As more and more companies experience crippling security breaches, the wave of compromised data is on the rise. Data breach statistics show that hackers are highly motivated by money to acquire data, and that personal information is a highly valued type of data to compromise. It’s also apparent that companies are still not prepared enough for breaches even though they are becoming more commonplace.
We’ve compiled 84 data breach statistics that cover types of data breaches, industry-specific stats, risks, and costs, as well as data breach defense and prevention resources. Hopefully, this will help organizations understand the importance of data security and how to better allocate their security budgets.
Cost of a data breach
It’s no secret that data breaches are costly for businesses. To calculate the average cost of a data breach, security institutes collect both the direct and indirect expenses suffered by the breached organization.
Direct expenses include forensic experts, hotline support, credit-monitoring subscriptions and potential settlements. Indirect costs include in-house investigations and communication, as well as customer turnover or diminished rates from a company’s impacted reputation after breaches. See below to find out just how expensive it is to experience a breach and what elements cause the cost to rise even more.
- The average total cost of a data breach is $4.88 million. (IBM)
- The average per-record (per capita) cost of a data breach is $165, one dollar higher than 2022 (IBM).
- Healthcare breach costs have fell 10.6 percent to $9.77 million in 2024. (IBM)
- Healthcare data breaches have been the most expensive for 14 years in a row. (IBM)
- In 2023, detection and escalation represent the largest share of breach costs, at an average total cost of $1.58 million(IBM).
- The average cost of a breach with a lifecycle over 200+ days is $5.46 million (IBM).
- 51 percent of costs are incurred in the first year following a data breach (IBM).
- In 2024, the United States is the country with the highest average total cost of a data breach at $9.36 million. The Middle East is a close second with $8.75 million (IBM).
- The average cost of a mega-breach of 50 to 60 million records in 2024 is $375 million, a $43 million increase from 2023 (IBM).
- Annually, hospitals spend 64 percent more on advertising the two years following a breach (American Journal of Managed Care).
- Phishing is an expensive initial attack vector, with a cost of $4.88 million in 2024, slightly down from last year. (IBM)
- Organizations with a high level of noncompliance show an average cost of $5.05 million, 12.6 percent higher than average (IBM).
Breaches by the numbers
