California is the first state to introduce data privacy protection regulations on par with the EU’s General Data Protection Regulation (GDPR). As one of the first pieces of digital consumer data privacy legislation in the country, the California Consumer Privacy Act (CCPA) provides strong individual rights and protections around data access and collection. Read on to learn more about what CCPA entails and how to achieve compliance in a step-by-step fashion.
When Does the Legislation Go Into Effect?
The CCPA law is designed to protect the data privacy rights of citizens living in California. It forces companies to provide additional information to consumers around how their data is being collected, stored, and used. The goal is to give consumers more transparency and control over their private data.
Citizens will now have more visibility into whether or not their data is being shared with — or sold to — third parties. The CCPA also empowers consumers with the right to opt-out of any data usage or activities they disapprove of. The CCPA was originally approved by Governor Jerry Brown in June of 2018 and took effect on schedule on January 1st of 2020.
Get the Free Essential Guide to US Data Protection Compliance and Regulations
Who Does the CCPA Affect?
The CCPA covers business — defined as a for-profit legal entity — that collects and sells the personal information of consumers. Per CCPA, the regulation applies to businesses that meet any one of the following criteria:
- Has an annual gross revenue of over $25 million
- Gathers, buys, sells, or receives the personal information of over 50,000 California residents, households, or devices
- Derives more than 50% of annual revenue from selling the personal information of California residents
Moreover, California lawmakers included language to exempt businesses that are already subject to robust federal data protection regulations. These types of companies include:
- Health providers and insurers already subject to HIPAA
- Banks and financial companies covered by Gramm-Leach-Bliley
- Credit reporting agencies, such as Equifax and TransUnion, that are under the Fair Credit Reporting Act
Why do we have the California Consumer Privacy Act?
While companies previously were forced to take steps to safeguard customer data, entities weren’t held responsible for what they did with it and with whom they shared information. With consumers now able to have greater visibility into how their data is being used — and the ability to control and access that data — the CCPA represents a giant step forward in personal data privacy.
With CCPA, legislators wanted to leave no doubt that personal data belonged strictly to the consumer. The types of data where consumers now have control over the collection, usage, and sharing of include:
- Credit and debit card numbers
- Legal names
- Postal addresses
- Social security numbers
- Demographic information
- Income and financial data
- Browsing and search history
- Age and date of birth
- Political and religious affiliation
- Education information
- Unique online account names
- Drivers license and passport
- Geolocation and biometric data
- Any other uniquely identifiable information
What are the CCPA Requirements?
The CCPA outlines specific requirements for companies that correlate with consumer rights over their personal data. These core requirements are as follows:
- Right to Disclosure. If you collect information about a consumer protected by the CCPA, then you must inform the consumer of your intentions at or before the point of data collection.
- Right to Access. Consumers have the right to request you provide them with the information in a readily usable format. This must be free of charge and provided within 45 days from the request. Individuals must also have clear and easy access to your full privacy policy.
- Right to Contact Information. You’re required to inform consumers where they can find more information about your privacy policy and CCPA compliance efforts. You also need to provide a toll-free telephone number and online contact details should they decide to contact you to exercise any CCPA-related rights.
- Right to be Forgotten. If a consumer requests that you delete any personal data and information, you’re legally mandated to do so under the CCPA. There are very narrow exceptions in cases where you need the information to fulfill some form of superseding legal obligation.
- Opt-out of Data Sales and Marketing. If you do sell visitors’ personal information, you must give consumers the opportunity to opt-out of this transaction. You’re required to have a web page that clearly presents an opt-out option, preferably with a link to your privacy policy page. They must also be able to opt-out of data usage for future marketing efforts.
- Right to Fair Treatment. In no way, shape, or form can you discriminate or treat users differently based on whether or not they exercise their CCPA rights. You must provide the same level of access and service to all consumers regardless of which rights they exercise.
- Periodic Privacy Policy Updates. You must update your privacy policy every 12 months. That way, customers know if you’re now collecting, selling, processing, or otherwise handling data differently than before. Or if you’re gathering more information than previously stated.
These requirements represent the basis of successful CCPA compliance. Now, you’re ready to put this knowledge into action by learning exactly how to begin your CCPA compliance journey.
Step-by-Step Guide to CCPA Compliance
Follow the six steps below to learn how to become CCPA compliant.
Step 1: Update Privacy Policy and Notices
The first thing you’ll need to do is review your current privacy policy, conduct a CCPA gap assessment, and update the policy where needed. Your new privacy policy should address all of the new rights as outlined above under the CCPA, and your procedures for granting said rights under various circumstances. Your privacy notices to consumers also need to be updated, informing them in more detail at the point of data collection about how their data can and will be used.
Step 2: Maintain a Sound Data Inventory
You’ll also need to maintain a data inventory, which is essentially a database that tracks all information processing activities. This includes various business processes, products, devices, and software that handles consumer data at any given time. Your CCPA data classification should identify which data types are sold, shared with third parties, or used for marketing purposes. Any rights requests for specific data types should also be recorded in the data inventory as proof that you’re CCPA compliant.
