AWS is built for scale and speed, but for security teams, that can mean complexity. Role- and resource-based policies allow entities to assume access easily, but as quickly as entities assume new roles, old ACLs get left behind or Public Access Blocks get left off.
To understand and mitigate the risk of this complexity in the cloud, security teams need to be able to both visualize and fix these risks at scale.
Map your AWS data access “blast radius”
AWS permissions rarely exist in isolation. They form a network of relationships between identities, roles, policies, and resources. Visualization helps teams interpret this network by turning abstract permission chains into something tangible and reviewable.
Instead of combing through individual policies, teams can view access pathways as connected nodes and edges. This perspective makes it easier to spot how a single identity could reach sensitive data, where lateral movement is possible, and which relationships quietly expand AWS exposure. When the full picture is visible, reducing blast radius becomes a targeted and informed process rather than guesswork.
How visualization helps to limit AWS exposure
Visualization becomes truly valuable when it enables security teams to transition from awareness to action. A clear map of access relationships helps teams understand where AWS exposure originates, but sustainable reduction requires embedding that insight into ongoing security processes. Here are a few ways visualization strengthens a security team.
Set decision criteria for reducing access
Establishing clear criteria for access reduction helps teams act consistently. This might include defining acceptable exposure levels for different data types or setting thresholds for when pathways should be reviewed or removed. Criteria like these prevent remediation from becoming an ad-hoc cleanup effort.
Bring visualization into everyday workflows
When access pathways are visible during architecture planning, incident response, or compliance reviews, teams can spot risks earlier. Visual context makes it easier to catch emerging issues before they become entrenched in production environments.
Use visuals to guide evidence-based remediation
Seeing why a pathway exists and how it connects across the environment allows teams to make targeted remediation decisions. Visual insight helps ensure that changes support business needs rather than applying blanket restrictions that may disrupt workflows.
By pairing graph-driven insight with structured decision-making, organizations can reduce AWS exposure in a way that is both repeatable and resilient.
How AWS Access Graph makes exposure more visible
AWS offers lots of flexibility when it comes to granting access; so much so that between access keys, identities, inline policies, and resource policies in AWS, there are over 17,000 possible IAM permissions to manage.
With Varonis’ access graph, security teams can easily analyze complex AWS access policies, identify overexposed sensitive data, and proactively block data pathways.
The access graph builds on Varonis’ existing in-depth view of AWS effective permissions, which normalizes permissions into an easy-to-understand CRUDS model. The AWS access graph gives security teams a visual map of effective access for every user, account, and role.
Visualize all identities with access to data and what policies affect their permissions.
.gif)
Visualize all identities with access to data and what policies affect their permissions.
With the AWS Access Graph, security teams can:
- Analyze effective access – quickly understand which access keys, groups, identity policies, inline policies, and resource policies affect access
- Prevent data exposure – see which policies expose sensitive data publicly
- Limit external access – surface trust roles that grant external access to internal resources
- Clean up stale policies – tighten access policies by identifying and removing stale or unused policies
The access graph updates dynamically when permissions change and allows security teams to analyze access bidirectionally—seeing both which entities can access a resource and what resources an entity can access.
Identify every resource that a single user has access to and map their pathways to sensitive data.
.gif)
Identify every resource that a single user has access to and map their pathways to sensitive data.
Cut off exposed pathways to data automatically
Being able to see access paths gives security teams a head start in protecting data. Importantly, however, a cloud security solution also needs to be able to remove risky access to effectively limit access to sensitive data and the potential blast radius of an attack.
Varonis builds scalable remediation directly into our platform, allowing security teams to secure AWS continuously and automatically.
With this release, we’re adding new policies specific to AWS to our already robust library of remediation policies. New remediation capabilities allow security teams to proactively block pathways to data and reduce exposure with the ability to:
- Remove stale policy assignments from users and roles
- Remove stale group memberships from users
- Restrict external access to roles (trust relationships)
- Delete unused customer-managed policies
Automatically and continuously revoke stale policy assignments.
