For the seventh consecutive year, Salesforce maintains the lion’s share of the CRM ecosystem worldwide. Salesforce comprises 20% of all CRM instances worldwide used to manage and process customer data. Businesses looking to secure their customer data and maintain compliance have a diverse set of security options available. One of most compelling of these options, however, resides within the Salesforce ecosystem itself: Salesforce Shield.
Discover your weak points and strengthen your resilience: Run a Free Ransomware Readiness Test
This guide will help you delve deeper into the robust controls available within Salesforce Shield and the advantages it has over the standard Salesforce security controls.
What is Salesforce Shield?

The Salesforce platform provides a very robust data security model out of the box to secure data at each level–from individual records and fields to the organization level. If you would like to understand the standard set of controls provided by the Salesforce platform, please refer to our article on Salesforce Data Protection for a more detailed analysis of the available options.
Salesforce Shield builds an additional layer upon these standard controls and provides a powerful suite of tools to strengthen further organization-level access, compliance, and trust in the Salesforce ecosystem. Let’s talk in detail about the various security tools and features within Salesforce Shield.
Salesforce Shield: Features You Need to Know
There are three primary features provided within Salesforce Shield – Shield Platform Encryption, Event Monitoring, and Field Audit Trail. Let us unpack each one of them in detail, with additional insights on how they improve on the standard controls provided by the platform.
Shield Platform Encryption
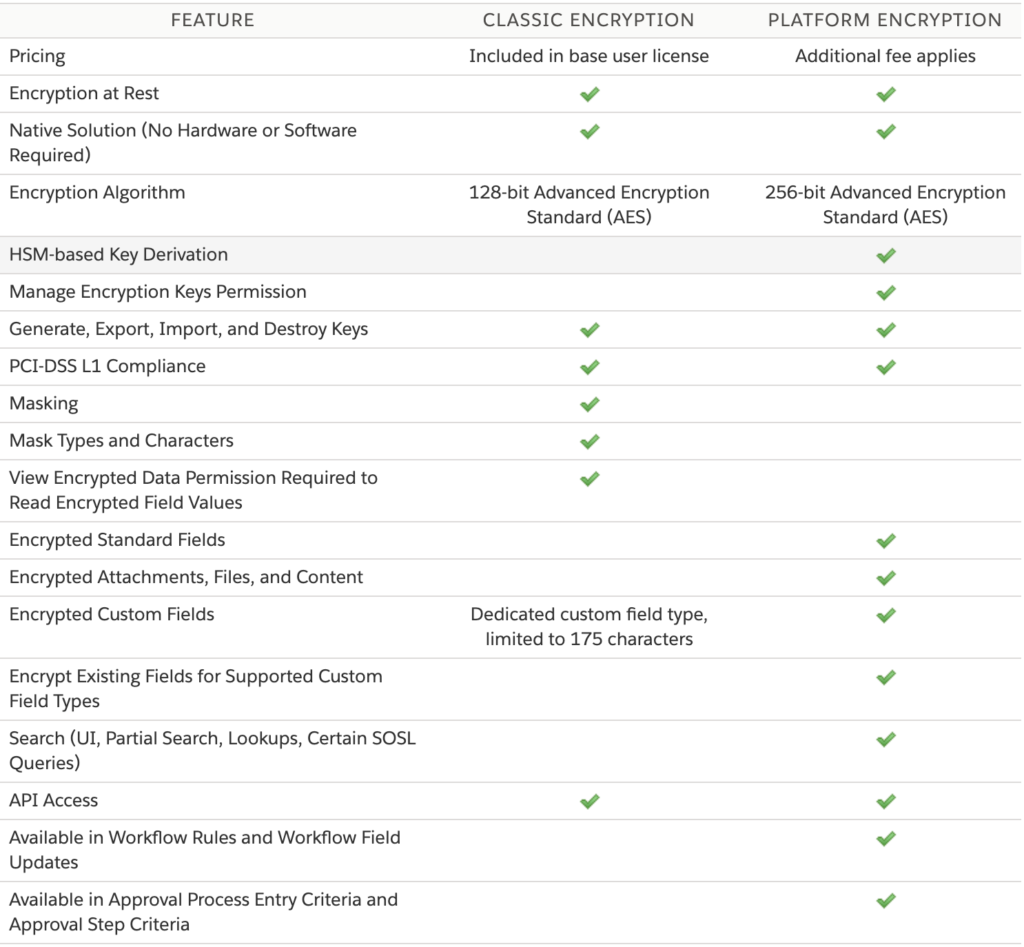
Shield Platform Encryption is a significant improvement on the Classic Encryption. Classic Encryption allows you to protect only specific custom fields, whereas Platform Encryption opens up possibilities to encrypt many standard and custom fields. It also considers all the use cases to find, render, and process encrypted data in these fields like search, workflows, and approvals, with the ability to customize and fine-tune data validation.
Platform Encryption also elevates the available encryption standards to 256-bit AES encryption and provides different encryption schemes for specific fields and elements and the ability to set, store, and fetch custom key information on-demand within the Salesforce instance or outside as needed.
A detailed rundown of the comparison between Classic Encryption and Shield Platform Encryption is available here.