There are many factors to consider when preparing for and managing a data breach, such as the amount of time it takes to respond to a data breach and the reputational impact it has on your company. Read below to see how breaches happen, view average response times, and learn other crucial information.
How breaches happen
- 65 percent of data breaches in 2023 involved internal actors, and 35% involved internal actors (Verizon).
- 95 percent of data breaches are financially motivated. This is an increase of 24 percent since 2019. (Verizon).
- Ransomware accounts for nearly 24 percent of incidents in which malware is used (Verizon).
- In more than 70 percent of cases, breaches can be traced back to organized crime groups (Verizon).
Average response time and lifecycle
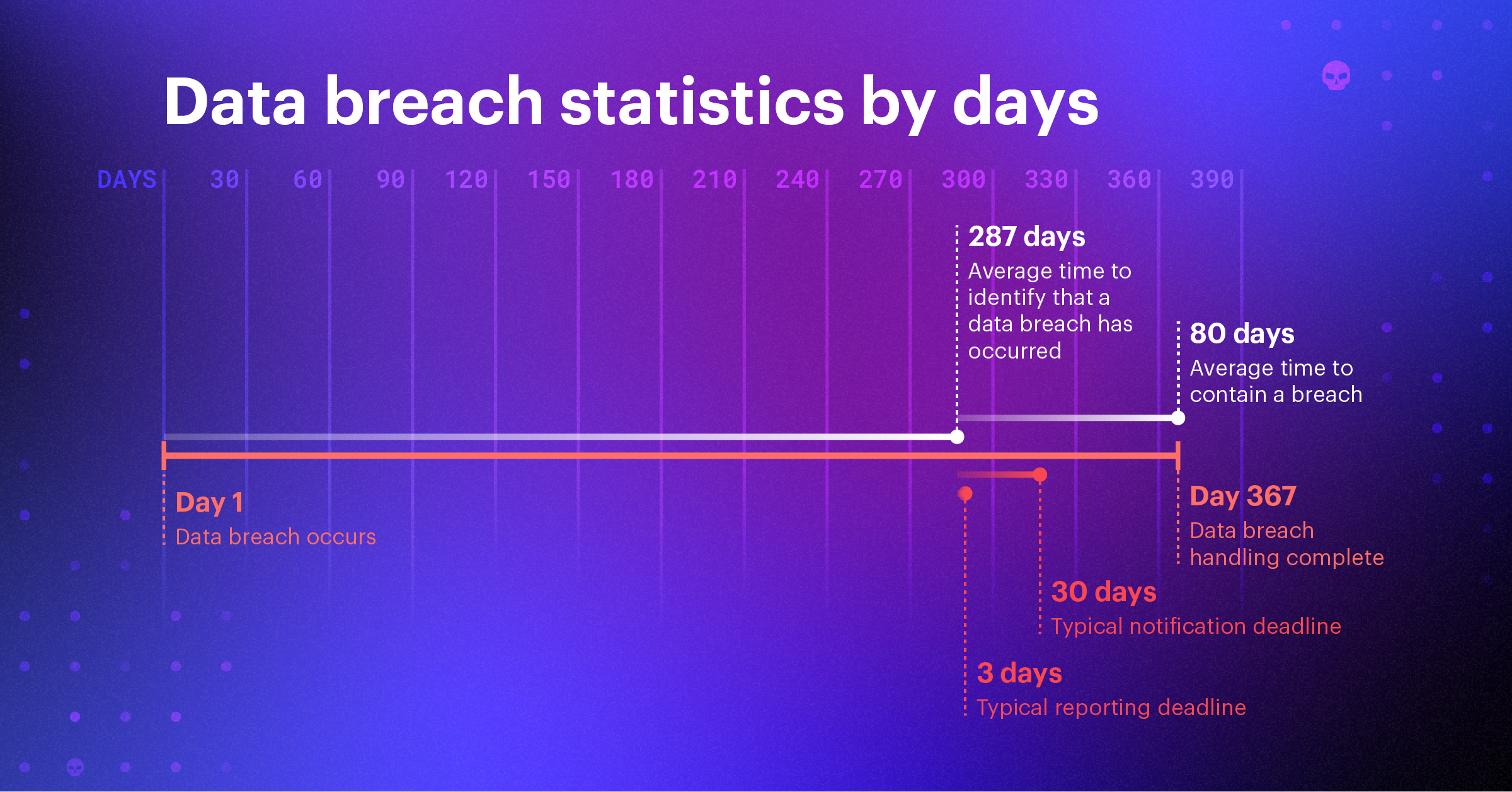
- It took an average of 194 days to identify a data breach globally in 2024, a slight decrease from 2023 (IBM).
- Organizations using threat intelligence identify threats 28 days faster on average (IBM).
- The average time to contain a breach was 64 days in 2024, 9 days less than in 2023 (IBM).
- Breaches that used stolen or compromised credentials took the longest to resolve, at 88 days (292 day data breach lifecycle) (IBM).
- A data breach lifecycle of under 200 costs on average $1.39 million less than a lifecycle of over 200 days (IBM).
Crucial information
- There were 6.06 billion malware attacks globally in 2023 (Statista).
- The number of data breaches in the U.S. has significantly increased, from a mere 447 in 2012 to more than 3,200 in 2023 (Statista).
- From November 2021 to October 2023, Microsoft Office applications were the most commonly exploited applications worldwide at 61 percent (Statista).
- In the five years from 2017 to 2022, the number of healthcare data records breached in the U.S. rocketed from 5.3 million to 51.4 million (Statista).
- In 2021, 98 percent of point-of-sale data breaches in the hospitality industry were financially motivated (Verizon).
- Online fraud cost Americans $12.5 billion in 2023 (TechRadar).
Remote working
The pandemic opened the pathway for remote workforces, which has been widely adopted as a normal business function. Proper security for virtual environments is crucial to stopping data breaches. Cybercriminals can target vulnerable victims in the healthcare industry, as well as those who are unemployed or working remotely. Here are a few of the most impactful data breach statistics related to remote work.
- The average total cost of a data breach was $173,074 higher when a remote workforce was a factor in causing the breach (IBM).
- 91% of cybersecurity professionals reported an increase in cyber attacks due to remote working (Zipdo).