Step 3: Implement Data Rights Protocols
The new consumer data rights set forth by CCPA should be central to your compliance efforts. Therefore, you need processes and protocols in place if and when consumers decide to exercise any of those rights. If a consumer contacts you to utilize their Right to Be Forgotten, for instance, your IT team should know exactly where that data is housed and already have a streamlined process in place to dispose of the data and notify the consumer in a CCPA-compliant way. Have protocols at the ready so that when consumers exercise their rights, the process is efficient and fully compliant.
Step 4: Fortify Your Cybersecurity Stack
Under the CCPA, all covered businesses are required to protect personal data with “reasonable” security measures. While this might seem like vague, legal language, in practice it typically means taking a risk-based approach to cybersecurity. You’ll want to assess the risks to your various data types, rank them in terms of most vulnerable to least, and beef up systems and technology where the risk is greatest. While the cost of implementing a new security and privacy platform for high-risk data can be high, if there’s a breach and you’re found to have not taken reasonable measures, the fines and penalties may far exceed the upgrade costs.
Step 5: Audit Third-Party Processor Agreements
If you work with other companies to process, store or transmit consumer data, you’ll need to audit and update those contracts to become CCPA compliant. This is where working with an experienced CCPA compliance partner can be extremely useful in helping you insert standard contractual language into your partnership agreements with minimal legal headache. Your contracts should cover all the bases with regards to CCOA compliance, from how your third parties process data to how they’ll work with you during data rights requests.
Step 6: Ongoing Internal Data Privacy Training
The CCPA mandates that you ensure all individuals who are involved with the handling of consumer data — especially those who process data rights requests — undergo training in how to do so safely and securely. While CCPA leaves it somewhat open-ended in terms of the “how,” typical training mechanisms can include on-site classroom sessions, live virtual training, or standardized courses with materials and testing. While the CCPA doesn’t specifically state how often training should take place, it’s recommended that you conduct refreshers on an annual basis at minimum.
CCPA Compliance Checklist
CCPA compliance doesn’t have to be a stressful, all-consuming effort within your organization. Here are a few tips and action items that you can take along with ways to ensure you’re CCPA compliant now, and well into the future.
1. Preparation
- Identify and classify your data assets
- Understand new consumer rights
- Conduct a data risk assessment
- Scour systems for hidden data
2. Implementation
- Update your data privacy policy
- Implement rights response processes
- Adjust permission and access controls
- Upgrade critical systems and software
3. Maintenance
- Review your privacy policy annually
- Conduct regular CCPA training
- Eliminate unnecessary data regularly
- Streamline rights response processes
How is Compliance Enforced?
The California Attorney General has the ultimate authority to enforce CCPA. Fines for non-compliance depend on the offense and various other factors. The CCPA provides for a “private right of action” in instances where there’s theft or disclosure of non-encrypted or non-redacted personal information.
Real World CCPA Penalties
Civil penalties start at $2,500 per violation for non-compliance that is deemed unintentional. For intentional non-compliance, those fines jump to as much as $7,500 per violation. There’s also the time frame in which the business responds. The CCPA states that if a company can “cure” the non-compliance within 30 days of being notified of the offense, they get off with a warning. If they can’t remedy the situation within the 30-day window, they’re back on the hook and once again subject to fines.
Data breaches are a separate matter, giving affected consumers the right to take specific action against the offending company. Consumers can bring an action for statutory damages in the event of a data breach caused by the organization’s failure to implement reasonable security procedures.
A Closer Look at Data Security in the CCPA and NIST CIS Framework
There are obvious parallels between the CCPA and the EU GDPR. A law firm has mercifully put together this chart comparing the two. One of the key differences between the CCPA and the GDPR is that the EU law has very strong data security requirements. The GDPR contains both data privacy and security rules. That is not the case with the CCPA, which is focused on consumer privacy.
Over the last few months, there have been a few amendments kicking around Sacramento. One that caught my attention, AB-1035, adds very specific language about data security.

NIST CIS framework makes an appearance in the CCPA. It was, sigh, subsequently removed.
AB-1035 takes on the challenge of defining the well-known boilerplate phrase “reasonable security”, which is often found in state data breach laws but typically with no explanation attached to it meaning. This amendment boldly proposes the NIST Framework for Improving Critical Infrastructure Cybersecurity (CIS) and another NIST standard 800-171, which is a trimmed-down version of the encyclopedic 800-53, as a potential baseline security standard for the state.
This is a big deal: not even the EU GDPR explicitly refers to outside data standards. Alas this amendment proved to be too radical for California: the CCPA was finalized on September 13, and the bill doesn’t include this particular amendment. Oh well.
Let’s give California credit for considering the CIS Framework. In case you’ve forgotten, a framework is not the same as a security standard. Instead, it’s a kind of meta-standard, which provides a list of meta-security controls that map into real security controls within existing data standards.
