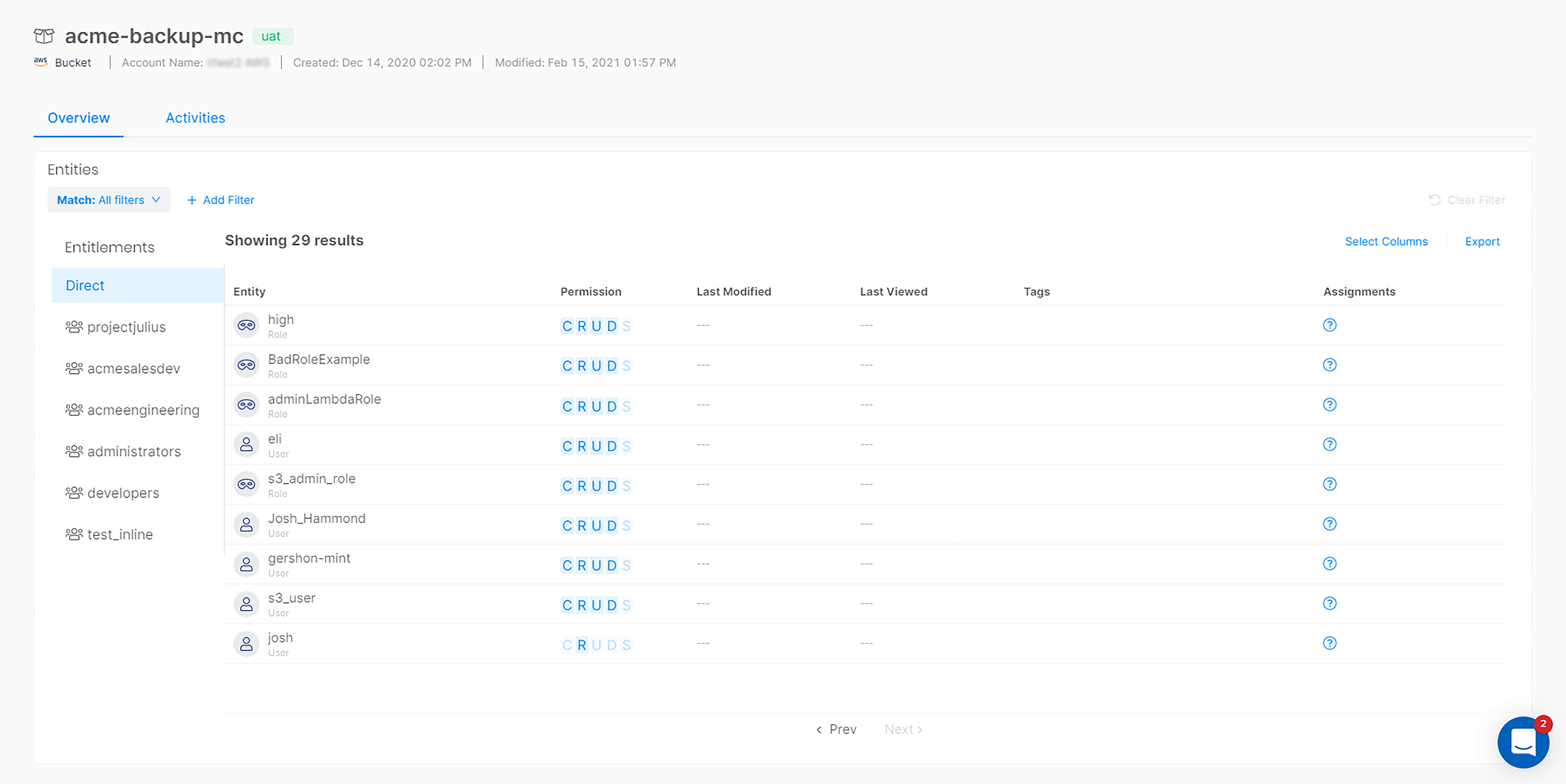 View all user and entity permissions for each S3 bucket.
View all user and entity permissions for each S3 bucket.
Unauthorized access to data
When someone leaves the company, you want to make sure they can no longer access your corporate data. Shockingly, three out of four ex-contractors can still access sensitive data after they've left the company. Varonis ties identities together across platforms to help you easily spot offboarding gaps, unsanctioned personal account use, or other compliance violations.
 Varonis ties related identities together automatically.
Varonis ties related identities together automatically.
Pinpoint misconfigurations.
Excessive permissions are a major way sensitive data can end up exposed, but a single system-wide misconfiguration can also put your AWS environment at risk.
From admins missing MFA, to S3 buckets without an audit trail, Varonis highlights these misconfigurations in our security posture management Insights Dashboard. Our dashboard provides recommendations on how to quickly fix these misconfigurations and improve your security posture.
 The Insights Dashboard highlights misconfigurations that can put AWS at risk.
The Insights Dashboard highlights misconfigurations that can put AWS at risk.
The Insights Dashboard includes findings from our elite cybersecurity research team. Any time the team finds a new potential configuration risk, Varonis can scan your environment and alert you if we think you're exposed.
Detect and investigate threats in AWS.
Knowing where you have sensitive data and who can access it is a critical first step in securing your cloud environment. But to detect threats, you need to monitor what users are doing with that data.
Spot abnormal activity in AWS.
Varonis closely monitors resource and data activity in S3, IAM, and EC2. Through our many out-of-the-box alerting policies or custom ones you design, you'll be notified of any suspicious or malicious behavior in AWS and your broader SaaS environment.
This includes unauthorized data access, risky sharing behavior, S3 buckets becoming public, stale contractor accounts becoming active again, and other activity that could put your data at risk of compromise.
 The Alerts Dashboard shows risky activity happening across your SaaS ecosystem.
The Alerts Dashboard shows risky activity happening across your SaaS ecosystem.
Unmask assumed roles.
The use of assumed roles has become a very popular practice in AWS. Admins can grant users access to these roles to give them temporary elevated permissions. Unfortunately, these roles can also be used by nefarious actors to mask their activity in AWS. When investigating a temporary admin’s actions in AWS without Varonis, you will only see the role in the AWS audit trail, not the name of the person or entity tied to it.
A “trusted” insider or an external threat using a sophisticated social engineering campaign can convince an admin to provide them access to one of these roles — which can be used to gain elevated permissions, mask their account, and hide amongst the other assumed roles in AWS to carry out attacks. This can make investigations very difficult.
Varonis can link these temporarily assumed roles to the assigned users and entities, helping you see who is behind these actions in AWS.
 See the user behind the temporary role and their actions.
See the user behind the temporary role and their actions.
Investigate alerts across your SaaS ecosystem.
From an alert, it's easy to dive into a cross-cloud investigation. You can drill down into that user's activity both in AWS and across SaaS apps to see what data was touched.
Varonis provides a complete, human-readable audit trail of data activity. With this, investigators can easily identify the actions taken on their different AWS services, by whom, and when — along with a host of other information that you will find useful in an investigation, such as IP address, country, and action type.
 Cross-cloud audit trail of events
Cross-cloud audit trail of events
Strengthen your AWS security with Varonis.
Varonis for AWS gives you a critical layer of protection over AWS, S3, and your broader SaaS environment. Easily find sensitive data, uncover who can access it and where it could be exposed, and monitor that data for suspicious activity and potential threats.
If you're interested in trying out DatAdvantage Cloud for AWS yourself, sign up for a complimentary Data Risk Assessment with our cloud experts to see where your SaaS and IaaS environments and data could be exposed.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.