- Web application breaches account for 25 percent of all breaches, consisting mostly of stolen credentials and vulnerabilities (Verizon).
- Cyber scams increased by 400 percent in the month of March 2020, making COVID-19 the largest-ever security threat (Reed Smith).

Data breach risk
IBM’s Cost of a Data Breach Report found that the average cost of a data breach is $3.86 million and moving in an upward trend. This data in particular validates the importance of investing in preventative data security. See the data breach risk statistics below to help quantify the effects, motivations and causes of these damaging attacks.
- As of 2021, a financial services employee has access to 11 million files (Varonis).
- The average distributed denial of service (DDoS) attack grew was 68 minutes in 2023 (THINK).
- The most common DDoS attack vectors in 2022 were NTP amplification, memcached, and UDP attacks (Nexusguard).
- More than 64 percent of financial service companies have 1,000-plus sensitive files accessible to every employee (Varonis).
- On average in 2021, 70 percent of all sensitive data was considered stale (Varonis).
- 58 percent of companies found more than 1,000 folders that had inconsistent permissions (Varonis).
- Only five percent of a company’s folders are protected (Varonis).
- 59 percent of financial services companies have more than 500 passwords that never expire, and nearly 40 percent have more than 10,000 ghost users (Varonis).
- Nearly three quarters of US small business owners reported a cyber-attack in 2022 (ITRC).
- 81 percent of confirmed breaches were due to weak, reused, or stolen passwords in 2022 (LastPass).
- A cyberattack is projected to occur every 39 seconds (University of Maryland).
- The larger the data breach, the less likely the organization will have another breach in the following two years (IBM).
- Security system complexity has the biggest impact on the total cost of a data breach (IBM).
- 62 percent of breaches not involving an error, misuse, or physical action involved the use of stolen credentials, brute force, or phishing (Varonis).
Breach projections
In the rapidly evolving field of data security, it’s vital that business owners stay informed of all potential issues. Below are the projected cybersecurity incidents that may occur in the coming years.
- By 2025, cybercrime is estimated to cost $10.5 trillion globally, increasing by 15 percent year over year (Cybersecurity Ventures).
- Natural disasters caused by climate change will drive more donations, which will result in an increase in phishing scams (Experian).
- Phishing scammers will also target online gamblers as more states legalize online sports betting (Experian).
- Cybercriminals will seek to exploit individuals who work, learn, and play games remotely (Experian).
- As more attackers learn of the vulnerabilities of cryptocurrency and NFTs, digital assets will be targeted as a means of identity theft (Experian).
- Cyberattackers will start to target physical infrastructure like electrical grids, dams, and transportation networks. This is especially likely as U.S. Congress attempts to rebuild outdated infrastructure (Experian).
- Security AI and automation will become a vital part of businesses protecting themselves from cyber attacks and detecting issues (IBM)
Historical data breach statistics
Once governments and businesses moved from paper to digital storage, data breaches became more commonplace.
In 2005 alone, there were 136 data breaches reported by the Privacy Rights Clearinghouse, and more than 4,500 data breaches have been made public since then. However, it’s reasonable to believe the actual number of data breaches is likely much higher, as some of the data breaches reported by the Privacy Rights Clearinghouse have unknown numbers of compromised records.
Below, we have provided a list of data breach statistics that led up to and launched the age of data infiltration.
- The first computer virus, known as Creeper, was discovered in the early 1970s (History of Information).
- In 2005, the Privacy Rights Clearinghouse began its chronology of data breaches (Symantec).
- The first-ever data breach in 2005 (DSW Shoe Warehouse) exposed more than one million records (Symantec).
- The largest insider attack occurred between 1976 to 2006 when Greg Chung of Boeing stole $2 billion worth of aerospace documents and gave them to China (NBC).
- AOL was the first known victim of phishing attacks in 1996 (Phishing).
- In 2017, one of the three major U.S. credit reporting agencies, Equifax, accidentally exposed 145.5 million accounts, including names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers of American consumers (Symantec).
- Social media data breaches accounted for 56 percent of data breaches in the first half of 2018 (ITWeb).
- The United States saw 1,802 data breaches in 2022 and had 422.14 million records exposed (Statista).
- Data breaches exposed 4.1 billion records in the first six months of 2019 (Forbes).