Event Monitoring
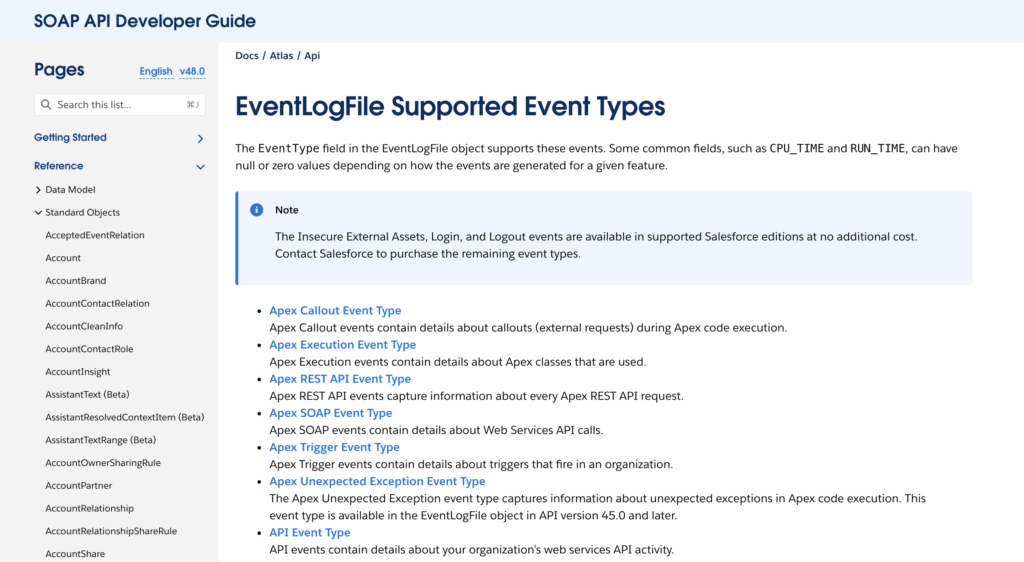
Event Monitoring is the second tool in the Shield suite of products that unlocks important insights for Shield users. Event Monitoring tracks 50+ event types within the Salesforce ecosystem, including access, web clicks, API calls, and report runs. It is a feature accessed through APIs and essentially stores event details in an API standard object called EventLogFile.
To simplify the daunting process of going through a massive amount of event logging, Salesforce provides the ability to view, filter, and download event logs through a web app called the Event Log File (ELF) Browser. If you are technically inclined to filter through the raw event data, you could also use cURL or Python to sift through the event data. You could also visualize the data in a more compelling approach using the Event Monitoring Analytics app, which comes with prebuilt dashboards. You could also port your data to visualize in your monitoring system of choice like Splunk, FairWarning, or New Relic.
Event Monitoring could help you with a variety of use cases to delve deeper into data usage behavior. It could help you diagnose adoption among newly deployed apps on Salesforce and spot usage problems early on. It could also provide deep insights into performance-related issues with your apps and highlight who is accessing critical business data, and help you prevent data theft and loss early on.
The detailed list of events that Event Monitoring enables for tracking and collating event information is available here.
Field Audit Trail
Field Audit Trail helps you prepare for stringent audit requirements on your Salesforce org by enabling you to track a wide variety of standard and custom objects. Audit Trail will allow you to specify a policy to retain archived history data for up to 10 years, using the Salesforce Metadata API. It also enables a higher limit of fields to be tracked per object (up to 60 versus 20 fields without this feature), and the tracking data does not count against your org’s data storage limit.
If you intend to enable Field Audit Trail and Platform Encryption in tandem, be informed that previously archived data would remain unencrypted before these features are enabled. You can find a complete list of the standard objects to set field history retention policies on this link.
Salesforce provides a comprehensive approach to implement every Salesforce Shield feature on the Shield Learning Map page.
Salesforce Shield: Aspects to Consider
If you are looking to secure your Salesforce org instance for audit and compliance requirements, Salesforce Shield enables a trio of powerful features to prepare accordingly. Having said that, it does come at considerable cost and effort to implement and enable Salesforce Shield in your Salesforce org.
Activation and Renewal Costs
Salesforce Shield is an add-on product on top of your existing Salesforce org, and the cost of activating Shield is a factor of your Salesforce org adoption. It could be a third of the total Salesforce licensing spend for many businesses, which is a marked departure from the usage-based model for Salesforce. As a result, your Salesforce spends each year could spiral up with an increase in product usage since your Shield expenses will increase in proportion to the same. As a Salesforce customer, you should ensure that you keep a close watch to negotiate your licensing agreement to activate and renew Shield each time.
Security and Encryption Efforts
Salesforce Shield acts in tandem with the security model you have defined at each level of your Salesforce org instance. It is critical that you implement and activate the data protection rules at the organization and the field levels before implementing any of these features, encryption in particular. Shield Platform Encryption can protect the visibility of critical fields, but it cannot cover up for any lax security rules set up for allowing inadvertent access to authorized users. Ensure that you have assessed your security model by taking the Salesforce Baseline Standard Health Check at a minimum and have spent considerable time and effort to activate the data security model before activating Salesforce Shield.
Salesforce Shield: A Worthy Addition to your Arsenal
Salesforce Shield is a great way to secure and monitor your Salesforce instance. As an admin, if you could imagine your data security model as a multi-layered cake, it would be prudent to think of Shield as the icing on the top. Ensure that your Salesforce data security model is consistently reviewed and updated to provide a strong foundation. When coupled with Salesforce Shield, you can tighten the screws further and create a formidable front to monitor for threats and safeguard your valuable customer data at all times.
Securing All your SaaS Apps
If your organization uses multiple SaaS applications in addition to Salesforce, it can be extremely tricky to answer questions like:
- Who’s got elevated permissions in each SaaS app?
- Who are my riskiest users?
- Which admin users don’t have MFA enabled?
- What actions did this user perform across Salesforce, Google, GitHub,etc.”
Each service has its own data types, permissions models, and activity log formats. The lack of unified visibility and control over data within SaaS and IaaS services leaves businesses vulnerable to devastating breaches.
DatAdvantage Cloud solves this problem by connecting to your biggest and most important cloud apps and data stores to collect, normalize, and correlate identities, permissions, and activities.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