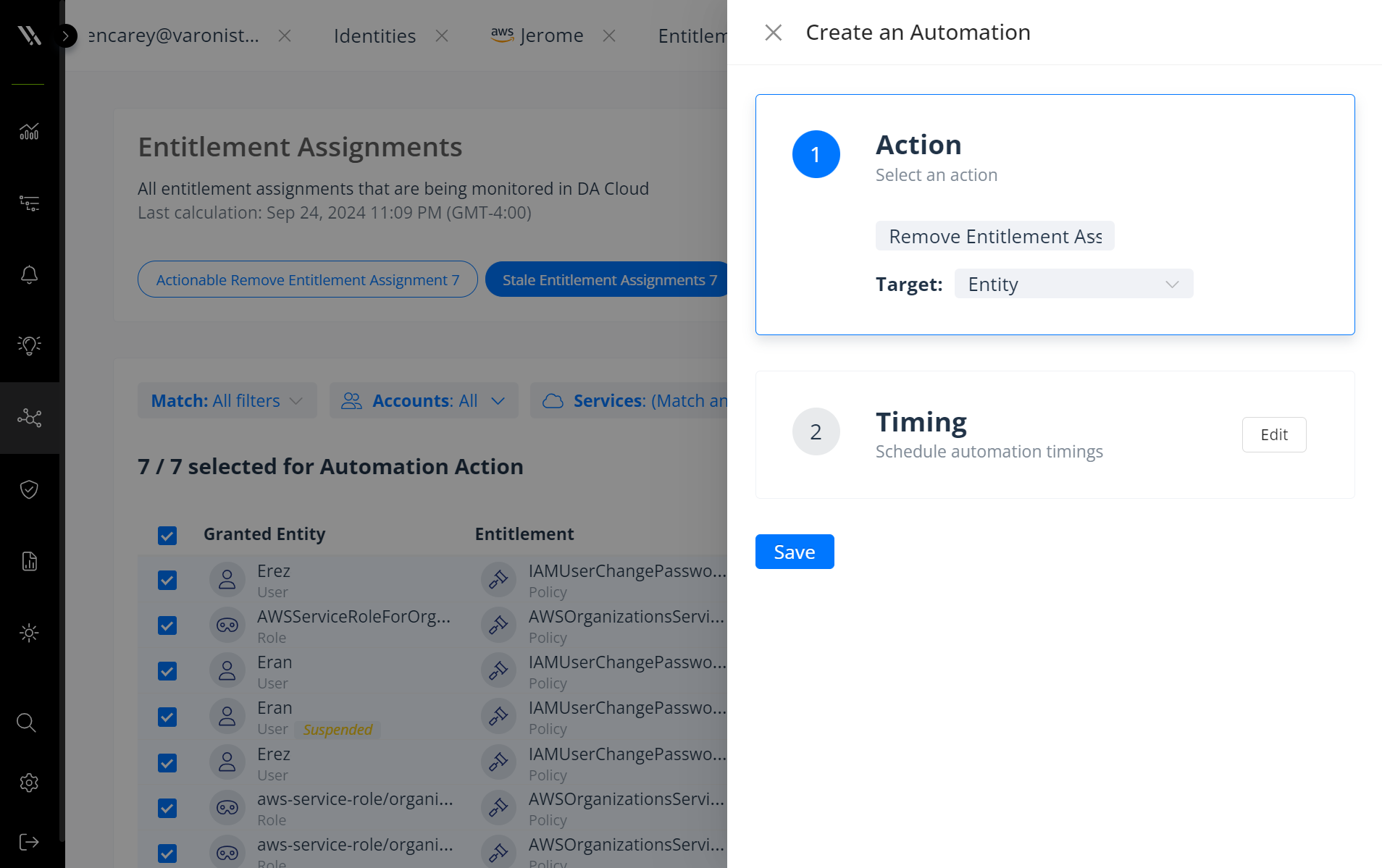
Automatically and continuously revoke stale policy assignments.
Improve security posture
Maintaining least privilege is a security best practice for good reason. It’s a big part of why using roles and resource-based policies is the recommended access method in AWS.
Direct permissions like those through ACLs, Public Access Blocks, or CloudFront Access can be easily forgotten and left unmanaged, leaving a larger blast radius for attackers to exploit.
The AWS access graph gives security teams a dashboard view of their security posture, showing where they are using best practices and where they may have risks like direct permissions, overexposed sensitive objects, or stale objects.
The AWS access graph provides a full view of the security posture and where sensitive data is exposed to risk.
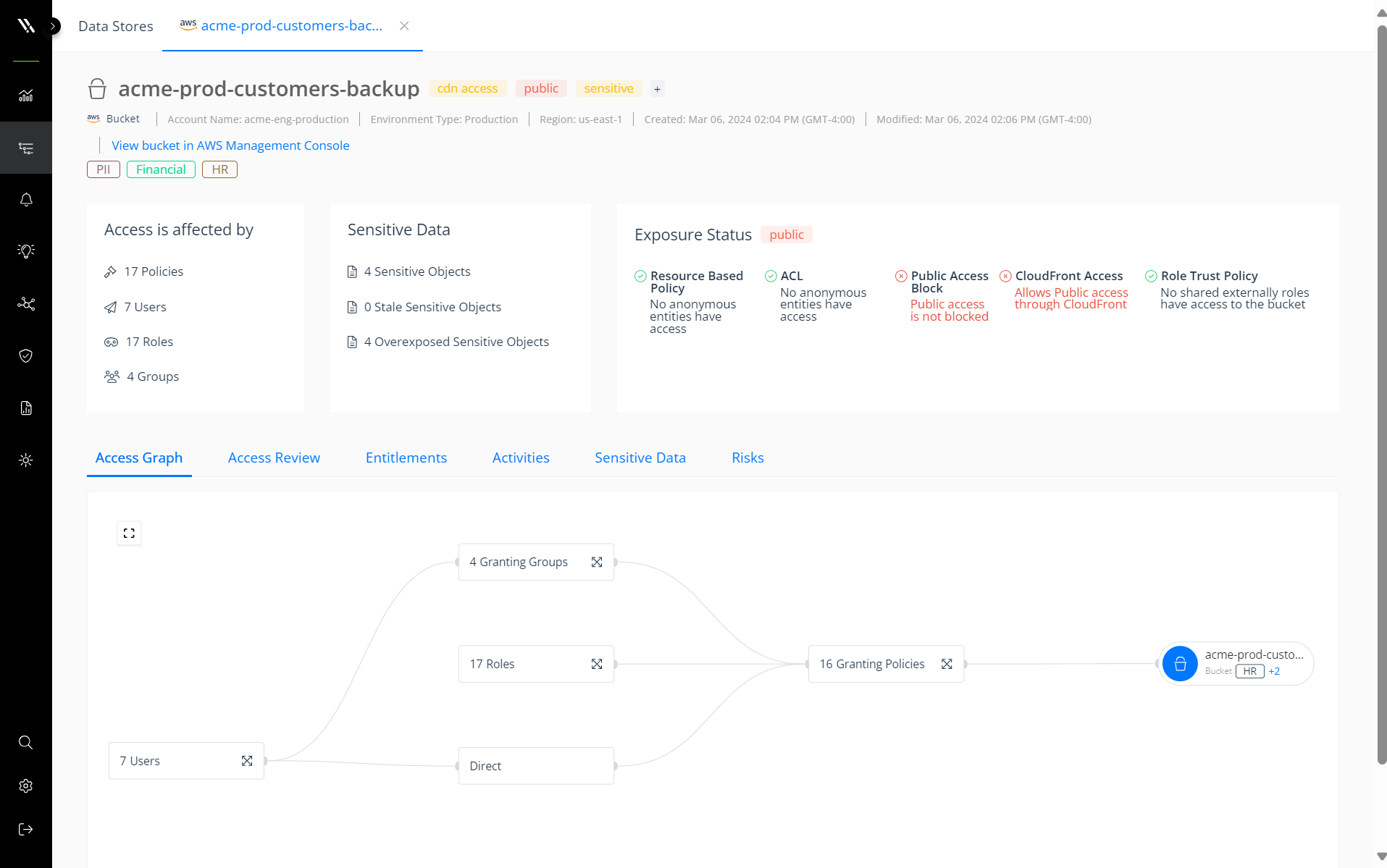
The AWS access graph provides a full view of the security posture and where sensitive data is exposed to risk.
Try Varonis for free.
Varonis’ cloud-native Data Security Platform is a force multiplier for security teams, helping them achieve outcomes with minimal manual effort.
With Varonis for AWS, organizations gain complete, contextual, and continuous visibility of their critical AWS data risk and achieve real security outcomes with the ability to automatically:
- Discover and classify critical data at scale, including shadow data
- Identify and remediate data exposure
- Detect configuration drift and fix critical misconfigurations
- Monitor activity to detect, investigate, and stop threats in real time
Want to try Varonis in your environment? Request a demo today and get a sneak peek with the video below.
FAQs about AWS data exposure
What contributes to sensitive data exposure in AWS environments?
Data exposure in AWS often stems from the complex layering of permission structures. Inline policies, resource-based policies, and identity access management (IAM) roles are often to blame. Users accumulate excessive access rights or "blast radius" over time. When old Access Control Lists (ACLs) are left unmanaged they can create unintended pathways for unauthorized entities to reach critical cloud resources.
How does an access graph help identify security risks?
