The “good news” about hacking is that while leaving you with potentially enormous incident response costs — customer notifications, legal fees, credit monitoring, class-action suits — your business can still generate revenue while all this is happening. Thank you cyber thieves for being merciful!
Ransomware disrupters, though, are not as generous. Their malware locks down entire file systems, preventing companies from operating and taking in revenue. The bottom line is that ransomware does literally affect the bottom line!
Want to learn ransomware basics and earn a CPE credit? Try our free course.
And ransomware ain’t going away. After a dip in activity, 2019 saw a breath-taking spike — a 500% increase from the previous year — in ransomware victims, including over 700 health care providers, 100 state and municipal government agencies, and 80 universities and colleges.
A ransomware incident at a Norwegian aluminum manufacturing company earlier this year provides a good example of the level of disruption that’s possible. The company experienced a massive attack that encrypted files on over 20,000 of its computers. Infected by the sinister LockerGoga, the manufacturer’s IT system was brought to a halt, and its 35,000 employees were forced to work manually. In other words, a 21st-century industrial company was brought back to working like 19th-century office clerks.
Industrial Scale Changes Everything
It wasn’t all that long ago, though, that cyber gangs were working at a less than industrial-scale. In the early aughts, one successful gang that targeted big-box retailers was really an informal group of hackers. They realized they could break into poorly secured WiFi networks from the parking lots of the branches, manually hunt for PII once in the network, and then sell credit card numbers on dark-web criminal exchanges. Some things never change so check out our white-hat-in-residence Kody’s WiFi videos to see what’s now going on in this space.
Fast forward to 2019 and consider the gang behind Sodinokibi, a devastating strain of ransomware that infects companies on a worldwide scale. They are more corporation than gang, and make their money through a ransomware-as-a-service business model. The front office receives a cut, in Bitcoins, of every ransom paid to their “affiliates”, smaller cyber thieves who initiate the actual ransomware infection.
There’s even a 24/7 call center to handle questions from victims. While many of the payments are small – in the tens of thousands —these busy affiliates are thought to have generated about a billion dollars in revenue for the gang.
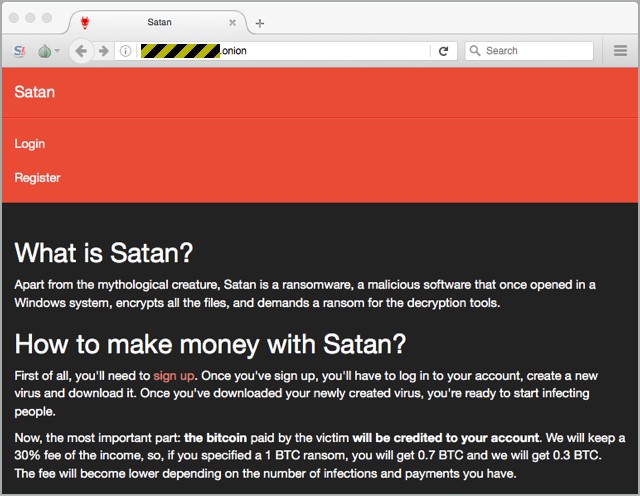
Further adding to the business-class level of the Sodinokibi, Inc. is their stream-lined operation: once the ransomware payload is on the system –typically after a phishing mail or a successful brute-force password — the cybercriminals can sit back and wait. Sodinokibi is completely automated!
The Sodinokibi ransomware searches to learn if certain known vulnerabilities are patched, and if not, it will exploit them and give itself higher-level privileges. It then generates its own keys and encrypts all files found locally and on the network, fully exploiting the multi-threading capabilities of the processor cores to speed up the attack. After the ransom note is displayed on users’ computers, the call center agents are ready to handle payments.
Fighting Back Against Automated Attacks
If that’s not enough, there’s still more discouraging news. Defenders are understaffed, corporate data continues to grow each year, and IT too often is in a pre-industrial age mindset when it comes to addressing a modern criminal organization. With their own R&D budgets, 21st-century cyber-thieves are always improving the product, making it faster, stealthier, and smarter about detecting and deleting backups and crippling other defenses.
IT can certainly get smarter about detecting phishing emails, improving password security, and educating employees on social engineered attacks. While making it harder for ransomware to gain a foothold is important, it doesn’t address the root problem of managing loose or excessive file permissions that make it possible for ransomware to encrypt huge segments of the file system.
Our own data security surveys show that companies have close to 1.5 million files per terabyte (TB) of data. Of those, over 350,000 files have global access available to anyone on the network including ransomware attackers. In other words, a ransomware attack may not need to have elevated permissions to be successful!
