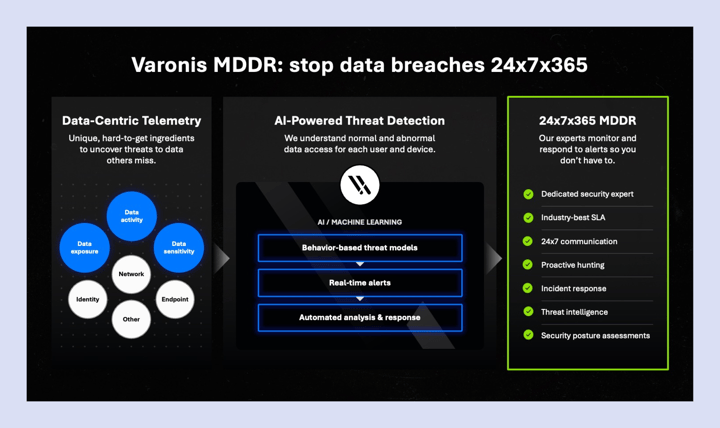
We're thrilled to announce the latest evolution in our mission to deliver effortless outcomes for our customers: Managed Data Detection and Response (MDDR). MDDR is the industry's first managed service dedicated to stopping threats at the data level.
The service combines Varonis' award-winning threat detection technology and automation with a global team of elite threat hunters, forensics analysts, and incident responders who investigate and respond to threats 24x7x365.
Our data-centric approach
Unlike traditional MDR services that are endpoint- and network-centric, MDDR focuses on a company's most critical asset — data.
"Organizations pay millions of dollars for threat detection products and services, yet when an incident occurs, they struggle to answer the most important question, 'Was any data stolen?'" said Matt Radolec, VP of Incident Response and Cloud Operations at Varonis. "Varonis brings threat detection and response closer to the target — closer to the data. MDDR gives customers the business outcome they want without the complexity and cost of building their own 24x7 operation."
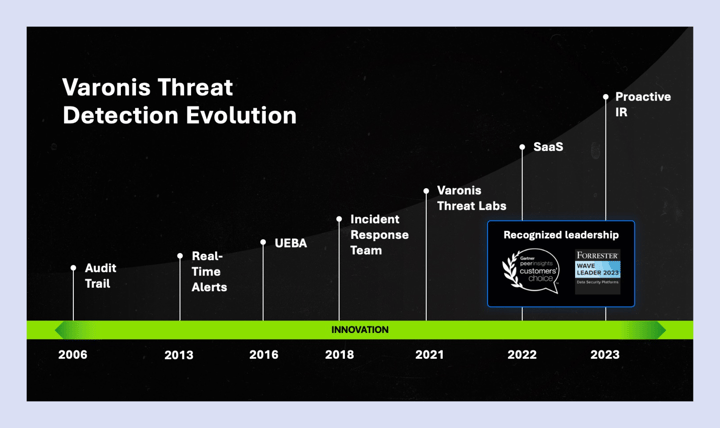
Varonis pioneered real-time data detection and response (DDR) in 2013, added advanced user and entity behavior analysis (UEBA) in 2016, and formed its incident response (IR) organization in 2018. Since its inception, Varonis IR has investigated over 10,000 incidents. Along the way, we’ve added accolades for our category-leading DSPM from top analyst firms and industry leaders.
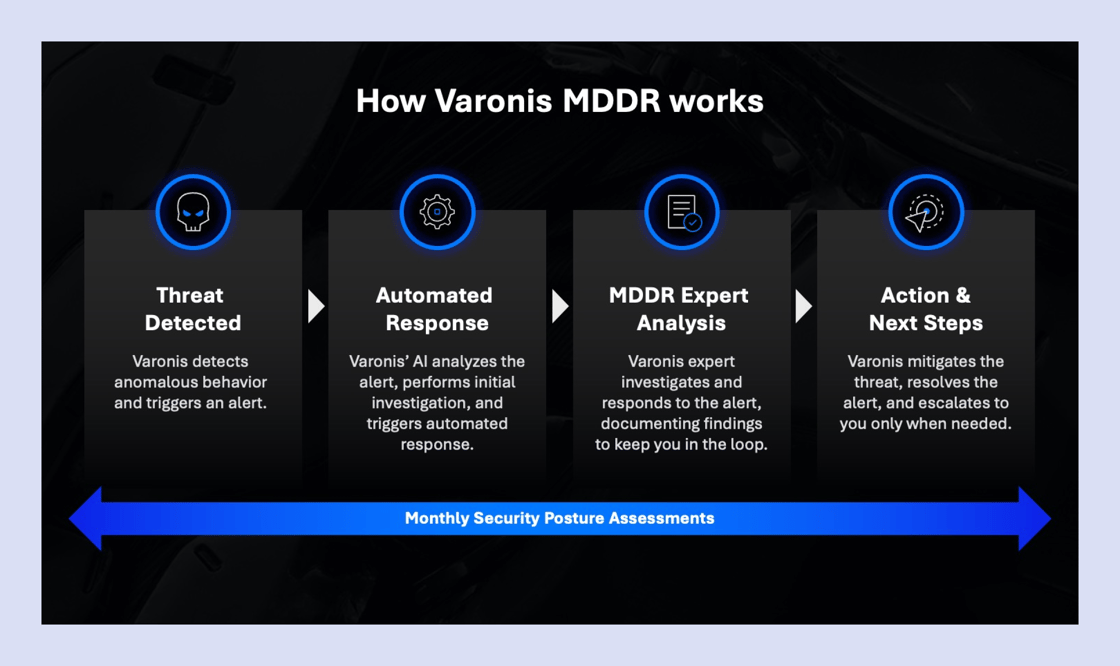
How MDDR works
Varonis MDDR enhances the overall customer value and fills a major void in the managed cybersecurity services market. When threat actors bypass endpoint and perimeter defenses, Varonis is an organization’s last and only line of defense.
MDDR gives our customers added assurance that their data is monitored around the clock:
- An industry-best SLA. Varonis MDDR offers a 30-minute response for ransomware attacks and a 120-minute response for all other alerts. The service also includes proactive threat hunting and monthly security assessments to ensure your data security posture is always improving.
- AI-driven investigations. MDDR is powered by Varonis’ proprietary data insights and an AI analysis engine that automates investigations. Critical alerts are sent to Varonis’ expert team for further investigation and mitigation.
- Immediate time-to-value. Up and running in hours, not days or weeks, MDDR is a turnkey solution that solves the challenge of protecting sensitive data automatically. We’ll seamlessly integrate with your team and escalate incidents only when needed.
The new service is delivered on top of Varonis's cloud-native Data Security Platform and is available today. Reach out to your Varonis representative, or see Varonis in action by scheduling your 30-minute demo and see how Varonis MDDR can help secure your organization.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.