- Cyberattacks are considered among the top ten risks to global stability (World Economic Forum).
Largest recorded data breaches
Data breaches are becoming more and more common, and some of the most recent data breaches have been the largest on record. Here’s a look at the largest data breaches in history.
- Cam4 holds the record for the largest data breach of all time, with ten billion compromised accounts (Statista).
- In 2013 Yahoo was hacked, affecting all 3 billion of their accounts. This was the worst breach for nearly a decade (New York Times).
- In 2019, First American Financial Corp. had 885 million records exposed online, including bank transactions, social security numbers and more. (Gizmodo)
- In 2019, Facebook had 540 million user records exposed on the Amazon cloud server (CBS).
- In 2018, a Marriott International data breach affected roughly 500 million guests (New York Times).
- In 2016, the AdultFriendFinder network was hacked, exposing 412 million users’ private data (ID Strong).
- Experian-owned Court Ventures inadvertently sold information directly to a Vietnamese fraudster service, involving as many as 200 million records (Forbes).
- In 2017, data of almost 200 million voters leaked online from Deep Root Analytics (CNN).
- In 2014, eBay was hacked, resulting in access to 145 million records (Yahoo).
- In 2008 and 2009, Heartland Payment Systems suffered a data breach, resulting in the compromise of 130 million records (Tom’s Guide).
- In 2007, a security breach at TJX Companies Inc. compromised 94 million records (Information Week).
- In 2015, Anthem experienced a breach that compromised 80 million records (Anthem).
- In 2013, Target confirmed a breach that compromised 70 million records (KrebsOnSecurity).
Data breach prevention
There are various proactive approaches you can take to lower your chances of experiencing a breach. Identifying cybersecurity risks to your data is a good place to start. See how companies are shifting their budgets and priorities to protect their assets and customers from cyberattacks.
- 63 percent of companies have implemented a biometric system or plan to implement one (Veridium).
- Security budgets have increased at an average of 6% in 2023, down from the 17% increase in the previous budget cycle (Help Net Security).
- IT budgets will increase in 40 percent of organizations in 2023, with cybersecurity being one of the top categories of increased investment (NordLayer).
- It was predicted that global cybersecurity spending would exceed $1.75 trillion cumulatively between 2021 and 2025 (Cybercrime Magazine).
- Worldwide IT security spending grew to $193 billion in 2022 and is projected to increase by 12.1 percent to $219 billion by the end of 2023 (ITC).
- Following a big jump up in 2021, the number of ransomware attempts dropped to 494 million in 2022. This is still 60 percent higher than in 2020 (Statista).
- 58 percent of organizations will have moved their application portfolios to a public cloud in the next two years. This changes the tools and approaches they will need to prevent attacks (CSO).
Definition of a data breach
A data breach is any incident in which confidential or sensitive information has been accessed without permission. Note: data does not have to have been exfiltrated from the network to be considered a breach. Breaches are the result of a cyberattack by criminals who gain unauthorized access to a computer system or network. They then steal the private, sensitive, or confidential personal and financial data of the customers or users contained within.
Common cyberattacks used in data breaches are:
The origin of data breaches
Although data breaches seem more prevalent nowadays because of cloud computing and increased digital storage, they have existed as long as companies have maintained confidential information and private records. However, publicly-disclosed data breaches increased in frequency in the 1980s, and awareness of data breaches grew in the early 2000s.
According to the Office of Inadequate Security, in 1984 the global credit information corporation known as TRW (now called Experian) was hacked and 90 million records were stolen. In 1986, 16 million records were stolen from the Canada Revenue Agency.
Most public information on data breaches only dates back to 2005. In 2020, multiple surveys showed that more than half of Americans were concerned about data breaches during natural disasters, as well as personal safety resulting from the pandemic. Data breaches today tend to impact millions of consumers in just one companywide attack.
How do data breaches occur?
A data breach occurs when a cybercriminal infiltrates a data source and extracts confidential information. This can be done by accessing a computer or network to steal local files or by bypassing network security remotely. While most data breaches are attributed to hacking or malware attacks, other breach methods include insider leaks, payment card fraud, loss or theft of a physical hard drive of files, and human error. The most common cyber attacks used in data breaches are outlined below.