An access graph provides a visual map of the relationships between identities, roles, and data It allows security teams to see effective permissions rather than just static policy definitions. By normalizing complex permission models into a simplified view, such as a CRUDS (Create, Read, Update, Delete, Share) model, teams can instantly identify which users have access to specific resources and determine if that access is necessary. This visibility is crucial for uncovering hidden risks like toxic combinations of permissions or external trust roles that might otherwise go unnoticed in standard log files.
Why is automating remediation important for AWS security posture?
Manual intervention is often too slow to address the scale and speed at which cloud environments change. Automated policies can continuously monitor for and revert dangerous misconfigurations. They remove stale policy assignments or sever unused trust relationships that grant external access. By systematically eliminating these risky pathways without human delay, organizations can enforce least privilege principles and significantly reduce the potential impact of a compromised account.
What is the "blast radius" in the context of cloud security?
The blast radius refers to the total amount of damage or data exposure that could occur if a specific identity, such as a user account or role, were compromised by an attacker. Visualizing this radius helps security teams understand the full scope of an entity's effective access. This includes the resources and sensitive files they can reach through direct permissions or assumed roles. Reducing this blast radius by cutting off unnecessary access paths is a fundamental strategy for limiting the impact of potential security incidents and protecting critical assets.
How do stale policies affect AWS vulnerability?
Stale policies widen the attack surface. Regularly identifying and cleaning up these stale policies is vital for maintaining hygiene in the cloud. By removing unused customer-managed policies or revoking old group memberships, businesses can ensure that only active, authorized personnel hold access rights.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.