IT is then faced with the enormous problem of addressing proper file permissions across multi-terabyte file systems. Obviously, at this astronomical scale, defenders have to fight fire with fire – employ automated processes to set permissions on hundreds of thousands of folders and millions of files.
One important first step is to have in place automated data governance practices: software for efficiently scanning file systems, determining employee access patterns, and then setting permissions that limit access to those who really need it.
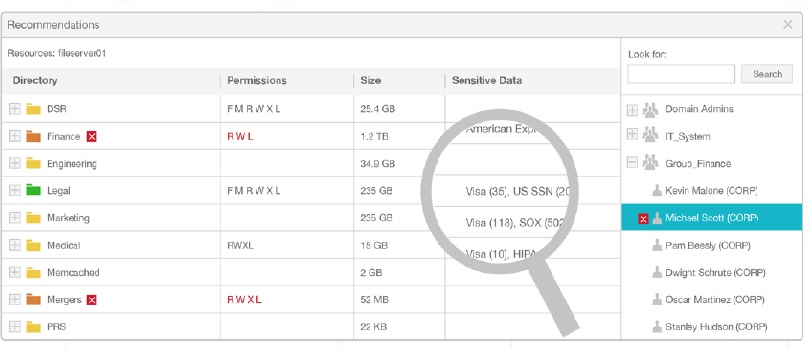
In addition, the software should be able to classify corporate data to find sensitive information — credit card numbers, passwords, and other account data — and lock these files down with special permissions restricted to very few employees. Again, with millions of files, this can’t be accomplished manually, or very effectively with home-grown IT tools.
Detecting Stealth Requires Automation and Machine Intelligence
Implementing good data governance through automated techniques limits total risk when an incident happens. However, you should want to detect and try to stop an attack before it advances very far.
Unfortunately, modern malware, like Sodinokibi, is designed to be hard to detect using conventional techniques, such as virus scanners. One of the reasons is that the malware takes advantage of existing Window software, particularly PowerShell, and other standard utilities. This is known as living-off-the-land. To IT staff, the malware might look like an average user running ordinary scripts when in fact it’s disabling defenses, searching for data, and then exfiltrating it.
How do defenders spot this specially crafted malware, in which the cyber organization has invested significant R&D dollars so that it can fly under the radar?
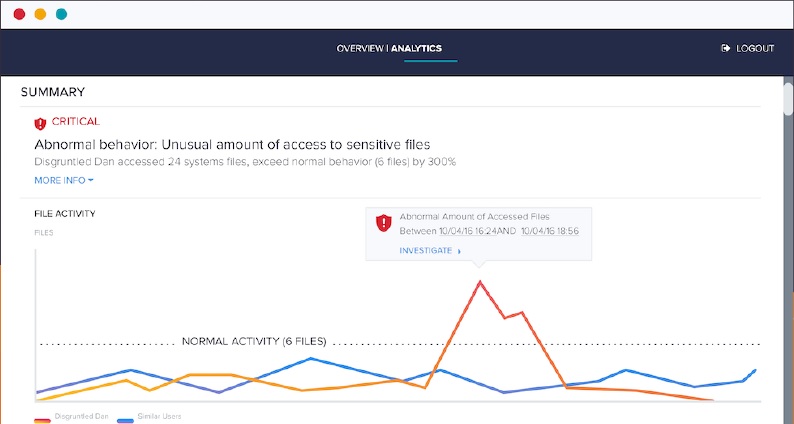
They need to respond with advanced techniques that more than matches the attackers’ cleverness. For example, one key idea is not to look for obvious signatures in the malware itself, but instead, focus on what it does.
In the case of ransomware, for example, we can expect rapid reads and writes of files within a directory. These and other unusual activities — brute force password attempts, updates to Windows registry entries, attempts to gain elevated permissions — can now be modeled and detection automated. Using machine-learning techniques to train malware threat software, companies have a far faster and more reliable approach to discover stealthy malware while keeping false positives to a minimum.
The Security Road Ahead
Finding sensitive data for millions of files, adjusting permissions, and then monitoring for threats in these enormous corporate file systems is beyond the capabilities of IT teams. That is, unless they have significant help from software automation.
That’s not to say that human intervention is not necessary. In fact, modern security tools powered by AI can display to IT security teams, through well-designed dashboards, the data security incidents and information that really do need the judgment of security pros.
AI then lets IT teams focus on those areas where their decisions make a difference while filtering out and handling threats that more easily fit into well-understood patterns that can be handled through automation.
Want to learn more? Check out our automated threat-detection solutions and reduce the risk of ransomware disrupting your business!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









