Ensure compliance with regulatory requirements through effective discovery, activity auditing, automated remediation, and on-demand reporting.
- Comprehensive
- Automated
- Secure



Partner with the leader in data security.
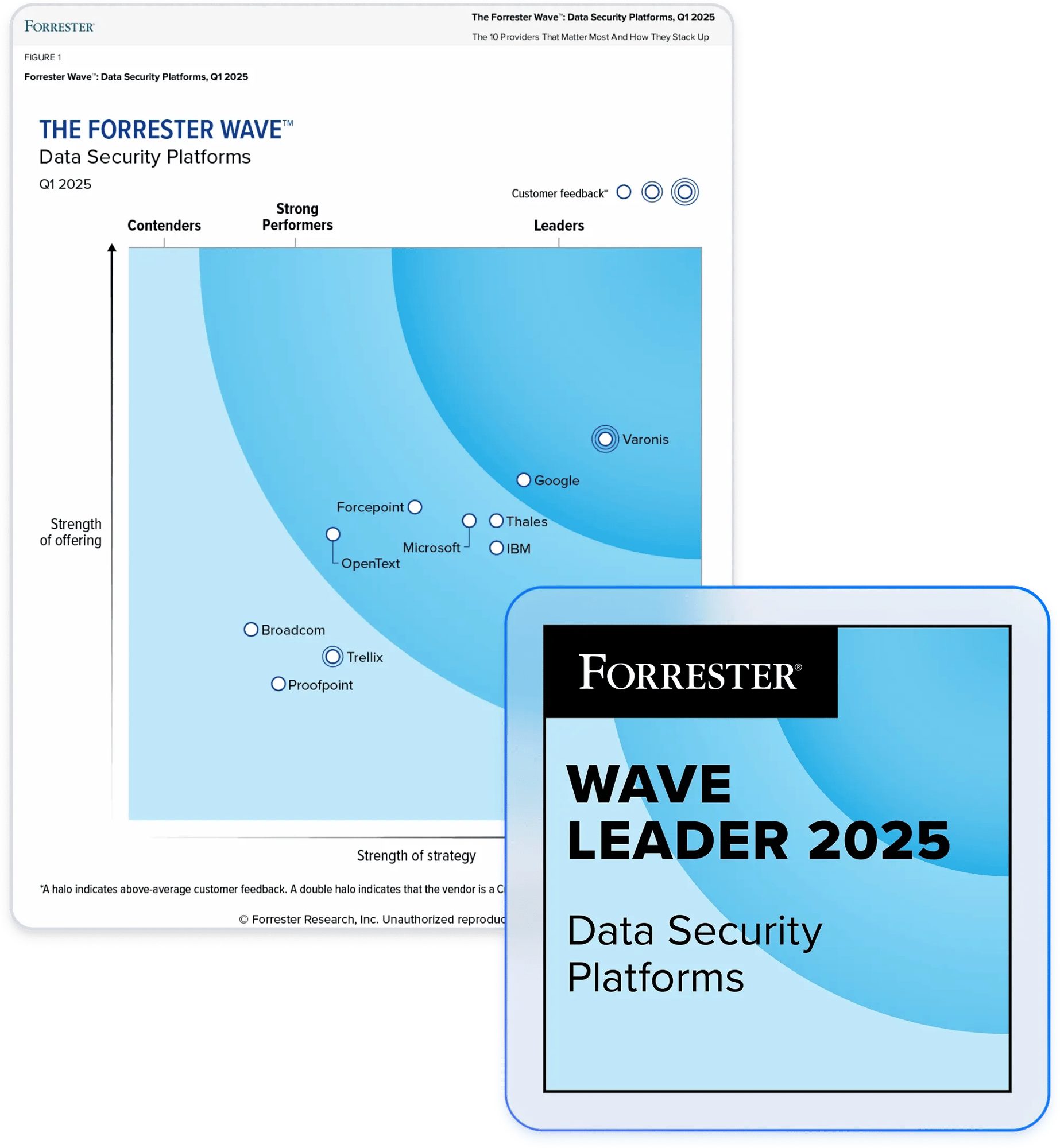
Complex data privacy laws? No longer a problem.
Easy and accurate classification
- Automatic discovery and classification of regulated data
- Pre-built classification policies for NIST, HIPAA, SOX and GDPR
- Cloud and on-prem coverage
Automated remediation
- Remove excessive permissions
- Fix risky misconfigurations
- Apply labels and enforce DLP policies
Award-winning threat detection
- Alert on abnormal behavior
- Automate threat response
- Get 24x7x365 MDDR coverage
“TPMG’s shareholders are an exceptional group of doctors. They all assume full risk. So even though their focus is on medicine, surgery, and the health of patients, they want to know what data we have that we need to protect."
Brett Brickey
CIO, TPMG
Read case studyCompliance simplified
Adhering to intricate regulatory frameworks can be daunting. Manual methods simply can’t keep up with the growing complexity and scale of data access management. Varonis simplifies compliance management and gives real-time visibility and control over your critical data.

Data discovery and classification
Automatically discover and classify regulated data both in the cloud and on-prem with pre-built, accurate classification policies, specific to regulations such as NIST, HIPAA, SOX, and GDPR.

Least privilege automation
Effortlessly eliminate data exposure and ensure privacy-by-design. Varonis makes intelligent decisions about who needs access to data and who doesn’t – continually reducing your blast radius without human intervention and without breaking the business, all without you even needing to log in.

Data activity auditing and searchable forensics
Varonis maps the flow of sensitive data with a searchable log of enriched data activity. Every create, read, update, delete, upload, download, and share action (with who, what, when, and where details) for files, folders, emails, and objects – accelerating cross-platform security investigations for cloud and on-prem environments and assisting with data breach reporting.

Compliance dashboards and reports
Live risk dashboards and on-demand compliance reports give auditors and compliance teams real-time awareness of exposure, usage, ownership, and staleness.

Data-centric UEBA
Varonis’ behavioral-based threat models detect abnormal data activity in real time – stopping threats to data before they become breaches. Our UEBA improves over time as it learns and adapts to customers’ data and ensures comprehensive ransomware protection and insider threat detection.
Our customers have spoken
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Additional Compliance resources
Go beyond Compliance Management.
Varonis tackles hundreds of use cases, making it the ultimate platform to prevent data breaches and ensure compliance.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital