When Varonis began protecting enterprise data in 2005, the cloud was just starting to form. Now, nearly 20 years since Varonis was founded, the way we create, consume, and secure data has changed dramatically. To meet the data security challenges of a cloud-first world and give our customers the best experience possible, we rebuilt Varonis as a cloud-native SaaS platform without taking any shortcuts.
Here’s how we did it.
Varonis as a cloud-native platform
While many companies take the shortcut of lifting and shifting to the cloud, Varonis purposefully took the opposite approach. We tasked our world-class R&D team with architecting our SaaS Data Security Platform from the ground up without any legacy constraints.
Our team had three non-negotiable requirements — varonis.io must be secure, compliant, and scalable.
To meet those needs, we adopted the secure software development lifecycle (SSDLC). This allowed Varonis to build secure applications and infrastructure quicker, addressing potential security and compliance issues up front.
Our customers operate some of the largest hybrid and multi-cloud environments in the world, creating terabytes of new data daily. To ensure scalability, Varonis worked with IaaS providers to project multi-year cloud growth and verify the capacity to cover our customers' needs seamlessly, whenever and wherever they are.
Varonis' cloud-native platform is fast and easy to deploy — take it from one of our SaaS customers, Drees Homes:
How does the cloud-based Varonis Data Security Platform work?
Our cloud-native platform taps into the intellectual property that has helped Varonis lead the data security market for nearly two decades. Under the hood, you’ll find ~145 patents for algorithms and data structures related to access-related event logging, user behavior analysis, granular data classification, data access intelligence, reporting, and much more.
The “brain” of the Varonis SaaS Data Security Platform is a collection of services running in Microsoft Azure.
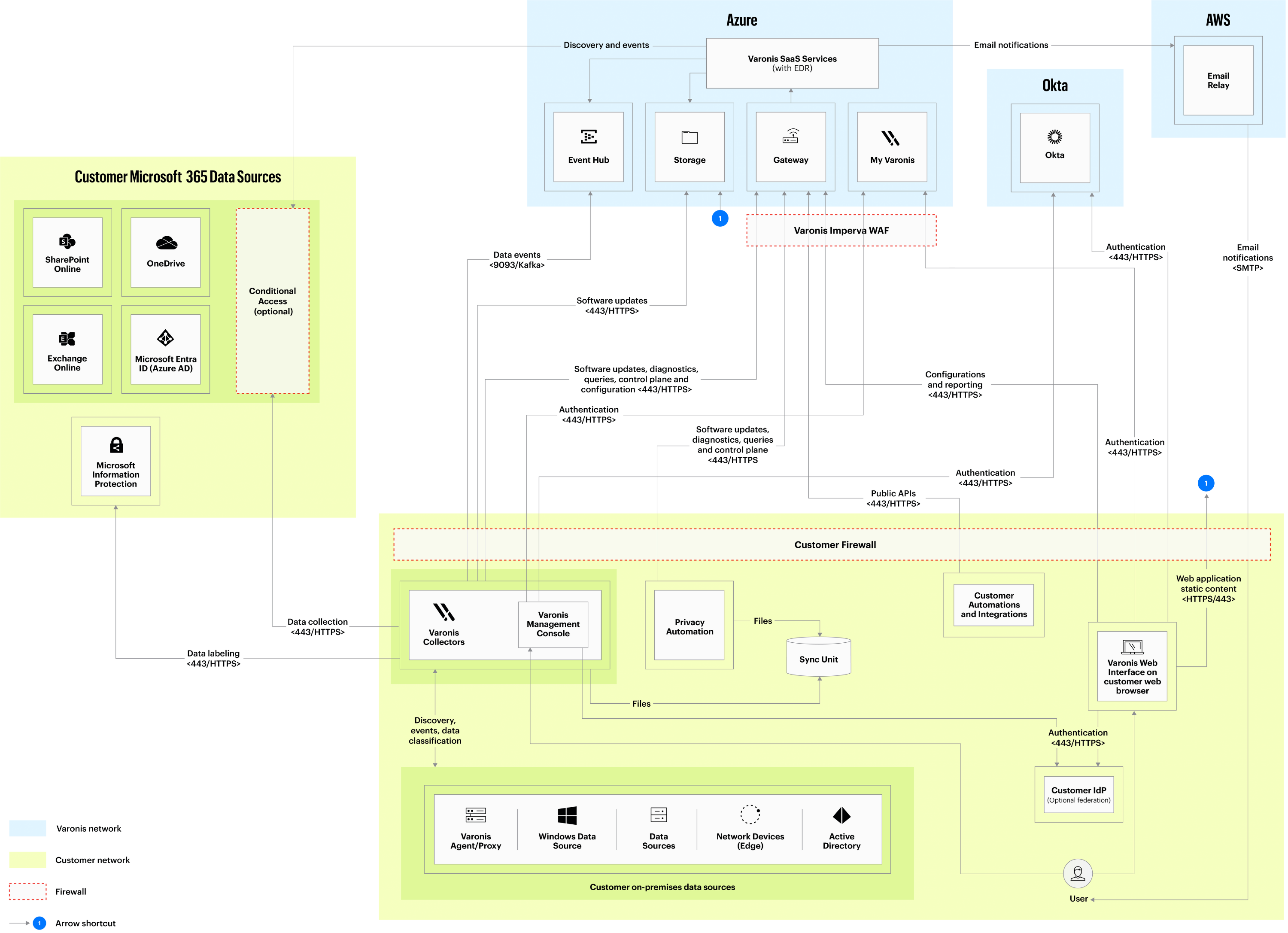
Collectors
Varonis' secure local Collectors are installed inside the customer's environment. They can be deployed either in the customer's cloud data center or in a physical data center. Collectors connect to both cloud or on-premises data sources, scan volumes and folders, classify file contents, and extract access events. The extracted metadata — including folder and file permissions, classification labels, and access events — are uploaded to the Varonis Data Security Platform.
For cloud data sources, metadata is extracted directly by the Varonis Data Security Platform. File contents are extracted and classified by the customer's Collector to avoid copying sensitive data to the Varonis cloud. Since the Collectors are deployed inside a customer's IT boundaries, data remains entirely under the customer's control, reducing risk and logistical costs.
Collectors that are deployed on-premises open outbound connections to Varonis and upload the metadata and classifications via the kafka protocol to the Varonis cloud platform.
Unmatched functionality
Within the Data Security Platform, customers can use dashboards and analytics to understand their data exposure in their organization, based on the collected metadata and audited access events. Our manual or automated remediations impact the actual data sources, applying actions like tightening permissions and creating focused security groups instead of broad global groups.
The Varonis Data Security Platform also provides near-real-time alerts, identifying patterns of access common to insider attackers and malware, alerting customers to threats, and preventing security incidents. For customers with the Varonis MDDR service, our team of incident responders and forensics experts investigate alerts on behalf of customers and escalate true incidents. Customers can also route alerts to extended detection and response products for further analysis or automatic response.
Alerts are generated based on models, which are trained using variety of machine learning algorithms, and are based on deep expertise of real world attack patterns observed by the Varonis Threat Labs team over many years.
Securing our SaaS platform
Varonis has invested heavily to create a secure platform, starting with adopting the SSDLC framework as part of our holistic development approach.
SSDLC’s proven approach focuses on adding security to the standard SDLC (software development lifecycle policy) and incorporating security as a major component of every phase of the SDLC. This empowers Varonis to build secure applications and IT systems more quickly, reducing the costs of rework and identifying and addressing potential security issues upfront.
Varonis has nearly 30 security policies in place, covering various security domains in our documentation and aligns policies with ISO/IEC standards (27001, 27017, 27018, and 27701), NIST 800-53, AICPA (American Institute of Certified Public Accountants), and other privacy regulations.
Varonis also implements:
- Rigorous change management
- Robust and secure continuous integration/continuous delivery (CI/CD)
- Data isolation inside the system
- Service compartmentalization and least privilege access
- Data encryption at rest and in motion
- Network segregation with web application firewalls (WAF) and network firewalls
- Distributed denial-of-service (DDoS) protection
- Continuous security scanning
- Frequent penetration testing
- Automated patching
- Access control and key management procedures
- SOC monitoring
Varonis complies with national data residence laws and judicial decisions, ensuring that customers' metadata is only kept within the country in which the Varonis region is deployed. Varonis supports multiple regions - for a complete list please see the Data residency in Security Standards and Practices.
If you want to learn more, we’ve dedicated a web page to outlining our security practices.
Built for petabyte-scale data environments
Varonis works with Microsoft Azure to project multi-year growth and usage, ensuring sufficient capacity will be present. By continuously monitoring usage, capacity can be added from Azure data centers without the need to add actual hardware. Cloud elasticity provides cost efficiencies by reducing capacity when it is no longer needed. This flexible architecture enables Varonis to offer a 99% service level agreement (SLA) to customers.
Technologically, Varonis implements true incremental scanning to ensure that only new or recently touched data is analyzed. This allows Varonis not to waste a customer's valuable time rescanning unchanged data, enabling Varonis to react quickly to the latest data and threats.
Customers can also rely on our teams to proactively monitor service health, investigate alerts and performance metrics, and perform maintenance often without disrupting business. Even in case of disaster scenarios, Varonis uses Azure geo-redundancy to handle failures of an individual data center, perform backups, and quickly recover.
Varonis is able to monitor both cloud and on-premise data sources, providing a single solution customers with hybrid deployments.
Varonis also supports large multinational and multi-data center customer deployments a couple ways:
- Customers can monitor petabytes of information without impacting performance.
- Collectors can be deployed across multiple regions so they are close in proximity to the data being monitored, which ensures maximum speed and efficiency.
- Varonis can collect, process, and store hundreds of millions of audit events generated by dozens of supported data sources (SaaS apps, NAS devices, email, network, etc.)

Why Varonis?
Varonis has years of experience securing 7,000+ organizations, including some of the largest IT environments from governments, multinational corporations, and healthcare organizations. With expertise in nearly three dozen regulatory and compliance frameworks, we understand how to handle complex security at scale. It is not unusual for customers to ask Varonis to do something that has never been done before.
The Varonis Data Security Platform comes with the unique ability to monitor dozens of different data sources, including SaaS applications, cloud infrastructure, network devices, email, and other systems that store and process sensitive data.
By providing an organization-wide view, companies can prioritize and focus on risks that matter to them, improving their security posture. Using the same policies and consistent analytical user interface, customers can apply data security management policies across all data sources without the need to implement specialized solutions for each data source separately.
Most data security products surface countless issues without separating the noise from meaningful alerts and give you a long to-do list to manually fix the problem. Varonis continuously classifies your data, remediates exposure, and stops cyberattacks with automation.
Varonis provides customers with autonomous and continuous data risk reduction alongside the world’s most sophisticated threat detection. Varonis captures more metadata about enterprise data and file systems than any other solution — no other vendor can capture and integrate this breadth and depth of information.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