The CIS Framework supports mappings into, not surprisingly, NIST 800.53, and the other usual suspects, including COBIT 5, SANS CCS, ISO 270001, and ISA 62443. You can see part of the mapping below:
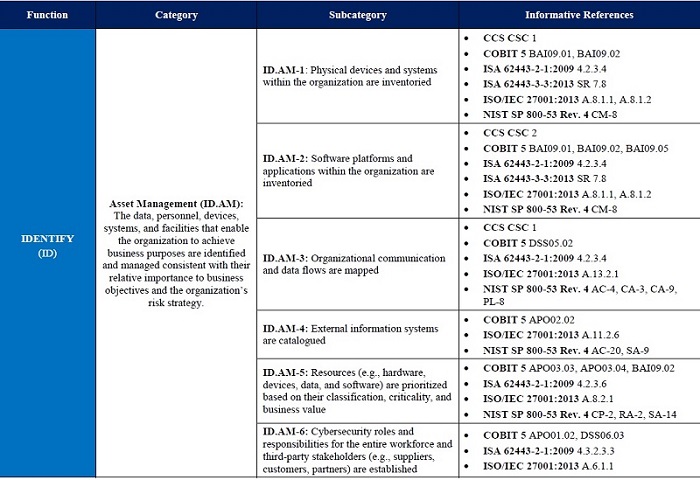
Amazing! NIST CIS Framework maps its security controls into many different standards. You may already be NIST compliant!
The big idea behind the NIST CIS Framework is that companies that are already following existing data security standards can continue to do so. They simply examine the parts of CIS they’ve covered, and then fill in shortfalls as needed. The CIS Framework as a legal basis for compliance makes good sense since it doesn’t penalize companies for having data security programs already in place!
The Future of Data Privacy and Security: CCPA’s Legacy
The CCPA is already making waves. With Washington still not providing leadership at the federal level, it’s not surprising that other states have taken a cue from California and drafted their own privacy laws. There are already several CCPA copycat laws from New York, Massachusetts, Maryland, North Dakota, and other states. And if you look at a recent proposal from US executives for a federal privacy law, it bears more than a passing resemblance to the CCPA.
Change is coming, whether from your own state or eventually at the federal level. Companies should play it smart, by aligning their data security and privacy practices with the CCPA. Specifically, they should have programs and technologies to classify personal data, protect it, and then constantly monitor and analyze for threats.
How does Varonis help with the CCPA?
We at Varonis have a history helping companies comply with various data security laws and compliance standards (PCI DSS and many others). You can read more about how we help in this fascinating series of blog posts on this very subject.
But here’s a quick tour of the Varonis approach to compliance. DatAdvantage reports can help IT staff spot and index folders containing sensitive CCPA data. Digging deeper with DatAdvantage, they can find those folders that have broad permissions – say “Everyone” access. DatAdvantage reports also can help IT groups track who’s accessing the files containing CCPA data.
They can then can move to the next phase and use DatAdvantage to work out the actual data owners of the folders — those who are the business users best suited to know who is authorized and who should be dropped. DatAdvantage can help in this process through automated recommendations for group ownership, and can also automatically adjust access rights. DataPrivilege then keeps the data owners in the loop by directing future access requests from users directly to the better-informed owners.
DatAlert is our always-on monitoring software that detects and alerts IT, staff when there are signs of unauthorized access, malware usage, or other unusual activities. With IT alerted, they can respond to a potential attack and take appropriate actions — deactivate accounts, quarantine files, etc.
Finally, to handle a CCPA consumer request for data, DatAnswers can quickly find personal data and then allow the company to quarantine or delete the information.
CCPA Compliance FAQs
What’s the difference between GDPR and CCPA?
While the CCPA is similar to the GDPR, it’s not exactly the same. If you’re already prepared for the GDPR, you may be able to leverage some of the work that you did to meet your CCPA requirements.
Does the CCPA apply to any specific industries?
The CCPA isn’t geared towards any industry or company type in particular. Any company that meets the criteria outlined by CCPA is subject to the regulation. However, companies that conduct extensive digital marketing activities will need to focus on CCPA more thoroughly.
Can I achieve CCPA compliance on my own?
Yes. Nowhere in the CCPA does it state that certification by a third-party is required for compliance. However, many companies do choose to work with an experienced CCPA compliance partner to streamline the process.
What does the CCPA define as Sale of Data?
Under the CCPA, the term “sale” has a broad definition ranging from actually selling or renting personal information to even disclosing, disseminating, and making personal data available to a third-party for monetary compensation.
What happens if my company is not in compliance with the CCPA?
The California Attorney General may levy fines and penalties if you’re found to be in non-compliance at any time, especially after a data breach. You also may be subject to civil litigation from affected consumers.
What data does the CCPA cover?
The CCPA covers a variety of forms of personally identifiable data as outlined earlier. This includes things like demographic data, financial history, social security, driver’s license numbers, and any other information that can be used to identify an individual.
The CCPA is the first of its kind in the United States, provides consumers with additional rights and ultimate control over their personal data. If you’re just getting started with CCPA compliance, you should also consider an end-to-end CCPA compliance platform to help organize your data and streamline your efforts. An ounce of prevention is worth a pound of cure, so making sure you’re CCPA compliant year-round will help you avoid any unnecessary fines, penalties, or headaches.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.



-1.png)