Ransomware
Ransomware is software that gains and locks down access to vital data. Data is encrypted in files and systems, and a fee — commonly in the form of cryptocurrency — is demanded to regain access to them.
Common Target: Enterprise companies and businesses
Malware
Malware, commonly referred to as “malicious software,” is a term that describes any program or code that harmfully probes systems. Malware is designed to infect your computer and commonly masquerades as a warning against harmful software. The fake warning attempts to convince users to download varying types of software, and while it does not damage the physical hardware of systems, it can steal, encrypt or hijack computer functions.
Malware can penetrate your computer when you are navigating hacked websites, downloading infected files, or opening emails from a device that lacks anti-malware security.
Common Target: Individuals and businesses
Phishing
Phishing scams are one of the most common ways hackers gain access to sensitive or confidential information. Phishing involves sending fraudulent emails that appear to be from a reputable company, with the goal of deceiving recipients into either clicking on a malicious link or downloading an infected attachment, usually with the intent of stealing financial or confidential information.
Common Target: Individuals and businesses
Denial of Service (DoS)
Denial of Service is a cyber attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting the services of a host connected to the internet. It is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
Common Target: Sites or services hosted on high-profile web servers, such as banks
Data breach defense + prevention resources
Companies need to examine lessons from the GDPR and update their data governance practices as more iterations are expected in the coming years. It’s crucial to properly set permissions on files and remove stale data.
Keeping data classification and governance up to par is instrumental to maintaining compliance with data privacy legislation like HIPAA, SOX, ISO 27001 and more. Today, modern solutions offer great protection and a more proactive approach to security to ensure the safety of sensitive information.
Examine your data breach response plan and try a free risk assessment to see where your vulnerabilities lie.
The following resources offer additional information on the improvement of data protection and tips for data breach prevention.
- Varonis Red Alert Data Breach Report
- Varonis Financial Data Risk Report
- Verizon’s Data Breach Investigations Report (DBIR)
- IBM’s Cost of a Data Breach Report
- DataLossDB, maintained by the Open Security Foundation
- Ponemon Institute
- Data Breach Risk Calculator
- Identity Theft Resource Center
- RiskBased Mid-Year Data Breach Report
Data breach insurance types
In order to mitigate the risk that comes along with data loss, many companies are now purchasing data breach insurance to support their data breach prevention and mitigation plans. Data breach insurance helps cover the costs associated with a data security breach. It can be used to support and protect a wide range of components, such as public relations crises, protection solutions and liability. It may also cover any legal fees accumulated from the breach.
Common types of data breach insurance are:
First-party insurance
With many different kinds of consequences that occur due to a data breach, significant time and money will be spent to recover. From recovering data and notifying stakeholders, first-party insurance covers the following:
- Investigating costs
- Notifying all affected parties
- Fielding inquiries
- Tools to help affected parties
Third-party insurance
Third-party insurance is primarily used by contractors and IT professionals to lessen their liability. The covered expenses may include things such as the following:
- Lawyers’ fees
- Settlements
- Judgments and liability
- Other court costs such as witness fees, docket fees, etc.
Data breach statistics FAQs
Below are some of the most frequently asked questions about data breaches with answers supported by data breach statistics and facts.
How many data breaches occur?
A: The Privacy Rights Clearinghouse keeps a chronology of data and public security breaches dating back to 2005. The actual number of data breaches is not known. The Privacy Rights Clearinghouse estimated that there have been 9,044 public breaches since 2005, however more can be presumed since the organization does not report on breaches where the number of compromised records is unknown.
What was the biggest data breach in history?
A: Cam 4 holds the record for the largest data breach of all time with over 10 billion compromised accounts (Statista).
How many data breaches were there in in the last year?
A: There were 5,212 confirmed data breaches in 2022 (Verizon).
How much does a data breach cost?
A: As of 2023, the average total cost of a data breach is $4.45 million (IBM).
What is the average size of a data breach?
A: 25,575 records (IBM).
Regardless of industry, there’s no question that data security and defense is highly valuable for companies in the digital economy we live in. Assess your business’s cybersecurity risk to make company-wide changes and improve overall security behavior.
Avoid being a data breach statistic by doing everything possible to protect your business from experiencing a breach. For more information on data security platforms learn how data protection solutions could positively impact your business.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.